Prisma AIRS
Use the Prisma AIRS AI Sessions and API Application Views
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Use the Prisma AIRS AI Sessions and API Application Views
Learn how to use the AI Session and A
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Prisma AIRS's AI Sessions and API Applications views provide you with essential
visibility into the runtime security of your AI applications. You can verify the
legitimacy of threat blocks, understand the context of security violations, and manage
your AI applications from a single interface in Strata Cloud Manager (SCM). Moreover,
you’re able to view the actual prompts and model responses that trigger security alerts.
And Additionally, you can view the specific LLM payloads that violated security
policies, helping you validate detections and reduce false positives.
The Applications View provides a centralized dashboard showing all your AI
applications with their associated security violations, allowing you to quickly identify
which applications need attention. You can filter applications by monitoring period,
violation severity, tags, security profiles, and cloud provider. For each application,
you can see detailed metadata, violation trends, and linked security profiles.
The Sessions View allows you to examine individual AI sessions, which are
logical groupings of related API calls sharing the same transaction ID. This view shows
the sequential flow of prompts and responses that make up a conversation, with clear
indicators of which content violated security policies. You can drill down into
individual transactions to see the exact payload content and which security profiles
were violated.
This feature requires your applications to send a consistent transaction ID
with related API calls to properly correlate them into sessions. If no transaction ID is
provided, the system automatically creates one for each atomic API call. For enterprise
deployments, the feature supports RBAC integration to ensure that sensitive data in
prompts and responses is only accessible to authorized personnel.
API Applications View
Prisma
AIRS Runtime Security's AI Application view provides you with comprehensive
visibility into your AI-enabled applications in Strata Cloud Manager (SCM). This
feature addresses a critical challenge for security teams - understanding which AI
applications exist in your environment and identifying which ones have security
violations.
You can discover and monitor all AI applications that
interact with your Prisma AIRS API, with each application displaying its associated
sessions, violations, and security profiles. The Application View enables you to
quickly identify which applications have the most violations through a top-level
dashboard that shows total applications with violations and application violation
trends over time. You can filter applications by monitoring period, violation
severity, tags, security profiles, and cloud provider to focus on specific segments
of your environment.
For each application, you see detailed
information including application ID, name, tags, cloud provider, and violation
metrics. When you select a specific application, a detailed flyout view reveals
expanded metadata, session counts, violation breakdowns by severity and type, and
linked security profiles. This context helps you prioritize which applications need
immediate security attention and understand the nature of the violations occurring
in each application.
The Application View displays a dashboard that
shows total applications with violations and application violation trends over time.
The Total Applications with Violations pie chart shows your
top five applications with security issues over the selected period. The
Application Violations Timeline presents a trend view of violations
across all applications for the past 30 days, allowing you to identify patterns or
spikes in security incidents.
The AI Application View becomes more
valuable when paired with the AI Sessions View, as you can click through from an
application to see all of its associated sessions, providing the context needed to
analyze and address security incidents. You can see the details of manually-created
applications and applications that are automatically discovered when developers make
API calls with new application names in metadata, enabling comprehensive visibility
regardless of how applications are onboarded.
You can filter applications using
several criteria. The Monitor Since filter limits results to a
specific time range. Violations by Severity allows you to focus
on critical, high, medium, or low severity issues. Tags filters
by user-defined application tags. Security Profiles Applied
narrows results to applications using specific security configurations.
Cloud filters by cloud provider, and
Source indicates the detection method.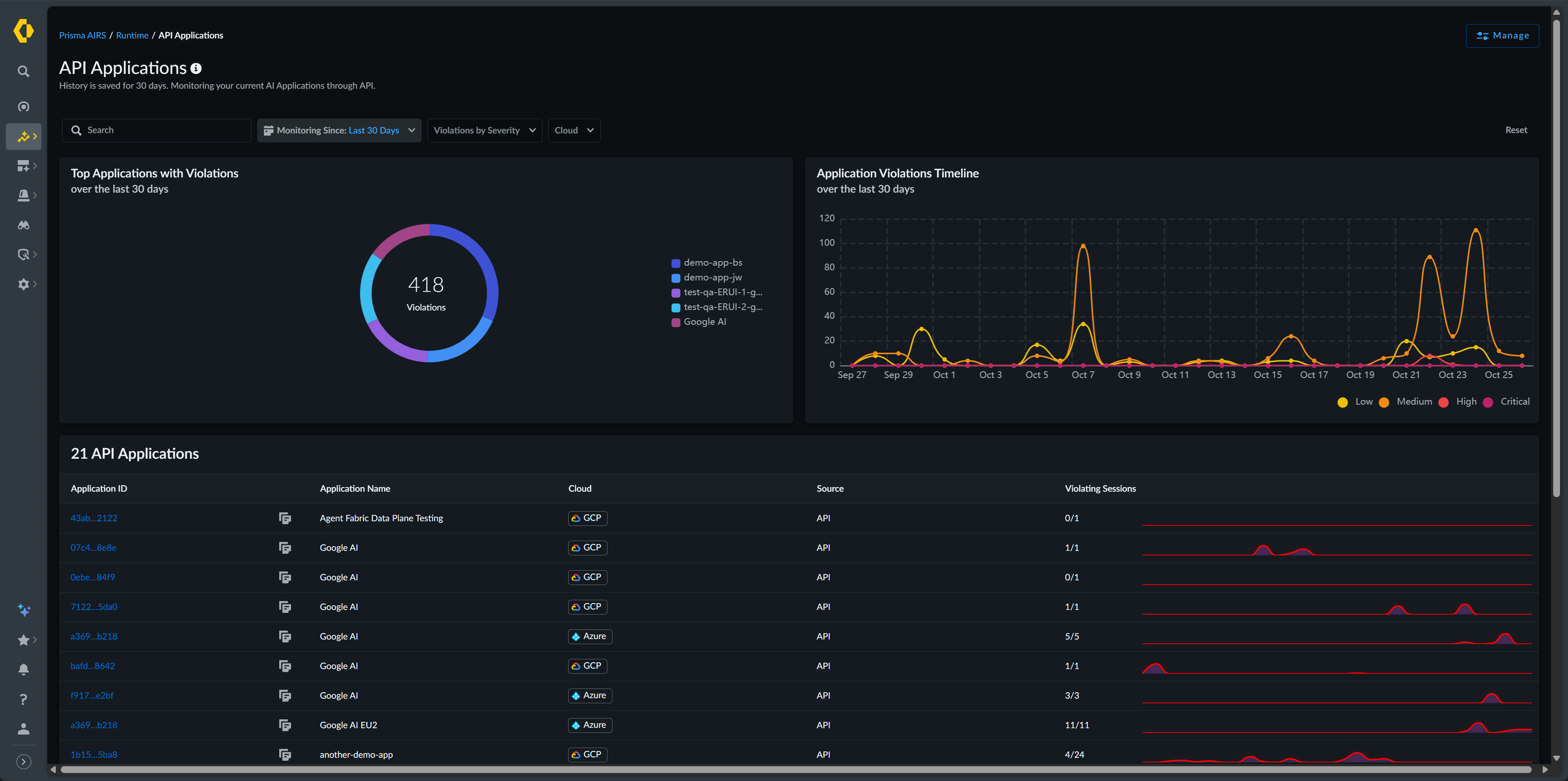
| Column Name | Description |
|---|---|
|
Application ID and Application Name
|
Unique identifiers for your application
|
|
Tags
|
User-defined labels for organization.
|
|
Cloud
|
The cloud service provider (AWS, Azure, GCP, or Other) hosting
your application
|
|
Source
|
The source of detection; how the application was discovered
|
|
Violating Sessions
|
The number of sessions that violate your enabled security
profiles and the total number of sessions detected
|
You can view further details about each application by clicking on
the Application Name.
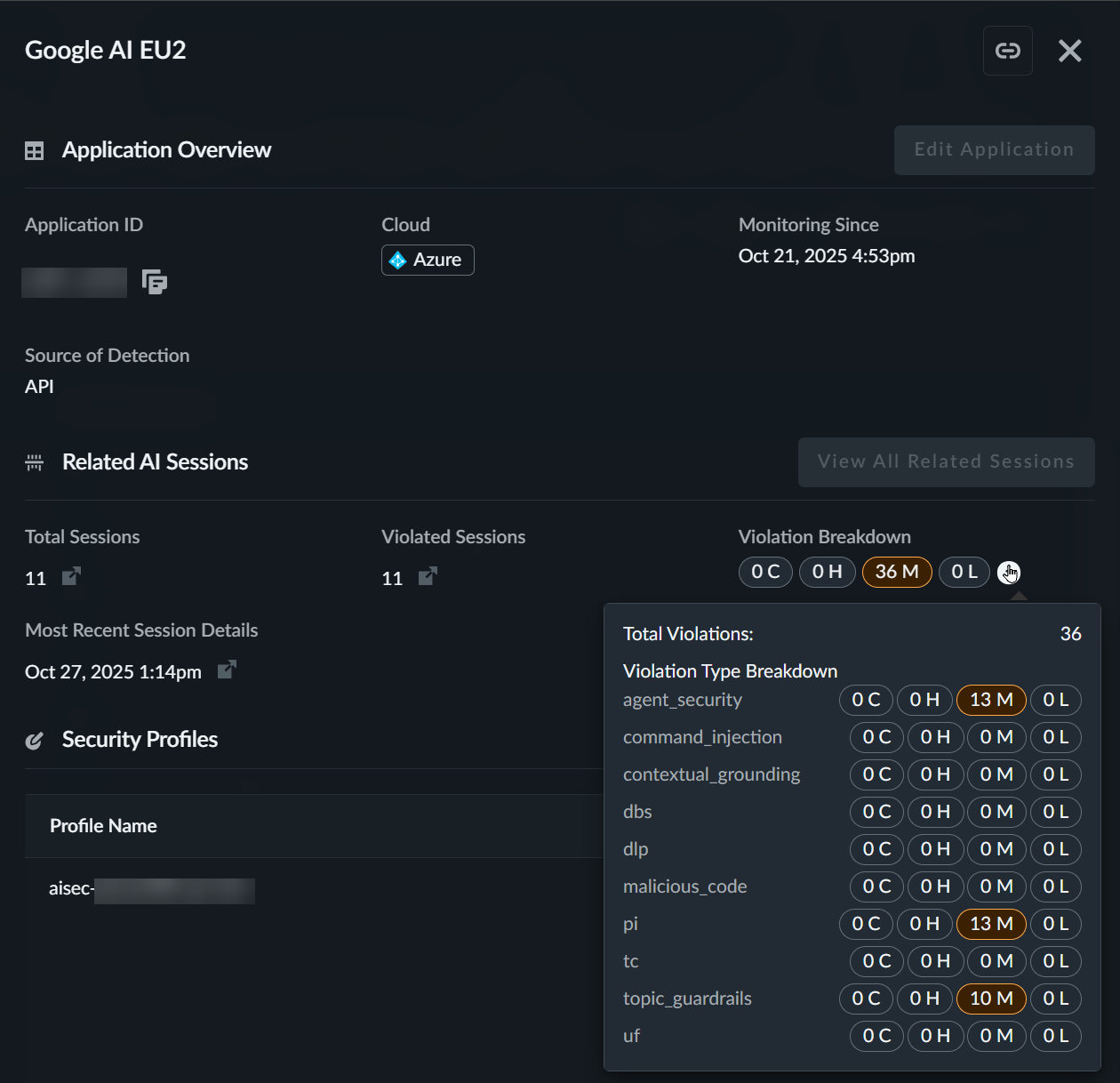
| Field Name | Description | |
|---|---|---|
|
Application Overview
| ||
|
Application Name
|
Unique identifier for your application
| |
|
Tag
|
User-defined labels for organization
| |
|
Cloud
|
The cloud service provider (AWS, Azure, GCP) hosting your
application
| |
|
Linked Security Profile
|
Shows which security configurations are protecting the
application
| |
|
Monitor Since
|
Indicates when monitoring began when monitoring of this
application began
| |
|
Source of Detection
|
Shows how the application was discovered
| |
|
Related AI Sessions
| ||
|
Total Sessions
|
The total session associated with this application
| |
|
Violated Sessions
|
The total number of sessions that violate a security profile
| |
|
Violation Breakdown
|
Provides details about the number of violations of each
severity level.
You can hover over the information icon to view
additional details about the violations, such as the violation
types and the number and severity of each type.
| |
|
Security Profile Overview
|
Provides details on the security policies protecting this
application
| |
AI Sessions View
Prisma AIRS
Runtime Security's AI Session view enables you to inspect and analyze individual AI
conversations processed through your Prisma AIRS API. This view provides visibility
into AI transactions by allowing you to verify the legitimacy of security findings
and understand the context in which violations occur.
To implement
this feature, you must configure your applications to include a consistent
transaction ID with related API calls. This allows the system to correlate requests
into coherent conversations, providing the context necessary for meaningful security
analysis.
The Session View displays high-level statistics at the top
of the page. These metrics aggregate data over the selected time period and display
percentage changes compared to the previous comparable period. The Total
AI Sessions vs. Violations bar chart visualizes the relationship
between your total sessions and those with security issues over time.
You can
filter sessions using several criteria. The Monitoring Period
lets you select from the past one hour, 24 hours, 7 days, or 30 days.
Application Name filters sessions to a specific application.
Violations by Severity narrows results by security impact
level. Security Profiles Applied shows sessions using particular
security configurations, and Cloud filters by provider.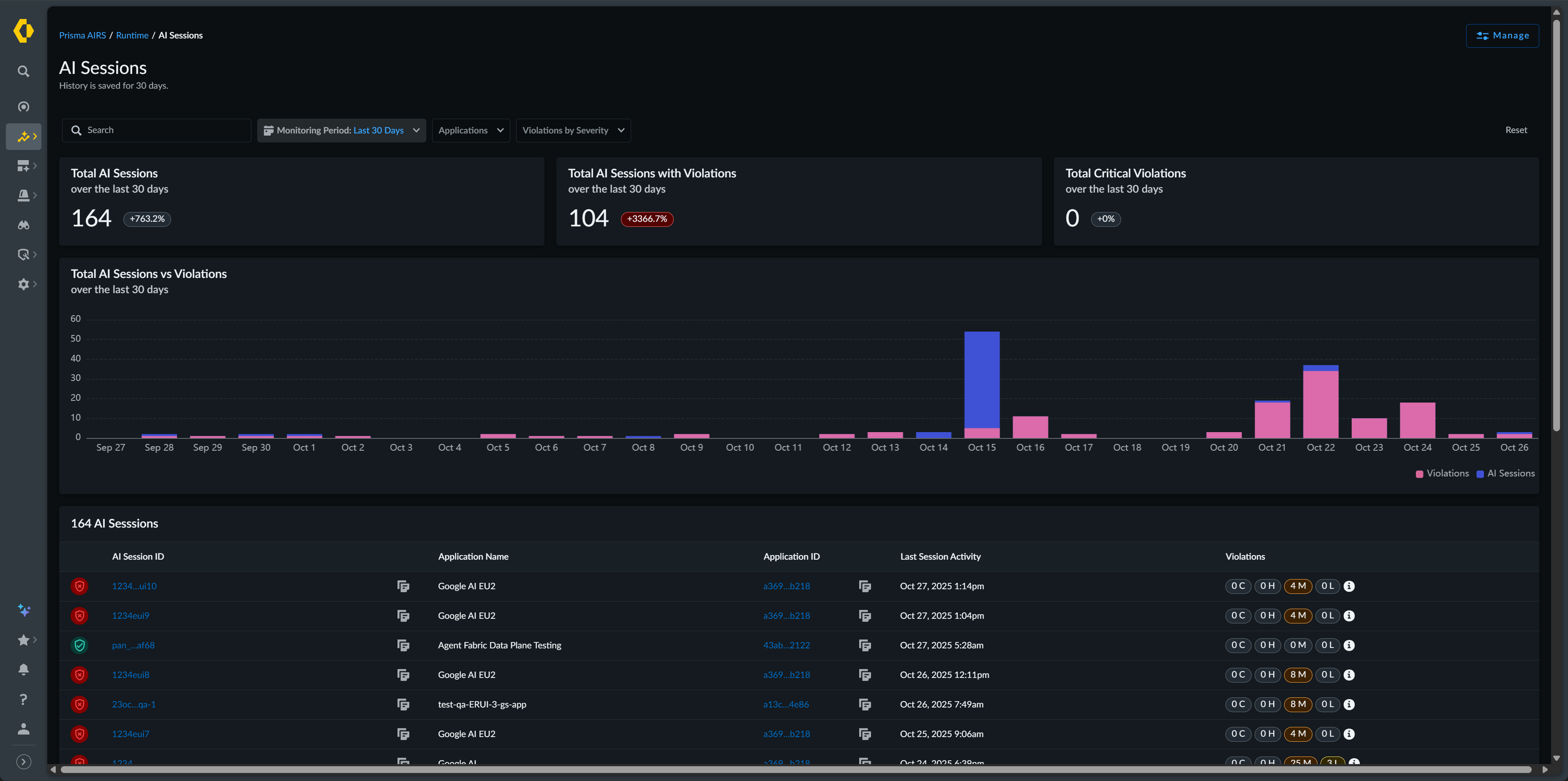
| Field Name | Description |
|---|---|
|
Total AI Sessions
|
The total number of AI sessions processed by Prisma AIRS during
the last 30 days
|
|
Total AI Sessions with Violations
|
The total number of AI sessions with violations identified during
the last 30 days
|
|
Total Critical Violations
|
The total number of AI sessions with critical violations
identified during the last 30 days
|
|
AI Session ID
|
Unique identifiers for the session
|
|
Application Name
|
The name of the application participating in the session
|
|
Tags
|
User-defined labels for organization
|
|
Last Session Activity
|
The date and time of the last activity of the session
|
|
Violations
|
The number of violations that occurred during the specified
session and the severity of each violation
|
You view additional details about each session by clicking on the
AI Session ID.
| Field Name | Description | |
|---|---|---|
|
AI Session Overview
| ||
|
AI Session ID
|
Unique identifier of the AI session
| |
|
Application Name
|
The name of the application associated with the session
| |
|
Application Tag(s)
|
User-defined tags applied to the application associated with the
session
| |
|
Cloud
|
The cloud service provider (AWS, Azure, GCP, or Other)) hosting
your application
| |
|
Source of Detection
|
Shows how the application was discovered
| |
|
Last Activity
|
The time and date of the last time activity was detected for the
session
| |
|
Start Time
|
The time and date the session began
| |
|
End Time
|
The time and date the session ended
| |
|
AI Session Transaction Details
| ||
|
Timestamp
|
The time of each transaction in the session
| |
|
Scan ID
|
A unique identifier of the scan
| |
|
Content Type
|
Indicates what the type of transaction occurred
| |
|
Security Breakdown
|
The number of violations per transaction and the severity of each
violation
| |
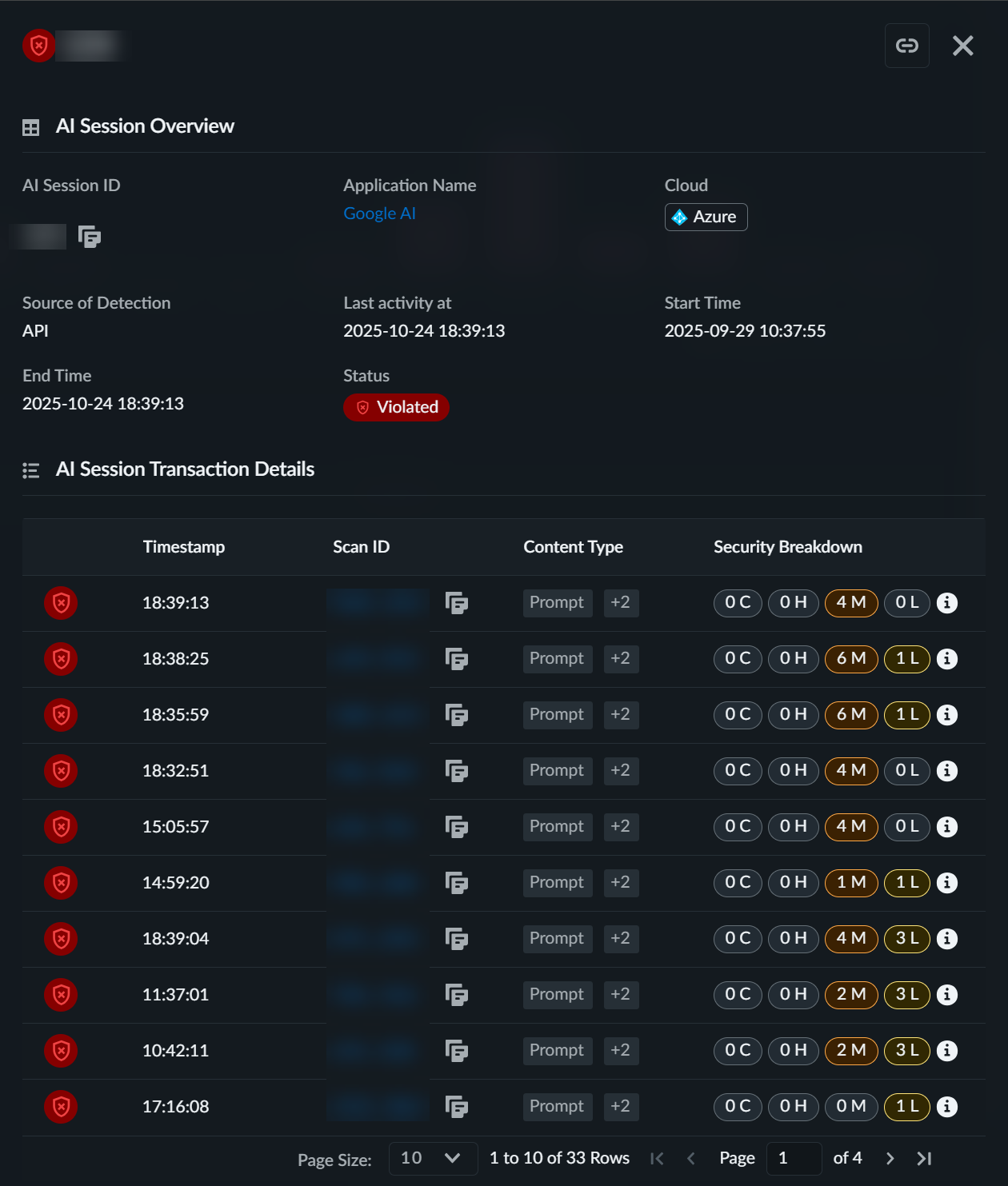
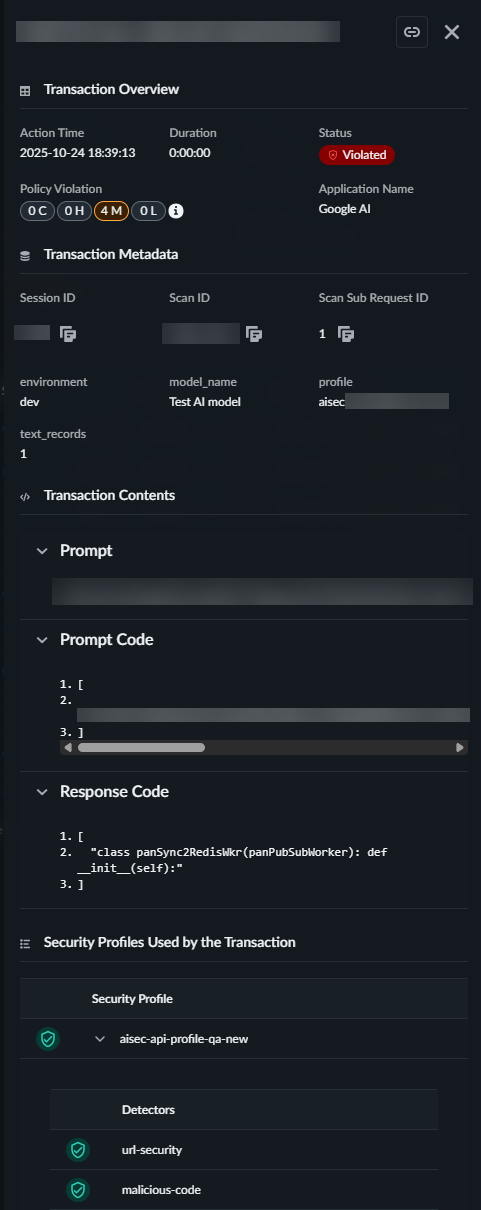
To gain further insight into the session, you can drill down to the transaction
that caused the security profile violation. This view provides the details of the
transaction including the prompt and response where the violation
occurred.
| Field Name | Description | |
|---|---|---|
|
Content Overview
| ||
|
Action Time
|
The time the transaction began
| |
|
Duration
|
The amount of time the transaction lasted
| |
|
Status
|
Displays the status of the transaction.
| |
|
Policy Violation
|
The number and severity of the violation(s)
| |
|
Application Name
| Name of the application that participated in the transaction | |
|
Transaction Metadata
| ||
|
Session ID
|
Unique identifier of the AI session
| |
| Scan ID |
A unique identifier of the scan
| |
|
Scan Sub Request ID
|
If the Scan API request is of the Async type, with multiple
requests sent in a batch, this identifier identifies each
request in the batch. Scan requests that are not batched have a
Scan Sub Request ID of zero (0).
| |
|
Environment
|
The cloud service provider (AWS, Azure, GCP, or Other) hosting
your application
| |
|
Model Name
| The AI model name sent in the API request metadata. | |
|
Environment
|
The cloud service provider (AWS, Azure, GCP, or Other) hosting
your application
| |
|
Profile
|
The security profiles applied to this session
| |
|
Transaction Content
| If the Content Type is Prompt |
The prompt and response of the transaction
|
| If the Content Type is Tool Event | The contents of the tool event request | |
|
Security Profiles Used by the Transaction
|
The security profiles applied to this session and on which
detector(s) the transaction failed
| |