Convert Internet Access Rules
Table of Contents
10.1
Expand all | Collapse all
Convert Internet Access Rules
Convert legacy port-based HTTP/HTTPS (port 80/443) internet
access rules to application-based rules.
An internet access rule controls traffic on
port 80 (HTTP) and port 443 (HTTPS). This rule usually sees the
largest number of applications and the greatest amount of traffic
in bytes. A port-based internet access rule may allow applications
you don’t want on your network and expose it to attacks. Control
and safely enable the applications you allow on those ports by converting
the port-based internet access rule to a set of application-based
rules. To do this, you need to understand which applications your
company sanctions for business use and which applications your company
tolerates for other purposes.
A good conversion method is
to group applications that require similar treatment in the same rule
instead of creating separate rules for each application to help
prevent rulebase bloat. Use Policy Optimizer to sort the applications
seen on a rule by application subcategory so you can see all the applications
on a rule for a particular subcategory, select the applications
your business uses, and then clone a rule to control those applications.
Policy Optimizer offers many sorting and filtering options to
organize and analyze applications seen on a rule.
Clone the
rule instead of directly converting it to ensure application availability.
Cloning a rule retains the original port-based rule and places the
cloned application-based rule directly above the port-based rule
in the Security rulebase. Create different internet access rules
from the original port-based rule for groups of applications you
want to treat differently, without risking application availability.
Easily see which applications match the cloned rule and which applications
filter through to the original port-based rule and then adjust the
rules as needed. When no applications you want to allow match the
port-based rule for a long enough period of time to be confident
that you’ve accounted for all the applications the business requires,
you can disable (or delete) the port-based rule, which finishes
the conversion without risking application availability.
Use
the same method to convert other rules that have seen more than
a few well-known applications. Use PoliciesSecurityPolicy OptimizerNo App Specified information
to help prioritize which rules to convert after you convert the
internet access rules. For example, you could prioritize based on
a combination of most Apps Seen and most
traffic over the last 30 days (Traffic (Bytes, 30 days))
to convert the most-used rules, or you could look at Days
with No New Apps and the Modified date
to find rules that have seen many applications but are also more
stable.
This example shows you how to clone an application-based
rule that controls general business applications from a port-based
internet access rule. Use the same cloning process to create application-based
rules safely for different subcatgories and individual applications
seen on any port-based rule.
- Navigate to PoliciesSecurityPolicy OptimizerNo App Specfied and find the
port-based rule(s) that control internet access. Use the filter (service/member eq ‘service-http’) and (service/member eq ‘service-https’) to find the port-based rule(s) configured with service-http and service-https, which is the internet access rule (or rules).
![]()
- Click Compare or the number of Apps Seen to open the Applications & Usage dialog.
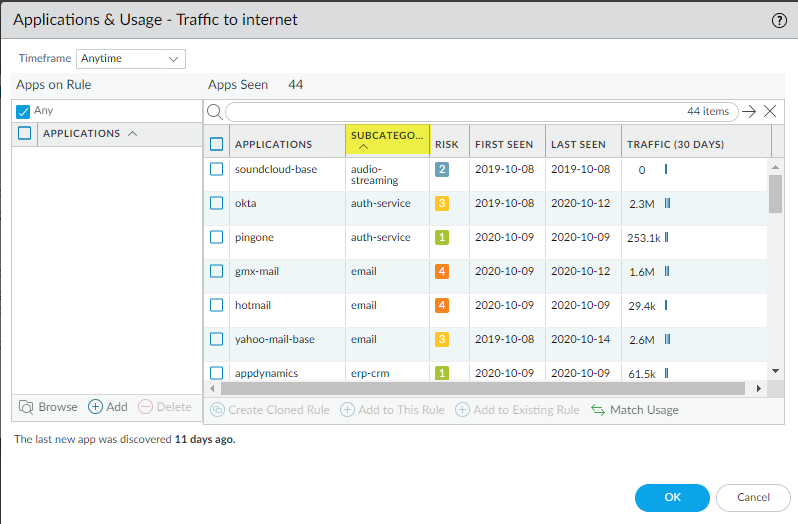
- Sort Apps Seen by application
subcategory to group similar applications that may be appropriate
to control in the same Security policy rule.Sort by Subcategory to group the applications seen on the rule:
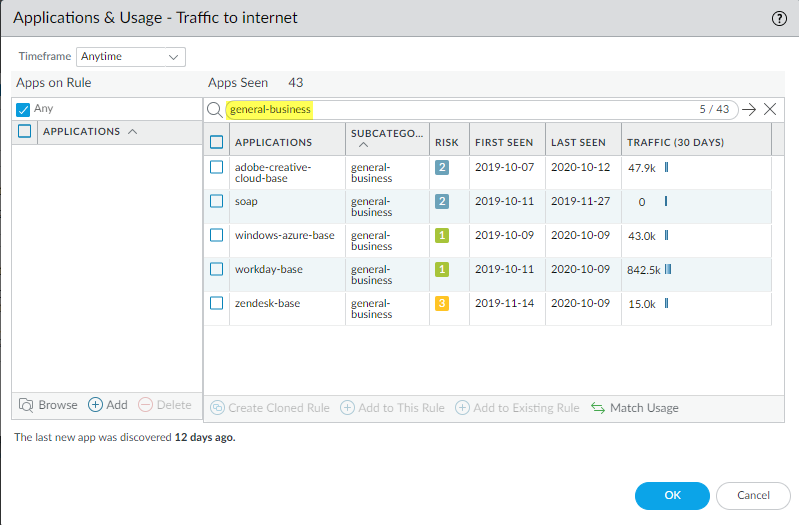
![]() You can also filter by a particular subcategory to see only the applications that belong to that subcategory. In this example, to create an App-ID based rule to control general-business applications, filter to view only the general business applications seen on the rule:
You can also filter by a particular subcategory to see only the applications that belong to that subcategory. In this example, to create an App-ID based rule to control general-business applications, filter to view only the general business applications seen on the rule:![]()
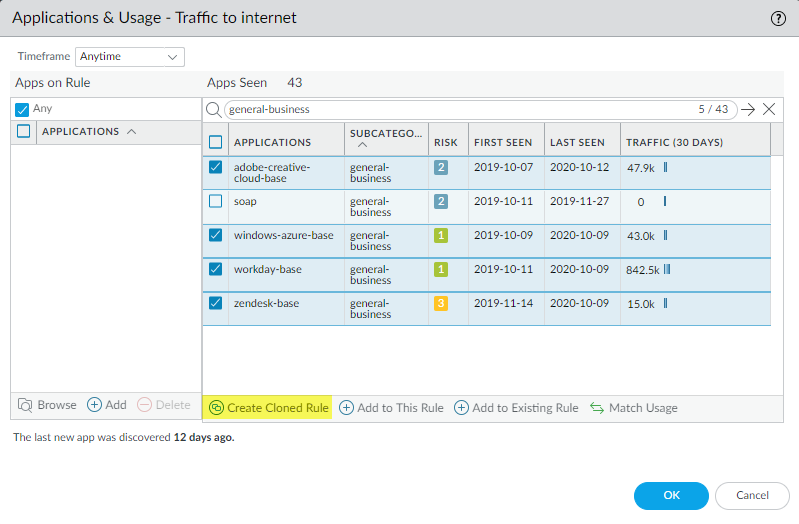
- Select
the applications you want to allow and then Create Cloned Rule to
clone the new application-based rule from the port-based rule.In this example, the company uses four of the applications but has not used one of the applications for a long period of time, which you can see in the Last Seen and Traffic (30 Days) columns. Based on usage and company-sanctioned applications, the company chooses not to allow the application that it isn’t using.
![]()
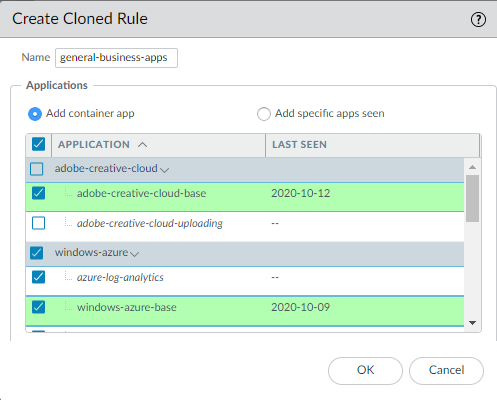
- In the Clone dialog, select the
applications associated with each container app that you want to
allow.Give the new rule a Name that describes its purpose—in this example, general-business-apps. Decide if you want to allow only specific applications from each container app or if you want to allow the container app. Allowing the container app allows all of the applications in the container. This future-proofs the rule by automatically allowing new applications if they are added to the container app, which helps ensure application availability. By default, all of the applications are selected. The container apps are shaded gray, applications that have been seen on the rule are shaded green, and applications in the container app that haven’t been seen on the rule are italicized and not shaded.In this example’s illustration, you can see the gray-shaded container apps “adobe-creative-cloud” and “windows-azure”, applications seen on the rule in green (“adobe-creative-cloud-base” and “windows-azure-base”), and two applications that have not been seen on the rule in italics (“adobe-creative-cloud-uploading” and “azure-log-analytics”). The example shows that the application “adobe-creative-cloud-uploading” is deselected, which also automatically deselects its container app (“adobe-creative-cloud”) while all of the “windows-azure” applications remain selected, so the “windows-azure” container app remains selected.
![]() Deselect an application if you don’t want users to have access to that particular application. However, if new applications are added to the “adobe-creative-cloud” container app, the firewall will not automatically allow them because the container app is deselected. Conversely, if new applications are added to the “windows-azure” container app, the firewall will automatically allow them, which future-proofs the rule.
Deselect an application if you don’t want users to have access to that particular application. However, if new applications are added to the “adobe-creative-cloud” container app, the firewall will not automatically allow them because the container app is deselected. Conversely, if new applications are added to the “windows-azure” container app, the firewall will automatically allow them, which future-proofs the rule. - Click OK to return to the Security
policy rule Usage tab and then click OK again
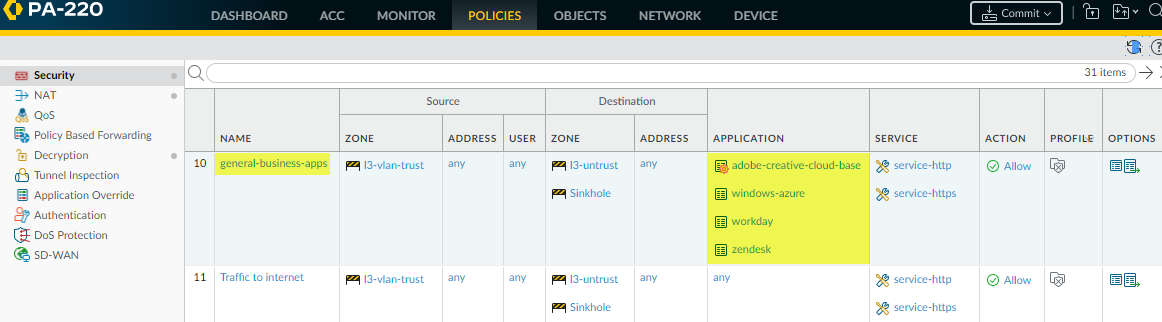
to create the rule. The firewall places the rule above the port-based
rule in the Security policy rulebase (PoliciesSecurity).
![]() If you select a container app, Policy Optimizer adds only the container app to the rule because the container app includes all of the applications. The red gear for “adobe-creative-cloud-base” indicates that it is an individual application, not a container app.
If you select a container app, Policy Optimizer adds only the container app to the rule because the container app includes all of the applications. The red gear for “adobe-creative-cloud-base” indicates that it is an individual application, not a container app. - Click the rule Name or a Service and change the Service to application-default to prevent evasive applications from gaining access on a non-standard port.
- Whenever you need to allow other sanctioned general business applications, add them to the general-business-apps rule, and remove applications from the rule if you no longer use them.