Create the Data Center Best Practice File Blocking Profile
Table of Contents
10.1
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
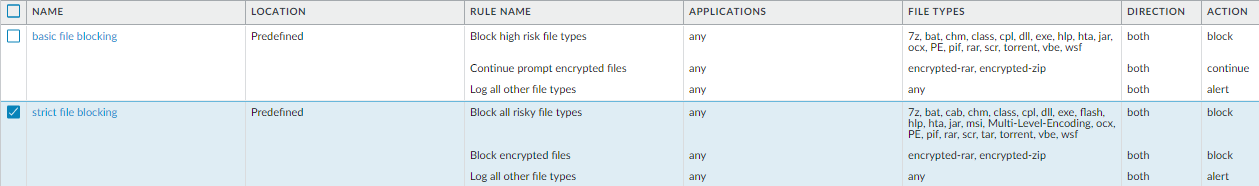
Create the Data Center Best Practice File Blocking Profile
Protect you data center from file types that you don’t
use and that don’t belong there.
Use the predefined strict File Blocking profile to block files that
are commonly included in malware attack campaigns and that have
no real use case for upload/download. Blocking these files reduces
the attack surface. The predefined strict profile blocks batch files,
DLLs, Java class files, help files, Windows shortcuts (.lnk), BitTorrent
files, .rar files, .tar files, encrypted-rar and encrypted-zip files,
multi-level encoded files (files encoded or compressed up to four
times), .hta files, and Windows Portable Executable (PE) files,
which include .exe, .cpl, .dll, .ocx, .sys, .scr, .drv, .efi, .fon,
and .pif files. The predefined strict profile alerts on all other
file types for visibility into other file transfers so that you
can determine if you need to make policy changes.
In some cases, the need to support critical applications may prevent you from blocking all of the
strict profile’s file types. Follow the safe transition advice to help determine
whether you need to make exceptions in different areas of the network. Review the
data filtering logs (MonitorLogsData Filtering) to identify file types used in the data center and talk with
business stakeholders about the file types their applications require. Based on this
information, if necessary, clone the strict profile and modify it as needed to allow
only the other file type(s) that you need to support the critical applications. You
can also use the Direction setting to restrict files types from flowing in both
directions or block files in one direction but not in the other direction.
The reason to attach the best practice File Blocking profile
to all security policy rules that allow traffic is to help prevent attackers
from delivering malicious files to the data center through file
sharing applications and exploit kits, or by infecting users who
access the data center, or on USB sticks.
- Traffic from users to the data center—Attach the strict File Blocking profile to security policy rules for applications that don’t entail file sharing or collaboration to block dangerous file types that can deliver exploits and malware.
- Intra data center traffic—Attach the strict File Blocking profile to security policy rules to prevent a compromised server from sharing a malicious file with other servers in the data center. This isolates the infection and prevents the spread of malware through the data center.
- Traffic from the data center to the internet—Limit file transfers to the file types required by the application in use.
If you don’t block all Windows PE files, send all unknown files
to WildFire for analysis. For user accounts, set the Action to continue to
help prevent drive-by downloads where malicious web sites, emails,
or pop-ups cause users to inadvertently download malicious files.
Educate users that a continue prompt for a file transfer they didn’t
knowingly initiate may mean they are subject to a malicious download.
