Cloud NGFW for AWS
Cloud NGFW on AWS WildFire Protection
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Cloud NGFW on AWS WildFire Protection
Configure a WildFire Analysis profile on Panorama to detect and forward threats to
WildFire.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Cloud NGFW can now detect and forward files, executables,
and malicious scripts (such as JScript and PowerShell) in your VPC traffic to
WildFire™ cloud service for analysis. WildFire then applies threat intelligence,
analytics, and correlations on these forwarded files (executables or scripts) and
delivers verdicts based on the analysis. If a threat is detected on them, WildFire
creates protections to block malware, and globally distribute these protection for
that threat in a few minutes.
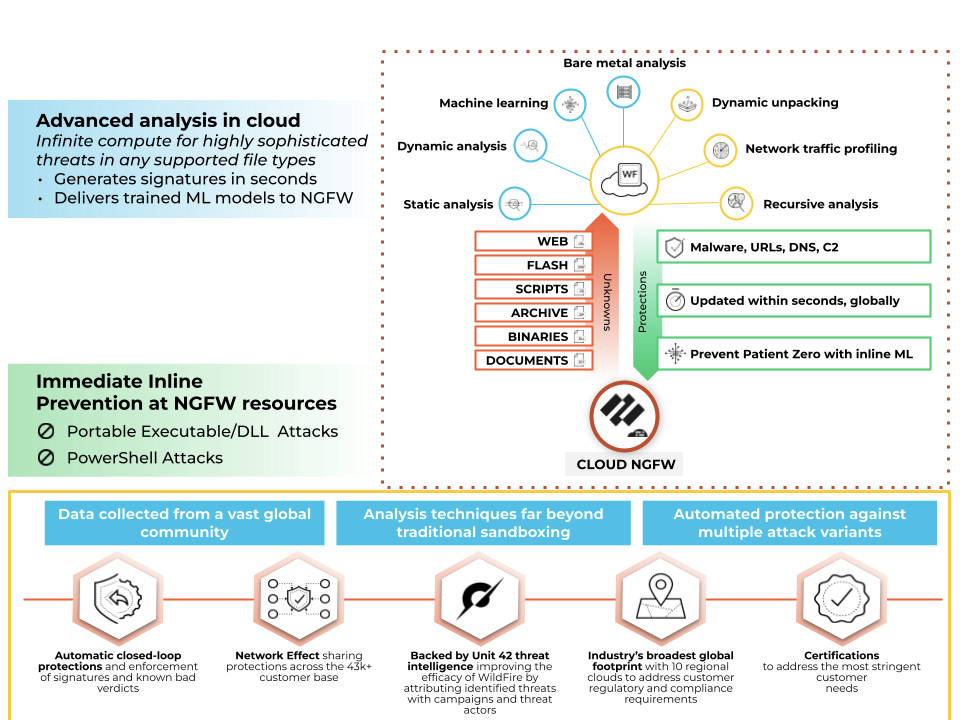
WildFire goes beyond traditional sandboxing approaches and uses multiple techniques
to identify files with potential malicious behaviors. These techniques include:
- Dynamic analysis - observes files as they execute in a purpose-built, evasion-resistant virtual environment, enabling detection of previously unknown malware using hundreds of behavioral characteristics.
- Static analysis - complements dynamic analysis with effective detection of malware, providing instant identification of malware variants. Static analysis further leverages dynamic unpacking to analyze threats attempting to evade detection through the use of packing tool sets.
- Network traffic profiles - detect malicious traffic patterns based on malware variants such as backdoor creation, download of next-stage malware, access to low-reputation domains, and network reconnaissance.
- Machine learning - extracts thousands of unique features from each file, training a predictive machine learning model to identify new malware, which isn't possible with static or dynamic analysis alone.
- A custom-built hypervisor - prevents attacker evasion techniques with a robust, proprietary hypervisor that does not depend on open-source projects or proprietary software to which attackers have access.
To configure WildFire on your Cloud NGFW AWS resource, you will need to:
Configure a WildFire Profile
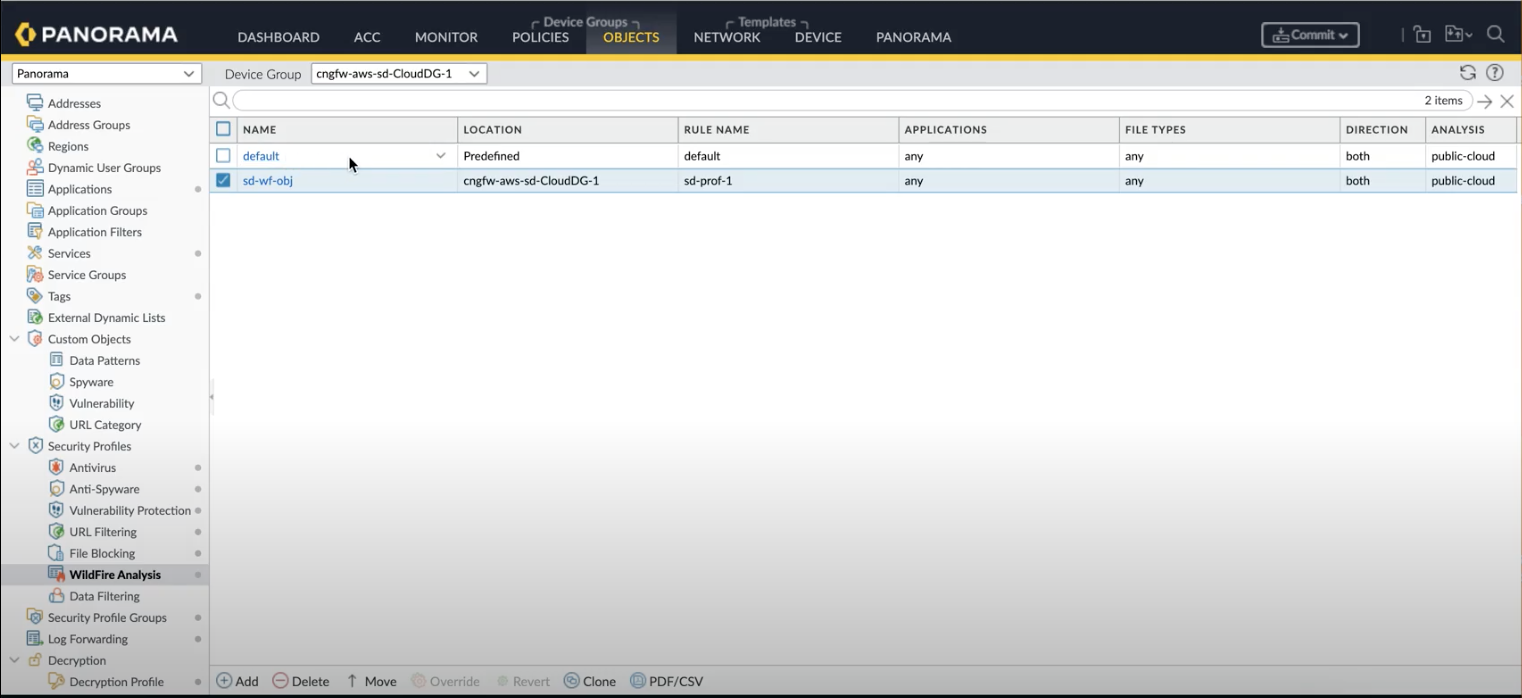
- Login to Panorama and click Objects > WildFire Analysis. The WildFire Analysis profile window appears.Select the device group from the drop-down menu where you want to create the profile.
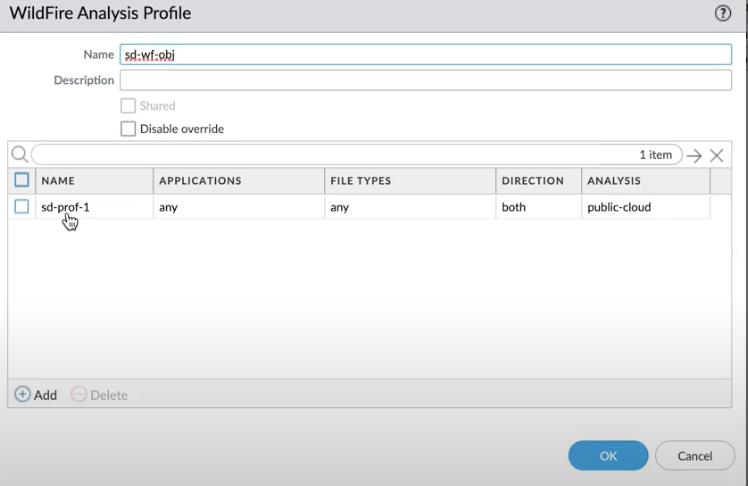
![]() Click Add.Enter a Name for the WildFire profile and click Add.Enter a descriptive Name for any rules you add to the profile.In the application section, click Add to select the application from the list of applications that you wish to allow access through your WildFire profile.Click FileTypes to select the file types you wish to allow.Click Direction to allow download or upload or both options.
Click Add.Enter a Name for the WildFire profile and click Add.Enter a descriptive Name for any rules you add to the profile.In the application section, click Add to select the application from the list of applications that you wish to allow access through your WildFire profile.Click FileTypes to select the file types you wish to allow.Click Direction to allow download or upload or both options.![]() Select the Destination for traffic to be forwarded for analysis: Select public cloud if you wish that all traffic matched to the rule is forwarded to the WildFire public cloud for analysis.Select private cloud if you wish that all traffic matched to the rule is forwarded to the WildFire appliance for analysis.Click OK.
Select the Destination for traffic to be forwarded for analysis: Select public cloud if you wish that all traffic matched to the rule is forwarded to the WildFire public cloud for analysis.Select private cloud if you wish that all traffic matched to the rule is forwarded to the WildFire appliance for analysis.Click OK.Define Security Rules
- Log in to Panorama, and click policy rules.Choose the required Device Group and click the preconfigured security rule (pre-rule or post-rule) or create a new rule.Click Actions.In the profile setting, select Profiles under the profile type.Select the WildFire profile you wish to choose in the WildFire Analysis drop-down.Click OK.Commit and push the device group to the Cloud NGFW resources.For more information, see Latest WildFire Cloud Features.
View WildFire Submission Logs
You can view WildFire submission logs in:View Logs in AWS Destinations
If you have previously configured Amazon Cloudwatch, Amazon S3 or Amazon Kinesis as your log destination you can review them for blocks of malicious traffic by WildFire.![]()
![]()
View Logs in Panorama
On Panorama, you can view the logs on the device group using Monitor > Threats.![]()
View Logs in Strata Logging Service
You can also view WildFire logs in your Strata Logging Service instance.- Click Explore and select Firewall/Threat from the explore drop-down.
- Enter sub_typevalue = wildfire or wildfire-virus and filter for WildFire logs.
![]()