CN-Series
Configure the Kubernetes Plugin for Panorama
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
-
-
- Deployment Modes
- In-Cloud and On-Prem
-
-
-
Configure the Kubernetes Plugin for Panorama
Use the Kubernetes Plugin for Panorama to propagate labels
to Panorama device groups
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Use the Kubernetes Plugin for Panorama to propagate labels to Panorama
device groups.
You can use the Kubernetes plugin to complete the integration of Panorama
and the Kubernetes API. The plugin learns new labels and propagates them to Panorama
device groups. These labels can include Kubernetes labels, services, namespaces, and
other metadata from which Dynamic Address Group match criteria can be defined.
If the cluster credential file size is greater than 32KB, you will
get an error message when importing the credentials file on the Panorama
Kubernetes plugin. The error message displays the size of the file as the
cause of the error.
If the cluster has many CA certificates in ca.crt
bundle, the Kubernetes plugin only requires the top CA certificate. You must
ensure to retain only the top CA certificate and remove all other CA
certificates and service.crt from the credential file. You
can then use this updated credential file.
This procedure assumes you have installed the supporting software listed in Prepare to Use the Helm Charts and Templates.
- Retrieve the pan-plugin-user service account credentials from the Kubernetes master.Enter each command as a single line:$ MY_TOKEN=`kubectl get serviceaccounts pan-plugin-user -n kube-system-o jsonpath='{.secrets[0].name}'`$ kubectl get secret $MY_TOKEN -n kube-system -o json >~/Downloads/pan-plugin-user.jsonCreate a Cluster definition in the Panorama Kubernetes plugin.Use the Kubernetes master address displayed in the Terraform output and the JSON credentials file located at ~/Downloads/pan-plugin-user.json.Define the labels you want to import from the Kubernetes API.Create a Notify Group definition in the Panorama Kubernetes plugin.This definition is used to propagate the labels learned from the Kubernetes API to a Panorama Device Group.Perform the following steps to create a Notify Group in the Panorama Kubernetes plugin:
- Select Panorama > Plugins > Kubernetes >
Setup > Notify Groups, and Add.
![]()
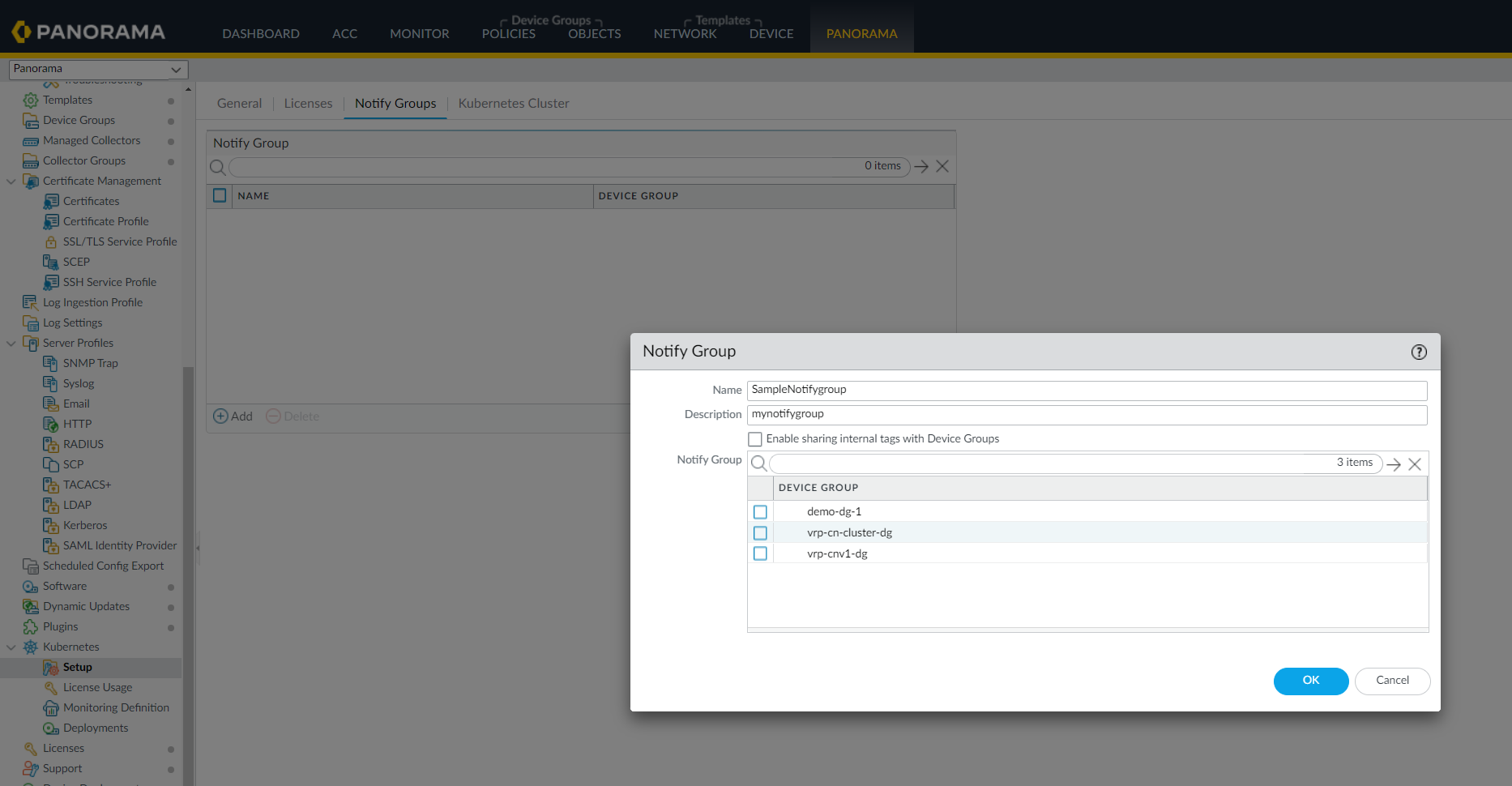
- Enter a Name of up to 31 characters for the notify group.
- Select Enable sharing internal tags with Device Groups if you want to share internal tags in addition to the external tags (default) created for the cluster.
- Select the device groups to wich you want to register the
tags.
![]()
- Click Ok.
Create a Monitoring Definition in the Panorama plugin.Use the Cluster and Notify Group definitions created in the previous steps.Commit to Panorama.To confirm API connectivity and MP container registrations, go to the Monitoring Definition and click on the Detailed Status and Cluster MPs.You are now ready to deploy an application and secure it with the CN-Series firewall.![]()