Prisma AIRS
Defend: Create a Security Policy Rule to Prevent AI Security Threats
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Defend: Create a Security Policy Rule to Prevent AI Security Threats
Prevent AI security threats by creating and enforcing security policy
rules.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
On this page, you will create an AI security profile with specific asset protections and add it to a
security profile group. Next, create a security policy rule and attach the profile
group to it. Push the security configurations for the security rule from Strata Cloud Manager or Panorama to Prisma AIRS AI
Runtime: Network intercept in your cloud.
The Prisma AIRS AI Runtime: Network intercept deployed in your
cloud environment gives you continuous real-time discovery and monitoring of your
cloud resources. After you identify the malicious threats in your AI network traffic
and correlate these with the cloud assets, such as AI applications, AI models, and
AI datasets, you can then prevent threats by creating policy rules between the cloud
resources. The AI security policy rule can be created and configured in Strata Cloud Manager or Panorama.
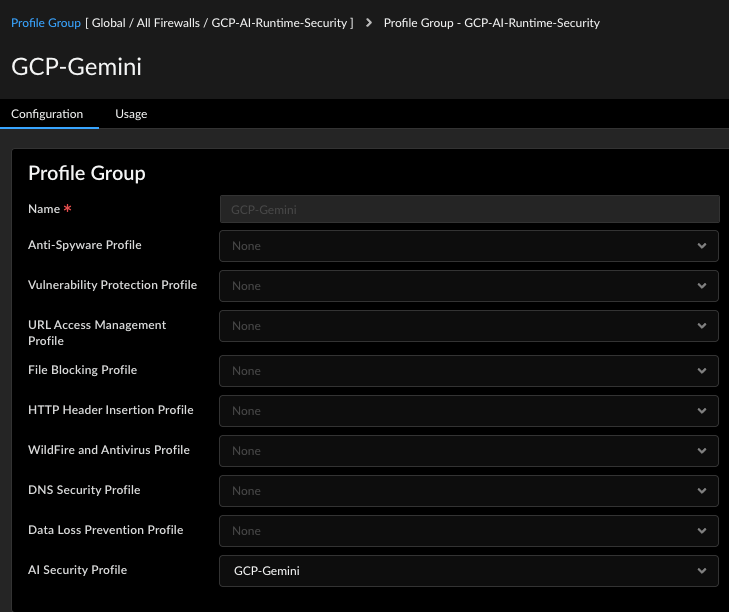
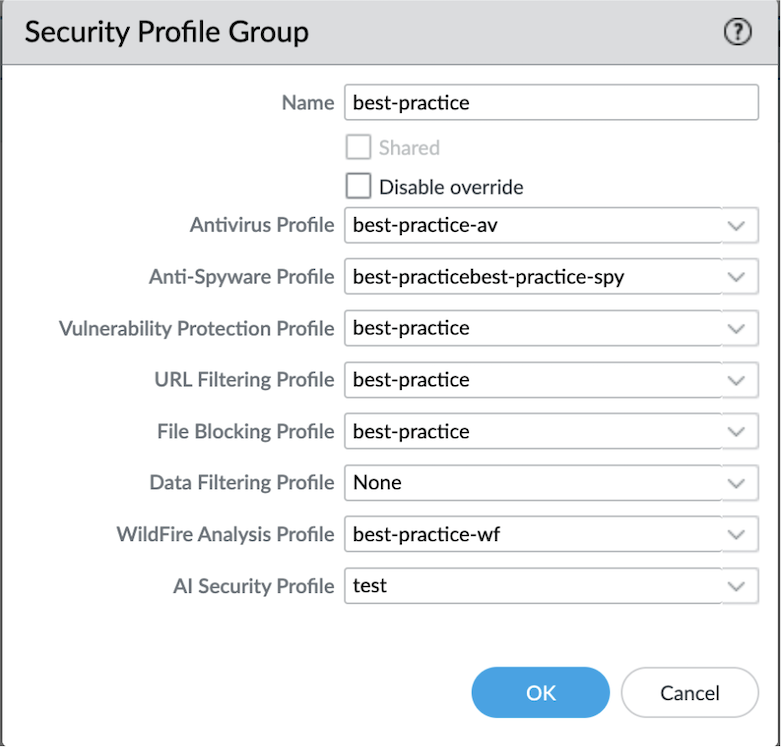
- Log in to Strata Cloud Manager or Panorama.Create an AI Security Profile.Create Security Profile Groups and attach the AI Security profile to each profile group.
![]()
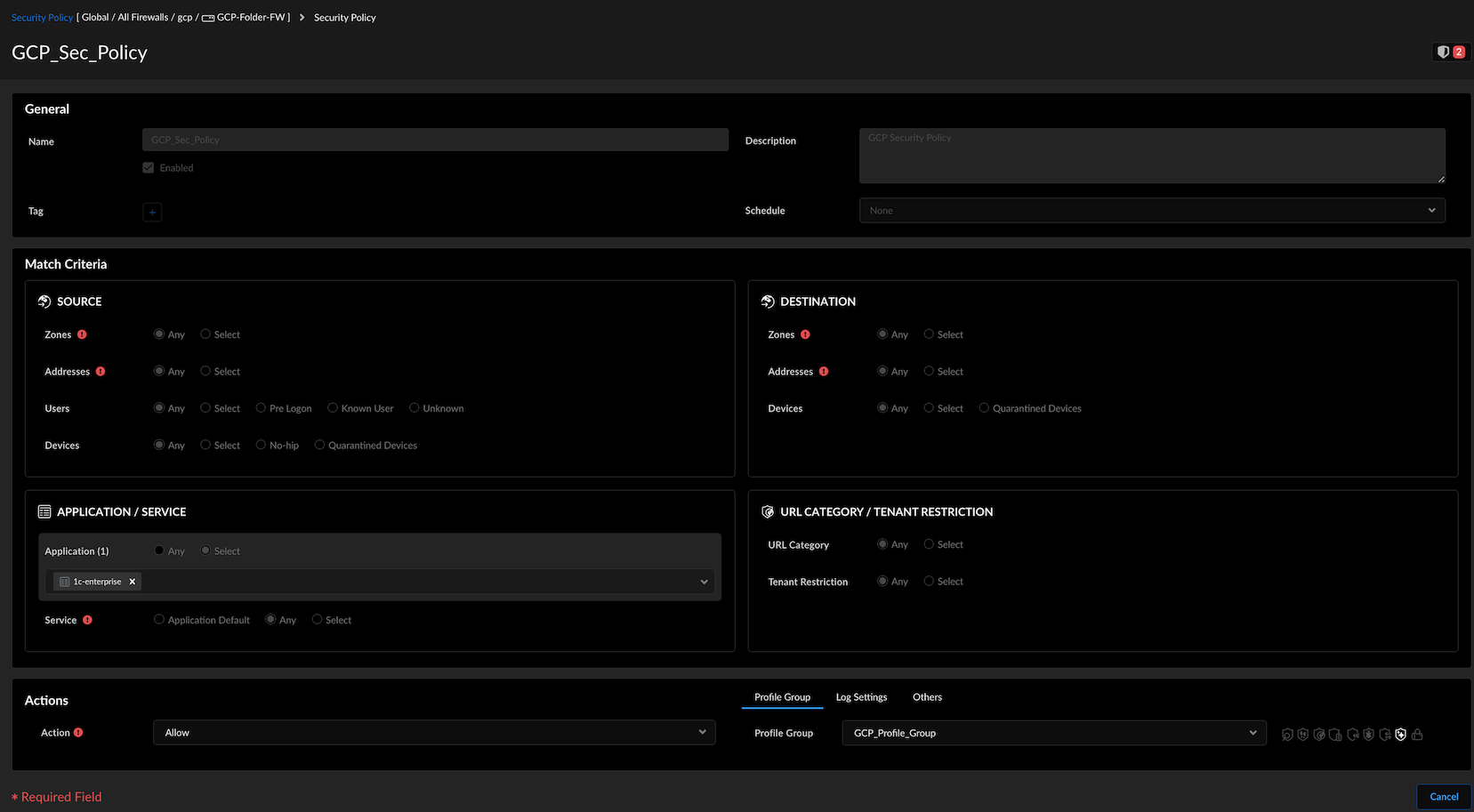
![]() Create a security policy rule in Strata Cloud Manager or Panorama.Attach the security profile group to the security policy under Profile Group.
Create a security policy rule in Strata Cloud Manager or Panorama.Attach the security profile group to the security policy under Profile Group.![]() Navigate to Manage→ Configuration → Operations → Push Config in Strata Cloud Manager or Commit → Commit and Push in Panorama.This pushes the policy configurations to Prisma AIRS AI Runtime: Network intercept to enforce the policy rules on the traffic.Navigate to Log Viewer.
Navigate to Manage→ Configuration → Operations → Push Config in Strata Cloud Manager or Commit → Commit and Push in Panorama.This pushes the policy configurations to Prisma AIRS AI Runtime: Network intercept to enforce the policy rules on the traffic.Navigate to Log Viewer.- Select Firewall/AI Security.
- Review the AI Security Log Viewer to see traffic blocked according to your AI Security profile.
For information on log fields, see the Strata Logging Service Log Reference Guide.