Cloud NGFW for AWS
Cloud NGFW for AWS Rule Usage
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Cloud NGFW for AWS Rule Usage
Learn how Panorama uses rules on your Cloud NGFW resource.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Use Panorama to manage rules on your Cloud NGFW resource to track and monitor rule
usage for operations and troubleshooting tasks. On your Panorama console, you can
view the rule usage at cloud device group to determine if all, some, or none of the
Cloud NGFW resources have traffic matches.
On Panorama, you can view the rule usage details for managed firewalls that have
policy rule hit count enabled (default), and for which you have defined and pushed
policy rules using device groups. Panorama cannot retrieve rule usage details for
policy rules configured locally on the firewall so you must log in to the firewall
to view rule usage information for locally configured rules. For more information,
see Monitor Policy Rule Usage.
Rule Usage - Rule Hit and Policy Optimizer
System Requirements
The following are the minimum system requirements to monitor your security policy
rule usage:
- Panorama (PAN-OS) version 10.2.8 and above
- AWS Plugin version 5.2.0 and above
- Cloud Services Plugin version 5.0.0 and above
- Cloud Connector Plugin version 2.0.1 and above
View the Rule Hit Count for a Cloud Device Group
In the Panorama console, after you associate a cloud device group
to a Cloud NGFW resource and configure policies for the cloud device group,
perform the following steps to view the rule hit count for a cloud device
group in Panorama:
The NGFW firewall resources report your rulehit data
for every 2 minutes to the Cloud NGFW service, and then the cloud NGFW
service will have a latency of maximum 2 minute to poll data from firewall
resources. This will create a maximum of 4 minute latency in rule hit count
data display on the Panorama console.
- Select Policies.In the Device Group section, use the drop-down to select the Cloud Device Group.Select a Rule, and click Rule Usage.You can monitor the rule usage status of your Pre, Post, and Default rules of Security, Decryption, and Application-override policy types.
![]() You can now see the Hit Count of the selected rule.
You can now see the Hit Count of the selected rule.![]() In the Panorama console, the rule hit count gets refreshed for every 4-minute interval, by default.Click Reset Rule Hit Counter to refresh the hit count of the selected rule.Click PDF/CSV to export the Rule usage details of a selected rule as a CSV or PDF file.
In the Panorama console, the rule hit count gets refreshed for every 4-minute interval, by default.Click Reset Rule Hit Counter to refresh the hit count of the selected rule.Click PDF/CSV to export the Rule usage details of a selected rule as a CSV or PDF file.![]()
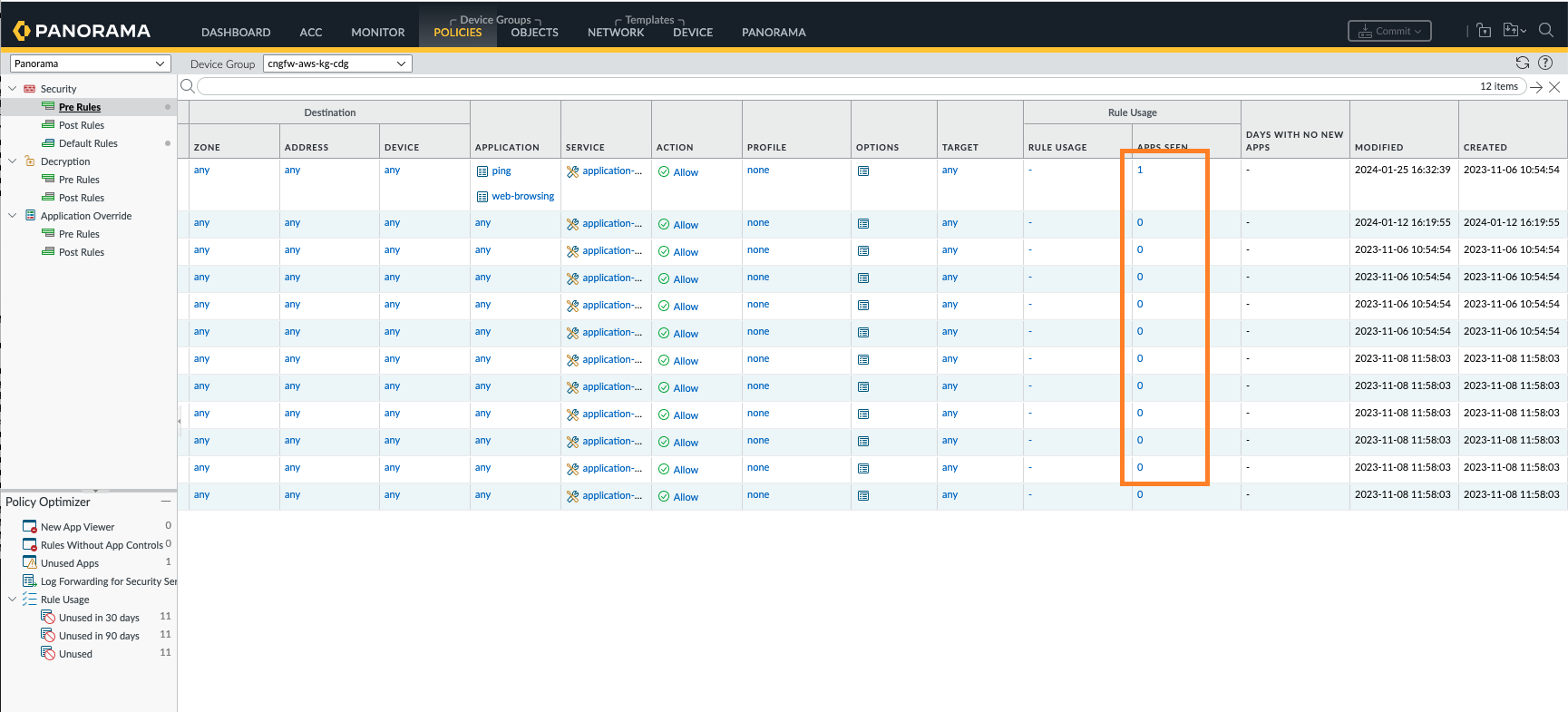
Rule Usage - App Seen and Policy Optimizer
You can view all your applications seen and allowed on the firewall
that match with your security policy rule. The number in Apps
Seen column indicates how many applications were seen on the
rule.
- In the Panorama console, go to the Policies tab.
- In the Device Group section, use the drop-down to select the Cloud Device Group.
- Select a Rule, and click Apps seen.
![]() You can now see the applications configured and displayed on your security policy rule.
You can now see the applications configured and displayed on your security policy rule.
For more information on Apps on Rule, Apps seen, and App seen actions,
see Applications and Usage.
In the Policy Optimizer section, you can also view the
rule hit count for all your configured cloud device groups on Panorama. Policy
Optimizer provides a simple workflow to migrate your legacy Security policy
rulebase to an App-ID based rulebase, which improves your security by reducing
the attack surface and gaining visibility into applications so you can safely
enable them. For more information, see Security Policy Rule Optimization and
Applications and Usage.