Next-Generation Firewall
Add Applications to an Existing Rule
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Add Applications to an Existing Rule
Use Policy Optimizer to add apps seen on a port-based
Security policy rule to an existing application-based rule.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
This is a core Network Security feature for NGFWs and Prisma
Access; no prerequisites needed.
|
In some cases, you may want to add applications
learned (seen) on a port-based rule to a rule that already exists.
For example, an administrator may create a cloned application-based
rule for general business web applications from a port-based rule
that allows internet access (a port 80/443 rule). Later, the administrator
notices that the port-based internet access rule has seen more general
business applications and wants to add some or all of them to the
cloned application-based rule (cloning another application-based
rule for the same type of application would create an unnecessary
rule and complicate the rulebase).
This example assumes that
an application-based Security policy rule to control general business
traffic already exists or was cloned from a port-based internet
access rule, similarly to the Rule Cloning Migration Use Case: Web Browsing and SSL Traffic. In that example,
we cloned an application-based rule from the port-based internet
access rule and changed the new rule’s Service to application-default
to prevent web-based applications from using non-standard ports.
In
addition to adding applications to an existing application-based
rule, you can add applications to an existing port-based rule. This converts
the port-based rule to an application-based rule for the applications
you add to the rule. If you do this, go to the rule and change the
Service to application-default to prevent the applications from
using non-standard ports (also, the Service configured on the rule
may not match the application).
This example
does not apply to using the New App Viewer to add
App-ID Cloud Engine (ACE) applications to an existing rule (see
the ACE documentation for
examples of how to do this); ACE requires a SaaS Security Inline license.
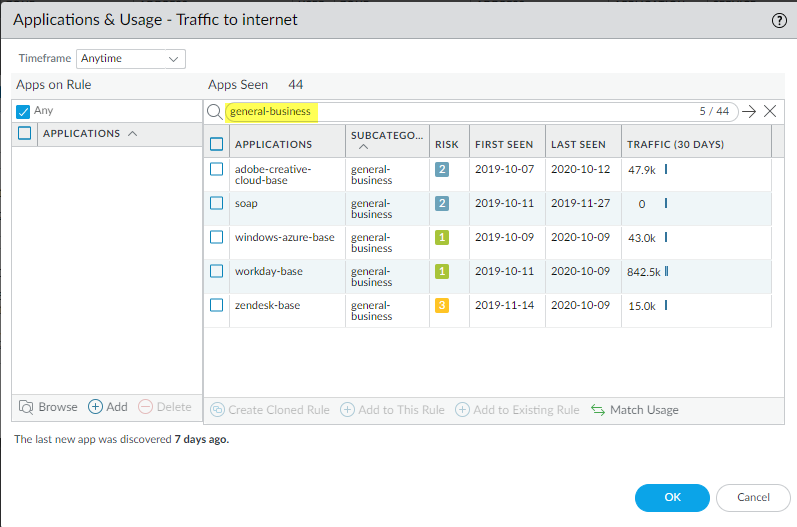
- You check the port-based internet access rule and discover that the rule has seen general business applications and that you need to allow some of them for business purposes.
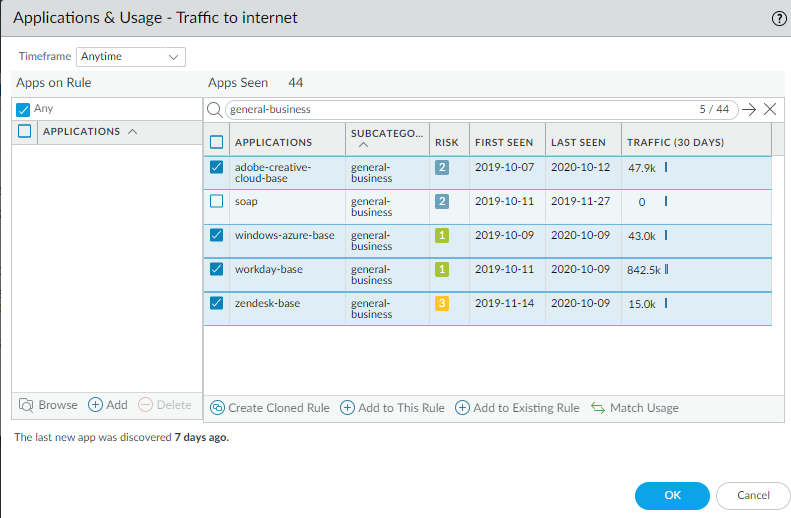
![]() Select the general business apps you want to add to the existing rule.
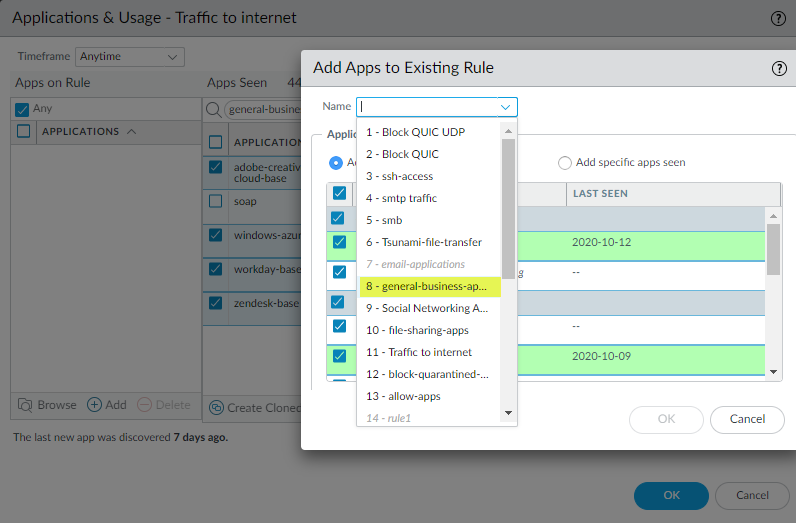
Select the general business apps you want to add to the existing rule.![]() Click Add to Existing Rule and select the Name of the rule to which you want to add the applications, in this example, general-business-applications.
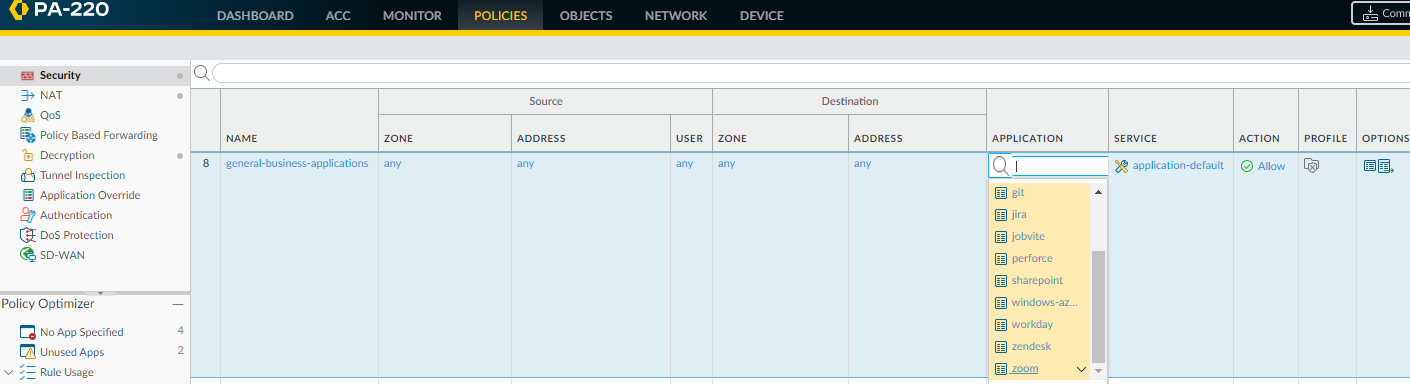
Click Add to Existing Rule and select the Name of the rule to which you want to add the applications, in this example, general-business-applications.![]() Click OK in Add Apps to Existing Ruleto add the selected applications to the general-business-applications rule.Click OK in Applications & Usage.The updated rule now controls the original applications on the rule and the applications you just added.
Click OK in Add Apps to Existing Ruleto add the selected applications to the general-business-applications rule.Click OK in Applications & Usage.The updated rule now controls the original applications on the rule and the applications you just added.![]()