Next-Generation Firewall
Update NGFWs Managed by Strata Cloud Manager
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Update NGFWs Managed by Strata Cloud Manager
Procedure for updating NGFWs managed by Strata Cloud Manager.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Group and schedule PAN-OS software and dynamic content updates for your
firewalls:
- Create a software update grouping rule so you can group sets of firewalls and schedule PAN-OS software upgrades for sets of firewalls. A firewall can only be associated with a single software update grouping rule. When you create a new software update grouping rule, only firewalls not already associated with an existing software update grouping rule are displayed as Target Devices.
- To ensure that you’re always protected from the latest threats, including those that haven’t yet been discovered, you must ensure that you keep your firewalls up to date with the latest content and software updates published by Palo Alto Networks.To install the latest Antivirus, Applications and Threats, and WildFire dynamic content updates on your firewalls, you can schedule a recurring update schedule to specify which dynamic content update to install. A Dynamic Update schedule can be configured at the snippet, folder, or firewall level. A Dynamic Update schedule created at the folder level is inherited by all nested folders and associated firewalls but can be modified for the nested folder or individual firewall.
- Schedule a PAN-OS software update to upgrade or downgrade your firewalls to a target PAN-OS version at a date and time of your choosing. Firewalls require an outbound internet connection in order to successfully download and install the PAN-OS software version from the Palo Alto Networks Update Server configured by default on the firewall. A software update schedule is a one time event to schedule updates to a specific PAN-OS version and aren’t reoccurring.
Create a Software Update Grouping Rule
- Log in to Strata Cloud Manager.Select ConfigurationNGFW and Prisma AccessSetup, set the Configuration Scope to All Firewalls, select Software UpdateSoftware Update Grouping Rules, and Add Software Upgrade Grouping Rule.Configure the General settings for software update grouping rule.
- Enter a Name.(Optional) Enter a Description for the software update grouping rule.Specify the Position of the update upgrade grouping rule.You can select Before or After an existing software update grouping rule. The position of the software update grouping rule determines which firewalls are Target Devices.Based on the rule position and Match Criteria, firewalls aren’t displayed as Target Devices if they’re already associated with a rule positioned before the rule you’re creating.Configure the Match Criteria to filter and specify target firewalls associated with the software update grouping rule.
- Specify the Folders the firewalls you want to target are associated with.
- Any (default)—Include all folders and the associated firewalls.
- Match—Select one or more folder names to match and include in the filtered target firewalls.
- Exclude (Negate)—Select one or more folder names to match and exclude from the filtered target firewalls.
Specify the firewall Models you want to target.All supported NGFW models are listed and not just the firewall models associated with the filtered Folders.- Any (default)—Include all firewall models.
- Match—Select one or more firewall models to match and include in the filtered target firewalls.
- Exclude (Negate)—Select one or more firewall models to match and exclude from the filtered target firewalls.
Specify one or more firewall Label you want to target.If you specify multiple labels, use the And, Or, and Not operators to further filter the target firewalls.(Optional) Exclude Devices from the list of Target Devices.Review the list of Target Devices to confirm all the firewalls you want to include in the software update grouping rule are included.If not all the firewalls you want to include are listed, go back and modify the Match Criteria until all the firewalls you want included are listed as Target Devices.Save.Schedule Dynamic Content Updates
- Log in to Strata Cloud Manager.Select ConfigurationNGFW and Prisma Access Device Setup and set the Configuration Scope to the NGFW or firewall folder where you want to create the Dynamic Updates schedule.You can select a folder or firewall from your Folders or select Snippets to configure the Dynamic Update schedule in a snippet.Click the cog wheel to edit the Dynamic Update Scheduler and Customize.If you modified the Dynamic Updates Scheduler for a nested folder or individual device, you can Revert to Inherited to revert the Dynamic Updates Scheduler configuration from the Customized configuration to that inherited from the parent folder of the nester folder or that inherited from the folder the firewall is associated with.Configure the Antivirus and Application and Threats dynamic content update schedule.
- Configure the Recurrence the firewall checks for Antivirus and Application and Threats dynamic content updates.
- None—No new dynamic content updates are retrieved or installed.
- (Application and Threats only) Every 30 Minutes—Firewall checks for new dynamic content updates every 30 minutes and installs a new content update if available.Specify how many Minutes Past Half-Hour the firewall should check for new dynamic content updates (between 0 and 29).
- Hourly—Firewall checks for new content updates every hour and installs a new dynamic content update if available.Specify how many Minutes Past Hour the firewall should check for new dynamic content updates (between 0 and 59).
- Daily—Firewall checks for new dynamic content updates every day and installs a new dynamic content update if available.Specify the Time of day the firewall should check for new dynamic content updates.
- Weekly—Firewall checks for new dynamic content updates every week and installs a new dynamic content update if available.Specify the Day and Time the firewall should check for new dynamic content updates.
Configure the Action the firewall takes when a new dynamic content update is available.- None—Firewall doesn’t download or install the new dynamic content update.
- Download Only—Firewall only downloads the new dynamic content update but doesn’t install.If you select Download Only, you must log in to the firewall web interface and install the dynamic content update.
- Download and Install—Firewall downloads and installs the new dynamic content update.
Configure the dynamic content update Threshold.This specifies the dynamic content update must be this many hours old in order for the Action to be taken (between (1 and 336 hours).(Application and Threats only) Configure the New App-ID Threshold.This specifies the amount of time the firewall waits to install a dynamic content update that contains a new App-ID (between (1 and 336 hours).(HA only) Check (enable) Sync to Peer to also install the Antivirus and Application and Threats dynamic content update on the firewall HA peer.Configure the WildFire dynamic content update schedule.- Configure the Recurrence the firewall checks for WildFire dynamic content updates.
- None—No new dynamic content updates are retrieved or installed.
- Every Minute—Firewall checks for new dynamic content updates every minute and installs a new content update if available.
- Every 15 Minutes—Firewall checks for new dynamic content updates every 15 minutes and installs a new content update if available.Specify how many Minutes Past Quarter-Hour the firewall should check for new dynamic content updates (between 0 and 14).
- Every 30 Minutes—Firewall checks for new dynamic content updates every 30 minutes and installs a new content update if available.Specify how many Minutes Past Half-Hour the firewall should check for new dynamic content updates (between 0 and 29).
- Every Hour—Firewall checks for new content updates every hour and installs a new dynamic content update if available.Specify how many Minutes Past Hour the firewall should check for new dynamic content updates (between 0 and 59).
Configure the Action the firewall takes when a new dynamic content update is available.- None—Firewall doesn’t download or install the new dynamic content update.
- Download Only—Firewall only downloads the new dynamic content update but doesn’t install.If you select Download Only, you must log in to the firewall web interface and install the dynamic content update.
- Download and Install—Firewall downloads and installs the new dynamic content update.
(HA only) Check (enable) Synchronize content with HA peer after download/install to also install the WildFire dynamic content update on the firewall HA peer.Save.Schedule a Software Update
- Log in to Strata Cloud Manager.Create a Software Update Grouping Rule.Select ConfigurationNGFW and Prisma AccessSetup, set the Configuration Scope to All Firewalls, select Software UpdateSchedules, and Add Schedule.
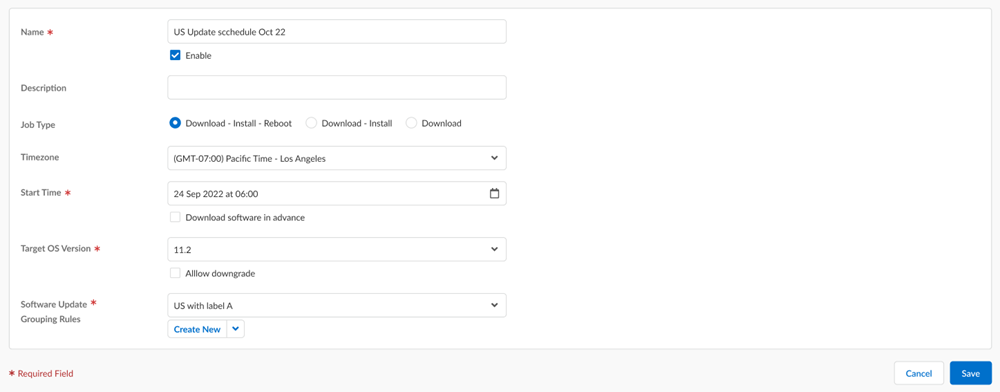
![]() Enter a Name.(Optional) Enter a Description.(Optional) Select the scope of the software upgrade:
Enter a Name.(Optional) Enter a Description.(Optional) Select the scope of the software upgrade:- Download-Install-Reboot to go through the full update process.
- Download-Install to skip the reboot and avoid downtime.
- Download to skip the installation and reboot and manage these manually.
Your NGFWs that have a pending reboot display a warning icon on the Device Management (WorkflowsNGFW SetupDevice Management) page. When you hover over the warning icon, a tooltip appears indicating that a reboot is required to complete the software upgrade process.Select the Timezone for the software install time.Specify the Software Install Time using the calendar tool to indicate the date and time you want the PAN-OS software download and install to occur.Apply the date and time you want the update to occur.(Optional) Check (enable) Download software in advanced to specify a date and time you want the PAN-OS software version to be downloaded on the target firewalls.Use the calendar tool to indicate the date and time you want the PAN-OS software version to be downloaded before install and Apply. The date and time must occur before the Software Install Time.Select the Target OS Version you want to update the firewall to.(PAN-OS Software Downgrades only) If you’re downgrading to an older PAN-OS, you must check (enable) Allow downgrade. The downgrade fails if this setting isn’t enabled.Select Device Grouping Rules to associate firewalls with the software update schedule.You can select multiple device grouping rules to update multiple sets of firewalls.Save.