Next-Generation Firewall
Perform the Initial Configuration for a NGFW
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Perform the Initial Configuration for a NGFW
Review information for how to perform the initial integration of your
NGFW.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
All Palo Alto Networks firewalls provide an out-of-band management port (MGT) that you
can use to perform the firewall administration functions. By using the MGT port, you
separate the management functions of the firewall from the data processing functions,
safeguarding access to the firewall and enhancing performance. When using the web
interface, you must perform all initial configuration tasks from the MGT port even if
you plan to use an in-band data port for managing your firewall going forward.
Some management tasks, such as retrieving licenses and updating the threat and
application signatures on the firewall require access to the Internet. If you do not
want to enable external access to your MGT port, you will need to either set up an
in-band data port to provide access to required external services (using service routes)
or plan to manually upload updates regularly.
Do not enable
access to your management interface from the internet or from other untrusted zones
inside your enterprise security boundary. This applies whether you use the dedicated
management port (MGT) or you configured a data port as your management interface.
When integrating your firewall into your management network, follow the Adminstrative Access Best Practices to
ensure that you are securing administrative access to your firewalls and other
security devices in a way that prevents successful attacks.
Cloud Management
Perform the initial configuration for your cloud managed NGFWs.
Coming Soon
PAN-OS & Panorama
Perform the initial configuration for a NGFW.
By default, the PA-Series firewall has an IP address of 192.168.1.1 and a
username/password of admin/admin. For security reasons, you must change these
settings before continuing with other firewall configuration tasks. You must perform
these initial configuration tasks either from the MGT interface, even if you do not
plan to use this interface for your firewall management, or using a direct serial
connection to the console port on the firewall.
- Install your firewall and connect power to it.If your firewall model has dual power supplies, connect the second power supply for redundancy. Refer to the hardware reference guide for your model for details.
- Gather the required information from your network administrator.
- IP address for MGT port
- Netmask
- Default gateway
- DNS server address
- Connect your computer to the firewall.You can connect to the firewall in one of the following ways:
- Connect a serial cable from your computer to the Console port and connect to the firewall using terminal emulation software (9600-8-N-1). Wait a few minutes for the boot-up sequence to complete; when the firewall is ready, the prompt changes to the name of the firewall, for example PA-220 login.
- Connect an RJ-45 Ethernet cable from your computer to the MGT port on the firewall. From a browser, go to https://192.168.1.1.
You may need to change the IP address on your computer to an address in the 192.168.1.0/24 network, such as 192.168.1.2, to access this URL. - When prompted, log in to the firewall.You must log in using the default username and password (admin/admin). The firewall will begin to initialize.
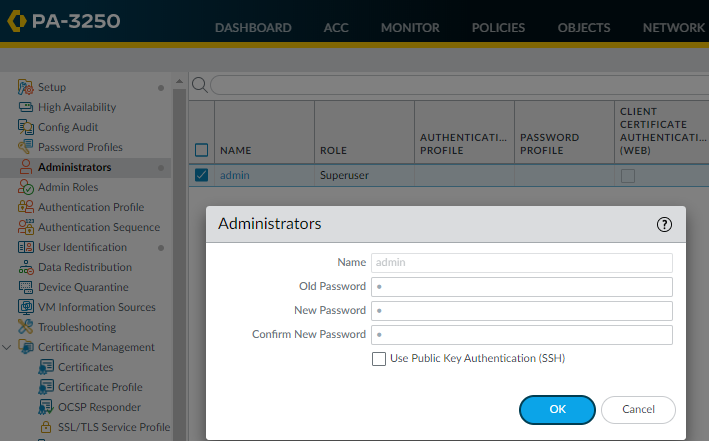
- Set a secure username and password for the admin account.Starting with PAN-OS 9.0.4, the predefined, default administrator password (admin) must be changed on the first login on a device. The new password must be a minimum of eight characters and include a minimum of one lowercase and one uppercase character, as well as one number or special character. Although you don’t have to configure a new username, it is a best practice to do so and to use unique usernames and passwords for each administrator. Beginning with PAN-OS 10.2, the login must include at least one alphabetical character or symbol (underscore, period, or hyphen, although a hyphen cannot be the first character in the username) and cannot be numbers only.Be sure to use the best practices for password strength to ensure a strict password and review the password complexity settings.
- Select DeviceAdministrators.
- Select the admin role.
- Enter the current default password and the new password.
![]()
- Click OK to save your settings.
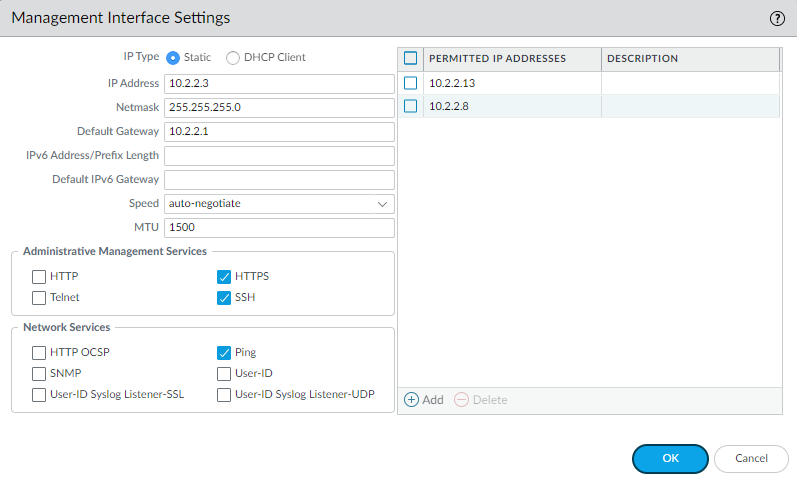
- Configure the MGT interface.
- Select DeviceSetupInterfaces and edit the Management interface.
- Configure the address settings for the MGT interface using one of the
following methods:
-
To configure static IP address settings for the MGT interface, set the IP Type to Static and enter the IP Address, Netmask, and Default Gateway.
-
To dynamically configure the MGT interface address settings, set the IP Type to DHCP Client. To use this method, you must Configure the Management Interface as a DHCP Client.
To prevent unauthorized access to the management interface, it is a an administrative best practice to Add the Permitted IP Addresses from which an administrator can access the MGT interface. -
- Set the Speed to auto-negotiate.
- Select which management services to allow on the interface.Make sure Telnet and HTTP are not selected because these services use plaintext and are not as secure as the other services and could compromise administrator credentials.
![]()
- Click OK.
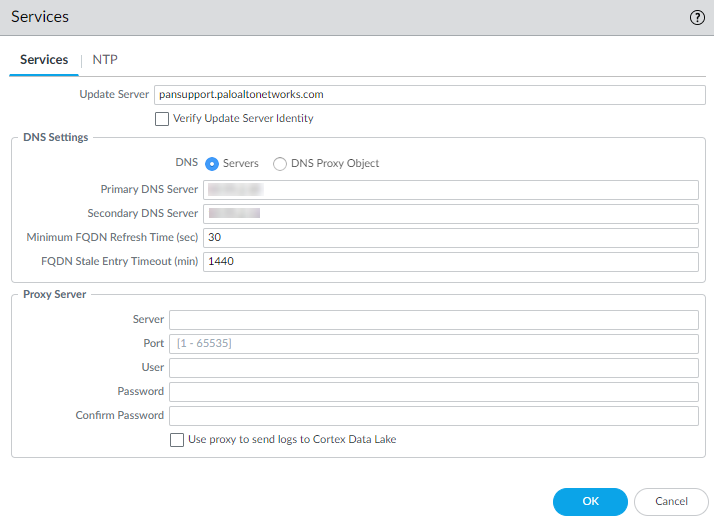
- Configure DNS, update server, and proxy server
settings.You must manually configure at least one DNS server on the firewall or it will not be able to resolve hostnames; it will not use DNS server settings from another source, such as an ISP.
- Select DeviceSetupServices.
-
For multi-virtual system platforms, select Global and edit the Services section.
-
For single virtual system platforms, edit the Services section.
-
- On the Services tab, for
DNS, select one of the following:
-
Servers—Enter the Primary DNS Server address and Secondary DNS Server address.
-
DNS Proxy Object—From the drop-down, select the DNS Proxy that you want to use to configure global DNS services, or click DNS Proxy to configure a new DNS proxy object.
![]()
-
- Click OK.
- Select DeviceSetupServices.
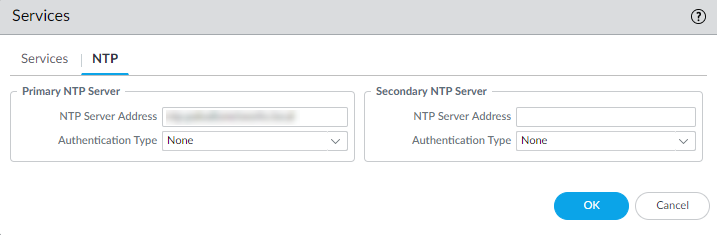
- Configure date and time (NTP) settings.
- Select DeviceSetupServices.
-
For multi-virtual system platforms, select Global and edit the Services section.
-
For single virtual system platforms, edit the Services section.
-
- On the NTP tab, to use the virtual cluster of
time servers on the Internet, enter the hostname
pool.ntp.org as the Primary NTP
Server or enter the IP address of your primary NTP
server.
![]()
- (Optional) Enter a Secondary NTP Server address.
- (Optional) To authenticate time updates from the NTP
server(s), for Authentication Type, select one of
the following for each server:
-
None—(Default) Disables NTP authentication.
-
Symmetric Key—Firewall uses symmetric key exchange (shared secrets) to authenticate time updates.
-
Key ID—Enter the Key ID (1-65534).
-
Algorithm—Select the algorithm to use in NTP authentication (MD5 or SHA1).
-
-
Autokey—Firewall uses autokey (public key cryptography) to authenticate time updates.
-
- Click OK.
- Select DeviceSetupServices.
- (Optional) Configure general firewall settings as needed.
- Select DeviceSetupManagement and edit the General Settings.
- Enter a Hostname for the firewall and enter your network Domain name. The domain name is just a label; it will not be used to join the domain.
- Enter Login Banner text that informs users who
are about to log in that they require authorization to access the
firewall management functions.As a best practice, avoid using welcoming verbiage. Additionally, you should ask your legal department to review the banner message to ensure it adequately warns that unauthorized access is prohibited.
- Enter the Latitude and Longitude to enable accurate placement of the firewall on the world map.
- Click OK.
- Commit your changes.When the configuration changes are saved, you lose connectivity to the web interface because the IP address has changed.Click Commit at the top right of the web interface. The firewall can take up to 90 seconds to save your changes.
- Connect the firewall to your network.
- Disconnect the firewall from your computer.
- (All firewalls except for the PA-5450) Connect the MGT port to a switch port on your management network using an RJ-45 Ethernet cable. Make sure that the switch port you cable the firewall to is configured for auto-negotiation.
- (PA-5450 only) Connect the MGT port to a switch port on your management network using a Palo Alto Networks certified SFP/SFP+ transceiver and cable.
- Open an SSH management session to the firewall.Using a terminal emulation software, such as PuTTY, launch an SSH session to the firewall using the new IP address you assigned to it.
- Verify network access to external services required for firewall management,
such as the Palo Alto Networks Update Server.You can do this in one of the following ways:
-
If you do not want to allow external network access to the MGT interface, you will need to set up a data port to retrieve required service updates. Continue to Set Up Network Access for External Services.
-
If you do plan to allow external network access to the MGT interface, verify that you have connectivity and then proceed to Register Your NGFW and Activate Subscription Licenses.
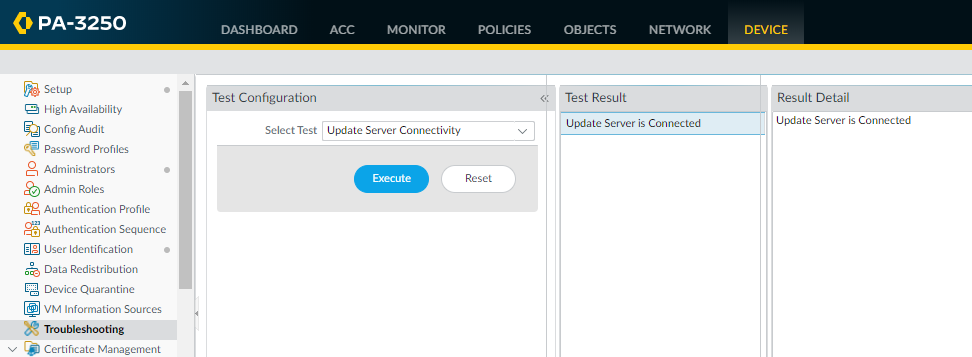
- Use update server connectivity test to verify network connectivity to
the Palo Alto Networks Update server as shown in the following
example:
-
Select DeviceTroubleshooting, and select Update Server Connectivity from the Select Test drop-down.
-
Execute the update server connectivity test.
![]()
-
- Use the following CLI command to retrieve information on the support
entitlement for the firewall from the Palo Alto Networks update
server:
request support checkIf you have connectivity, the update server will respond with the support status for your firewall. If your firewall is not yet registered, the update server returns the following message:Contact Us https://www.paloaltonetworks.com/company/contact-us.html Support Home https://www.paloaltonetworks.com/support/tabs/overview.html Device not found on this update server
-