Configure Credential Detection with the Windows User-ID Agent
Table of Contents
End-of-Life (EoL)
Configure Credential Detection with the Windows User-ID Agent
Learn how to configure credential detection with the
Windows User-ID agent to prevent credential phishing.
Domain
Credential Filter detection enables the firewall to detect
passwords submitted to web pages. This credential detection method
requires the Windows User-ID agent and the User-ID credential service,
an add-on to the User-ID agent, to be installed on a read-only
domain controller (RODC).
The Domain Credential
Filter detection method is supported with the Windows User-ID agent
only. You cannot use the PAN-OS integrated User-ID agent to configure this
method of credential detection.
An RODC is a Microsoft
Windows server that maintains a read-only copy of an Active Directory
database that a domain controller hosts. When the domain controller
is located at a corporate headquarters, for example, RODCs can be
deployed in remote network locations to provide local authentication
services. Installing the User-ID agent on an RODC can be useful
for a few reasons: access to the domain controller directory is
not required to enable credential detection and you can support
credential detection for a limited or targeted set of users. Because
the directory the RODC hosts is read-only, the directory contents
remain secure on the domain controller.
Because
you must install the Windows User-ID agent on the RODC for credential
detection, as a best practice deploy a separate agent for this purpose.
Do not use the User-ID agent installed on the RODC to map IP addresses
to users.
After you install the User-ID agent on an
RODC, the User-ID credential service runs in the background and
scans the directory for the usernames and password hashes of group members
that are listed in the RODC password replication policy (PRP)—you
can define who you want to be on this list. The User-ID credential
service then takes the collected usernames and password hashes and
deconstructs the data into a type of bit mask called a bloom
filter. Bloom filters are compact data structures that provide
a secure method to check if an element (a username or a password
hash) is a member of a set of elements (the sets of credentials
you have approved for replication to the RODC). The User-ID credential service
forwards the bloom filter to the Windows User-ID agent; the firewall
retrieves the latest bloom filter from the User-ID agent at regular
intervals and uses it to detect usernames and password hash submissions.
Depending on your settings, the firewall then blocks, alerts, or
allows on valid password submissions to web pages, or displays a
response page to users warning them of the dangers of phishing,
but allowing them to continue with the submission.
Throughout
this process, the User-ID agent does not store or expose any password
hashes, nor does it forward password hashes to the firewall. Once
the password hashes are deconstructed into a bloom filter, there
is no way to recover them.
- Configure user mapping using the Windows User-ID agent.To enable credential detection, you must install the Windows User-ID agent on an RODC. Refer to the Compatibility Matrix for a list of supported servers. Install a separate User-ID agent for this purpose.Important items to remember when setting up User-ID to enable domain credential filter detection:
- Because the effectiveness of credential phishing detection is dependent on your RODC setup, make sure that you also review best practices and recommendations for RODC Administration.
- Download User-ID software updates:
- User-ID Agent Windows installer—UaInstall-x.x.x-x.msi.
- User-ID Agent Credential Service Windows installer—UaCredInstall64-x.x.x-x.msi.
- Install the User-ID agent and the User Agent Credential service on an RODC using an account that has privileges to read Active Directory via LDAP (the User-ID agent also requires this privilege).
- The User-ID Agent Credential Service requires permission to log on with the local system account. For more information, refer to Create a Dedicated Service Account for the User-ID Agent.
- The service account must be a member of the local administrator group on the RODC. For more information, refer to the following link.
Enable the User-ID agent and the User Agent Credential service (which runs in the background to scan permitted credentials) to share information.- On the RODC server, launch the User-ID Agent.Select Setup and edit the Setup section.
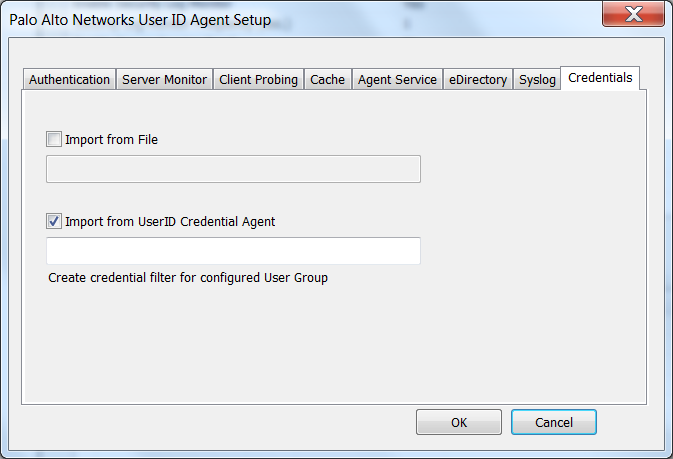
![]() Select the Credentials tab. This tab only displays if you have already installed the User-ID Agent Credential Service.
Select the Credentials tab. This tab only displays if you have already installed the User-ID Agent Credential Service.![]() Select Import from User-ID Credential Agent. This enables the User-ID agent to import the bloom filter that the User-ID credential agent creates to represent users and the corresponding password hashes.Click OK, Save your settings, and Commit.In the RODC directory, define the group of users for which you want to support credential submission detection.
Select Import from User-ID Credential Agent. This enables the User-ID agent to import the bloom filter that the User-ID credential agent creates to represent users and the corresponding password hashes.Click OK, Save your settings, and Commit.In the RODC directory, define the group of users for which you want to support credential submission detection.- Confirm that the groups that should receive credential submission enforcement are added to the Allowed RODC Password Replication Group.
- Check that none of the groups in the Allowed RODC Password Replication Group are also in the Denied RODC Password Replication Group by default. Groups listed in both will not be subject to credential phishing enforcement.
Continue to the next task.Set up credential phishing prevention on the firewall.