Next-Generation Firewall
App-ID and HTTP/2 Inspection
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
App-ID and HTTP/2 Inspection
Palo Alto Networks firewalls can inspect and enforce
security policy for HTTP/2 traffic, on a stream-by-stream basis.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
This is a core Network Security feature for NGFWs and Prisma
Access; no prerequisites needed.
|
You can now safely enable applications running
over HTTP/2, without any additional configuration on the firewall.
As more websites continue to adopt HTTP/2, the firewall can enforce
security policy and all threat detection and prevention capabilities
on a stream-by-stream basis. This visibility into HTTP/2 traffic
enables you to secure web servers that provide services over HTTP/2,
and allow your users to benefit from the speed and resource efficiency
gains that HTTP/2 provides.

The firewall
processes and inspects HTTP/2 traffic by default when SSL decryption is enabled.
For HTTP/2 inspection to work correctly, the firewall must be enabled
to use ECDHE (elliptic curve Diffie-Hellman) as a key exchange algorithm
for SSL sessions. ECDHE is enabled by default, but you can check
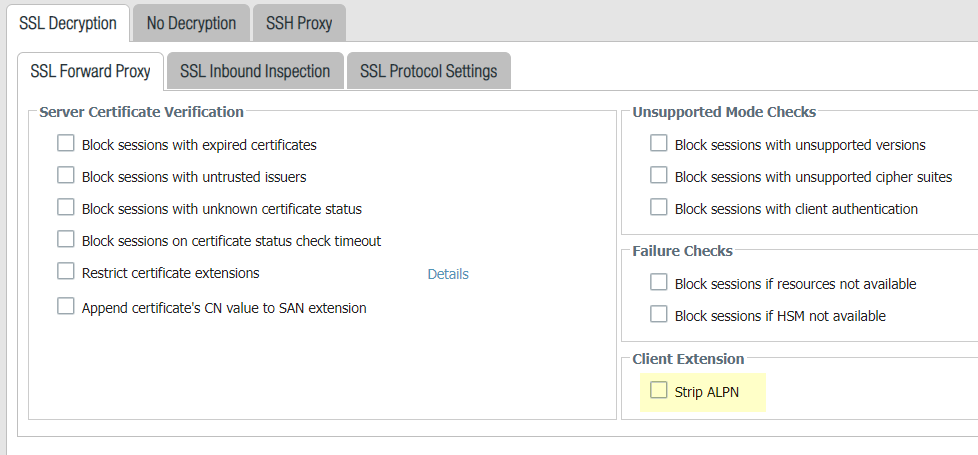
to confirm that it’s enabled by selecting ObjectsDecryptionDecryption ProfileSSL DecryptionSSL Protocol Settings.

You can disable
HTTP/2 inspection for targeted traffic, or globally:
- Disable HTTP/2 inspection for targeted traffic.You’ll need to specify for the firewall to remove any value contained in the Application-Layer Protocol Negotiation (ALPN) TLS extension. ALPN is used to secure HTTP/2 connections—when there is no value specified for this TLS extension, the firewall either downgrades HTTP/2 traffic to HTTP/1.1 or classifies it as unknown TCP traffic.
![]()
- Select ObjectsDecryptionDecryption ProfileSSL DecryptionSSL Forward Proxy and then select Strip ALPN.Attach the decryption profile to a decryption policy (PoliciesDecryption) to turn off HTTP/2 inspection for traffic that matches the policy.Commit your changes.Disable HTTP/2 inspection globally.Use the CLI command: set deviceconfig setting http2 enable no and Commit your changes. The firewall will classify HTTP/2 traffic as unknown TCP traffic.