Next-Generation Firewall
Use the Administrator Login Activity Indicators to Detect Account Misuse
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Use the Administrator Login Activity Indicators to Detect Account Misuse
Monitor and analyze administrator login activity indicators in PAN-OS to identify
suspicious access patterns, failed login attempts, and potential compromise or misuse on
NGFWs.
| Where Can I Use This? | What Do I Need? |
|---|---|
| NGFW (Managed by PAN-OS or Panorama) |
|
The last login time and failed login attempts
indicators provide a visual way to detect misuse of your administrator
account on a Palo Alto Networks firewall or Panorama management
server. Use the last login information to determine if someone else
logged in using your credentials and use the failed login attempts
indicator to determine if your account is being targeted in a brute-force
attack.
- View the login activity indicators to monitor recent activity on your account.
- Log in to the web interface on your firewall or Panorama management server.View the last login details located at the bottom left of the window and verify that the timestamp corresponds to your last login.
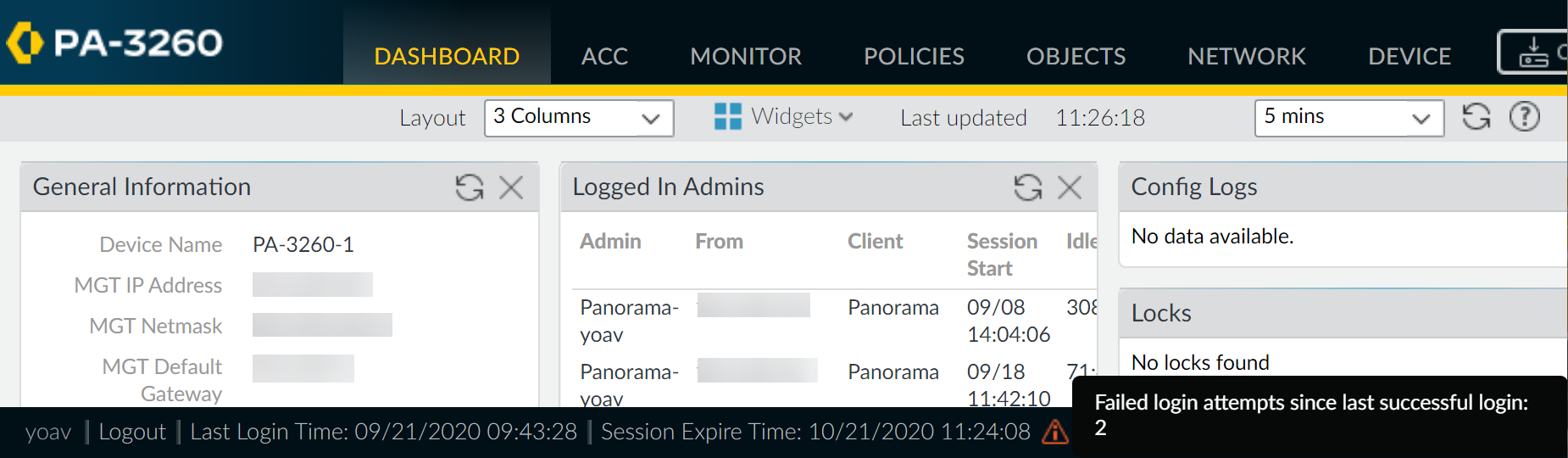
![]() Look for a caution symbol to the right of the last login time information for failed login attempts.The failed login indicator appears if one or more failed login attempts occurred using your account since the last successful login.
Look for a caution symbol to the right of the last login time information for failed login attempts.The failed login indicator appears if one or more failed login attempts occurred using your account since the last successful login.- If you see the caution symbol, hover over it to display the number of failed login attempts.
![]()
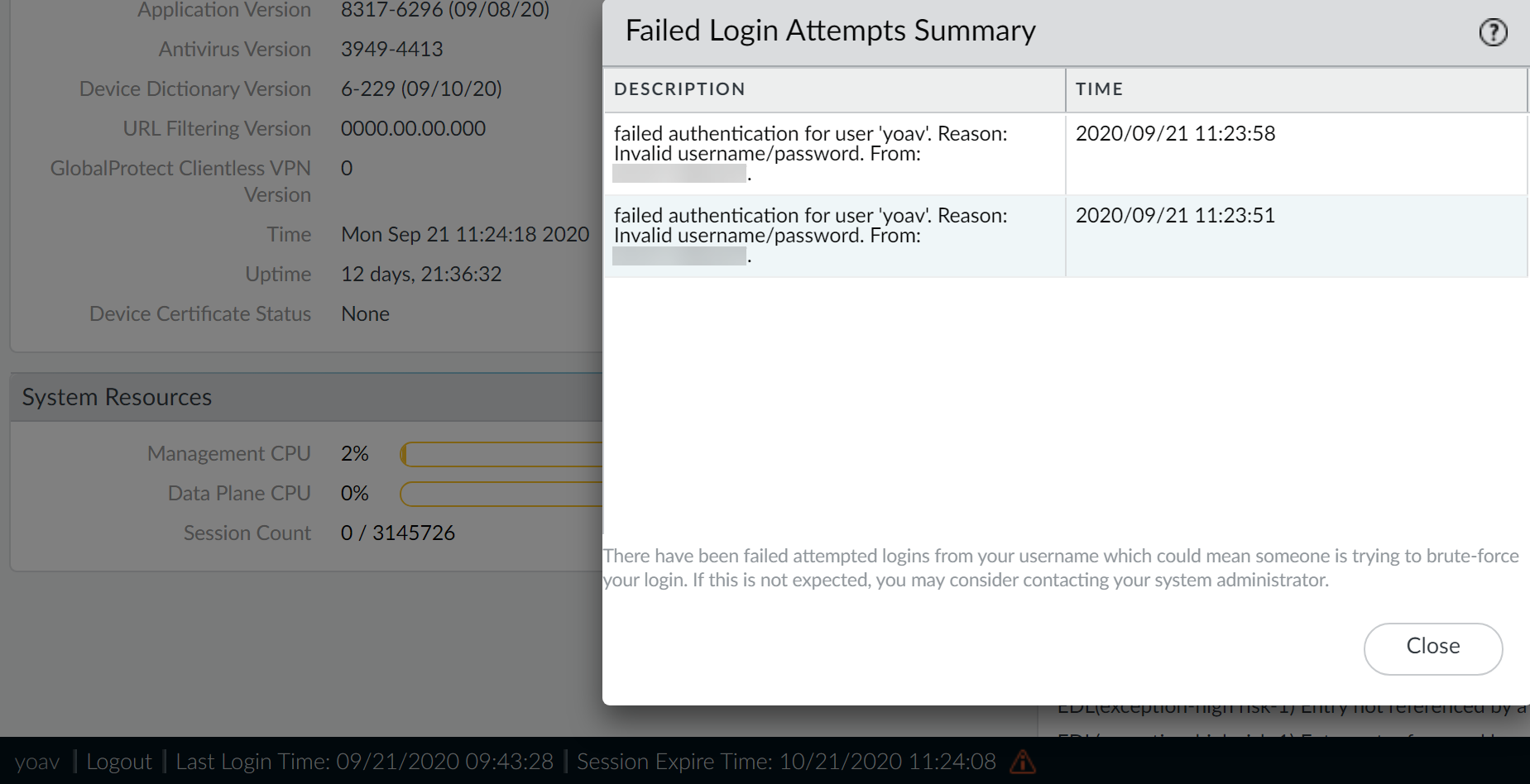
- Click the caution symbol to view the failed login attempts summary. Details include the admin account name, the reason for the login failure, the source IP address, and the date and time.After you successfully log in and then log out, the failed login counter resets to zero so you will see new failed login details, if any, the next time you log in.
Locate hosts that are continually attempting to log in to your firewall or Panorama management server.- Click the failed login caution symbol to view the failed login attempts summary.Locate and record the source IP address of the host that attempted to log in. For example, the following figure shows multiple failed login attempts.
![]() Work with your network administrator to locate the user and host that is using the IP address that you identified.If you cannot locate the system that is performing the brute-force attack, consider renaming the account to prevent future attacks.Take the following actions if you detect an account compromise.
Work with your network administrator to locate the user and host that is using the IP address that you identified.If you cannot locate the system that is performing the brute-force attack, consider renaming the account to prevent future attacks.Take the following actions if you detect an account compromise.- Select MonitorLogsConfiguration and view the configuration changes and commit history to determine if your account was used to make changes without your knowledge.Select DeviceConfig Audit to compare the current configuration and the configuration that was running just prior to the configuration you suspect was changed using your credentials. You can also do this using Panorama.If your administrator account was used to create a new account, performing a configuration audit helps you detect changes that are associated with any unauthorized accounts, as well.Revert the configuration to a known good configuration if you see that logs were deleted or if you have difficulty determining if improper changes were made using your account.Before you commit to a previous configuration, review it to ensure that it contains the correct settings. For example, the configuration that you revert to may not contain recent changes, so apply those changes after you commit the backup configuration.Use the following best practices to help prevent brute-force attacks on privileged accounts.
- Limit the number of failed attempts allowed before the firewall locks a privileged account by setting the number of Failed Attempts and the Lockout Time (min) in the authentication profile or in the Authentication Settings for the Management interface (DeviceSetupManagementAuthentication Settings).
- Use Interface Management Profiles to Restrict Access.
- Enforce complex passwords for privileged accounts.