Next-Generation Firewall
Register Your NGFW
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Register Your NGFW
Learn about how to register your NGFW with the Palo Alto Networks Customer Support
Portal.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Before you can activate support and other licenses and subscriptions, you must first
register the NGFW. Before you can register a NGFW, though, you must first have an
active support account. Perform one of the following tasks depending on whether you
have an active support account:
- If you don’t have an active support account, then Create a New Support Account and Register a Next-Generation Firewall.
- If you already have an active support account, then you are ready to Register the NGFW.
- (Optional) Perform Day 1 Configuration on a registered NGFW.
- If your NGFW uses line cards such as an NPC (Network Processing Card), then Register the NGFW Line Cards.
If you are registering a VM-Series NGFW, refer to
the VM-Series Deployment Guide for
instructions.
Create a New Support Account and Register an NGFW
If you do not already have an active Palo Alto Networks support account, then you
need to register your NGFW when you create your new support account.
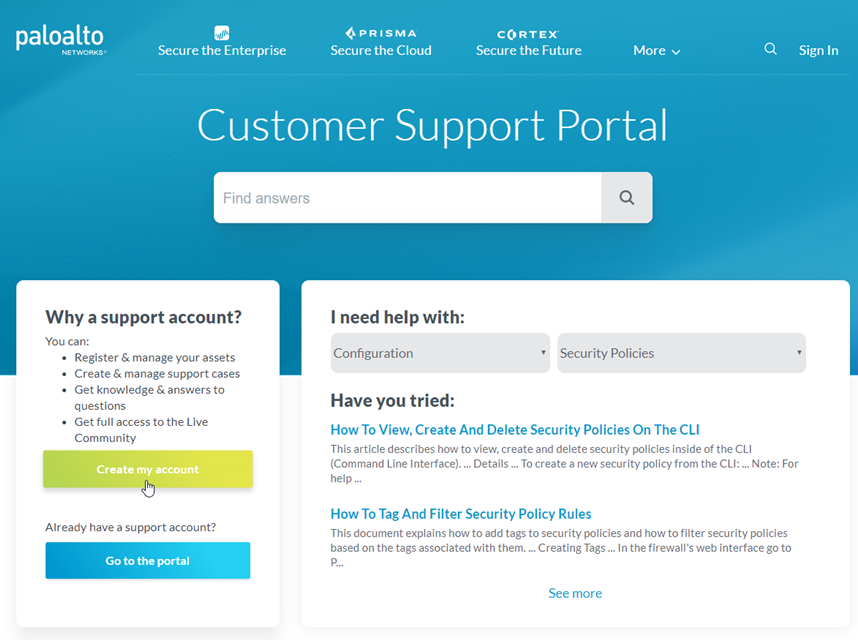
- Go to the Palo Alto Networks Customer Support Portal.Click Create my account.
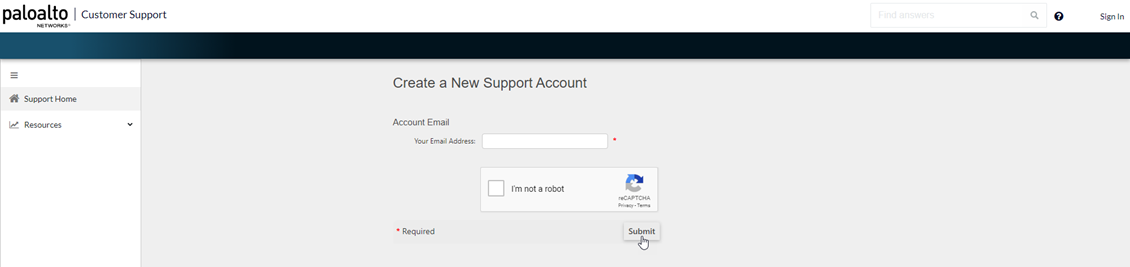
![]() Enter Your Email Address, check I’m not a robot, and click Submit.
Enter Your Email Address, check I’m not a robot, and click Submit.![]() Select Register device using Serial Number or Authorization Code and click Next.
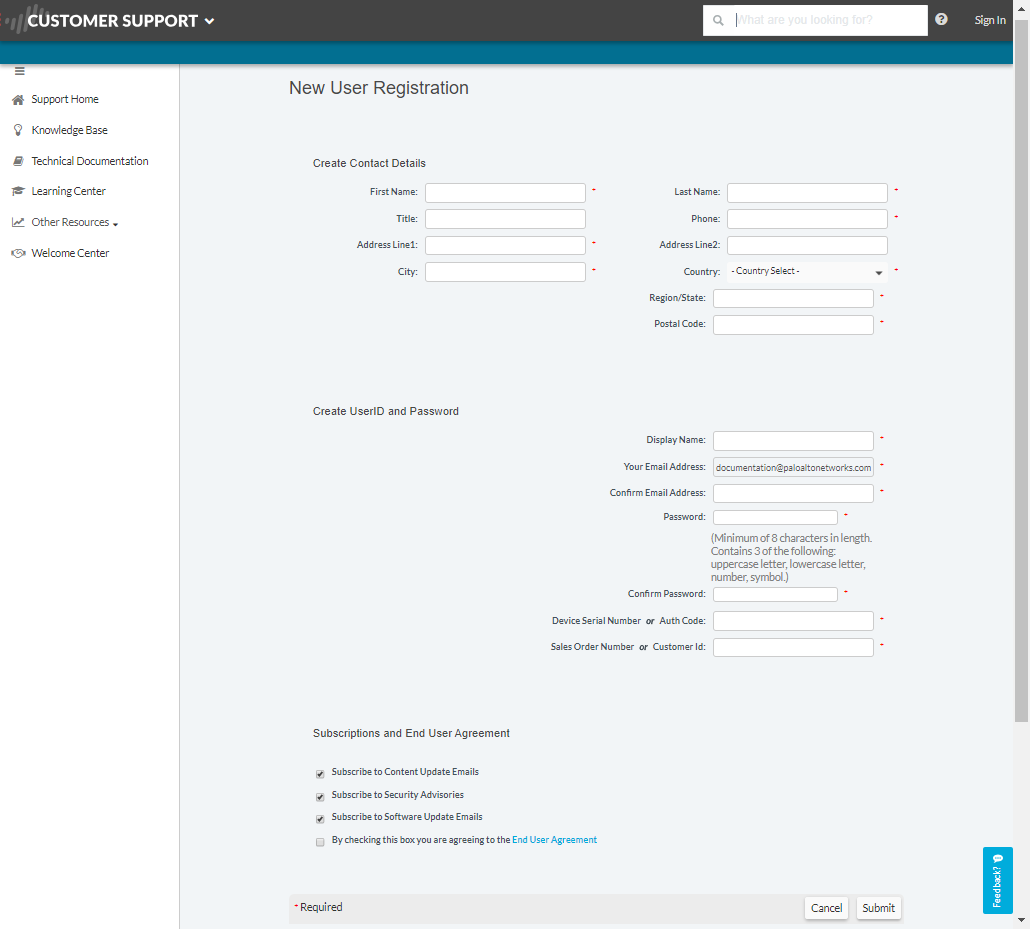
Select Register device using Serial Number or Authorization Code and click Next.![]() Complete the registration form.
Complete the registration form.- Enter your contact details. Required fields are indicated by red asterisks.Create a UserID and Password for the account. Required fields are indicated by red asterisks.Enter the Device Serial Number or Auth Code.Enter your Sales Order Number or Customer Id.To ensure that you are always alerted to the latest updates and security advisories, Subscribe to Content Update Emails, Subscribe to Security Advisories, and Subscribe to Software Update Emails.Select the check box to agree to the End User Agreement and Submit.
![]()
Register an NGFW
If you already have an active Palo Alto Networks Customer Support account, perform the following task to register your NGFW.- Log in to the NGFW web interface.Using a secure connection (HTTPS) from your web browser, log in using the new IP address and password you assigned during initial configuration (https://<IP address>).Locate your serial number and copy it to the clipboard.On the Dashboard, locate your Serial Number in the General Information section of the screen.Go to the Palo Alto Networks Customer Support Portal and, if not already logged in, Sign In now.
![]() Register the NGFW.
Register the NGFW.- On the Support Home page, click Register a Device.
![]() Select Register device using Serial Number or Authorization Code, and then click Next.
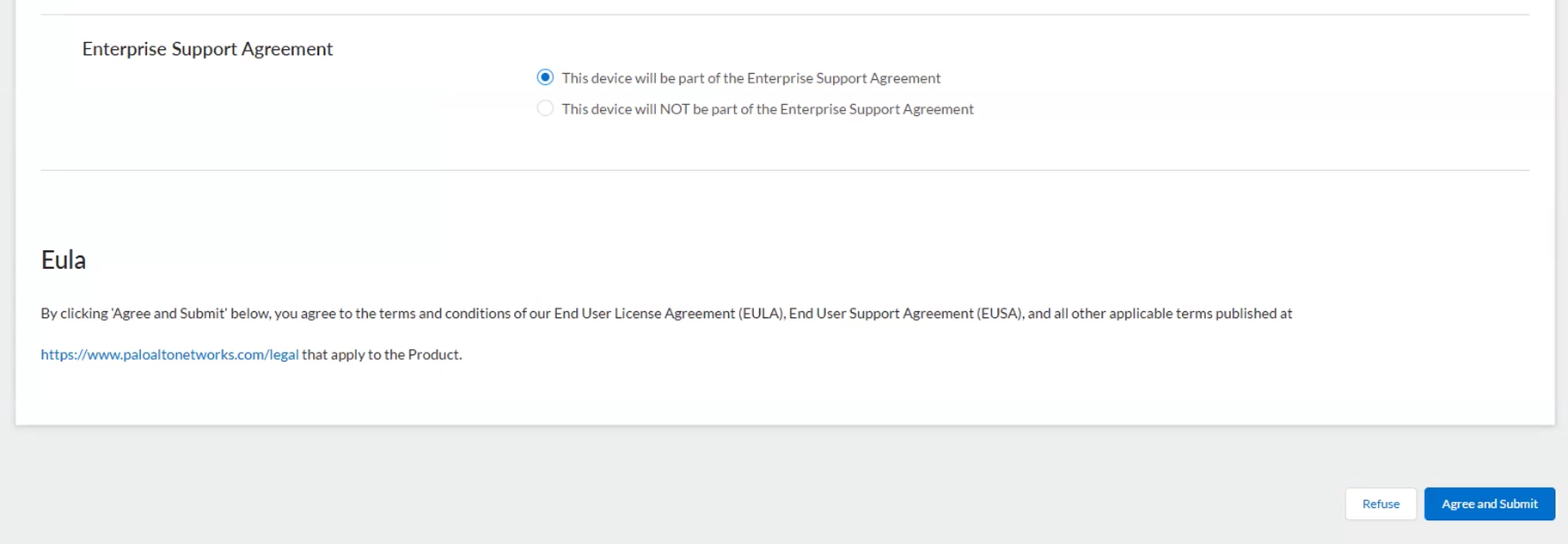
Select Register device using Serial Number or Authorization Code, and then click Next.![]() Enter the NGFW Serial Number (you can copy and paste it from the NGFW Dashboard).(Optional) Enter the Device Name and Device Tag.(Optional) If the device will not have a connection to the internet, select the Device will be used offline check box and then, from the drop-down, select the OS Release you plan to use.Provide information about the physical location where you plan to deploy the NGFW including the Address, City, Postal Code, and Country.The physical location of the NGFW is set on the Customer Support Portal. There is no command on the NGFW to set the physical location.Select whether or not the device will be a part of the Enterprise Support Agreement. If you select This device will be a part of the Enterprise Support Agreement, the device is added to your ESA contract and is made visible on the ESA dashboard. From here, you can monitor coverage and usage of the device as it pertains to your total hardware estate.You can remove a device from the Enterprise Agreement by visiting the Enterprise Agreements dashboard.Read the End User License Agreement (EULA) and the Support Agreement, then Agree and Submit.
Enter the NGFW Serial Number (you can copy and paste it from the NGFW Dashboard).(Optional) Enter the Device Name and Device Tag.(Optional) If the device will not have a connection to the internet, select the Device will be used offline check box and then, from the drop-down, select the OS Release you plan to use.Provide information about the physical location where you plan to deploy the NGFW including the Address, City, Postal Code, and Country.The physical location of the NGFW is set on the Customer Support Portal. There is no command on the NGFW to set the physical location.Select whether or not the device will be a part of the Enterprise Support Agreement. If you select This device will be a part of the Enterprise Support Agreement, the device is added to your ESA contract and is made visible on the ESA dashboard. From here, you can monitor coverage and usage of the device as it pertains to your total hardware estate.You can remove a device from the Enterprise Agreement by visiting the Enterprise Agreements dashboard.Read the End User License Agreement (EULA) and the Support Agreement, then Agree and Submit.![]() You can search for and manage the NGFW you just registered from the Network Security page.(Firewalls with line cards) To ensure that you receive support for your NGFW’s line cards, make sure to register the NGFW line cards.
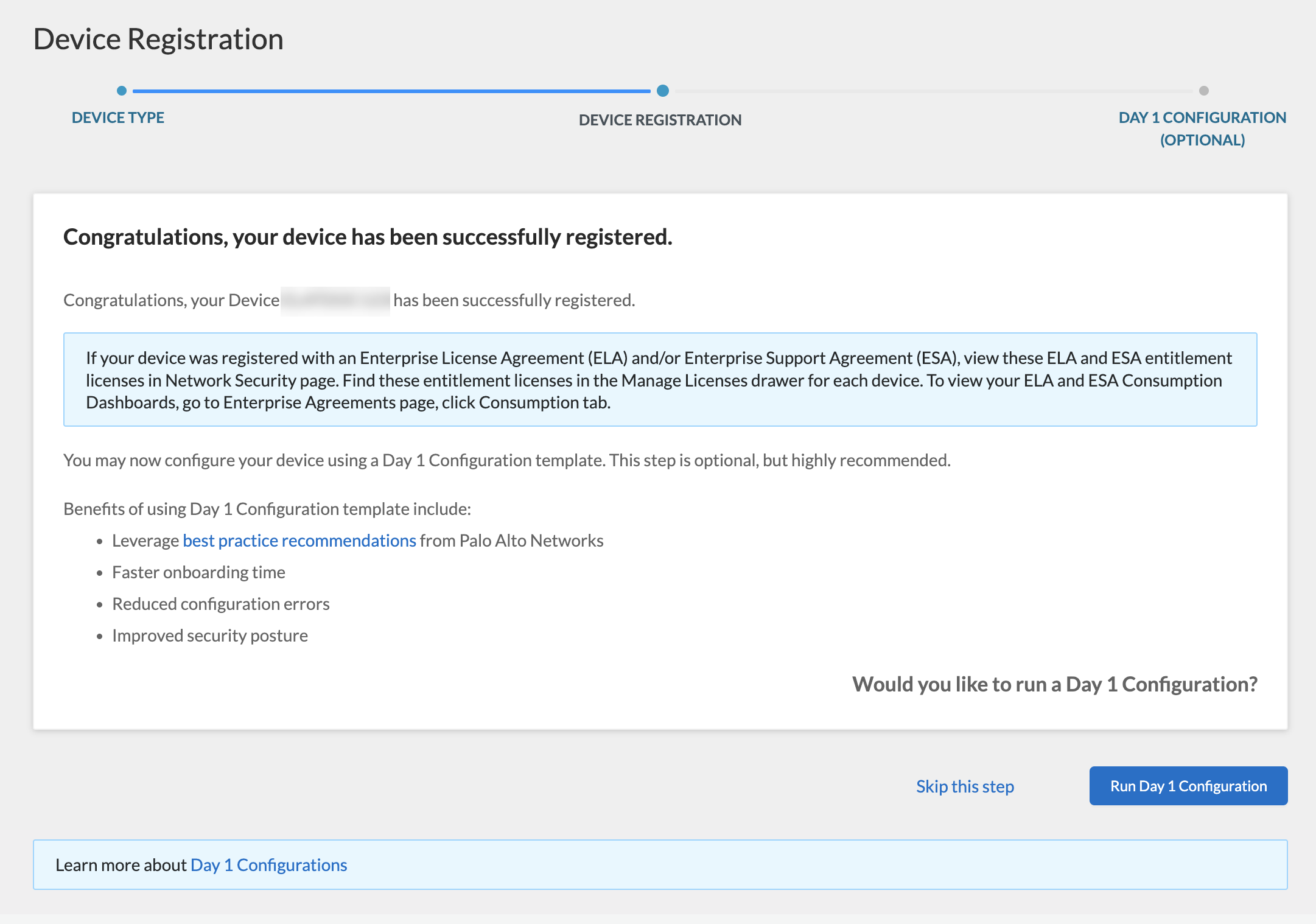
You can search for and manage the NGFW you just registered from the Network Security page.(Firewalls with line cards) To ensure that you receive support for your NGFW’s line cards, make sure to register the NGFW line cards.(Optional) Perform Day 1 Configuration
After you register your NGFW, you have the option of running Day 1 Configuration. The Day 1 Configuration tool provides configuration templates informed by Palo Alto Networks best practices, which you can use as a starting point to build the rest of your configuration.The benefits of Day 1 Configuration templates include:- Faster implementation time
- Reduced configuration errors
- Improved security posture
Perform Day 1 Configuration by following these steps:- From the page that displays after you have registered your NGFW, select Run Day 1 Configuration.
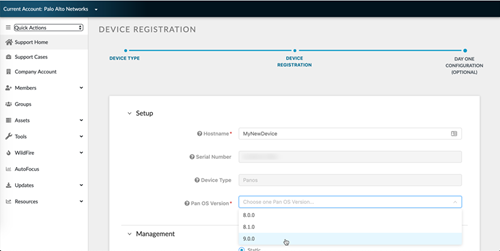
![]() If you’ve already registered your NGFW but haven’t run Day 1 Configuration, you can also run it from the Customer Support Portal home page by selecting ToolsRun Day 1 Configuration.Enter the Hostname and Pan OS Version for your new device, and optionally, the Serial Number and Device Type.
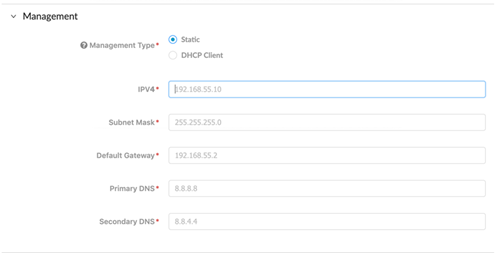
If you’ve already registered your NGFW but haven’t run Day 1 Configuration, you can also run it from the Customer Support Portal home page by selecting ToolsRun Day 1 Configuration.Enter the Hostname and Pan OS Version for your new device, and optionally, the Serial Number and Device Type.![]() Under Management, select either Static or DHCP Client for your Management Type.Selecting Static will require you fill out the IPV4, Subnet Mask, and Default Gateway fields.
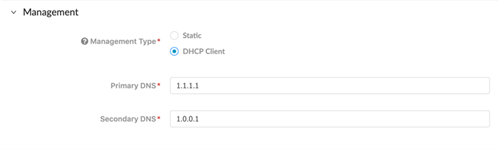
Under Management, select either Static or DHCP Client for your Management Type.Selecting Static will require you fill out the IPV4, Subnet Mask, and Default Gateway fields.![]() Selecting DHCP Client only requires that you enter the Primary DNS and Secondary DNS. A device configured in DHCP client mode will ensure the management interface receives an IP address from the local DHCP server, or it will fill out all the parameters if they are known.
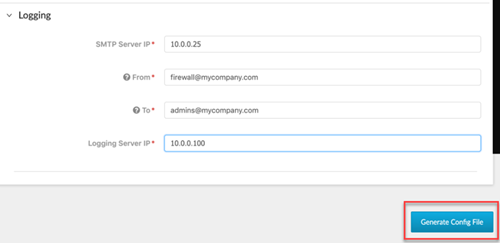
Selecting DHCP Client only requires that you enter the Primary DNS and Secondary DNS. A device configured in DHCP client mode will ensure the management interface receives an IP address from the local DHCP server, or it will fill out all the parameters if they are known.![]() Fill out all fields under Logging.Click Generate Config File.
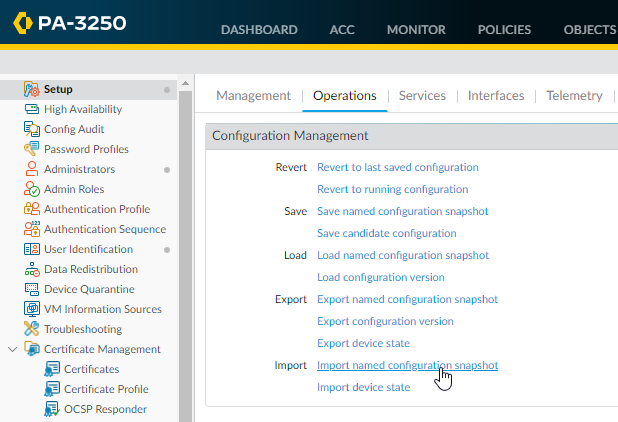
Fill out all fields under Logging.Click Generate Config File.![]() To import and load the Day 1 Configuration file you just downloaded to your NGFW:
To import and load the Day 1 Configuration file you just downloaded to your NGFW:- Log into your NGFW web interface.Select DeviceSetupOperations.Click Import named configuration snapshot.Select the file.
![]()
Register the NGFW Line Cards
The following NGFWs use line cards that must be registered to receive support with troubleshooting and returns:- PA-7000 Series NGFWs
- PA-5450 NGFW
Return to these instructions after creating your Customer Support account and registering your NGFW.- Go to the Palo Alto Networks Customer Support Portal and, if not already logged in, Sign In now.Select AssetsLine Cards/Optics/FRUs.Register Components.Enter the Palo Alto Networks Sales Order Number of the line cards into the Sales Order Number field to display the line cards eligible for registration.Register the line cards to your NGFW by entering its chassis serial number in the Serial Number field. The Location Information below auto-populates based on the registration information of your NGFW.Click Agree and Submit to accept the legal terms. The system updates to display the registered line cards under AssetsLine Cards/Optics/FRUs.