Upgrade a ZTP Firewall
Table of Contents
10.1
Expand all | Collapse all
-
-
- Upgrade Panorama with an Internet Connection
- Upgrade Panorama Without an Internet Connection
- Install Content Updates Automatically for Panorama without an Internet Connection
- Upgrade Panorama in an HA Configuration
- Migrate Panorama Logs to the New Log Format
- Upgrade Panorama for Increased Device Management Capacity
- Downgrade from Panorama 10.1
- Troubleshoot Your Panorama Upgrade
-
- What Updates Can Panorama Push to Other Devices?
- Schedule a Content Update Using Panorama
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade a WildFire Cluster from Panorama with an Internet Connection
- Upgrade a WildFire Cluster from Panorama without an Internet Connection
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
Upgrade a ZTP Firewall
Automatically upgrade your a ZTP firewall.
After you successfully add a ZTP firewall to the Panorama™
management server, configure the target PAN-OS version of the ZTP firewall. Panorama
checks whether PAN-OS version installed on the ZTP firewall is greater than or equal
to the configured target PAN-OS version after it successfully connects to Panorama
for the first time. If the PAN-OS version installed on the ZTP firewall is less than
the target PAN-OS version, then the ZTP firewall enters an upgrade cycle until
target PAN-OS version is installed.
When upgrading ZTP firewalls from PAN-OS 10.1 to PAN-OS 11.1 or
later versions, do not use the To SW Version column to set a target
PAN-OS version. Using the To SW Version column causes the upgrade
flow to download and install an intermediary base version with an expired
root certificate, causing the firewall to lose connection with Panorama.
Instead, after onboarding the ZTP firewall, manually upgrade to the target PAN-OS
version that includes a valid root certificate.
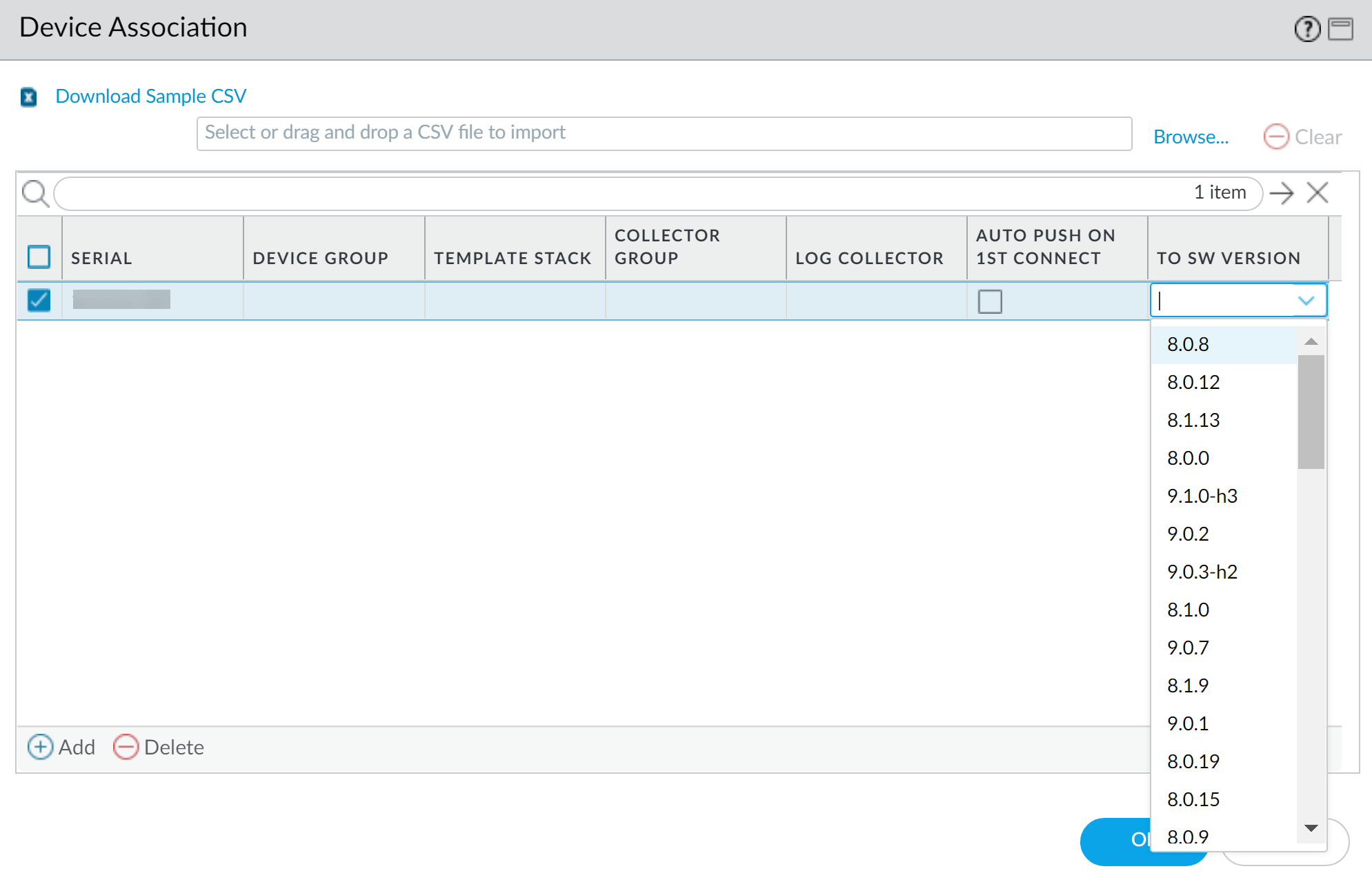
- Log in to the Panorama Web Interface as an admin user.Add a ZTP Firewall to Panorama.Select PanoramaDevice DeploymentUpdates and Check Now for the latest PAN-OS releases.Select PanoramaManaged DevicesSummary and select one or more ZTP firewalls.Reassociate the selected ZTP firewall(s).Check (enable) Auto Push on 1st Connect.In the To SW Version column, select the target PAN-OS version for the ZTP firewall.Click OK to save your configuration changes.
![]() Select Commit and Commit to Panorama.Power on the ZTP firewall.When the ZTP firewall connects to Panorama for the first time, it automatically upgrades to the PAN-OS version you selected. If you are upgrading to a PAN-OS maintenance release, the base PAN-OS image is installed first before the target maintenance release is installed.For example, you configured the target To SW Version for the managed firewall as PAN-OS 10.1.5. On first connection to Panorama, PAN-OS 10.1.0 is installed on the managed firewall first. After PAN-OS 10.1.0 successfully installs, the firewall is automatically upgraded to the target PAN-OS 10.1.5 release.Verify the ZTP firewall software upgrade.
Select Commit and Commit to Panorama.Power on the ZTP firewall.When the ZTP firewall connects to Panorama for the first time, it automatically upgrades to the PAN-OS version you selected. If you are upgrading to a PAN-OS maintenance release, the base PAN-OS image is installed first before the target maintenance release is installed.For example, you configured the target To SW Version for the managed firewall as PAN-OS 10.1.5. On first connection to Panorama, PAN-OS 10.1.0 is installed on the managed firewall first. After PAN-OS 10.1.0 successfully installs, the firewall is automatically upgraded to the target PAN-OS 10.1.5 release.Verify the ZTP firewall software upgrade.- Log in to the Panorama Web Interface.Select PanoramaManaged DevicesSummary and navigate to the ZTP firewall(s).Verify the Software Version column displays the correct target PAN-OS release.For all future PAN-OS upgrades, see Upgrade Firewalls Using Panorama.