Next-Generation Firewall
Configure an SSH Service Profile
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Configure an SSH Service Profile
Create an SSH service profile to harden SSH connections to your management and HA
appliances.
SSH service profiles enable you to customize SSH parameters to enhance the
security and integrity of SSH connections to your Palo Alto Networks management and
high availability (HA) appliances. By default, SSH supports all ciphers, key
exchange algorithms, and message authentication codes, which leaves your connection
vulnerable to attack. In an SSH service profile, you can restrict the algorithms
your SSH server supports. You can also generate a new host key and specify data
volume, time, and packet-based thresholds for SSH session key regeneration and
exchange.
Depending on the SSH server instance, configure either a management
or HA SSH service profile. You can configure the profiles from your firewall,
Panorama™ web interface (if applying settings to multiple firewalls or appliances),
or CLI.
You can configure a maximum of four management and four HA
server profiles.
To use the same SSH connection settings for
each Dedicated Log Collector (M-series or Panorama virtual appliance in Log
Collector mode) in a Collector Group, configure an SSH
service profile from the Panorama management server,
Commit your changes to
Panorama, and then Push the configuration to the Log
Collectors. You can also perform these steps from the CLI using set
log-collector-group <name> general-setting management ssh
commands.
Create an SSH Management Profile
To customize SSH settings for management connections, create an SSH
management profile.
You can configure or update an existing
management profile from your CLI.
- Create a Management - Server Profile.
- Select DeviceCertification ManagementSSH Service Profile.Add a Management - Server Profile.
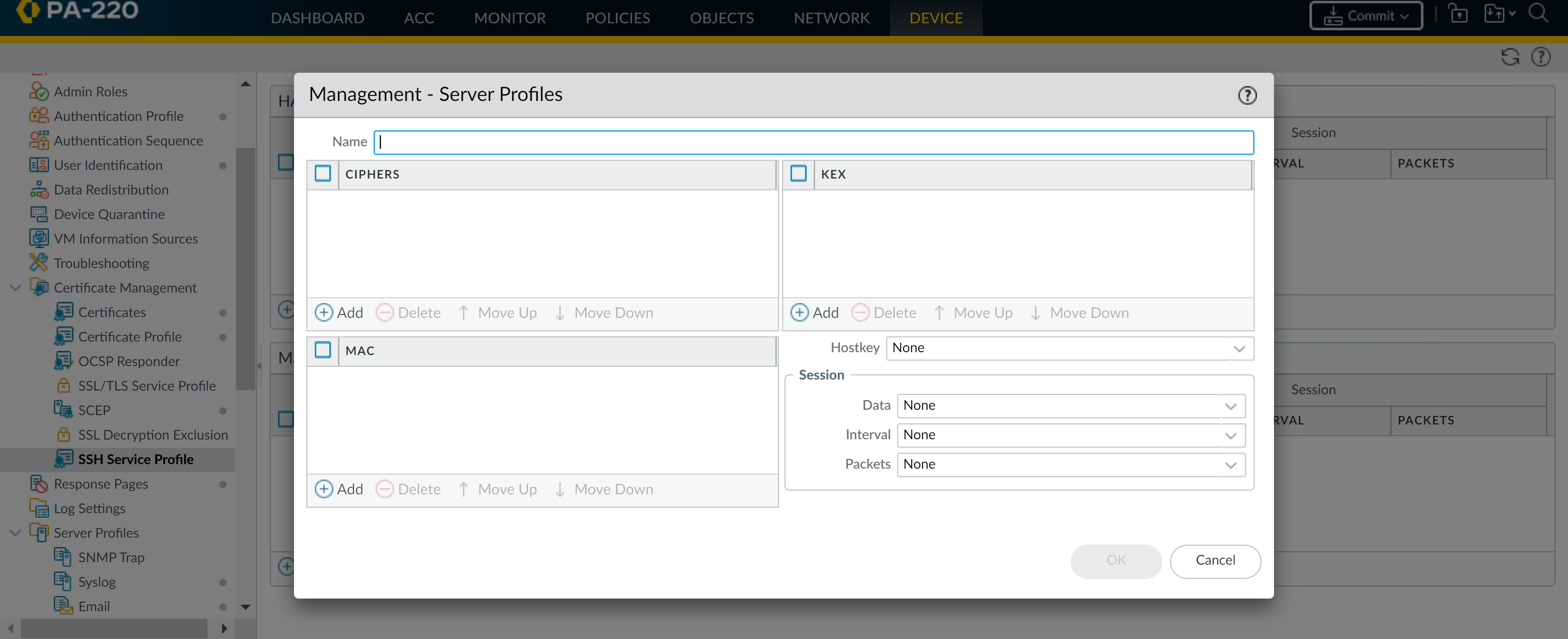
![]() Enter a Name to identify the profile.(Optional) Add the ciphers, message authentication codes, or key exchange algorithms the profile supports.(Optional) Select a Hostkey and key length.(Optional) Enter values for the SSH session rekey parameters: Data, Interval, and Packets.
Enter a Name to identify the profile.(Optional) Add the ciphers, message authentication codes, or key exchange algorithms the profile supports.(Optional) Select a Hostkey and key length.(Optional) Enter values for the SSH session rekey parameters: Data, Interval, and Packets.![]() Click OK and Commit your changes.Select a management profile to apply.
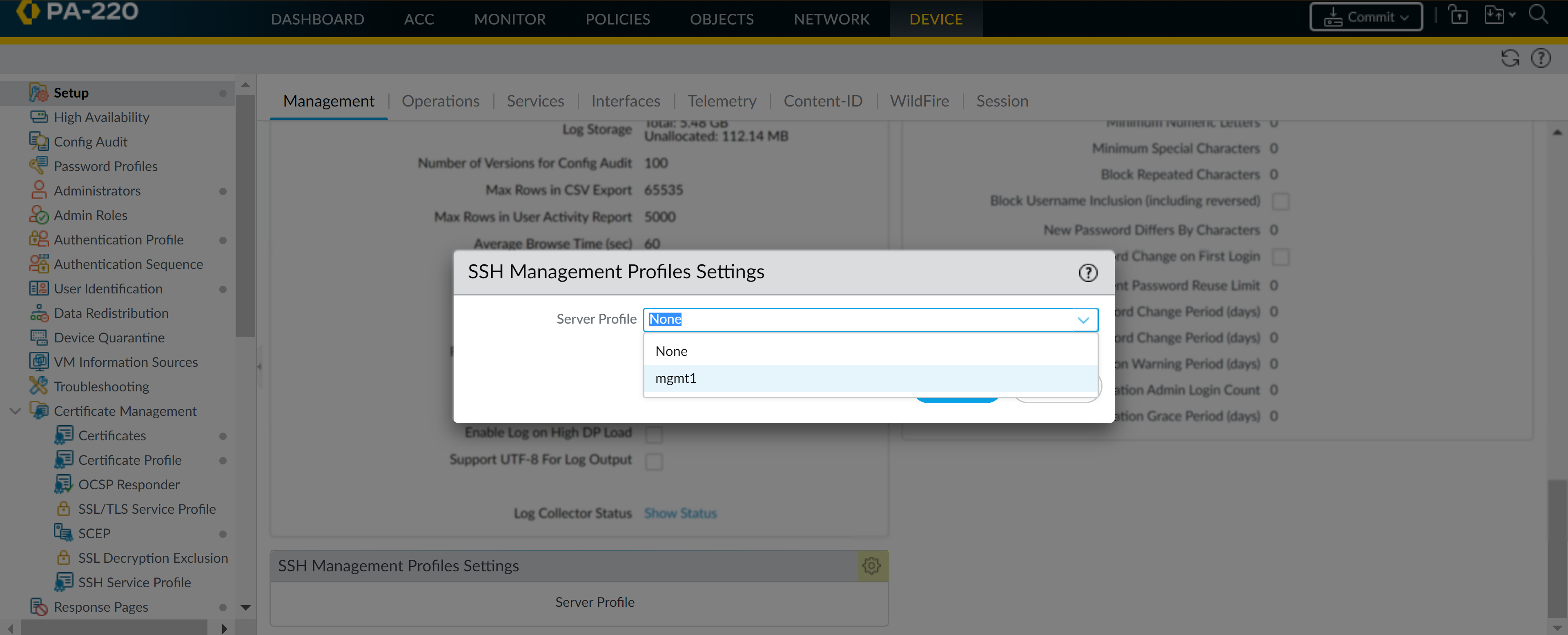
Click OK and Commit your changes.Select a management profile to apply.- Select DeviceSetupManagement.Under SSH Management Profiles Settings, select an existing profile.
![]() Click OK and Commit your changes.Restart management SSH service from the CLI to apply the profile.You need to restart the connection each time you apply a new profile or make changes to a profile in use. Configuration changes do not affect active sessions, and new profiles apply to subsequent connections (or sessions).Use the set ssh service-restart mgmt CLI command.
Click OK and Commit your changes.Restart management SSH service from the CLI to apply the profile.You need to restart the connection each time you apply a new profile or make changes to a profile in use. Configuration changes do not affect active sessions, and new profiles apply to subsequent connections (or sessions).Use the set ssh service-restart mgmt CLI command.Create an SSH HA Profile
To secure SSH communications between appliances in an HA pair, create an SSH HA profile. Before you create a profile, establish an HA connection between the HA peers. To establish an HA connection, you’ll need to enable encryption on the control link connection, export the HA key to a network location, and import the HA key on the peer. (See Configure Active/Passive HA or Configure Active/Active HA.)You can configure or update an existing HA profile from your CLI.- Create an HA Profile.
- Select DeviceCertification ManagementSSH Service Profile.Add an HA Profile.
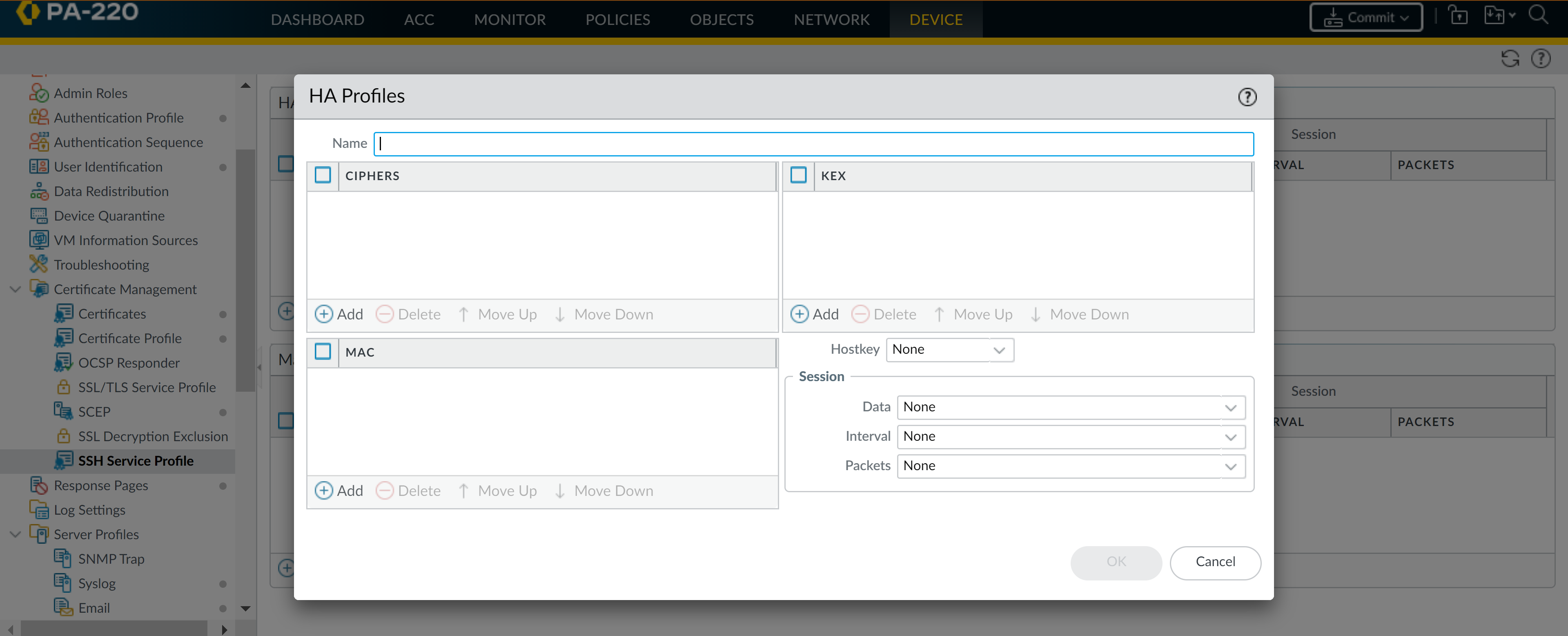
![]() Enter a Name to identify the profile.(Optional) Add the ciphers, message authentication codes, or key exchange algorithms the profile supports.(Optional) Select a Hostkey and key length.(Optional) Enter values for the SSH session rekey parameters: Data, Interval, and Packets.
Enter a Name to identify the profile.(Optional) Add the ciphers, message authentication codes, or key exchange algorithms the profile supports.(Optional) Select a Hostkey and key length.(Optional) Enter values for the SSH session rekey parameters: Data, Interval, and Packets.![]() Click OK and Commit your changes.Select an HA Profile to apply.
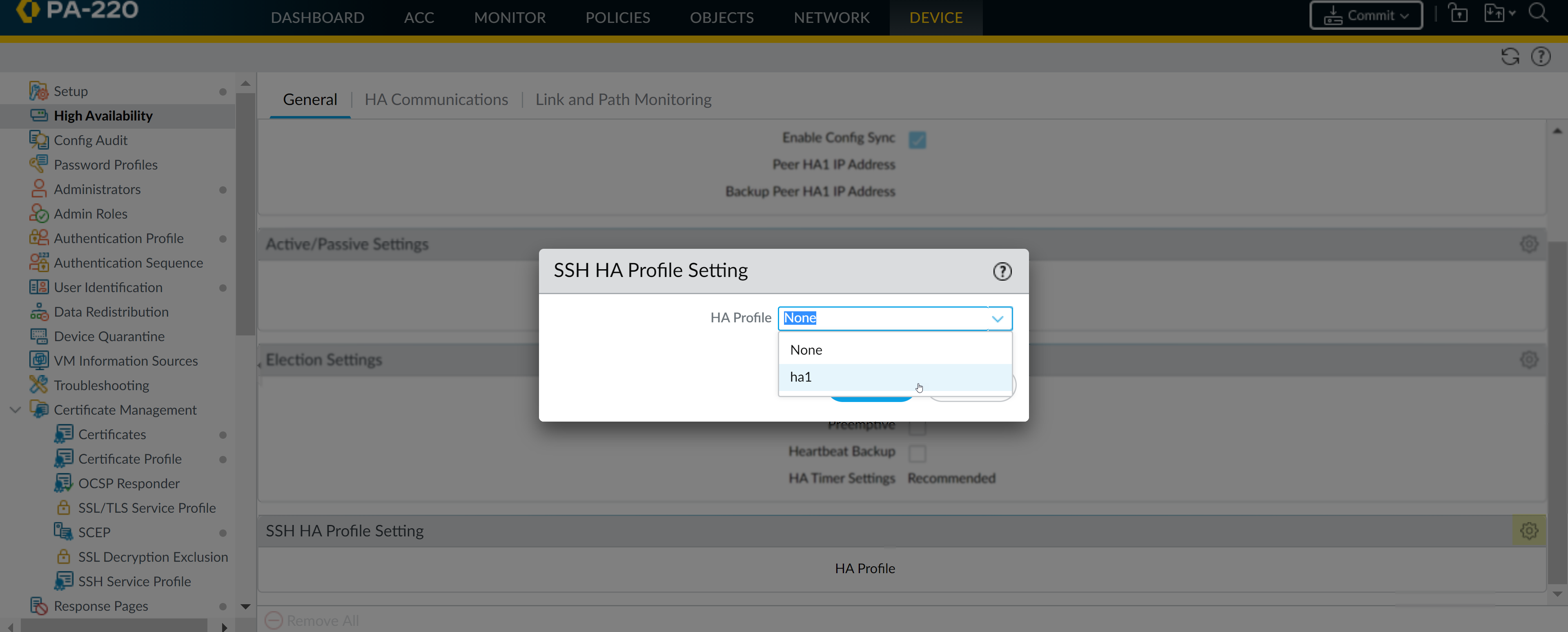
Click OK and Commit your changes.Select an HA Profile to apply.- Select DeviceHigh AvailabilityGeneral.Under SSH HA Profile Setting, select an existing profile.
![]() Click OK and Commit your changes.Restart HA1 SSH service from the CLI to apply the profile.You need to restart the connection each time you apply a new profile or make changes to a profile in use. Configuration changes do not affect active sessions, and new profiles apply to subsequent connections (or sessions).Use the set ssh service-restart ha CLI command.If a connection exists between the appliances in the HA pair, you can use the following commands to minimize the downtime that accompanies an SSH service restart.
Click OK and Commit your changes.Restart HA1 SSH service from the CLI to apply the profile.You need to restart the connection each time you apply a new profile or make changes to a profile in use. Configuration changes do not affect active sessions, and new profiles apply to subsequent connections (or sessions).Use the set ssh service-restart ha CLI command.If a connection exists between the appliances in the HA pair, you can use the following commands to minimize the downtime that accompanies an SSH service restart.- (HA1 Backup is configured) admin@PA-3260> request high-availability session-reestablish
- (No HA1 Backup is configured or HA1 Backup link is down) admin@PA-3260> request high-availability session-reestablish forceYou can force the firewall to reestablish HA1 sessions if there is no HA1 backup. However, this causes a brief split-brain condition, where the HA peers cannot detect each other and assume an active role as a result. (Using the force option when an HA1 backup is configured has no effect.)