Create Filters for the Advanced Routing Engine
Table of Contents
End-of-Life (EoL)
Create Filters for the Advanced Routing Engine
Create filters for an Advanced Routing Engine to filter
and redistribute routes.
The Advanced Routing Engine supports the filters
described in this topic. Access lists, prefix lists, and redistribution
route maps can apply to BGP, OSPFv2, OSPFv3 and RIPv2. Access lists
and prefix lists can also apply to IPv4 multicast. Multicast route
maps apply to IPv4 multicast. AS path access lists, community lists,
and BGP route maps apply to BGP only.
Create a filter and
reference the filter in a profile or other appropriate location
to easily and consistently apply settings that control such things
as route acceptance from peers into the local RIB, route advertisements
to peers, conditional advertisements, setting attributes, exporting
and importing routes to and from other routers, route aggregation,
and route redistribution.
- Access Lists—Use an
access list:
- To filter network routes based on IPv4/IPv6 source addresses and IPv4 destination addresses. For IPv4 access lists, source and destination addresses can be specified by an address and wildcard mask to express a range of addresses. IPv6 access lists can specify source addresses and subnet.
- In a BGP Filtering profile, specify an Inbound Distribute List (access list) to control which routes BGP will accept from a peer group or peer (neighbor). This means that routes matching a deny access list rule are not placed in the local BGP RIB; routes matching a permit access list rule are placed in the local BGP RIB. You apply the BGP Filtering profile to a BGP peer group or peer in the Filtering IPv4 Unicast or Filtering IPv6 Unicast field. (To do this for a peer, select Inherit No). Peer settings take precedence over peer group settings.
- In a BGP Filtering profile, specify an Outbound Distribute List (access list) to control which routes the firewall advertises to its peer group or peer, based on your network and BGP deployment. Then apply the BGP Filtering profile to a BGP peer group or peer in the Filtering IPv4 Unicast or Filtering IPv6 Unicast field. (To do this for a peer, select Inherit No). Peer settings take precedence over peer group settings.
- As match criteria in a Redistribution route map to specify IPv4 or IPv6 destination Addresses, Next Hop, or Route Source.
- In a BGP route map as match criteria for an IPv4 Address, Next Hop, or Route Source, and also for an IPv6 Address.
- In OSPFv2 and OSPFv3 Import Lists and Export Lists for an Area Border Router (ABR).
- To specify PIM group permissions for IPv4 multicast.
An access list is not for filtering user traffic or for providing security.An access list can have multiple rules; routes are evaluated against the rules in sequential order. When a route matches a rule, the deny or permit action occurs and the route is not evaluated against subsequent rules.The aggregated view displays all configured access lists; you can highlight an access list to then modify or delete it. - Prefix Lists—Use a prefix list:
- To filter network routes that are added to a local RIB based on route prefix and prefix length.
- In a BGP Filtering Profile, specify an Inbound Prefix List to control which routes BGP will accept from a peer group or peer (neighbor). This means that routes matching a deny prefix list rule are not placed in the local BGP RIB; routes matching a permit prefix list rule are placed in the local BGP RIB. Then apply the BGP Filtering profile to a BGP peer group in the Filtering IPv4 Unicast or Filtering IPv6 Unicast field. (To do this for a peer, select Inherit No). Peer settings take precedence over peer group settings.
- In a BGP Filtering profile, specify an Outbound Prefix List to control which routes the firewall advertises to its peer group or peer, based on your network and BGP deployment. Then apply the BGP Filtering profile to a BGP peer group or peer in the Filtering IPv4 Unicast or Filtering IPv6 Unicast field. (To do this for a peer, select Inherit No). Peer settings take precedence over peer group settings.
- As match criteria in a Redistribution route map to specify IPv4 or IPv6 destination Addresses, Next Hop, or Route Source.
- In a BGP route map as match criteria for an IPv4 Address, Next Hop, or Route Source, and also for an IPv6 Address.
- For an OSPFv2 or OSPFv3 ABR of an area, in an Inbound Filter List or Outbound Filter List.
- In an IPv4 Multicast PIM general configuration to specify an SPT threshold.
- In an IPv4 Multicast route map.
A prefix list can have multiple rules; routes are evaluated against the rules in sequential order. When a route matches a rule, the deny or permit action occurs and the route is not evaluated against subsequent rules. A prefix list is flexible in that it allows you to configure a prefix with a prefix length (that together identify the prefix), and also have a range by specifying that the prefix length be greater than, less than, or equal to a value. The firewall evaluates prefix lists more efficiently than access lists. - Redistribution Route Maps—Use a Redistribution Route
Map in a Redistribution Profile to specify which BGP, OSPFv2, OSPFv3,
RIP, connected or static routes (the source protocol) to redistribute
to BGP, OSPFv2, OSPFv3, RIP, or the local RIB (the destination protocol).
You can also redistribute BGP host routes to BGP peers. The match
criteria can include IPv4 and IPv6 addresses specified by an access
list and prefix list.A Redistribution route map can have multiple entries; routes are evaluated against the entries in sequential order. When a route matches an entry, it is permitted or denied and the route is not evaluated against subsequent entries. If the action of the matching entry is Permit, the firewall also sets the configured attributes from the route map to the redistributed route.
- Multicast Route Maps—Create a multicast route map to filter sources for a dynamic IGMP interface.
The following
filters apply to BGP only.
- AS Path Access Lists—Create
an AS Path access list:
- To control importing of BGP routes (into the local BGP RIB) that came from another router, use in a BGP Filtering Profile, in the Inbound Filter List. For example, you want to import only routes that came through specific autonomous systems.
- To control exporting of BGP routes to another router, use in a BGP Filtering Profile, in the Outbound Filter List.
- To do anything a BGP route map can do, use in a BGP route map as a match criterion.
- To redistribute BGP routes, use in a BGP Redistribution route map (AS Path) as a match criterion.
An AS Path access list can have a maximum of 64 rules and ends with an implicit Permit Any rule. Use an AS Path access list to deny autonomous systems. Routes are evaluated against the rules in sequential order. When a route matches a rule, the deny or permit action occurs and the route is not evaluated against subsequent rules. - Community Lists—Create a community list:
- To reference in a BGP route map to match on BGP community attributes of routes that you want to control in some way. For example, you can set a group of routes (that share a community attribute) to have a specific metric or local preference.
- To reference in the set actions of a BGP route map to remove communities from routes that meet the match criteria.
- To match BGP communities in routes that you want to redistribute using a Redistribution route map.
A community list can have multiple rules; routes are evaluated against the rules in sequential order. When a route matches a rule, the deny or permit action occurs and the route is not evaluated against subsequent rules. - BGP Route Maps—Create a BGP route map:
- For the Default Originate Route-Map field of a BGP AFI Profile; the match criteria define when to generate the default route (0.0.0.0). Apply the BGP AFI profile to a BGP peer group or peer. The Match criteria can be any parameter and if there is a match to an existing BGP route, the default route is created; the Set portion of the route map is not used. Instead, you can use an outbound route-map to set properties for the generated default route.
- To set (override) BGP attributes that BGP is sending to a peer.
- For NAT, to set Source Address and IPv4 Next Hop for a certain group of prefixes you are advertising, enter a public IP address from the NAT pool to replace a private IP address.
- To redistribute static, connected, or OSPF routes into BGP; then reference the BGP route map in a BGP Redistribution profile.
- In a BGP Filtering Profile, use a BGP route map in Inbound Route Map or Outbound Route Map to filter routes that are accepted (learned) from BGP peers into the local BGP RIB (inbound) or advertised to BGP peers (outbound).
- To conditionally advertise BGP routes, in a BGP Filtering Profile, create an Exist Map, which specifies that if these conditions in the route exist, advertise the route based on an Advertise Map. Alternatively, specify that if these conditions do not exist, advertise the route based on a Non-Exist Advertise Map.
- In a BGP Filtering Profile, set an IPv4 Next Hop to use a public NAT address rather than a private address.
- In a BGP Filtering Profile, use a BGP route map to unsuppress routes that were suppressed due to route dampening or aggregation.
- To conditionally filter more specific routes, for a logical router, configure BGP Aggregate Routes and provide the Suppress Map.
- To set attributes for an aggregate route, for a logical router, configure BGP Aggregate Routes and provide the Attribute Map.
A
filter can have multiple rules; the firewall evaluates packets or
routes against the rules in a filter in order by sequence number
(Seq) of the rule. When a packet or route
matches a rule, the deny or permit action occurs and the packet
or route is not evaluated against subsequent rules.
All filters except AS Path access lists end
with an implicit Deny Any rule. All filters
except for AS Path access lists must have at least one Permit rule;
otherwise, all examined routes/packets are denied. AS Path access
lists end with an implicit Permit Any rule.
Select
a configured Seq number to open a rule and
modify it. Select an Action field in a configured
rule to modify only the Permit or Deny action.
When adding a rule, leave enough unused
sequence numbers between rules to allow future rules to be inserted
in the filter. For example, use Seq numbers 10, 20, 30, etc.
- Create an access list to permit or deny IPv4 or IPv6 addresses where this filter is applied.
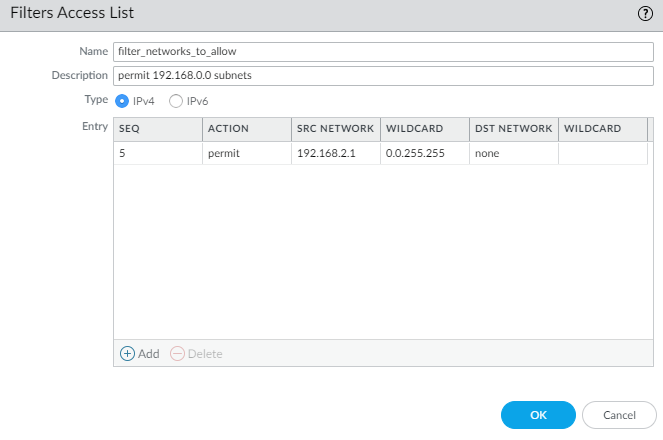
- Select NetworkRoutingRouting ProfilesFilters.Add a Filters Access List by Name (maximum of 63 characters). The name must start with an alphanumeric character, underscore (_), or hyphen (-), and can contain a combination of alphanumeric characters, underscore, or hyphen. No dot (.) or space is allowed.Enter a helpful Description.Select the Type of access list: IPv4 or IPv6.
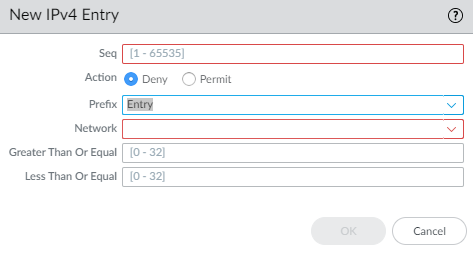
- For IPv4, Add an IPv4 Entry and enter the Seq number for the rule (range is 1 to 65,535).
- Select the Action: Deny (the default) or Permit.
- For Source Address, there are three options: select Address and in the subsequent Address field, enter an IPv4 address. Enter a Wildcard mask to indicate a range. A zero (0) in the mask indicates that bit must match the corresponding bit in the address; a one (1) in the mask indicates a “don’t care” bit. The other options are Any orNone.
- For Destination Address, select Address and in the subsequent Address field, enter an IPv4 address. Enter a Wildcard. A zero (0) in the mask indicates a bit that must match; a one (1) in the mask indicates a “don’t care’ bit. The other options are Any or None.
- Click OK to save the entry.
![]() Alternatively, select the Type to be IPv6.
Alternatively, select the Type to be IPv6.- For IPv6, Add an IPv6 Entry and enter the Seq number (range is 1 to 65,535).
- Select the Action: Deny (the default) or Permit.
- For Source Address, there are three options: select Address and in the subsequent Address field, enter an IPv6 Address. Optionally select Exact Match of this address to have the firewall perform a comparison of both the prefix and prefix length and they must match exactly; otherwise, the firewall determines the match comparison based on whether the route is in the same subnet as the configured prefix. (If the Source Address is Any or None, you cannot select Exact Match of this address.) The other options are Any or None.
- Click OK to save the entry. Optionally add more entries.
![]() Click OK to save the access list.Create a prefix list.
Click OK to save the access list.Create a prefix list.- Select NetworkRoutingRouting ProfilesFilters.Add a Filters Prefix List by Name (maximum of 63 characters). The name must start with an alphanumeric character, underscore (_), or hyphen (-), and can contain a combination of alphanumeric characters, underscore, or hyphen. No dot (.) or space is allowed.Enter a helpful Description.Select the Type of prefix for this rule to filter: IPv4 or IPv6.
![]()
- For IPv4, Add an IPv4 Entry, and enter the Seq number for the rule; range is 1 to 65,535.
- Select the Action: Deny (the default) or Permit.
- For Prefix, there are three options; default is None. Another option is to select Network any. The third option is to select Entry and enter an IPv4 Network prefix with slash and a base prefix length that together specify a network, for example, 192.168.2.0/24. Optionally specify that the prefix length be Greater Than Or Equal to a number (that is at least as large as the base length you specified; range is 0 to 32). Optionally specify a top limit to the range by specifying Less Than Or Equal to a number (that is at least as high as the base length and at least as high as the Greater Than Or Equal length if configured; range is 0 to 32).
![]() Comparing a route to the prefix rule (IPv4 or IPv6) is a two-step process: 1) Match the prefix with the network first. 2) Match the prefix length to the mask range (Greater Than or Equal to Less Than Or Equal). For example, consider the preflix list rule with Network 192.168.3.0/24, and a prefix length Greater Than or Equal to 26 and Less Than or Equal to 30. The following table shows routes that are tested and whether they pass or fail the rule. Routes that pass the rule are subject to the configured action (Deny or Permit).Sample RouteResult192.168.3.0/28Pass: the network and prefix length match the rule.192.168.2.0/30Fail: network does not match the rule.192.168.3.0/32Fail: prefix length does not match the rule.In the output summary of the rule, LOU is Logical Operator Unit (equal, greater or equal, less or equal). >= indicates a prefix length greater than or equal to the value; it is the lowest value of a range of the prefix length. <= indicates a prefix length less than or equal to the value; it is the highest value of a range of the prefix length.Alternatively, Add an IPv6 Entry and follow the steps similar to those for an IPv4 prefix rule. The range of the IPv6 prefix length is Greater Than or Equal to 0 to 128 and Less Than Or Equal to 0 to 128.For example, consider the prefix list rule with Network 2001:db8:1/48, and a prefix length Greater Than or Equal to 56 and Less Than or Equal to 64. The following table shows routes that are tested and whether they pass or fail the rule. Routes that pass the rule are subject to the configured action (Deny or Permit).Sample RouteResult2001:db8:1/64Pass: the network and prefix length match the rule.2001:db8:2/48Fail: network does not match the rule.2001:db8:1/65Fail: prefix length does not match the rule.Click OK to save the prefix entry. Optionally add more entries.Click OK to save the Prefix List.Create an AS Path Access List for BGP.
Comparing a route to the prefix rule (IPv4 or IPv6) is a two-step process: 1) Match the prefix with the network first. 2) Match the prefix length to the mask range (Greater Than or Equal to Less Than Or Equal). For example, consider the preflix list rule with Network 192.168.3.0/24, and a prefix length Greater Than or Equal to 26 and Less Than or Equal to 30. The following table shows routes that are tested and whether they pass or fail the rule. Routes that pass the rule are subject to the configured action (Deny or Permit).Sample RouteResult192.168.3.0/28Pass: the network and prefix length match the rule.192.168.2.0/30Fail: network does not match the rule.192.168.3.0/32Fail: prefix length does not match the rule.In the output summary of the rule, LOU is Logical Operator Unit (equal, greater or equal, less or equal). >= indicates a prefix length greater than or equal to the value; it is the lowest value of a range of the prefix length. <= indicates a prefix length less than or equal to the value; it is the highest value of a range of the prefix length.Alternatively, Add an IPv6 Entry and follow the steps similar to those for an IPv4 prefix rule. The range of the IPv6 prefix length is Greater Than or Equal to 0 to 128 and Less Than Or Equal to 0 to 128.For example, consider the prefix list rule with Network 2001:db8:1/48, and a prefix length Greater Than or Equal to 56 and Less Than or Equal to 64. The following table shows routes that are tested and whether they pass or fail the rule. Routes that pass the rule are subject to the configured action (Deny or Permit).Sample RouteResult2001:db8:1/64Pass: the network and prefix length match the rule.2001:db8:2/48Fail: network does not match the rule.2001:db8:1/65Fail: prefix length does not match the rule.Click OK to save the prefix entry. Optionally add more entries.Click OK to save the Prefix List.Create an AS Path Access List for BGP.- Select NetworkRoutingRouting ProfilesFilters.Add an AS Path Acess List by Name (maximum of 63 characters). The name must start with an alphanumeric character, underscore (_), or hyphen (-), and can contain a combination of alphanumeric characters, underscore, or hyphen. No dot (.) or space is allowed.Enter a helpful Description.Add an Entry and enter a Seq number; range is 1 to 65,535.Select the Action: Deny (the default) or Permit.Each AS Path access list ends with an implicit Permit Any rule. Use an AS Path access list to deny autonomous systems.Enter the Aspath Regex (regular expression) in the format regex1:regex2:regex3, where a colon (:) separates three AS values. Characters allowed are 1234567890_^|[,{}()]$*+.?-\. For example, .*65000 in a Deny statement excludes prefixes originating from AS 65000.
![]() Click OK to save the entry. Optionally add more entries; a maximum of 64 entries are allowed in an AS Path access list.Click OK to save the AS Path access list.Create a Community List.
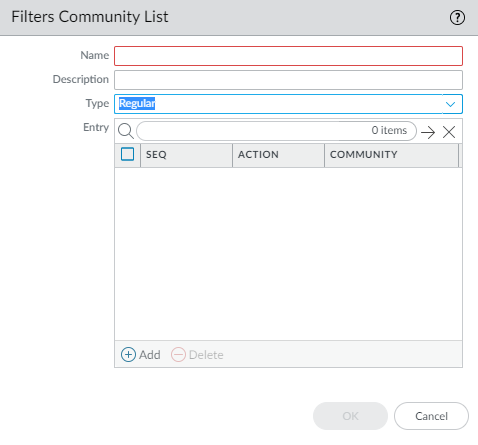
Click OK to save the entry. Optionally add more entries; a maximum of 64 entries are allowed in an AS Path access list.Click OK to save the AS Path access list.Create a Community List.- Select NetworkRoutingRouting ProfilesFilters.Add a Filters Community List by Name (maximum of 63 characters). The name must start with an alphanumeric character, underscore (_), or hyphen (-), and can contain a combination of alphanumeric characters, underscore, or hyphen. No dot (.) or space is allowed.Enter a helpful Description.
![]() Select the Type:
Select the Type:- Regular—Add a Seq number
(range is 1 to 65,535), select the Action: Deny (the default)
or Permit, and Add one
or more community values, select one or more well-known communities,
or enter a combination of community values and well-known communities. Separate
multiple communities with a vertical bar (|), for example, 6409:10|6520:13|internet.
Enter a maximum of 16 communities in a Regular entry
(rule).
- A regular community value in the format AA:NN where AA is an AS number and NN is a network number (each with a range of 0 to 65,535).
- accept-own—Represents well-known community value ACCEPT-OWN (0xFFFF0001)
- blackhole—Represents well-known community value BLACKHOLE (0xFFFF029A). The neighboring network should discard traffic destined for the prefix.
- graceful-shutdown—Represents well-known community value GRACEFUL_SHUTDOWN (0xFFFF0000)
- internet—Represents well-known community value 0 (0x00). Advertise a prefix to all BGP neighbors.
- local-as—Represents well-known community value NO_EXPORT_SUBCONFED (0xFFFFFF03). The effect is to not advertise the prefix outside of the sub-AS in a confederation.
- no-advertise—Represents well-known community value NO_ADVERTISE (0xFFFFFF02). Adding this community to a prefix means the receiving BGP peer will place the prefix in its BGP route table, but won’t advertise the prefix to other neighbors.
- no-export—Represents well-known community value NO_EXPORT (0xFFFFFF01).Adding this community to a prefix means the receiving BGP peer will advertise the prefix only to iBGP neighbors, not neighbors outside the AS.
- no-peer—Represents well-known community value NOPEER (0xFFFFFF04).
- route-filter-v4—Represents well-known community value ROUTE_FILTER_v4 (0xFFFF0003).
- route-filter-v6—Represents well-known community value ROUTE_FILTER_v6 (0xFFFF0005).
![]()
- Large—Add a Seq number
(range is 1 to 65,535), select the Action: Deny (the
default) or Permit, and Add a
large community regular expression (LC REGEX) entry. Characters
allowed in an entry are 1234567890_^|[,{}()]$*+.?-\. Each community
must be in the format regex1:regex2:regex3;
for example, 203[1-2]:205[2-5]:206[5-6].
Enter a maximum of eight communities in a Large entry
(rule).
![]()
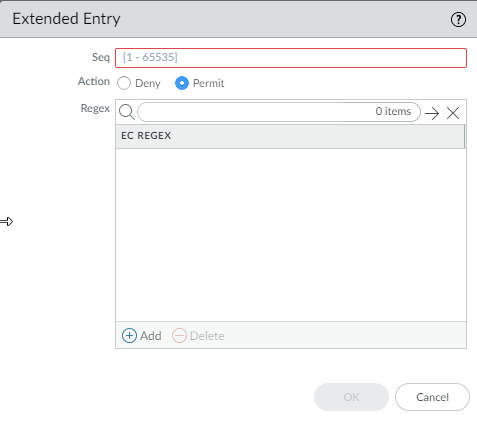
- Extended—Add a Seq number
(range is 1 to 65,535), select the Action: Deny (the
default) or Permit, and Add the BGP extended community regular expression
(EC REGEX). Characters allowed are 1234567890_^|[,{}()]$*+.?-\.
Each extended community must be in the format regex1:regex2;
for example, 204*[3-8]:205*[4-8]. Enter a
maximum of eight communities in an Extended entry
(rule).
![]()
Click OK to save the entry in the Community List. Optionally add more entries of the same type (Regular, Large, or Extended).Click OK to save the Community List.Create a BGP route map.- Select NetworkRoutingRouting ProfilesFilters.Add a Filters Route Maps BGP by Name (maximum of 63 characters). The name must start with an alphanumeric character, underscore (_), or hyphen (-), and can contain a combination of alphanumeric characters, underscore, or hyphen. No dot (.) or space is allowed.Enter a helpful Description of the route map.
![]() Add a route map and on the Entry tab, assign a Seq number; range is 1 to 65,535.Assign sequence numbers that are five or more numbers apart so you have unused numbers for which to insert additional entries in the future.Enter a helpful Description of the entry (rule).For Action, select Deny or Permit.On the Match tab, specify the criteria that determine which routes are subject to the function that uses this route map. Multiple attributes are logically ANDed, meaning all criteria must be met.
Add a route map and on the Entry tab, assign a Seq number; range is 1 to 65,535.Assign sequence numbers that are five or more numbers apart so you have unused numbers for which to insert additional entries in the future.Enter a helpful Description of the entry (rule).For Action, select Deny or Permit.On the Match tab, specify the criteria that determine which routes are subject to the function that uses this route map. Multiple attributes are logically ANDed, meaning all criteria must be met.![]()
- AS Path Access List—Select an AS path list. Default is None.
- Regular Community—Select a Community list. Default is None.
- Large Community—Select a Large Community list. Default is None.
- Extended Community—Select an Extended Community list. Default is None.
- Metric—Enter a value in the range 0 to 4,294,967,295.
- Interface—Select a local interface from the list of all interfaces for all logical routers. Make sure to choose an interface that belongs to the logical router you are configuring. Default is None. At commit, the firewall checks that the interface you chose belongs to the logical router you are configuring.
- Origin—Select the origin of the route: ebgp, ibgp, or incomplete. Default is none.
- Tag—Enter a tag value that has meaning in your networks, in the range 0 to 4,294,967,295.
- Local Preference—Enter a value in the range 0 to 4,294,967,295.
- Peer—Select a peer name or local (Static or Redistributed routes). Default is none.
Select IPv4 or IPv6 to match on various types of addresses. If you select IPv4:- On the Address tab, select an Access List to specify addresses to match.
- Select a Prefix List to specify addresses
to match. It matches the prefix received from a peer or a prefix
redistributed to protocol from another protocol.If both an access list and prefix list are specified, both requirements must be met (logical AND).
- On the Next Hop tab, select an Access List to specify next hop addresses to match.
- Select a Prefix List to specify next hop addresses to match.
- On the Route Source tab, select an Access List to specify a source IP address of a route to match. For example, the access list could permit a distant peer with the address 192.168.2.2 who is advertising a route to a certain prefix. You can make this BGP route map match on the route’s source address 192.168.2.2 and then perhaps filter the route based on matching the peer address 192.168.2.2 as the source of the route, or set a next hop for routes matching that route source.
- Specify a Prefix List to specify one or more source network prefixes to match.
If you select IPv6:- On the Address tab, select an Access List to specify addresses to match.
- Select a Prefix List to specify addresses to match.
- On the Next Hop tab, select an Access List to specify next hop addresses to match.
Set any of the following attributes for routes that meet the match criteria:![]()
- Enable BGP atomic aggregate—Mark the route as a less specific route because it has been aggregated. ATOMIC_AGGREGATE is a well-known discretionary attribute that alerts BGP speakers along a path that information has been lost due to route aggregation, and therefore the aggregate path might not be the best path to the destination. When some router are aggregated by an aggregator, the aggregator attaches its Router-ID to the aggregated route into the AGGREGATOR-ID attribute and it sets the ATOMIC_AGGREGATE attribute or not, based on whether the AS_PATH information from the aggregated routers was preserved.
- Aggregator AS—Enter the Aggregator AS. The Aggregator attribute includes the AS number and the IP address of the router that originated the aggregated route.The IP address is the Router ID of the router that performs the route aggregation.
- Router ID—Enter the aggregator’s Router ID (usually a loopback address).
- Local Preference—Enter the local preference to which matching routes are set; range is 0 to 4,294,967,295. IBGP Update packets carry local preference, which is advertised to IBGP peers only. When there are multiple routes to another AS, the firewall prefers the highest local preference.
- Tag—Set a tag; range is 1 to 4,294,967,295.
- Metric Action—Select an action: set, add, or subtract. You can set the specified Metric Value, or add the specified Metric Value to the matching route’s original metric value, or subtract the specified Metric Value from the matching route’s original metric value; default is set. Select the add or subtract action to adjust a metric and thus prioritize or deprioritize the matching route.
- Metric Value—Enter the metric value to set matching routes to, or add to, or subtract from the original metric value; range is 0 to 4,294,967,295.
- Weight—Set a weight (applied locally; not propagated); range is 0 to 4,294,967,295.
- Origin—Set the origin of the matching routes: ebgp, ibgp, or incomplete (unclear how the route came to be added to the RIB).
- Originator ID—Set the IP address of the originator of the matching routes.
- Delete Regular Community—Select a regular community to delete. Default is None.
- Delete Large Community—Select a large community to delete. Default is None.
- Select IPv4 or IPv6 as the AFI.
- On the IPv4 tab, select a Source Address to set from the list of all source addresses from all logical routers or select None. At commit, the firewall checks that the source address you chose belongs to the logical router you are configuring.
- Select an IPv4 Next-Hop to set: none, peer-address (Use Peer Address), or unchanged.
- On the IPv6 tab, select IPv6 Nexthop Prefer Global Address to prefer the global unicast address over the other IPv6 address types (link-local address, anycast address, or multicast address) for next hop. (By default, connected peers prefer a link-local next hop address over a global next hop address.)
- On the IPv6 tab, select a Source Address to set from the list of all source addresses from all logical routers or select None. At commit, the firewall checks that the source address you chose belongs to the logical router you are configuring.
- Select an IPv6 Next-Hop to set: none or peer-address (Use Peer Address).
- In the AS Path window, Add up to four AS paths to Exclude from the AS path of matching routes, perhaps to remove an AS from a confederation.
- Add up to four AS Paths to Prepend to the AS Path of matching route(s) (to make the route in an advertisement less desirable).
- In the Regular Community window, select Overwrite Regular Community to overwrite the regular community.
- Add a Regular Community to add one or more regular communities.
- In the Large Community window, select Overwrite Large Community to overwrite the large community.
- Add a Large Community to add one or more large communities.
- In the Regular Community window, select Overwrite Regular Community to overwrite the regular community.
- Add a Regular Community to add one or more regular communities.
- In the Large Community window, select Overwrite Large Community to overwrite the large community.
- Add a Large Community to add one or more large communities.
Click OK to save the route map entry. Optionally add more entries.Click OK to save the BGP route map.Create a Redistribution Route Map.- Select NetworkRoutingRouting ProfilesFilters.Add a Filters Route Maps Redistribution by Name (maximum of 63 characters). The name must start with an alphanumeric character, underscore (_), or hyphen (-), and can contain a combination of alphanumeric characters, underscore, or hyphen. No dot (.) or space is allowed.Enter a helpful Description.To redistribute from a Source Protocol, select BGP, OSPF, OSPFv3, RIP, or Connected Static. The source protocol is where the Match selections apply.To redistribute the routes to a Destination Protocol or local RIB, select BGP, OSPF, OSPFv3, RIP, or Rib. The destination protocol is where the Set selections apply. The Destination Protocols available in the dropdown depend on the Source Protocol selected. (This step shows an example of BGP redistributed to OSPF.)
![]() Add an Entry and enter the Seq number (range is 1 to 65,535).Enter a helpful Description.Select the Action: Deny or Permit.Select the Match tab to configure criteria for the source protocol; this example specifies BGP attributes to match.
Add an Entry and enter the Seq number (range is 1 to 65,535).Enter a helpful Description.Select the Action: Deny or Permit.Select the Match tab to configure criteria for the source protocol; this example specifies BGP attributes to match.![]() Select an AS Path Access List; default is None.Select a Regular Community; default is None.Select a Large Community; default is None.Select an Extended Community; default is None.Enter a Metric; range is 0 to 4,294,967,295.Select an Interface; default is None.Select the Origin of the route: ebgp, ibgp, or incomplete; default is none.Enter a Tag; range is 1 to 4,294,967,295.Enter a Local Preference; range is 0 to 4,294,967,295.Select a Peer name or local (Static or Redistributed routes); default is none.The Address tab refers to the Destination address in a route. Select an Access List to specify routes with a destination address that must match in order to be redistributed. Default is None.Select a Prefix List to specify routes with a destination address that must match in order to be redistributed. Default is None.Select the Set tab to configure actions to perform on routes matching this rule, which will be redistributed to the destination protocol. (In this example, the destination protocol is OSPF.)
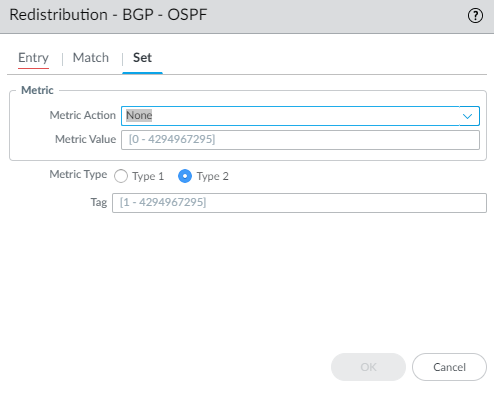
Select an AS Path Access List; default is None.Select a Regular Community; default is None.Select a Large Community; default is None.Select an Extended Community; default is None.Enter a Metric; range is 0 to 4,294,967,295.Select an Interface; default is None.Select the Origin of the route: ebgp, ibgp, or incomplete; default is none.Enter a Tag; range is 1 to 4,294,967,295.Enter a Local Preference; range is 0 to 4,294,967,295.Select a Peer name or local (Static or Redistributed routes); default is none.The Address tab refers to the Destination address in a route. Select an Access List to specify routes with a destination address that must match in order to be redistributed. Default is None.Select a Prefix List to specify routes with a destination address that must match in order to be redistributed. Default is None.Select the Set tab to configure actions to perform on routes matching this rule, which will be redistributed to the destination protocol. (In this example, the destination protocol is OSPF.)![]() Select the Metric Action for the redistribution rule: you can set the Metric value, add the specified Metric Value to the matching route’s original Metric value, or subtract the specified Metric Value from the matching route’s original Metric value; default is None. Select the add or subtract action to adjust a metric and thus prioritize or deprioritize the matching route.For example, you can put the metric of an IGP into BGP by using redistribution. The metric is dynamic, and you can simply add to its value rather than set it to an absolute number.Enter a Metric Value to set, add to, or subtract from the metric; range is 0 to 4,294,967,295.Select the Metric Type: Type 1 or Type 2 (because this example uses OSPF as the destination protocol).Specify a Tag; range is 1 to 4,294,967,295.Click OK to save the rule. Optionally add more rules.Click OK to save the Redistribution route map.
Select the Metric Action for the redistribution rule: you can set the Metric value, add the specified Metric Value to the matching route’s original Metric value, or subtract the specified Metric Value from the matching route’s original Metric value; default is None. Select the add or subtract action to adjust a metric and thus prioritize or deprioritize the matching route.For example, you can put the metric of an IGP into BGP by using redistribution. The metric is dynamic, and you can simply add to its value rather than set it to an absolute number.Enter a Metric Value to set, add to, or subtract from the metric; range is 0 to 4,294,967,295.Select the Metric Type: Type 1 or Type 2 (because this example uses OSPF as the destination protocol).Specify a Tag; range is 1 to 4,294,967,295.Click OK to save the rule. Optionally add more rules.Click OK to save the Redistribution route map.