Next-Generation Firewall
Configure Service Routes
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Configure Service Routes
Configure service routes to change the interface the firewall uses to send requests
to external services or for log forwarding.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of these licenses for Strata Cloud Manager managed NGFWs:
|
The firewall uses the management (MGT) interface by default to access
external services, such as DNS servers, external authentication servers, Palo Alto
Networks® services such as software, URL updates, licenses and
AutoFocus. An alternative to using the MGT interface is to configure a data port (a
regular interface) to access these services. The path from the interface to the
service on a server is known as a service route. The service packets
exit the firewall on the port assigned for the external service and the server sends
its response to the configured source interface and source IP address.
You can configure service routes globally for the firewall or customize service routes for a virtual
system on a firewall enabled for multiple virtual systems so that you
have the flexibility to use interfaces associated with a virtual system. Any virtual
system that does not have a service route configured for a particular service
inherits the interface and IP address that are set globally for that service.
The following procedure enables you to configure service routes to change the
interface that the firewall uses to send requests to external services such as the
Palo Alto Network cloud services or for log forwarding. For firewalls in a high availability (HA) configuration, the
service route configuration is synchronized across the HA peers
For firewalls in an active/passive high availability (HA), the
service route you configured to leverage an external service or for log forwarding
sees activity only on the active HA peer while the
passive HA peer sees no activity if you configured
an Ethernet interface as the Source Interface. For example,
you configure a service route with Ethernet 1/3 as the source interface to forward
logs to Strata Logging Service. In this scenario, all logs are forwarded from
the active HA peer but no logs, including the system
and configuration logs, are forwarded from the passive
HA peer. However, if you configure the MGT interface as the service route
Source Interface, activity occurs on both the
active and passive HA
peers.
Configure Service Routes (PAN-OS)
Procedure for configuring service routes in PAN-OS & Panorama.
- Configure service routes.
- Select DeviceSetupServicesGlobal (omit Global on a firewall without multiple virtual system capability), and in the Services Features section, click Service Route Configuration.
![]() To force all firewall service communication with external servers through the management (MGT) interface, select Use Management Interface for all and click OK.When a service request originates from a firewall that has IPv6 enabled and has both IPv4 and IPv6 configured, the firewall behaves as a dual-stack host. Consequently, if the DNS resolution returns an IPv6 address as the first result, the firewall attempts to use that as the destination address.Additionally, in cases where the management interface is configured with only an IPv4 address and lacks a valid IPv6 configuration, if the DNS resolution returns an IPv6 address as the first result, the firewall doesn't Use Management Interface for all (which would be an IPv4 address). The firewall instead uses a dataplane IPv6 interface address as the source for the service request. Thus the service route has an IPv6 address at each end of the route.As an alternative to using the MGT interface, select Customize and do one of the following to create a service route:
To force all firewall service communication with external servers through the management (MGT) interface, select Use Management Interface for all and click OK.When a service request originates from a firewall that has IPv6 enabled and has both IPv4 and IPv6 configured, the firewall behaves as a dual-stack host. Consequently, if the DNS resolution returns an IPv6 address as the first result, the firewall attempts to use that as the destination address.Additionally, in cases where the management interface is configured with only an IPv4 address and lacks a valid IPv6 configuration, if the DNS resolution returns an IPv6 address as the first result, the firewall doesn't Use Management Interface for all (which would be an IPv4 address). The firewall instead uses a dataplane IPv6 interface address as the source for the service request. Thus the service route has an IPv6 address at each end of the route.As an alternative to using the MGT interface, select Customize and do one of the following to create a service route:- For a predefined service:
- Select IPv4 or IPv6 and click the link for the service for which you want customize the service route.To easily use the same source address for multiple services, select the checkbox for the services, click Set Selected Routes, and proceed to the next step.
- To limit the list for Source Address, select a Source Interface; then select a Source Address (from that interface) as the service route. An Address Object can also be referenced as a Source Address if it is already configured on the selected interface. Selecting Any Source Interface makes all IP addresses on all interfaces available in the Source Address list from which you select an address. Selecting Use default causes the firewall to use the management interface for the service route, unless the packet destination IP address matches the configured Destination IP address, in which case the source IP address is set to the Source Address configured for the Destination. Selecting MGT causes the firewall to use the MGT interface for the service route, regardless of any destination service route.The Service Route Source Address does not inherit configuration changes from the referenced interface and vice versa. Modification of an Interface IP Address to a different IP address or Address Object will not update a corresponding Service Route Source Address. This may lead to commit failure and require you to update the Service Route(s) to a valid Source Address value.
- Click OK to save the setting.
- Repeat this step if you want to specify both an IPv4 and IPv6 address for a service.
- For a destination service route:
- Select Destination and Add a Destination IP address. In this case, if a packet arrives with a destination IP address that matches this configured Destination address, then the source IP address of the packet will be set to the Source Address configured in the next step.
- To limit the list for Source Address, select a Source Interface; then select a Source Address (from that interface) as the service route. Selecting Any Source Interface makes all IP addresses on all interfaces available in the Source Address list from which you select an address. Selecting MGT causes the firewall to use the MGT interface for the service route.
- Click OK to save the setting.
Repeat the prior steps for each service route you want to customize.Click OK to save the service route configuration.Commit.Configure Service Routes (SCM)
Procedure for configuring service routes in Strata Cloud Manager.- Log in to Strata Cloud Manager.Configure an interface to use for the service route.
- (PA-5200 Series Firewalls only) Configure the Auxiliary Interface Settings
Select ManageConfigurationNGFW and Prisma AccessDevice SettingsDevice SetupManagementConfigurationNGFW and Prisma AccessDevice SettingsDevice SetupManagement and select the Configuration Scope where you want to create the service route.You can select a folder or firewall from your Folders or select Snippets to configure the service route in a snippet.Config Service Route.If you have already configured service routes for some services, the Service Route Settings is labeled as Customized.Configure a service route.- Select Customize.If you have already configured service routes, you can quickly configure all services to Use Management Interface for all to restore the default service routes for all services.Configure the service route for a service.
- For a Predefined Service
- Select IPv4 or IPv6 and click the Service name for which you want to customize the service route.
- Select the Source Interface.Select Any to make all IP addresses on all interfaces available in the Source Address.
- Select the Source Address.
- Update.
- For a Destination Service Route
- Select Destination and Add destination service route.
- Enter the Destination IP address.In this case, if a packet arrives with a destination IP address that matches the configured Destination IP address, then the source IP address of the packet is sent to the Source Address configured in the next step.
- Select the Source Interface.Select Any to make all IP addresses on all interfaces available in the Source Address.
- Select the Source Address.
- Add.
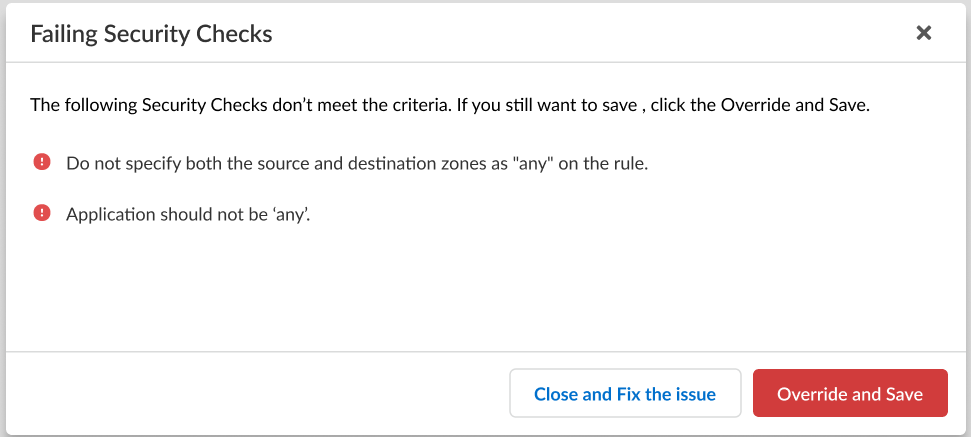
- Save.
If the configuration you're trying to save doesn't meet the criteria to pass the compliance check, you'll have the option to remediate the issue or override the warning and save the configuration anyway.![]() Configure a custom service route that the firewall uses to query for User-ID information.Push Config to push your configuration changes.
Configure a custom service route that the firewall uses to query for User-ID information.Push Config to push your configuration changes.