Prisma Access Agent
Configure Enhanced Anti-Tamper Protection for Prisma Access Agents
Table of Contents
Configure Enhanced Anti-Tamper Protection for Prisma Access Agents
Configure the Prisma Access Agent's anti-tamper protection features to protect agent
processes, files, and registries from unauthorized tampering.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma Access Agent's anti-tamper feature protects the agent's services, processes,
files, and registries from tampering by users. When configured, users require
specific one-time passwords (OTPs) or a Privileged Access Token to perform
privileged actions such as restarting agent services or uninstalling the agent.
The enhanced anti-tamper functionality addresses several security concerns:
- Provides unique per-device OTPs for specific privileged operations
- Enforces role-based access controls (RBAC) for viewing or generating anti-tamper credentials
- Maintains comprehensive audit trails for anti-tamper usage
- Offers a "break glass in case of emergency" Privileged Access Token for use in case of the loss of network connectivity
The anti-tamper protection system supports several types of passwords for different
purposes:
| Password Type | Expires After First Use | System Generated | Purpose |
|---|---|---|---|
| Disable Agent OTP | Yes | Yes | Single-use token for temporarily disabling the agent |
| Uninstall Agent OTP | Yes | Yes | Single-use token for uninstalling the agent |
| Privileged Access OTP | Yes | Yes | Used for any privileged operation including restarting agent services |
| Privileged Access Token | No | No | Administrator-defined emergency token for critical access scenarios |
All OTPs will refresh after one-time use and are never stored on the endpoint. The
Privilege Access Token is static and does not expire after each use.
To configure anti-tamper protection:
- Navigate to the Prisma Access Agent agent app settings page.
- For Strata Cloud Manager Managed Prisma Access deployments:
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.
- For Panorama Managed
Prisma Access
deployments:
- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access Agent.
- Click Launch Prisma Access Agent.
- Select ConfigurationPrisma Access AgentSettingsPrisma Access Agent.
- For NGFW (Managed by Panorama) deployments:
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationPrisma Access AgentSettingsPrisma Access Agent.
Add an agent setting or edit an existing agent setting.- (Optional) Set up the Match Criteria such as OS and User Entities to deploy the agent settings to specific users or user groups.Configure the anti-tamper protection settings:
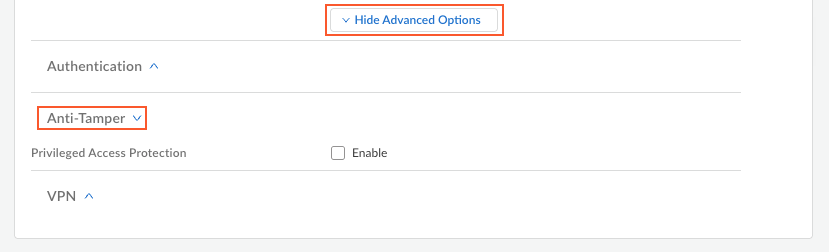
- (Strata Cloud Manager only) In the App Configuration
section, select Show Advanced OptionsAnti-Tamper.
![]()
- Configure the following anti-tamper options:
![]()
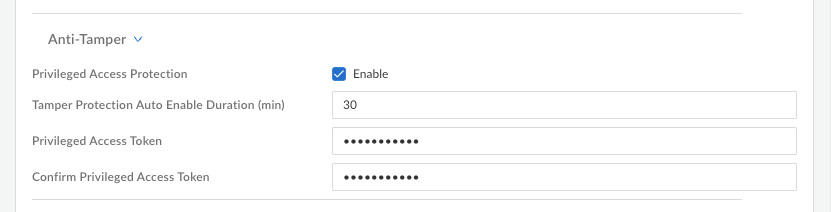
- Privileged Access Protection—Select this option to enable anti-tamper protection on the endpoints that meet the Match Criteria. Enabling this option reveals the anti-tamper configuration options. (Default: Disabled)
- Tamper Protection Auto Enable Duration (min)—Specify the duration (30-480 minutes) for which the end-user gains privileged access by providing the Privileged Access OTP or Privileged Access Token. (Default: 30 minutes)
- Privileged Access Token—Enter and
confirm an emergency access password for use in critical
access scenarios. The token must have 8-16 alphanumeric
characters with at least one uppercase letter, lowercase
letter, number, and optionally one special character
from the following set:
@$!%?&The Privileged Access Token and Tamper Protection Auto Enable Duration are required when you enable Privileged Access Protection.
These settings are only visible to administrators with superuser privileges through RBAC controls. - Save the agent configuration.
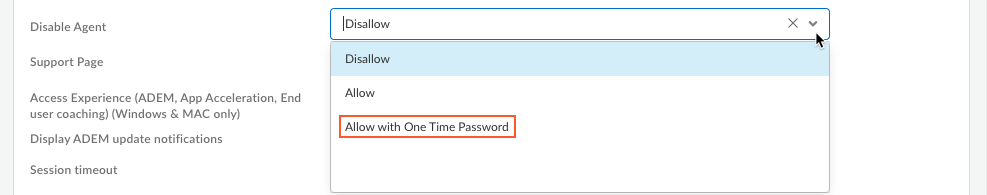
(Optional): Set up the disable agent configuration.Configure the Disable Agent option:- Allow—Any user can disable the Prisma Access Agent without requiring a password.
- Disallow—Does not allow users to disable the agent. The Disable option is not available in the Prisma Access Agent app.
- Allow with OTP—Users can disable the agent only with a valid OTP or token.
![]() Push the Prisma Access Agent Configuration.View and access device-specific OTPs in the Endpoint Management page in case you need to share the OTPs with your users.
Push the Prisma Access Agent Configuration.View and access device-specific OTPs in the Endpoint Management page in case you need to share the OTPs with your users.- Select ConfigurationEndpoint Management.Select a Hostname in the Devices table.In the window that slides open, view the Anti-Tamper section. Depending on the configuration, you will see the following combinations of fields:
Configuration Anti-Tamper Fields - Privileged Access ProtectionDisabled
- Disable Agent with OTPDisallow
![]()
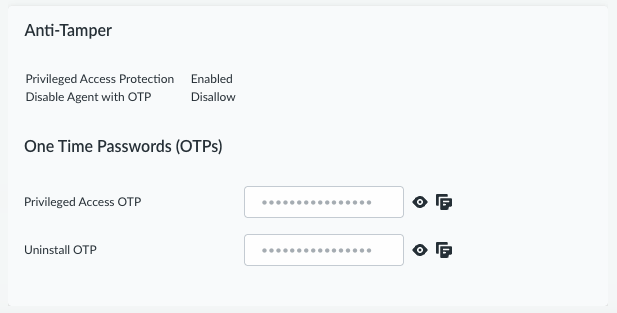
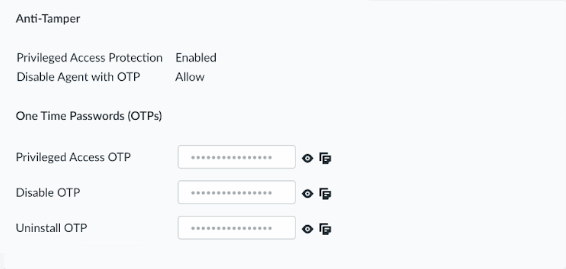
- Privileged Access ProtectionEnabled
- Disable Agent with OTPDisallow
![]()
- Privileged Access ProtectionEnabled
- Disable Agent with OTPAllow
![]()
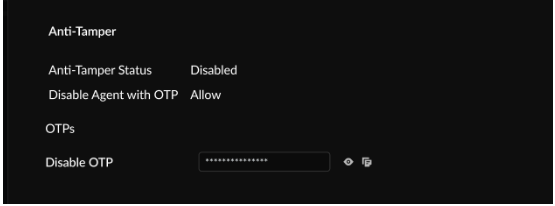
- Privileged Access ProtectionDisabled
- Disable Agent with OTPAllowed
![]() From this page, you can view and copy device-specific OTPs for:
From this page, you can view and copy device-specific OTPs for:- Disabling the agent
- Using privileged access (for any privileged command)
- Uninstalling the agent
Use the Privileged Access Token for emergency access.In case of emergency scenarios where normal access methods are unavailable:- Use the Privileged Access Token (emergency access password) that you configured.
- This token works for all privileged operations on all agents.
- The token does not refresh after each use, unlike the OTPs.
As a best practice, rotate the Privileged Access Token every three months for enhanced security.Verify that anti-tamper protection is enabled for the Prisma Access Agent on an endpoint by using the Prisma Access Agent command-line tool (PACli).- Check the status of the anti-tamper protection by running the following command on an endpoint:
- On macOS
agents:
/Applications/Prisma\ Access\ Agent.app/Contents/Helpers/pacli protect status
- On Windows
agents:
"C:\Program Files\Palo Alto Networks\Prisma Access Agent\pacli" protect status
If you successfully enabled anti-tamper protection, the following output should appear:Protection State --------------- ---------- File Enabled Process Enabled Registry Enabled Service Enabled
Try to disable the anti-tamper protection by running the following command:pacli protect disable
If you successfully enabled anti-tamper protection, the agent will prompt you to Enter password.Audit and monitor anti-tamper activities and OTP usage in the Log Viewer or Strata Logging Service. The system maintains comprehensive audit trails for anti-tamper activities:- Agent audit logs:
- OTP generation events
- Successful and failed OTP validation attempts
- Endpoint management audit logs:
- Tamper-protection disablement events (from endpoint management logs)
- Privileged command execution during tamper protection disabled periods (from endpoint management logs)
These audit logs are available in the Event Log Viewer and are subject to RBAC permissions. For security, raw OTPs and tokens are never logged in the audit trails. - On macOS
agents:
- For Strata Cloud Manager Managed Prisma Access deployments: