Prisma Access Agent
Pre-Logon Prerequisites
Table of Contents
Pre-Logon Prerequisites
Complete the prerequisite tasks before configuring the pre-logon feature for Prisma
Access Agent.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Pre-logon for Prisma Access Agent is a feature that establishes a limited but secure
tunnel to Prisma Access before a user logs in to their device. The pre-logon tunnel
can establish a secure tunnel connection by verifying the device itself using
machine certification.
Before you begin to configure pre-logon on Strata Cloud Manager, you must complete
several prerequisite tasks on the endpoints.
Disable Windows Automatic Restart Sign-On
(Windows Endpoints Only) Introduced in Windows 10 Version 1903, the
Windows automatic restart sign-on (ARSO) feature can automatically log into
Windows after a restart using the credentials of the last logged-in user.
To the end user, the system appears to be logged out, but in reality it's logged
in but locked. ARSO also determines whether applications opened before restart
will automatically relaunch upon unlocking. This can affect Prisma Access Agent
pre-logon behavior because the users only log in or out of Windows when they
explicitly click the Sign out button.
You need to disable ARSO by updating and applying the Windows group policy. You
can do this using several methods:
- Update the group policy locally on Windows endpoint:
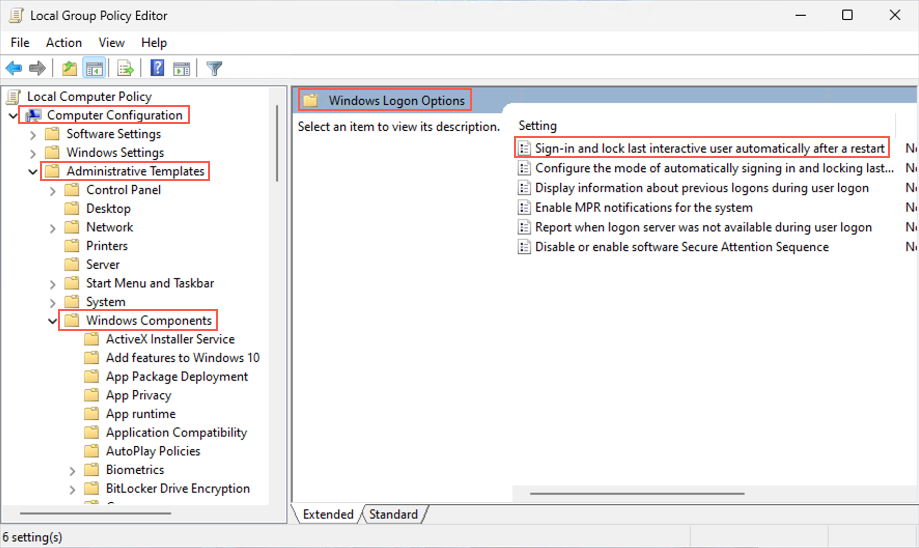
- Open the Local Group Policy Editor by running the gpedit.msc command.Select Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Logon Options.Disable Sign-in and lock last interactive user automatically after a restart.
![]() Update the local group policy by running the gpupdate /force command.Configure group policy settings in Microsoft Intune:
Update the local group policy by running the gpupdate /force command.Configure group policy settings in Microsoft Intune:- Log in to the Microsoft Intune admin center.Go to DevicesManage devicesConfigurationCreateNew policy.Make the following selections:
- Set the Platform to Windows 10 and later.
- Set the Profile type to Administrative Templates.
Click Create.In Basics, enter a Name and Description for the policy.In Configuration settings, select Computer configurationWindows componentsWindows Logon Options.Disable Sign-in and lock last interactive user automatically after a restart.Select OK to save your changes.Complete other necessary settings for the policy and Review + create your settings.The next time a device checks for configuration updates, the settings you configured are pushed to the device.Update the registry on unmanaged Windows devices:- Navigate to the registry path: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\SystemConfigure the following registry key:
- Key: DisableAutomaticRestartSignOn
- Type: DWORD
- Value: 0
Deploy Certificates to Endpoints
Before you begin to configure pre-logon, deploy machine certificates throughout your environment. Prisma Access Agent will use these certificates for device authentication during the pre-logon process.Install a user certificate and machine certificate on endpoints manually or using mobile device management (MDM) software. Use a trusted third-party CA, self-signed CA, or an internal PKI CA to issue a machine certificate. Push the machine certificate in the system store so it will be available while the computer is logged out or locked. Deploy both certificates to the proper certificate store on the endpoints.When deploying the machine certificate, ensure that the machine certificate CN matches the hostname of the endpoint, and be sure to push the machine certificate to the following locations on the endpoint:- (Windows) Local Machine store
- (macOS) System keychain
When deploying the user certificate, be sure to push the user certificate to the following location on the endpoint:- (Windows) Current User store
- (macOS) Login keychain
A successful agent installation or a first boot will create a pre-logon tunnel, which will allow logging in and pulling the initial user profile. This will trigger the OS to download the user certificate while still connected to the pre-logon tunnel, and will allow the transition and connection to a user-specific tunnel.