Prisma Access Agent
Set Up Pre-Logon for Prisma Access Agent
Table of Contents
Set Up Pre-Logon for Prisma Access Agent
Complete the Cloud Identity Engine settings and configure pre-logon for Prisma Access
Agent.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To set up pre-logon for Prisma Access Agents, you need to install the root
certificate for signing client certificates in Cloud Identity Engine. Then,
configure the machine certificate as an authentication method to establish a tunnel
from an endpoint before logging in to Prisma Access on Strata Cloud Manager, and
create a certificate profile that includes the pre-logon CA certificate. Finally,
configure the pre-logon settings in the Agent Settings and set up security policy
rules for pre-logon users in Strata Cloud Manager.
Before you begin to configure pre-logon, you need to complete the prerequisites on the endpoints.
Complete the following steps to configure pre-logon for Prisma Access Agents:
- In Cloud Identity Engine, install the root certificate for signing client certificates, which signs the machine hostname of the endpoint.
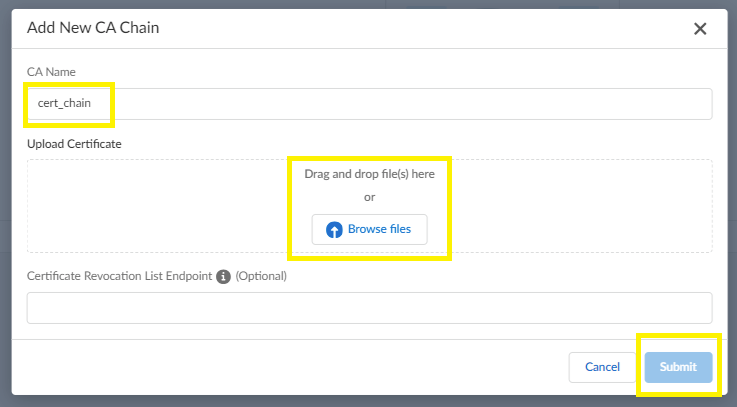
- Add a certificate to the CA Chains as follows:
- Select CA ChainsAdd CA Chain.
- Enter the name for the new CA Chain in CA
Name.
![]()
- Drag and drop the certificate to Upload Certificate and Submit.
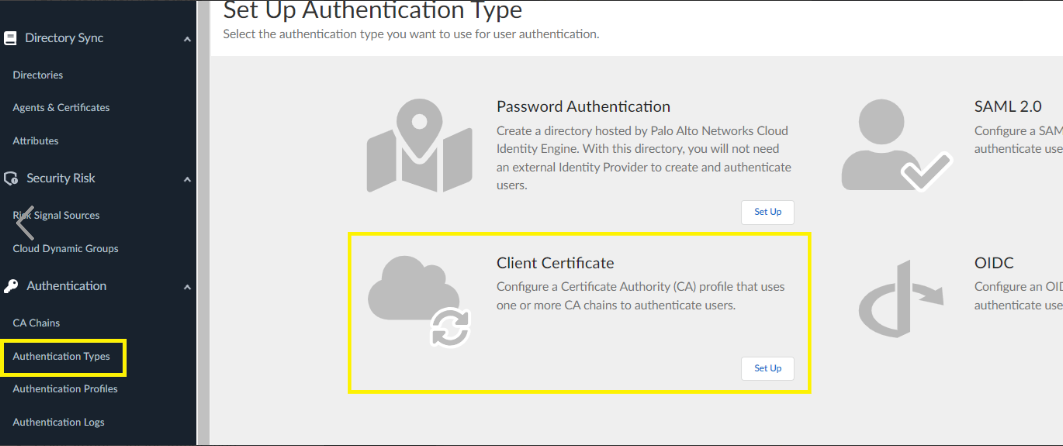
Add an authentication type for the CA chain you added.- Select Authentication TypesAdd New Authentication Type.
- Set Up an authentication type for the
client certificate.
![]()
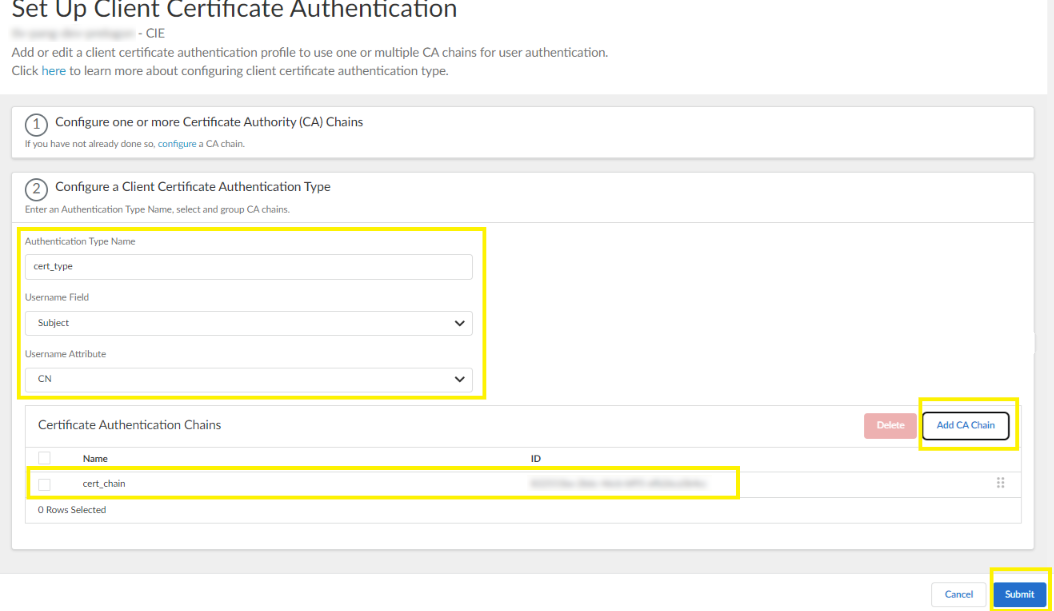
- Enter a meaningful name for the Authentication Type Name.
- Add CA Chain and select the CA chain that
you added in step 1.a and
Submit.
![]()
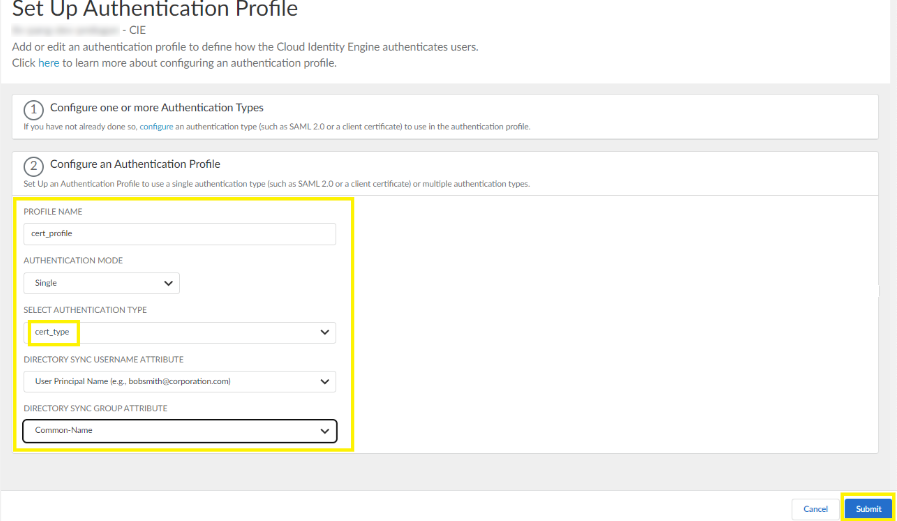
Add an authentication profile for the authentication type that you created for the client certificate.- Select Authentication ProfilesAdd Authentication Profile.
- Enter a meaningful PROFILE NAME.
- Choose the Single authentication mode.
- Select the authentication type that you created in step 1.b.
- Select User Principal Name for the Directory Sync Username Attribute.
- Select Common-Name for the Directory Sync Group Attribute.
- Submit.
![]() In Strata Cloud Manager, configure machine certificate authentication for pre-logon users.
In Strata Cloud Manager, configure machine certificate authentication for pre-logon users.- Import a third-party root CA certificate.Use a machine certificate as an authentication method to establish a tunnel from an endpoint before logging in to Prisma Access.
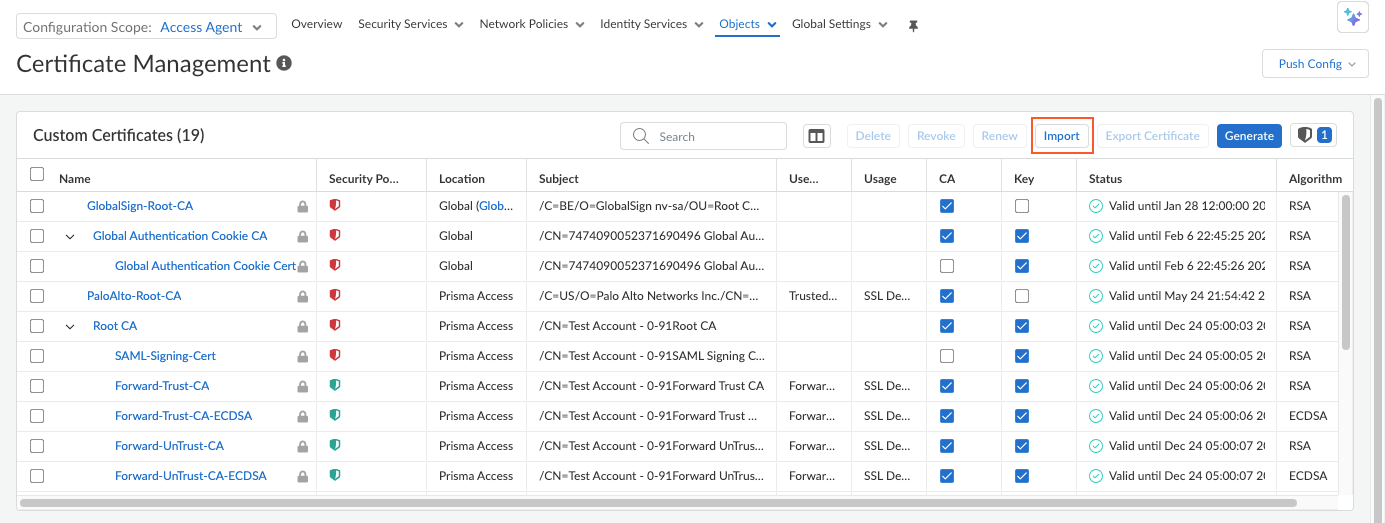
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentObjectsCertificate Management.
- Import a custom certificate. Ensure that
you're importing the certificate for Prisma Access Agent mobile
users.
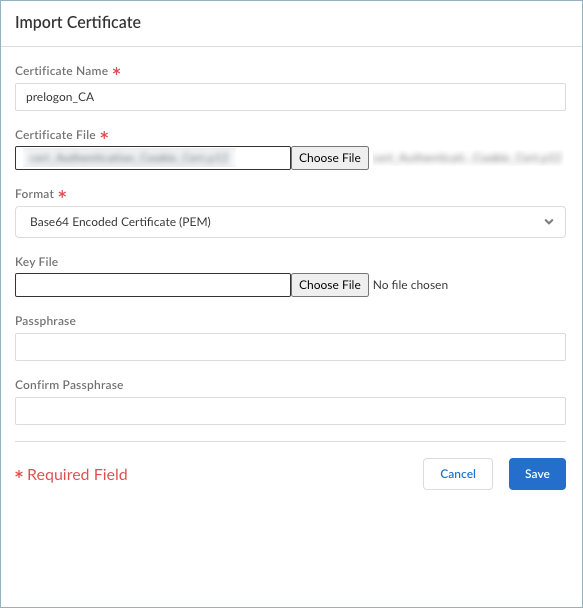
![]()
- Enter the required values, and Save the
certificate settings.
![]()
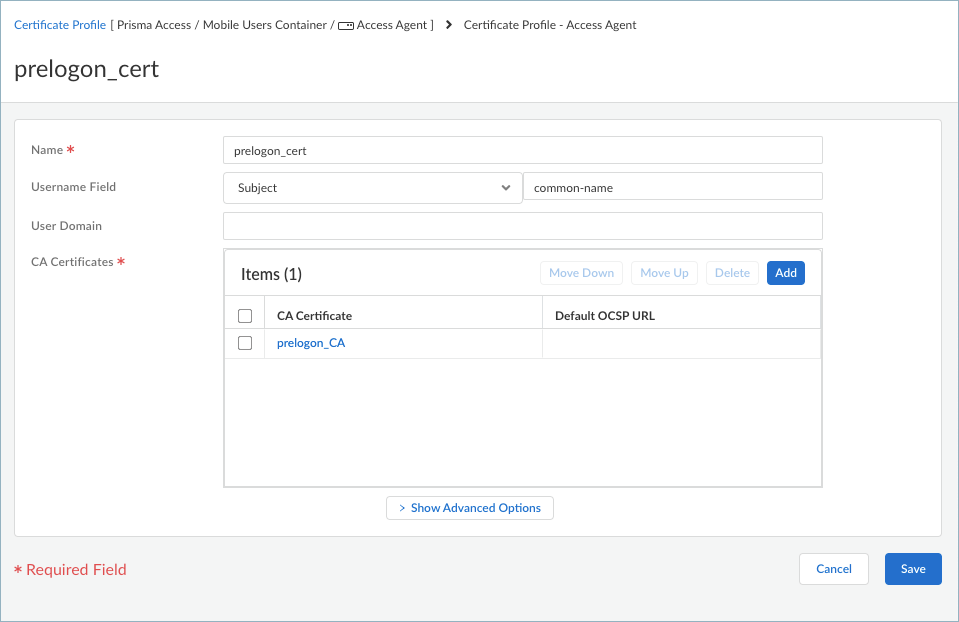
Create a pre-logon certificate profile.Create a certificate profile and include the self-signed root CA. This CA validates the machine certificate by the Prisma Access Agent mobile user during pre-logon.- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentObjectsCertificate Management.
- Add Profile.
- Enter a Name for the certificate profile.
- Add the root pre-logon CA certificate you imported in step 2.a.
- Save the certificate profile
settings.
![]()
Configure the user authentication settings in Strata Cloud Manager.- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.Add User Authentication.Select the following options:
- Authenticate Users From—Select Match Any.
- Authentication Type—Select Client Certificate OR SAML.
- Certificate Profile—Select the pre-logon certificate profile that you created in step 2.b.
- Authentication Profile—Select or create the authentication profile based on the Cloud Identity Engine profile you created in step 1.c.
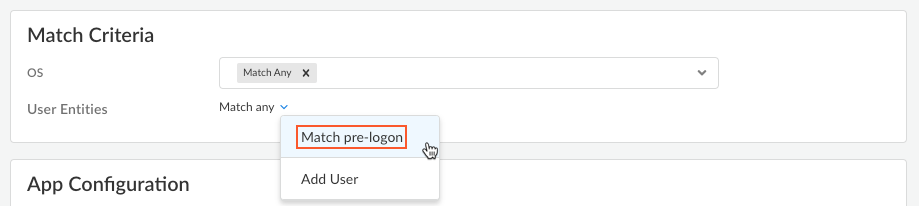
Enable pre-logon in the Agent Settings on Strata Cloud Manager.- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.Click Add Agent Settings to create a new agent setting or select an existing agent setting to enable the pre-logon feature.In the Match Criteria, select Match anyMatch pre-logon. With this setting, devices running the pre-logon tunnel will get the agent configurations.
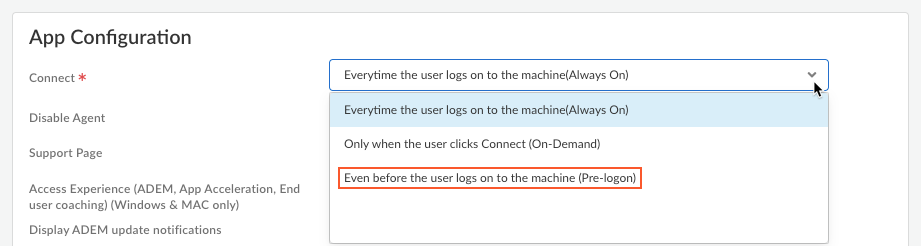
![]() In the Connect drop-down, select Even before the user logs on to the machine (Pre-logon).
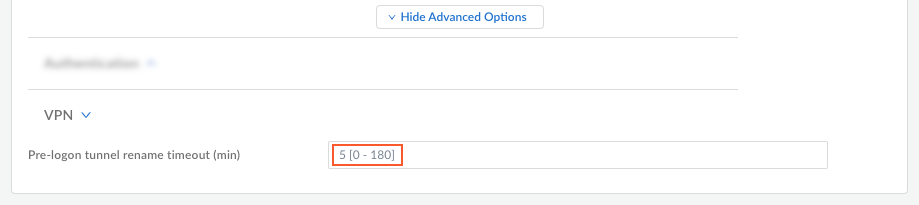
In the Connect drop-down, select Even before the user logs on to the machine (Pre-logon).![]() Select Show Advanced OptionsVPN and set the Pre-logon tunnel rename timeout (min) value.This determines, after a user logs in, how long the pre-logon tunnel will remain active before transitioning to a user-specific tunnel (when the pre-logon tunnel gets renamed to the user-specific tunnel). The range is 0-180 minutes. The default is 5 minutes.
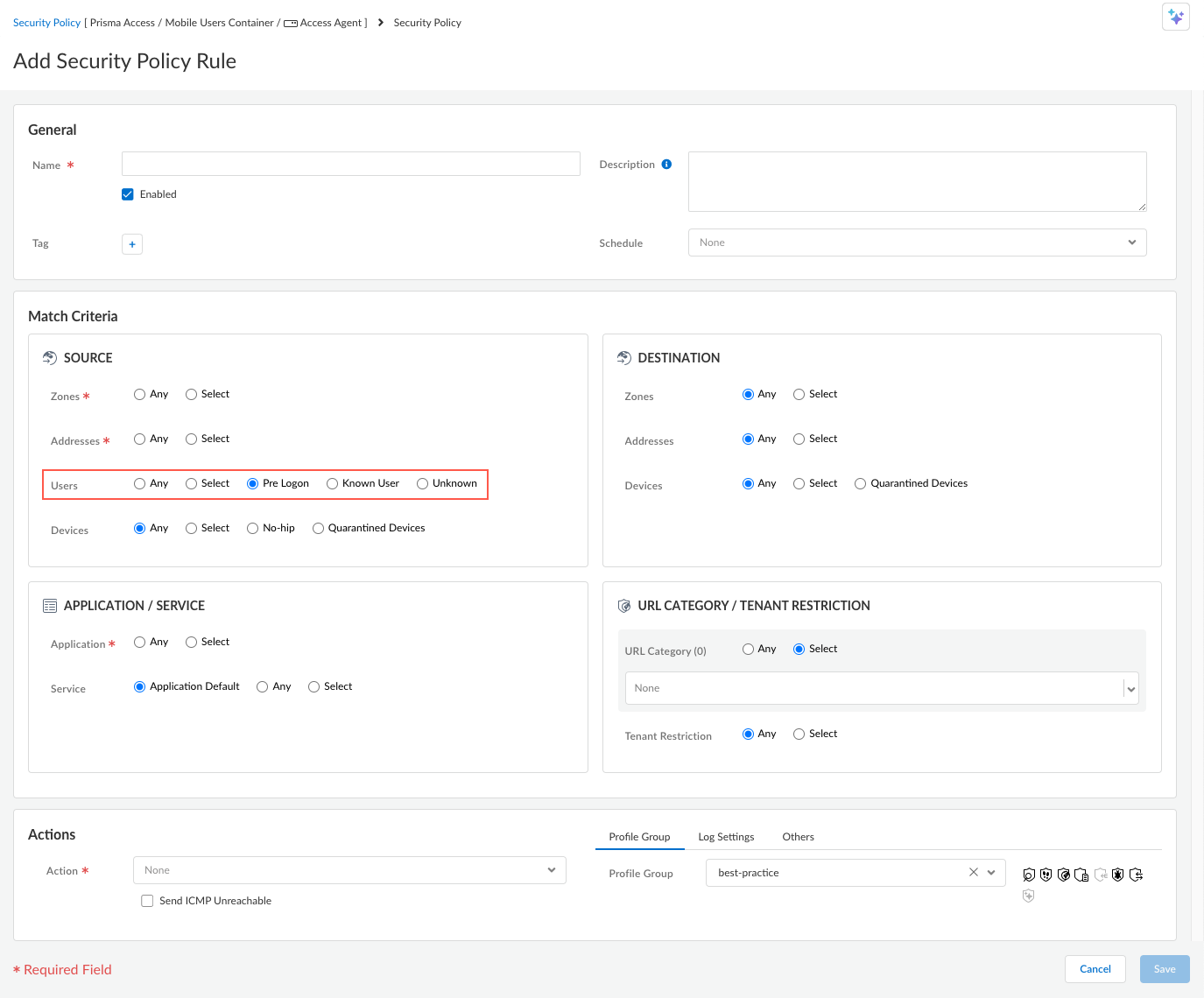
Select Show Advanced OptionsVPN and set the Pre-logon tunnel rename timeout (min) value.This determines, after a user logs in, how long the pre-logon tunnel will remain active before transitioning to a user-specific tunnel (when the pre-logon tunnel gets renamed to the user-specific tunnel). The range is 0-180 minutes. The default is 5 minutes.![]() To allow endpoints to access resources, create security policy rules that match the pre-logon user. These policy rules should allow access to only the basic services for starting up the system; for example, DHCP, DNS, specific Active Directory services, antivirus, or other update services.
To allow endpoints to access resources, create security policy rules that match the pre-logon user. These policy rules should allow access to only the basic services for starting up the system; for example, DHCP, DNS, specific Active Directory services, antivirus, or other update services.- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess Agent.Select Security ServicesSecurity Policies.Select Add RuleSecurity Rule to create a security policy rule or modify an existing rule.Build the rule by configuring the appropriate rule components. Be sure to select UsersPre Logon.
![]() Push the Prisma Access Agent Configuration.Add the following statement to the Prisma Access Agent configuration file (config.json) for predeployment:
Push the Prisma Access Agent Configuration.Add the following statement to the Prisma Access Agent configuration file (config.json) for predeployment:"pre_logon_supported" : true
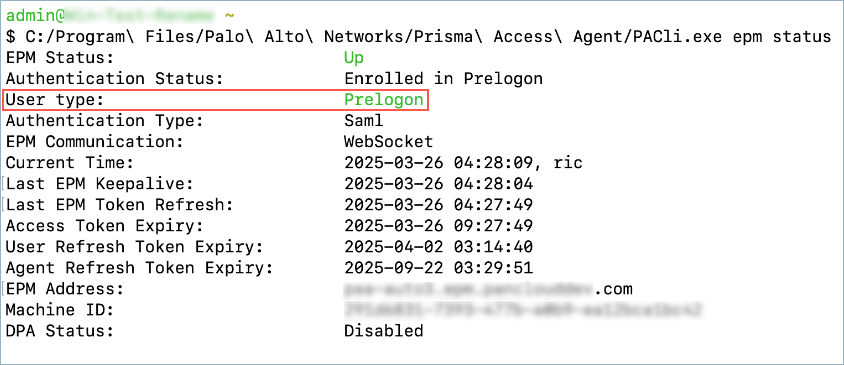
This will cause the agent to enroll to the Prisma Access Agent Manager (EPM) during pre-logon. Predeployment is only necessary for the first-time user.Test the configuration by rebooting a device and verifying that it establishes a pre-logon tunnel before user authentication. On Windows devices, check the Windows login screen. You can refer to the pre-logon workflow for more details.Verify the pre-logon tunnel status using the pacli command on the endpoint.- Run the pacli epm status command and check the Authentication Status and User type fields in the output.A user type of Prelogon indicates that the user has not signed on to the operating system and the pre-logon tunnel is active. A user type of Logged on indicates that the user has successfully authenticated to the operating system and the pre-logon tunnel has transitioned to the user-specific tunnel.
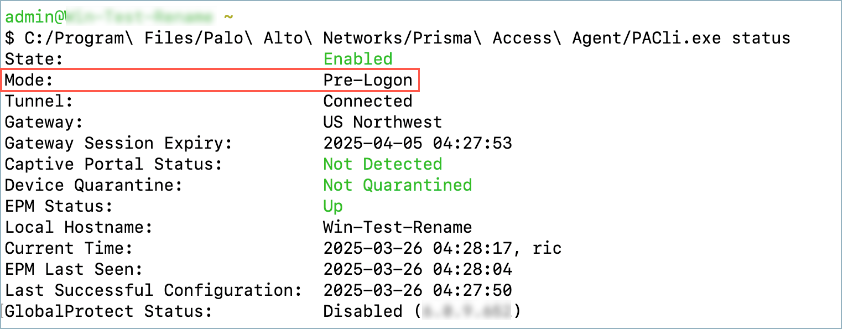
![]() Run the pacli status command and check the Mode and field to determine the tunnel mode that’s active.
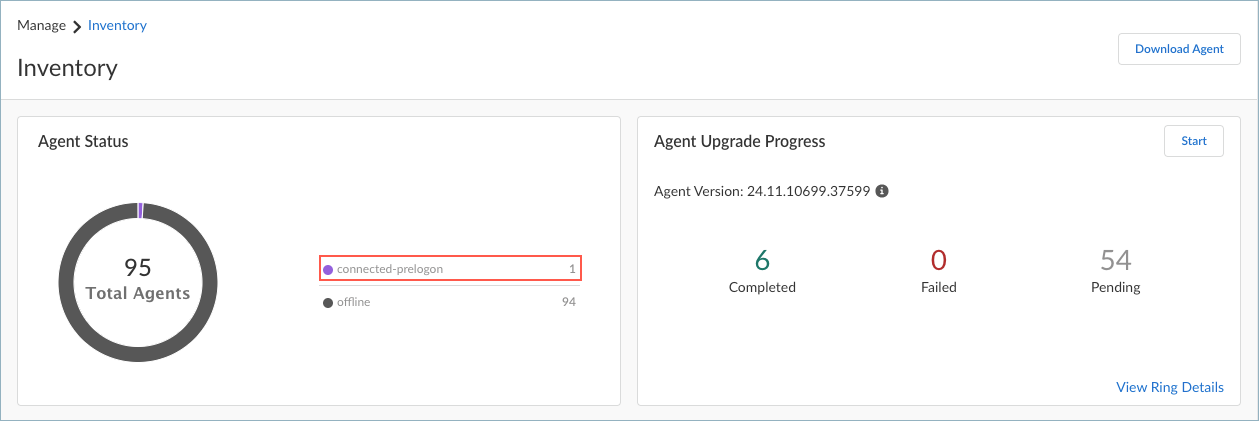
Run the pacli status command and check the Mode and field to determine the tunnel mode that’s active.![]() After transitioning to the user-specific tunnel, the mode will change to the previously configured connection mode for the user (Always On or On Demand) and the same agent session will resume.Monitor the Endpoint Management page to view the number of devices currently connected in pre-logon mode.
After transitioning to the user-specific tunnel, the mode will change to the previously configured connection mode for the user (Always On or On Demand) and the same agent session will resume.Monitor the Endpoint Management page to view the number of devices currently connected in pre-logon mode.- Select ConfigurationEndpoint Management.The Agent Status chart will show the number of agents connected to the gateway via the pre-logon tunnel. The status for agents in the pre-logon mode is connected-prelogon.
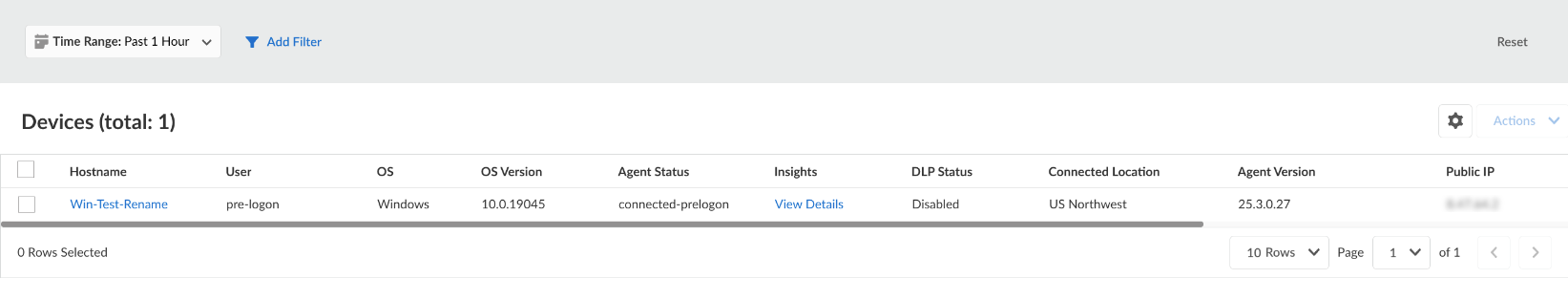
![]() The Agent Status column in the Devices table will show that a device is connected via the pre-logon tunnel with status connected-prelogon. In pre-logon mode, the User is always pre-logon.
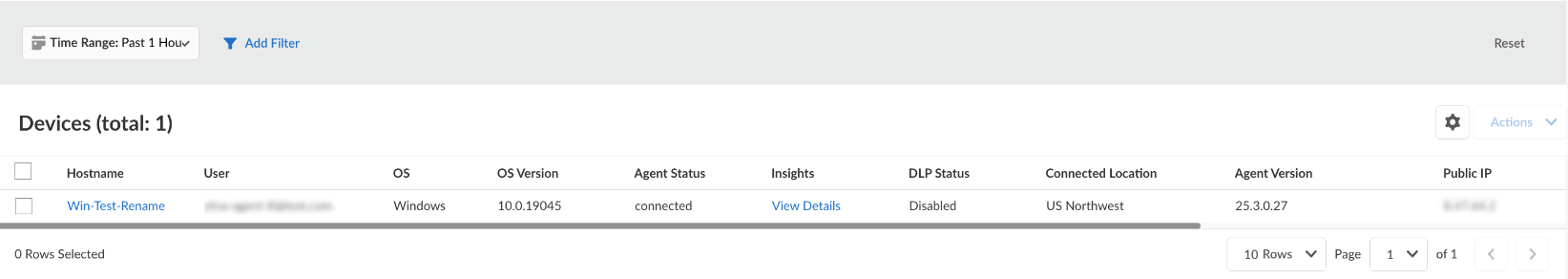
The Agent Status column in the Devices table will show that a device is connected via the pre-logon tunnel with status connected-prelogon. In pre-logon mode, the User is always pre-logon.![]() To show the users who are connected in pre-logon mode, you can filter on the User column to show only users the username of pre-logon.After the pre-logon tunnel transitions to the user-specific tunnel, the Agent Status will change to connected, and the User column will display the username associated with the device.
To show the users who are connected in pre-logon mode, you can filter on the User column to show only users the username of pre-logon.After the pre-logon tunnel transitions to the user-specific tunnel, the Agent Status will change to connected, and the User column will display the username associated with the device.![]() There might be a brief interval (a few seconds) when the tunnel becomes disconnected during the tunnel transition. However, typically the agent will reconnect before sending the disconnection status to the Endpoint Management page.
There might be a brief interval (a few seconds) when the tunnel becomes disconnected during the tunnel transition. However, typically the agent will reconnect before sending the disconnection status to the Endpoint Management page.