Prisma Access Agent
Set Up SAML Authentication With Cloud Identity Engine
Table of Contents
Set Up SAML Authentication With Cloud Identity Engine
Configure SAML authentication for Prisma Access Agent using Cloud Identity
Engine.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Security Assertion Markup Language (SAML) is an XML-based, open-standard data format
used to exchange authentication and authorization data between parties, specifically
between an identity provider (IdP) and a service provider. Set up user
authentication using SAML 2.0 and Cloud Identity Engine so that only legitimate Prisma Access Agent users have access to your services and applications.
Authenticated users are associated with configuration rules that define how
the Prisma Access Agent is configured when it is deployed to
endpoints.
You can use client certificates or SAML with Cloud Identity Engine as authentication
methods for Prisma Access Agent. (Client
certificates do not apply to Prisma Access Agent Linux)
Before you begin, Set Up Cloud Identity Engine for Prisma Access Agent User Authentication and
set up an authentication profile.
You can set up SAML authentication depending on the deployment you're using.
Set Up SAML User Authentication With CIE (Prisma Access Deployment)
Learn how to set up the user authentication for Prisma Access Agent users in
Prisma Access deployments.
For Prisma Access deployments, you can use Strata Cloud Manager or Panorama
to set up user authentication so that only legitimate Prisma Access Agent
users have access to your services and applications.
Before you begin, Set Up Cloud Identity Engine for Prisma Access Agent User Authentication and
set up an authentication profile.
You can set up user authentication depending on the management platform you're using.
Set Up SAML Authentication with CIE (Prisma Access Deployment on Strata Cloud Manager)
Use Strata Cloud Manager to set up the authentication for Prisma Access Agent
users in Prisma Access deployments.
You can use Strata Cloud Manager to set up user authentication using SAML with Cloud
Identity Engine so that only legitimate Prisma Access Agent users have access
to your services and applications.
- Set up an authentication profile that refers to the Cloud Identity Engine authentication profile that you created in Cloud Identity Engine, which validates the login credentials of end users who access resources and applications using the Prisma Access Agent.
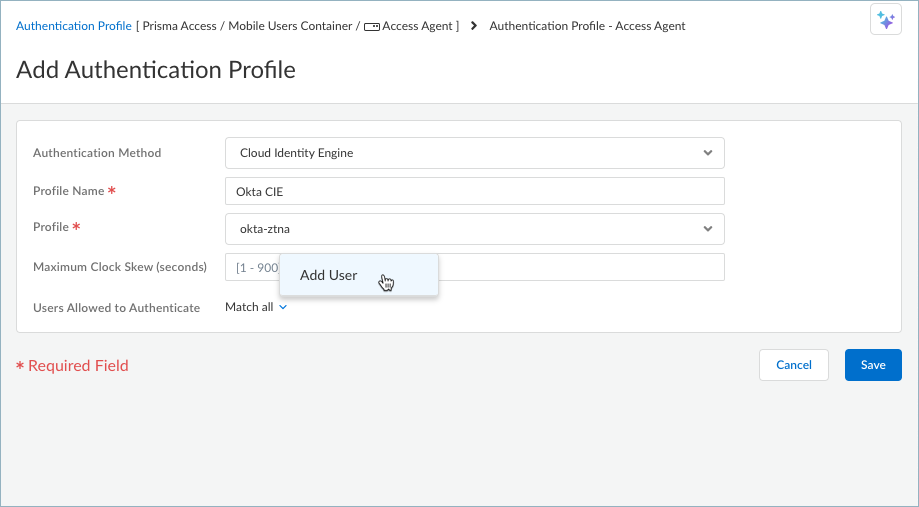
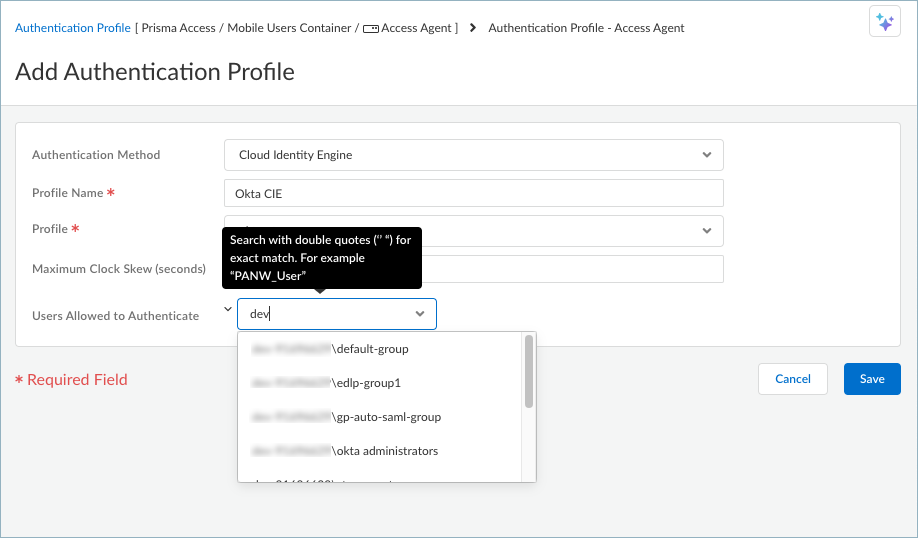
- In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess Agent.Select Identity ServicesAuthenticationAuthentication Profiles.Add Profile.Select Authentication MethodCloud Identity Engine.Enter a Profile Name.Select an available Profile (which comes from Cloud Identity Engine).Enter the Maximum Clock Skew in seconds, which is the allowed system time difference (in seconds) between the IdP and Prisma Access when Prisma Access validates IdP messages. The default value is 60 seconds, and the range is 1-900 seconds. If the difference exceeds this value, authentication fails.By default, all users can authenticate with Prisma Access. To select specific users or user groups, select Match allAdd User and select the user or user group that you want to add.
![]() You can add more users or groups by clicking the plus sign + and searching for a user or user group. Click away from the drop-down to save your query.
You can add more users or groups by clicking the plus sign + and searching for a user or user group. Click away from the drop-down to save your query.![]() Save your new profile.In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetup.If this is your first time setting up the Prisma Access Agent, click Set Up User Authentication.
Save your new profile.In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetup.If this is your first time setting up the Prisma Access Agent, click Set Up User Authentication.![]() Otherwise, select an authentication method to update it or Add User Authentication.
Otherwise, select an authentication method to update it or Add User Authentication.![]() To authenticate users to Prisma Access, select an Authentication Type.
To authenticate users to Prisma Access, select an Authentication Type.![]() The following authentication types are available with Cloud Identity Engine:
The following authentication types are available with Cloud Identity Engine:- (Unsupported on Prisma Access Agent Linux) Client Certificate (Cloud Identity Engine)—Select this to use a client certificate from the Cloud Identity Engine to obtain usernames and authenticate Prisma Access Agent users to Prisma Access. To authenticate users based on a client certificate, one of the certificate fields, such as the Subject Name field, must identify the username. End users who successfully authenticate through client certificate authentication don't have the option to sign out of the Prisma Access Agent.
- SAML (Cloud Identity Engine)—Select this to use SAML 2.0 to integrate Prisma Access with an identity provider (IdP) that controls access to both external and internal services and applications. SAML single sign-on (SSO) enables one login to access multiple applications, and is helpful in environments where each user accesses many applications and authenticating for each one would impede user productivity. In this case, SAML single sign-on (SSO) enables one login to access multiple applications. This is the default selection.
- (Unsupported on Prisma Access Agent Linux) Client Certificate OR SAML (Cloud Identity Engine)—Select this to grant access to end users as long as they have successfully passed either client certificate authentication or SAML authentication.
- (Unsupported on Prisma Access Agent Linux) Client Certificate AND SAML (Cloud Identity Engine)—Select this to require users to pass both certificate authentication and SAML authentication.
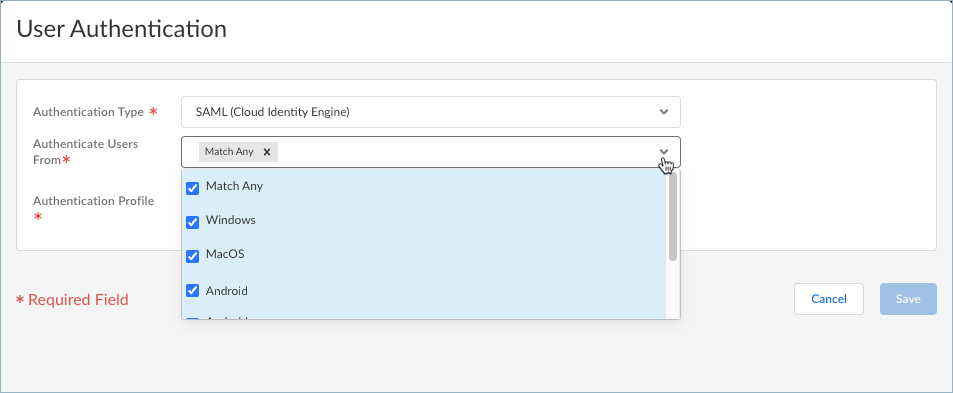
Select the endpoint operating system to Authenticate Users From. Selecting Match Any will authenticate users from all supported operating systems. The default is Match Any.![]() Select a profile to use for authentication based on the authentication type.
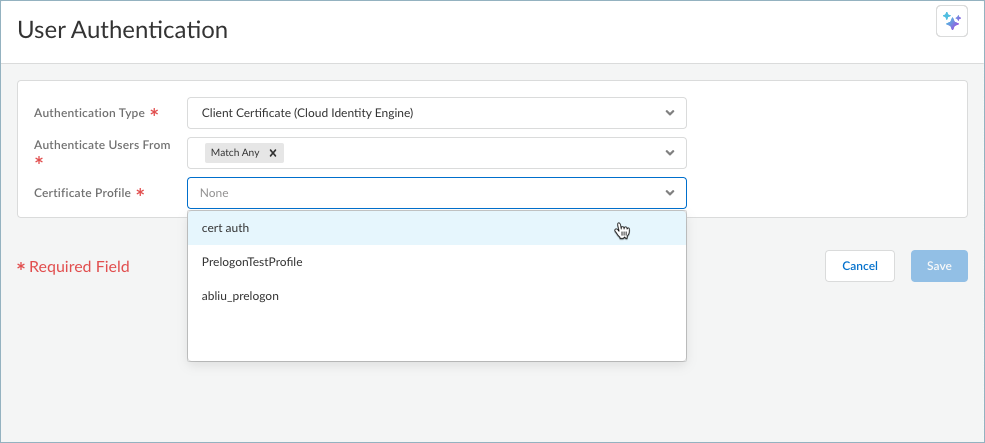
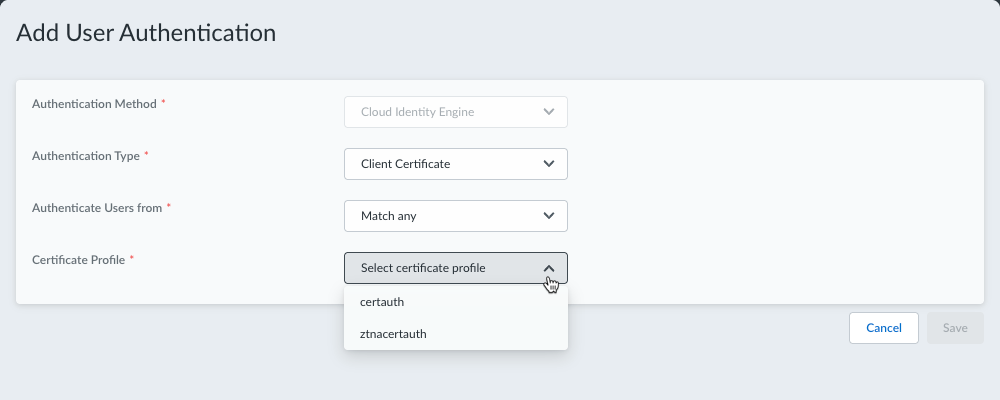
Select a profile to use for authentication based on the authentication type.- (Unsupported on Prisma Access Agent Linux) If you're using the Client Certificate (Cloud Identity Engine) authentication type, select a Certificate Profile to verify the certificates that Prisma Access Agent users present to Prisma Access during a connection request. The certificate profile specifies the contents of the username and user domain fields; lists CA certificates; criteria for blocking a session; and offers ways to determine the revocation status of CA certificates.Because the certificate is part of the authentication for the user, you must predeploy certificates used in certificate profiles to your users before their initial login. The certificate profile specifies which certificate field contains the username (Subject or Subject Alt). If the certificate profile specifies Subject in the Username Field, the certificate presented by the endpoint must contain a Common Name for the endpoint to connect. If the certificate profile specifies a Subject-Alt with an Email or Principal Name as the Username Field, the certificate must contain the corresponding fields, which will be used as the username when the Prisma Access Agent authenticates to Prisma Access.
![]() If no certificate profile is listed, you need to configure a certificate profile in Cloud Identity Engine.
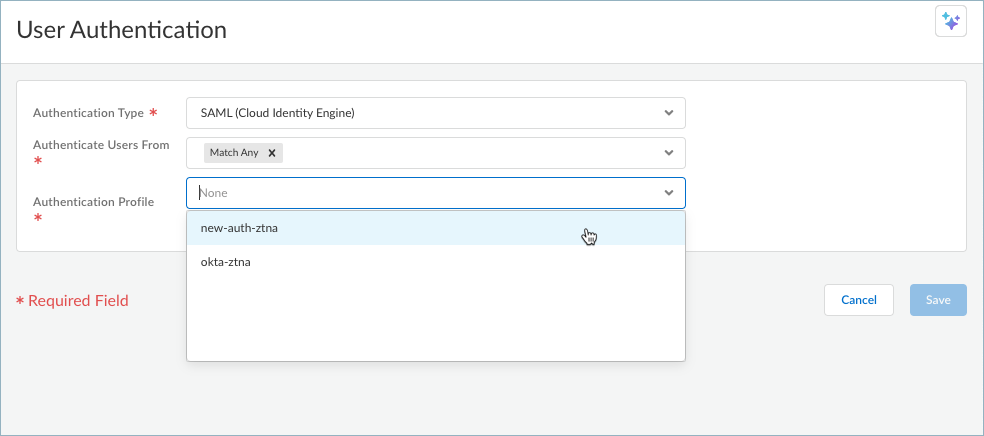
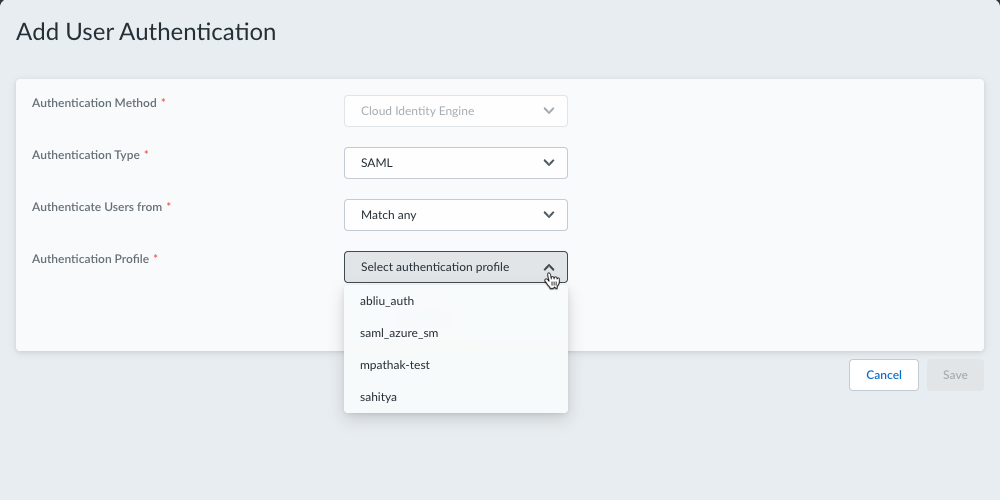
If no certificate profile is listed, you need to configure a certificate profile in Cloud Identity Engine. - If you're using SAML (Cloud Identity Engine),
select an Authentication Profile. This
authentication profile is the profile you set up in step 1, which defines the
authentication service that validates the login credentials of end users
who access resources and applications using the Prisma Access Agent.
![]()
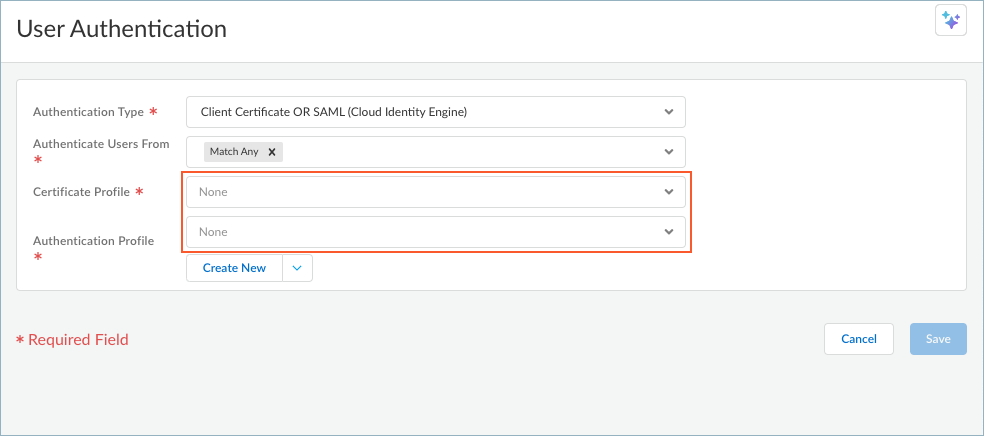
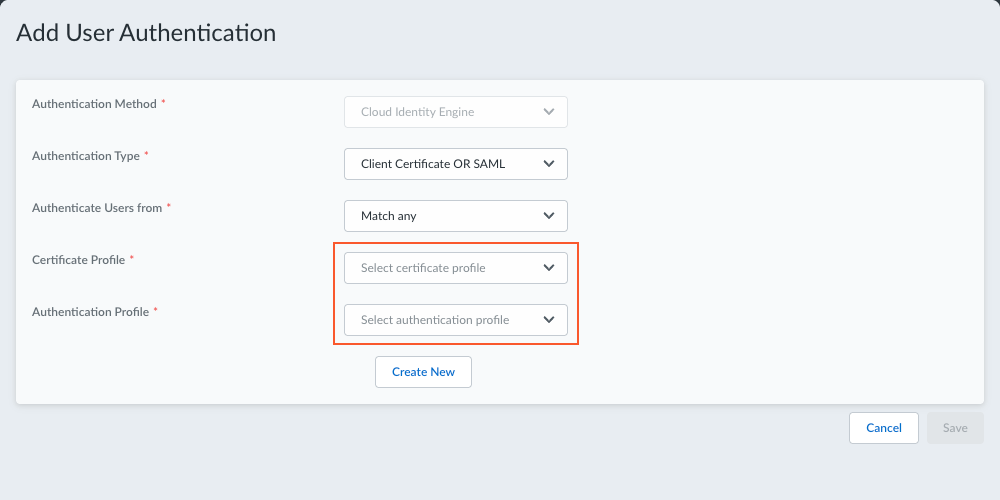
- (Unsupported on Prisma Access
Agent Linux) If you're using Client
Certificate OR SAML (Cloud Identity Engine), select a
Certificate Profile and an
Authentication Profile. This will grant
access to end users as long as they have successfully passed either
client certificate authentication or SAML authentication.
![]()
- (Unsupported on Prisma Access Agent Linux) If you're using Client Certificate AND SAML (Cloud Identity Engine), select a Certificate Profile and an Authentication Profile. This will require users to pass both certificate authentication and SAML authentication.
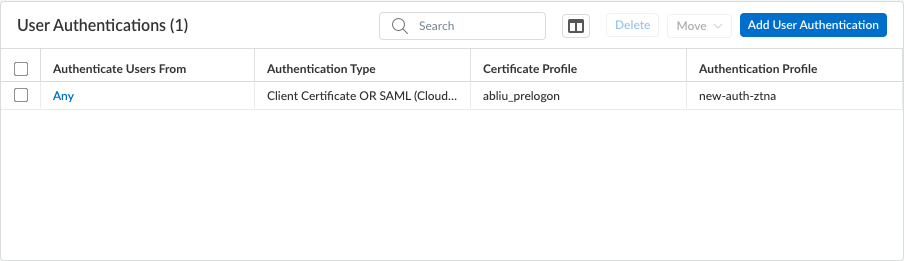
Save your user authentication settings.Your new or updated user authentication will appear in the User Authentications table. Ensure that the OS listed in the Authenticate Users From column follows the hierarchy with the OS-specific profiles at the top, and the Any OS at the bottom. If the user authentication profile with the Any OS is placed above the OS-specific authentication profiles, the Any OS profile won’t get matched since Prisma Access Agent always selects the authentication profile with the exact matching OS.You can select a user authentication profile and Move it up or down the table.Set Up SAML Authentication with CIE (Prisma Access Deployment on Panorama)
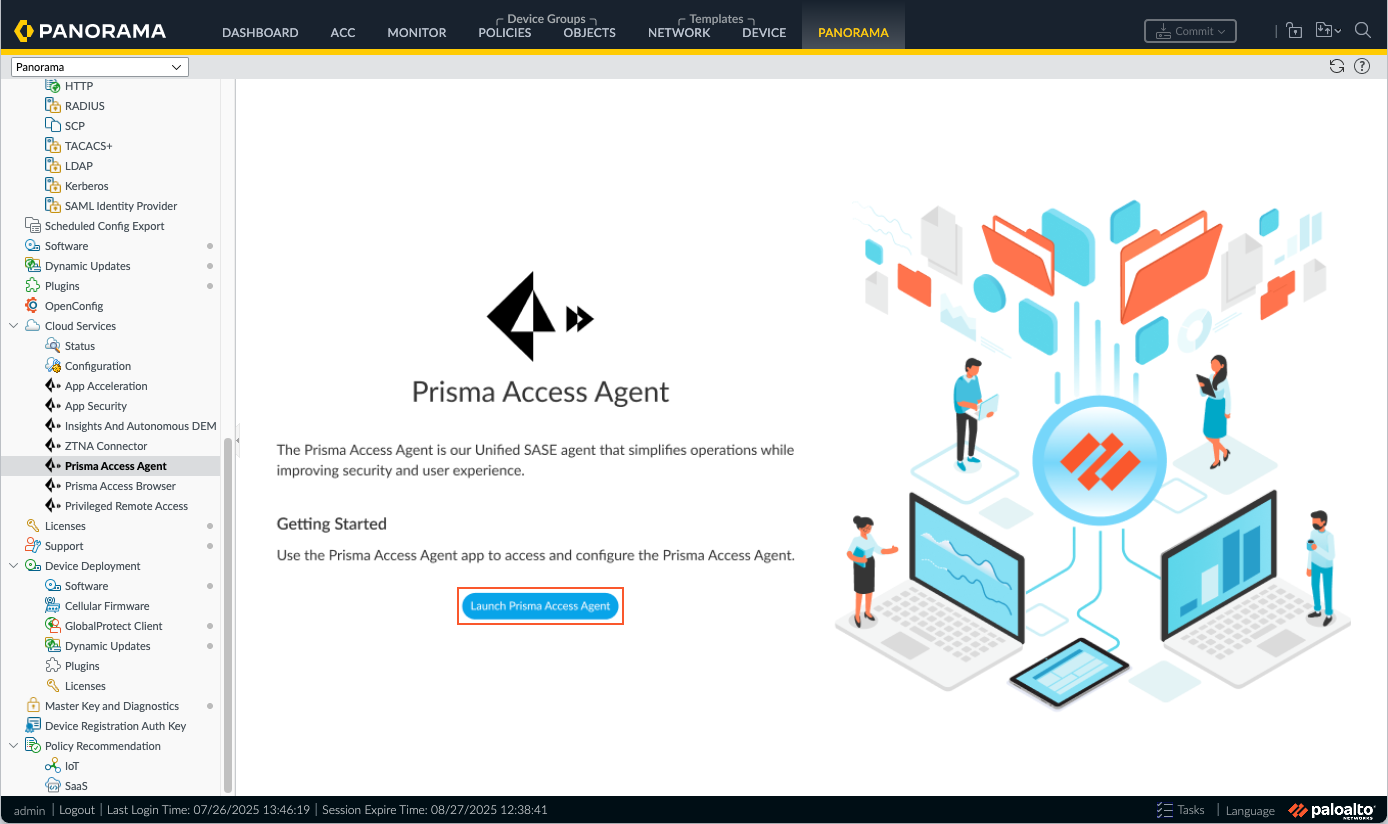
Use Panorama to set up the authentication for Prisma Access Agent users in Prisma Access deployments.For Panorama Managed Prisma Access deployments, you can set up user authentication so that only legitimate Prisma Access Agent users have access to your services and applications.- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access AgentLaunch Prisma Access Agent.
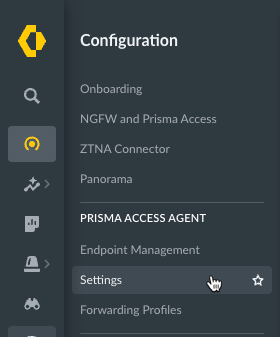
![]() Select ConfigurationPrisma Access AgentSettings.
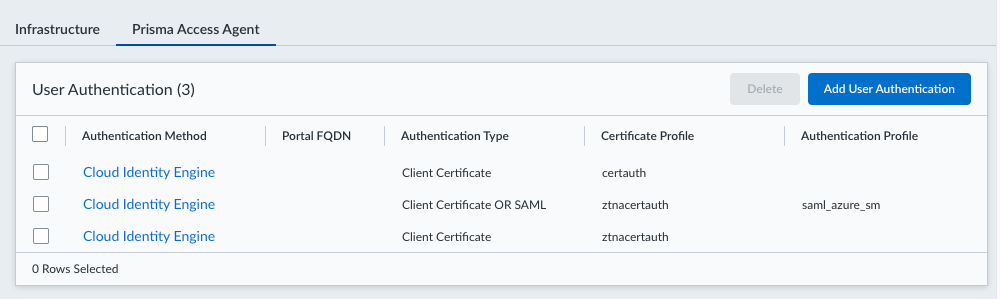
Select ConfigurationPrisma Access AgentSettings.![]() Select the Prisma Access Agent tab.Click Add User Authentication or select an existing user authentication from the table to update it.
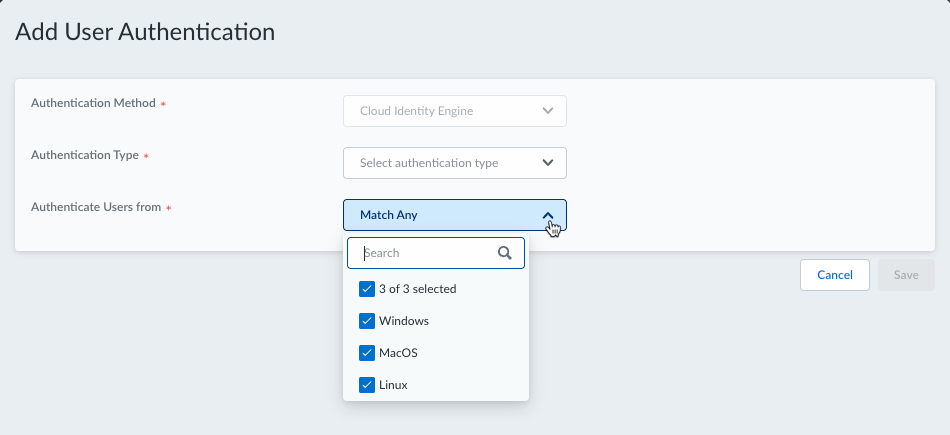
Select the Prisma Access Agent tab.Click Add User Authentication or select an existing user authentication from the table to update it.![]() Select the endpoint operating system to Authenticate Users From. Selecting Match Any will authenticate users from all supported operating systems. The default is Match Any.
Select the endpoint operating system to Authenticate Users From. Selecting Match Any will authenticate users from all supported operating systems. The default is Match Any.![]() Select an Authentication Type.
Select an Authentication Type.![]() The following authentication types are available with Cloud Identity Engine:
The following authentication types are available with Cloud Identity Engine:- SAML—Select this to use SAML 2.0 to integrate Prisma Access with an identity provider (IdP) that controls access to both external and internal services and applications. SAML single sign-on (SSO) enables one login to access multiple applications, and is helpful in environments where each user accesses many applications and authenticating for each one would impede user productivity. In this case, SAML single sign-on (SSO) enables one login to access multiple applications. This is the default selection.
- (Unsupported on Prisma Access Agent Linux) Client Certificate—Select this to use a client certificate from the Cloud Identity Engine to obtain usernames and authenticate Prisma Access Agent users to Prisma Access. To authenticate users based on a client certificate, one of the certificate fields, such as the Subject Name field, must identify the username. End users who successfully authenticate through client certificate authentication don't have the option to sign out of the Prisma Access Agent.
- (Unsupported on Prisma Access Agent Linux) Client Certificate OR SAML—Select this to grant access to end users as long as they have successfully passed either client certificate authentication or SAML authentication.
- (Unsupported on Prisma Access Agent Linux) Client Certificate AND SAML—Select this to require users to pass both certificate authentication and SAML authentication.
Select an Authentication Profile to use for authentication based on the authentication type.- If you're using SAML, select an
Authentication Profile or Create
New. This authentication profile maps to the Cloud Identity Engine authentication profile that validates the login
credentials of end users who access applications and resources using the
Prisma Access Agent.
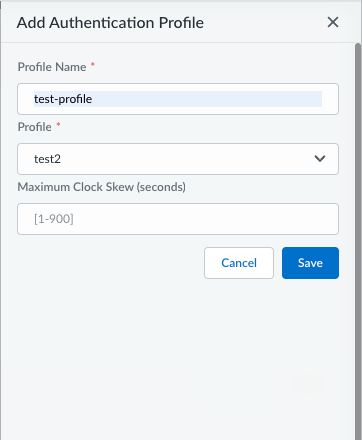
![]() If you're creating a new profile:
If you're creating a new profile:- Click Create New.
- Enter a Profile Name and select an available Cloud Identity Engine Profile.
- (Optional) Enter the Maximum Clock Skew
(seconds), which is the allowed system time
difference (in seconds) between the IdP and Prisma Access
when Prisma Access validates IdP messages. The default value
is 60 seconds, and the range is 1-900 seconds. If the difference
exceeds this value, authentication fails.
![]()
- Save your new profile. The profile is added to the Authentication Profile list.
- Select the profile you created if you want to use it to authenticate your users.
- (Unsupported on Prisma Access Agent Linux) If you're using the Client Certificate authentication type, select a Certificate Profile to verify the certificates that Prisma Access Agent users present to Prisma Access during a connection request. The certificate profile specifies the contents of the username and user domain fields; lists CA certificates; criteria for blocking a session; and offers ways to determine the revocation status of CA certificates.Because the certificate is part of the authentication for the user, you must predeploy certificates used in certificate profiles to your users before their initial login. The certificate profile specifies which certificate field contains the username (Subject or Subject Alt). If the certificate profile specifies Subject in the Username Field, the certificate presented by the endpoint must contain a Common Name for the endpoint to connect. If the certificate profile specifies a Subject-Alt with an Email or Principal Name as the Username Field, the certificate must contain the corresponding fields, which will be used as the username when the Prisma Access Agent authenticates to Prisma Access.
![]()
- (Unsupported on Prisma Access
Agent Linux) If you're using Client
Certificate OR SAML, select a Certificate
Profile and an Authentication
Profile. This will grant access to end users as long as
they have successfully passed either client certificate authentication
or SAML authentication.
![]()
- (Unsupported on Prisma Access Agent Linux) If you're using Client Certificate AND SAML, select a Certificate Profile and an Authentication Profile. This will require users to pass both certificate authentication and SAML authentication.
Save your user authentication settings.
Set Up SAML Authentication with CIE (NGFW Deployment)
Learn how to set up the user authentication for Prisma Access Agent users in NGFW deployments.For Panorama managed NGFW deployments, you can set up user authentication so that only legitimate Prisma Access Agent users have access to your services and applications.- Log in to Strata Cloud Manager as the administrator.Select ConfigurationPrisma Access AgentSettings.
![]() Select the Prisma Access Agent tab.Click Add User Authentication or select an existing user authentication from the table to update it.
Select the Prisma Access Agent tab.Click Add User Authentication or select an existing user authentication from the table to update it.![]() Select the endpoint operating system to Authenticate Users From. Selecting Match Any will authenticate users from all supported operating systems. The default is Match Any.
Select the endpoint operating system to Authenticate Users From. Selecting Match Any will authenticate users from all supported operating systems. The default is Match Any.![]() Select an Authentication Type.
Select an Authentication Type.![]() The following authentication types are available with Cloud Identity Engine:
The following authentication types are available with Cloud Identity Engine:- SAML—Select this to use SAML 2.0 to integrate Prisma Access with an identity provider (IdP) that controls access to both external and internal services and applications. SAML single sign-on (SSO) enables one login to access multiple applications, and is helpful in environments where each user accesses many applications and authenticating for each one would impede user productivity. In this case, SAML single sign-on (SSO) enables one login to access multiple applications. This is the default selection.
- (Unsupported on Prisma Access Agent Linux) Client Certificate—Select this to use a client certificate from the Cloud Identity Engine to obtain usernames and authenticate Prisma Access Agent users to Prisma Access. To authenticate users based on a client certificate, one of the certificate fields, such as the Subject Name field, must identify the username. End users who successfully authenticate through client certificate authentication don't have the option to sign out of the Prisma Access Agent.
- (Unsupported on Prisma Access Agent Linux) Client Certificate OR SAML—Select this to grant access to end users as long as they have successfully passed either client certificate authentication or SAML authentication.
- (Unsupported on Prisma Access Agent Linux) Client Certificate AND SAML—Select this to require users to pass both certificate authentication and SAML authentication.
Select an Authentication Profile to use for authentication based on the authentication type.- If you're using SAML, select an
Authentication Profile or Create
New. This authentication profile maps to the Cloud Identity Engine authentication profile that validates the login
credentials of end users who access applications and resources using the
Prisma Access Agent.
![]() If you're creating a new profile:
If you're creating a new profile:- Click Create New.
- Enter a Profile Name and select an available Cloud Identity Engine Profile.
- (Optional) Enter the Maximum Clock Skew
(seconds), which is the allowed system time
difference (in seconds) between the IdP and Prisma Access
when Prisma Access validates IdP messages. The default value
is 60 seconds, and the range is 1-900 seconds. If the difference
exceeds this value, authentication fails.
![]()
- Save your new profile. The profile is added to the Authentication Profile list.
- Select the profile you created if you want to use it to authenticate your users.
- (Unsupported on Prisma Access Agent Linux) If you're using the Client Certificate authentication type, select a Certificate Profile to verify the certificates that Prisma Access Agent users present to Prisma Access during a connection request. The certificate profile specifies the contents of the username and user domain fields; lists CA certificates; criteria for blocking a session; and offers ways to determine the revocation status of CA certificates.Because the certificate is part of the authentication for the user, you must predeploy certificates used in certificate profiles to your users before their initial login. The certificate profile specifies which certificate field contains the username (Subject or Subject Alt). If the certificate profile specifies Subject in the Username Field, the certificate presented by the endpoint must contain a Common Name for the endpoint to connect. If the certificate profile specifies a Subject-Alt with an Email or Principal Name as the Username Field, the certificate must contain the corresponding fields, which will be used as the username when the Prisma Access Agent authenticates to Prisma Access.
![]()
- (Unsupported on Prisma Access
Agent Linux) If you're using Client
Certificate OR SAML, select a Certificate
Profile and an Authentication
Profile. This will grant access to end users as long as
they have successfully passed either client certificate authentication
or SAML authentication.
![]()
- (Unsupported on Prisma Access Agent Linux) If you're using Client Certificate AND SAML, select a Certificate Profile and an Authentication Profile. This will require users to pass both certificate authentication and SAML authentication.
Save your user authentication settings.