Prisma Access Agent
Configure macOS Platform SSO for Prisma Access Agent
Table of Contents
Configure macOS Platform SSO for Prisma Access Agent
Configure macOS Platform SSO by deploying an SSO extensions configuration profile
through your MDM to authorize agent access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
macOS Platform SSO enables Prisma Access Agent to automatically authenticate users
using their existing macOS device credentials, eliminating separate authentication
prompts while maintaining always-on security protection. This integration leverages
the macOS Single Sign-On Extension framework to provide seamless connectivity
between device login and network access.
When a user logs into their macOS device using supported credentials, the SSO
extension validates these credentials with your identity provider and creates an SSO
token. Prisma Access Agent requests this token from the SSO extension rather than
prompting for separate credentials, establishing the secure connection automatically
without user interaction or browser prompts.
If Platform SSO becomes unavailable due to token expiration, SSO extension
misconfiguration, or connectivity issues, Prisma Access Agent falls back to SAML
authentication. The system notifies the user of the authentication issue and prompts
for manual credential entry to maintain connectivity.
Required Components
To deploy macOS Platform SSO with Prisma Access Agent, you need several components
working together:
- Identity Provider (IdP): Your environment must use an identity provider (IdP) that supports macOS Platform SSO such as Microsoft Entra ID or Okta.
- Mobile Device Management (MDM): An MDM solution such as Microsoft Intune or Jamf manages and deploys the SSO extension profiles to macOS devices. The MDM pushes configuration profiles that define SSO policies and configure the connection between the device and your identity provider.
- Platform SSO Configuration Profile: The SSO extensions configuration profile contains the configuration settings that enable Platform SSO on macOS devices. This profile specifies the identity provider endpoints, authentication methods, token handling parameters, and which applications are authorized to use SSO tokens.
- Managed macOS Devices: Target devices must run macOS 14 or later and be enrolled in your MDM solution.
Limitation with Traffic Forwarding and macOS Platform SSO
When macOS Platform SSO is enabled and the agent requires token refresh while traffic
enforcement policies are active, authentication traffic from the SSO application
becomes subject to existing traffic steering restrictions. You must configure a forwarding rule to allow all
network addresses required by your identity provider's SSO application, including
any potential redirection endpoints, to ensure successful authentication flow
completion, obtain a refreshed token from the IdP, and subsequently establish the
agent connection using that token. While your MDM configuration provides most
required addresses, additional redirections during authentication may occur that
cannot be automatically identified. You are responsible for identifying and allowing
all SSO-related network connections in your forwarding profile configuration to
prevent authentication failures.
The following procedure shows how to configure a Platform SSO configuration profile
for Prisma Access Agent. It has been qualified for Jamf Pro using the Intune Company
Portal extension with Entra ID as the IdP:
- (Optional) To prevent the Prisma Acesss Agent embedded browser from appearing momentarily during single sign-on, configure the Agent Settings in Strata Cloud Manager as follows:
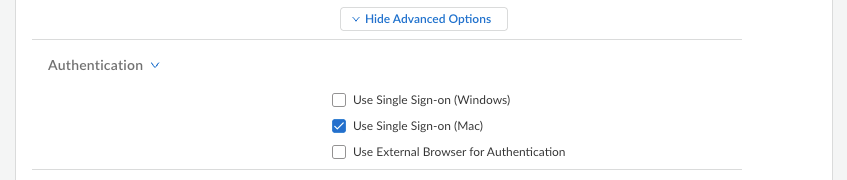
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.Add or update an existing agent setting.In the App Configuration section, select Show Advanced OptionsAuthentication and enable Use Single Sign-on (Mac).
![]() Save and push your configuration updates.Configure a platform SSO configuration profile for Microsoft Entra ID using Jamf Pro.
Save and push your configuration updates.Configure a platform SSO configuration profile for Microsoft Entra ID using Jamf Pro.- Fill in the General configuration profile information.Select the Single Sign-On Extensions payload and Add a single sign-on extension with the following properties:
- Payload Type = SSO
- Extension Identifier = com.microsoft.CompanyPortalMac.ssoextension
- Team Identifier = UBF8T346G9
- Sign-on Type = Redirect
- URLs: Specify all the URLs listed here that macOS should redirect to the Company Portal app for authentication.
- Use Platform SSO = Enabled
- Custom Configuration: Add
com.paloaltonetworks. to the
AppPrefixAllowList key in the PLIST file.
For
example:
<?xml version="1.0" encoding="UTF-8"?> <plist version="1.0"> <dict> <key>AppPrefixAllowList</key> <string>[existing_strings],com.paloaltonetworks.</string> <key>browser_sso_interaction_enabled</key> <integer>1</integer> <key>disable_explicit_app_prompt</key> <integer>1</integer> </dict> </plist>
Deploy the configuration profile.Assign the completed SSO extension profile to the appropriate computer or computer groups that should receive Platform SSO functionality. Ensure that the profile deployment scope includes all devices where Prisma Access Agent will use seamless authentication.If not done already, Configure the Jamf policy for Prisma Access Agent deployment.Verify the configuration.After deploying the SSO extension profile, test the configuration by having a user log into their macOS device and observe the Prisma Access Agent authentication behavior. The agent should connect automatically without prompting for credentials.Check the agent logs to confirm that SSO token retrieval is successful and that authentication completes using the Platform SSO mechanism. If authentication fails, verify that the AppPrefixAllowList includes the correct Palo Alto Networks application identifier and that the SSO extension is properly communicating with your identity provider.