Prisma Access Agent
Create a Device Profile with Prisma Access Agent for iOS Endpoints Using Microsoft Intune
Table of Contents
Create a Device Profile with Prisma Access Agent for iOS Endpoints Using Microsoft Intune
Create a Device Profile with Prisma Access Agent for iOS Endpoints Using Microsoft
Intune
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You must create a device profile and configure Prisma Access
Agent in the VPN settings of the profile using
Microsoft Intune with desired authentication method and connect method. When you
deploy the Prisma Access Agent, these settings are pushed to your managed iOS
endpoints and based on these settings, the Prisma Access Agent connection is
established for you to access your organization’s network.
On the Microsoft Intune admin center
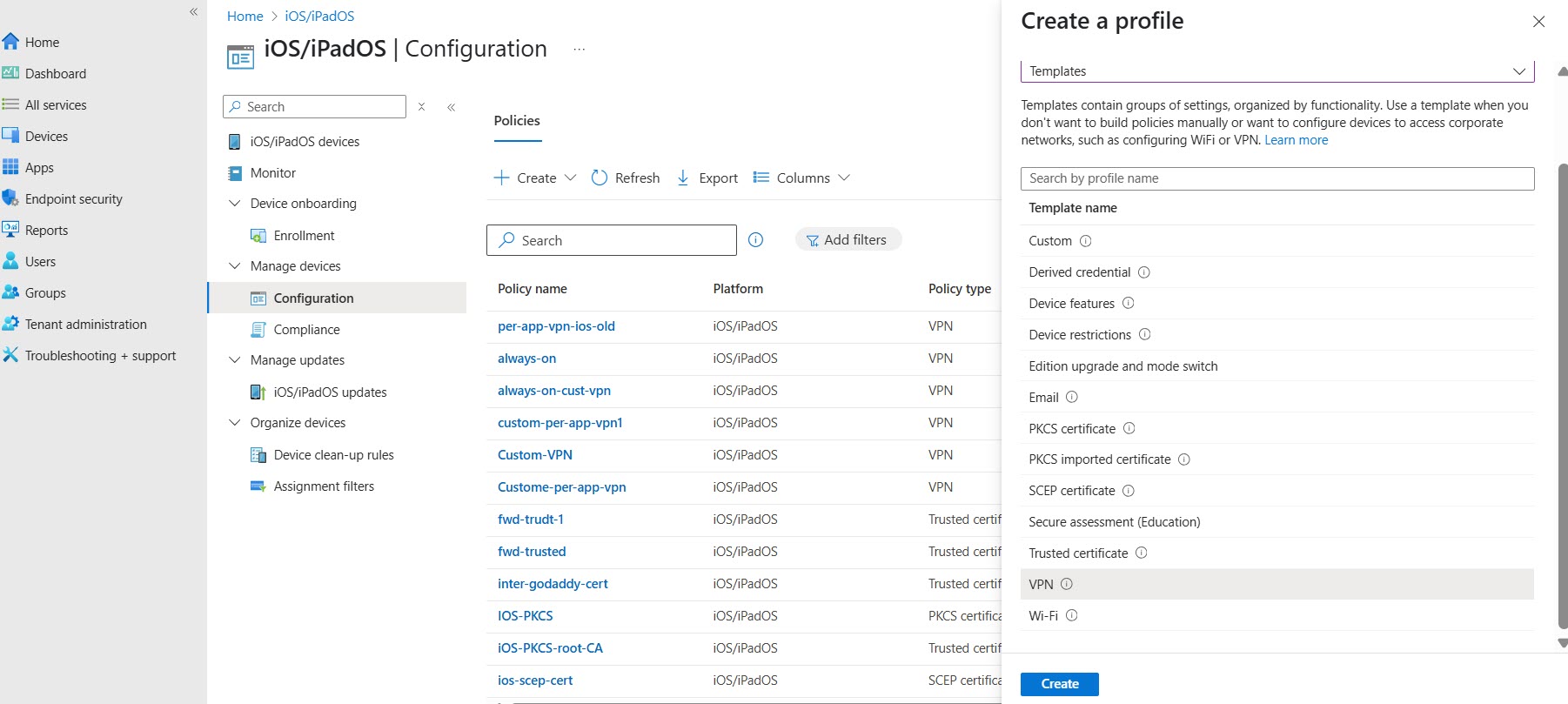
- On the Microsoft Intune admin center, click Devices iOS/iPadOSManage Devices Configuration.Click CreateNew Policy.Select profile type to Template and select VPN as the template name.Click Create to create VPN settings for Prisma Access Agent.
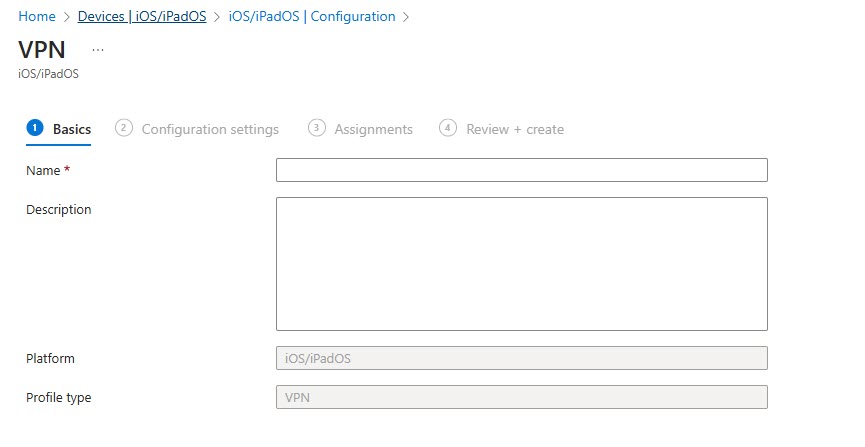
![]() In the Basics tab, enter a name and description and click Next.
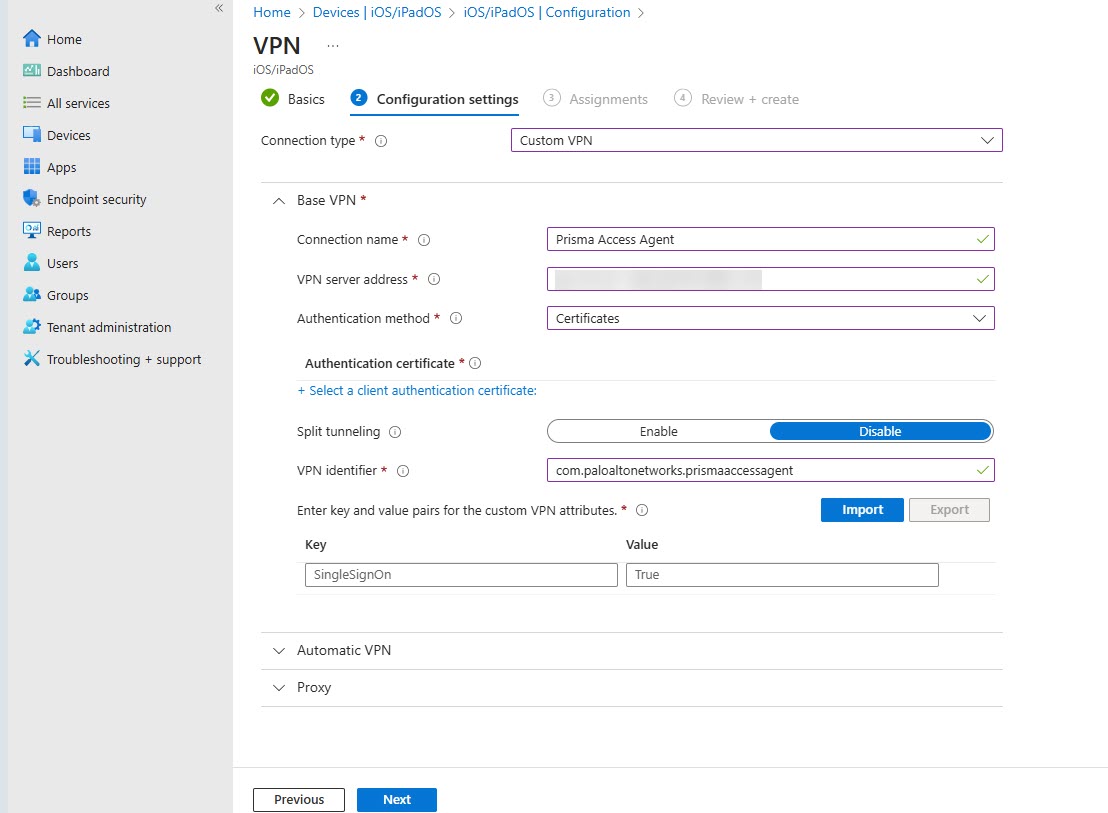
In the Basics tab, enter a name and description and click Next.![]() In the Configuration settings tab, specify the connection type as Custom VPN.Expand the Base VPN section and specify the following details:
In the Configuration settings tab, specify the connection type as Custom VPN.Expand the Base VPN section and specify the following details:- Enter the Connection name will be displayed to end users on their endpoints.In the VPN server address, specify the server address of the Prisma Access Agent Manager.Select the authentication method as per your requirement. If you are using Certificates to authenticate to the app, you must push the certificate to the endpoints. The supported authentication methods are:
Authentication Method Steps SAML authenticationSet authentication method to Username and password. You must select the Username and password and leave the fields blank.Local authentication is not supported.Certificates- Set authentication method to Certificates.
- Select the SCEP certificate to authenticate the connection.
You can leave the Split tunneling option blank. If you desire split-tunneling, then Per-App configuration is recommended.Specify the VPN Identifier as com.paloaltonetworks.prismaaccessagent .Enter key-value pairs for your organization's custom VPN attributes. The following pairs are supported on Microsoft Intune for iOS devices.Key Value Type Description Example tag String Tag to identify devices in security policies. You can specify any value for this parameter, it will appear in the HIP report and can be used to create security policies with.GuestAccount, HRdeparment compliance String Tag to identify devices in security policies. You can specify any value for this parameter, it will appear in the HIP report and can be used to create security policies with.yes ownership String Tag to identify devices in security policies. You can specify any value for this parameter, it will appear in the HIP report and can be used to create security policies with.corporation owned Expand the Automatic VPN section and configure one of the connect methods as required.Connect Method Configuration On-Demand Users must manually open the Prisma Access Agent to initiate a connection.Set Type of Automatic VPN to Not Configured.Always-On Automatically connects Prisma Access Agent.- Set Type of Automatic VPN to On-demand VPN.
- Add an on-demand rule by clicking Add.
- Set I want to do the following to connect VPN.
- Set I want to restrict to All domains.
- Click Save.
Per-App In a per-app configuration, you can configure the managed apps that will route traffic through Prisma Access Agent. When the users access the managed app, Prisma Access Agent will automatically connect and only traffic for the managed apps you have configured under the configuration profile will be routed through Prisma Access Agent.You can attach VPN profile to an app, add URLs for the app you want access to, or do a combination of both.To add app URLs:- Type of Automatic VPN to Per-app VPN.
- Add one or more website URLs. When these URLs are visited using the Safari browser on the device, the VPN connection is automatically established.
- Enter Associated Domains to use with Prisma Access Agent.
- In Excluded Domains, enter Safari domains that can bypass Prisma Access Agent for the per-app connect method. Traffic to the excluded domains uses the public internet even if Prisma Access Agent is connected.
- You can Block users from disabling automatic VPN.
![]() Click Next.Assign user groups and device groups to the device profile. To deploy the policy broadly to all applicable devices, select Add all users or Add all devices.Click Next.Review the policy summary and click Create to create the device configuration profile.
Click Next.Assign user groups and device groups to the device profile. To deploy the policy broadly to all applicable devices, select Add all users or Add all devices.Click Next.Review the policy summary and click Create to create the device configuration profile.