Prisma Access
Integrate Prisma Access with HPE Aruba Networking EdgeConnect SD-WAN
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Integrate Prisma Access with HPE Aruba Networking EdgeConnect SD-WAN
Learn how to integrate Prisma Access with HPE Aruba Networking EdgeConnect SD-WAN
(Siver Peak)
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Organizations leveraging HPE Aruba Networking EdgeConnect SD-WAN (formerly
Silver Peak) can seamlessly integrate with Prisma Access to enhance branch internet
traffic security. This integration simplifies the onboarding of Remote Networks
(with aggregate bandwidth) using IPSec tunnels between HPE Aruba Networking
EdgeConnect SD-WAN devices and Prisma Access, promoting wider adoption.
The solution simplifies tunnel creation across multiple devices, ensures
consistent configurations, and uses automated WAN interface selection and automated
IPSec termination node selection—enabling secure, scalable connectivity without
manual intervention. This automated approach supports various tunnel topologies,
making integration seamless, reliable, and easier to scale.
The integration supports tunnel formation from up to two user-selected
WAN links per SD-WAN device to a maximum of two Prisma Access compute locations.
To onboard the HPE Aruba Networking EdgeConnect SD-WAN devices manually,
see Integrate Prisma Access with HPE Aruba Networking EdgeConnect
SD-WAN (Manual Integration).
Ensure you meet the following requirements before you integrate Prisma
Access with HPE Aruba Networking EdgeConnect SD-WAN:
| Product | Requirement |
|---|---|
| Prisma Access |
|
| HPE Aruba Networking EdgeConnect SD-WAN |
|
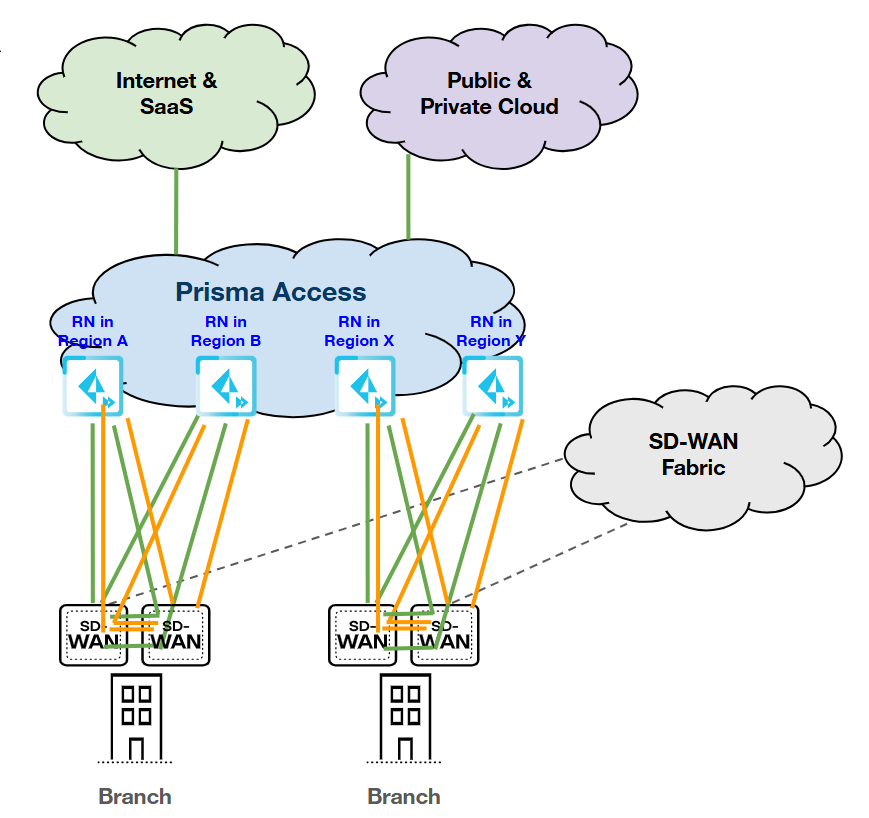
HPE Aruba Networking EdgeConnect SD-WAN Topologies
This section outlines several topology options for integrating HPE Aruba
Networking EdgeConnect SD-WAN with Prisma Access. The integration supports a
range of deployment scenarios—from simple single-tunnel setups to complex
high-availability configurations—allowing you to select the most suitable design
based on your network architecture, redundancy requirements, and performance
goals.
| Use Case | Architecture |
|---|---|
|
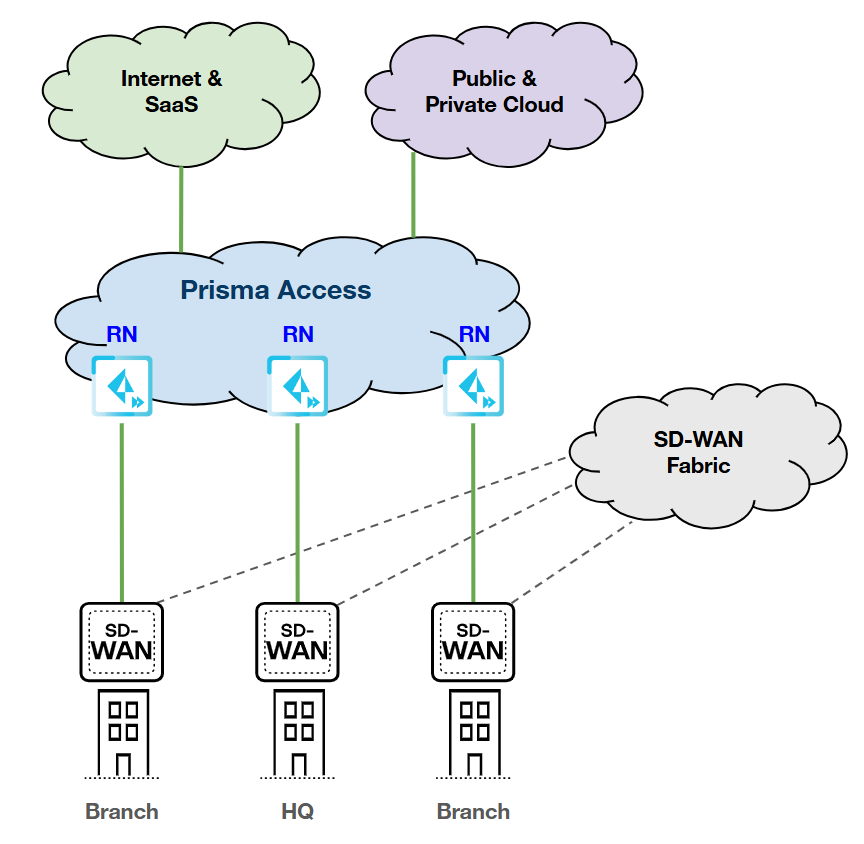
Single Device; Single Link (Primary); Single
RN-SPN
HPE SD-WAN:
Prisma Access:
|
|
|
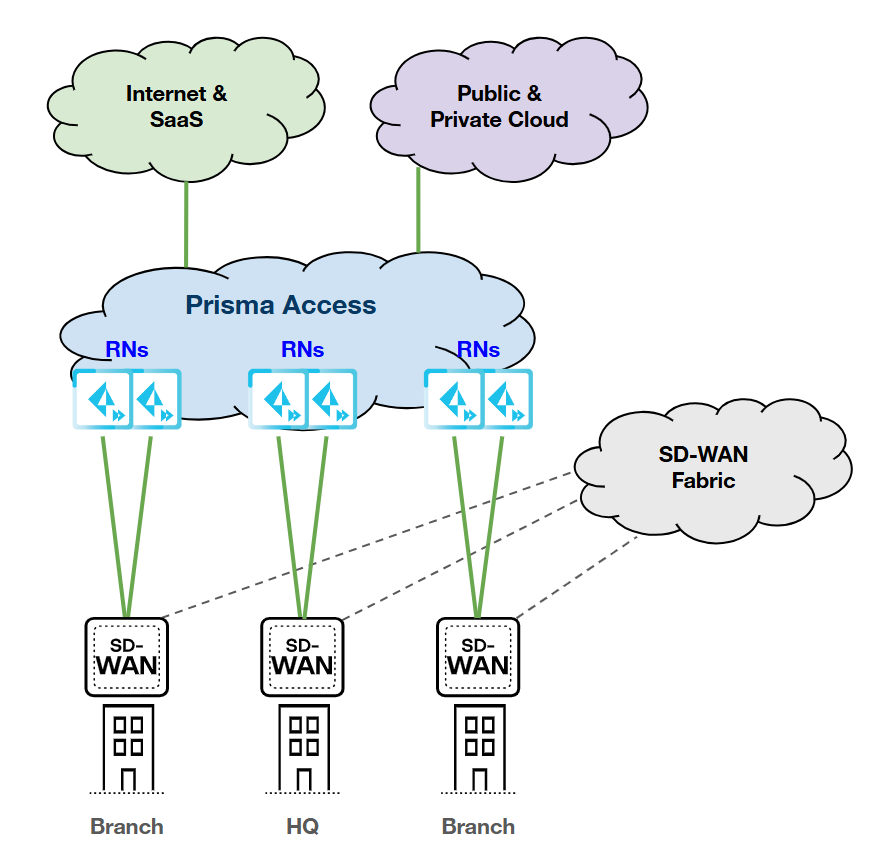
Single Device; Single Link (Primary); Dual RN-SPNs
HPE SD-WAN:
Prisma Access:
|
|
|
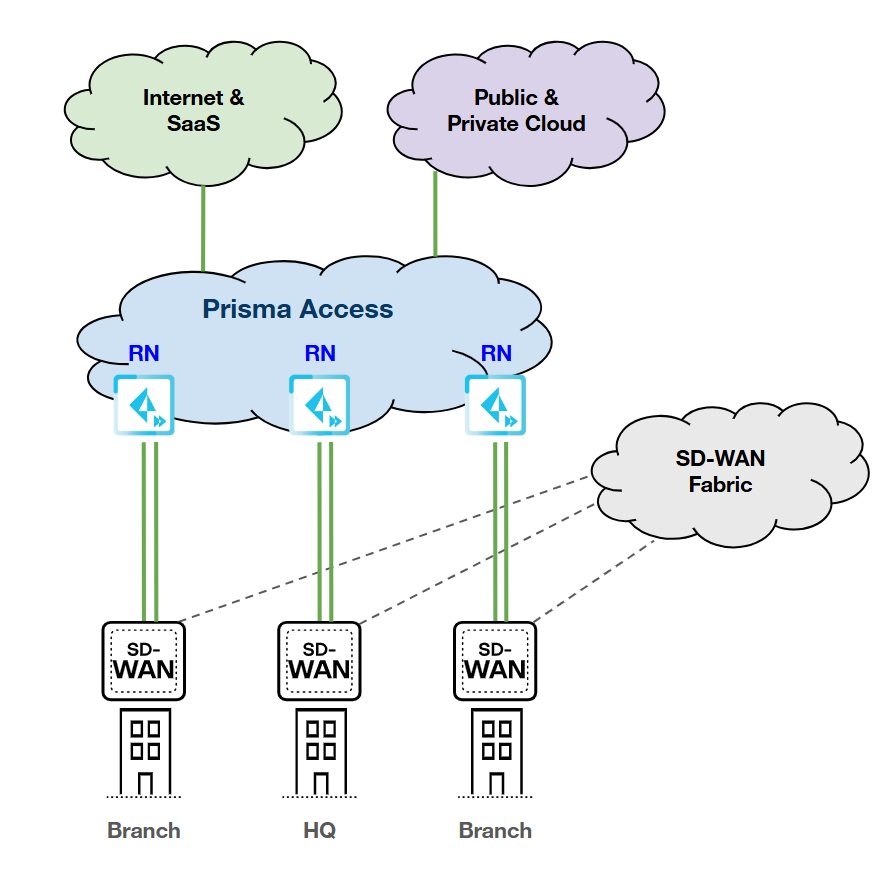
Single Device; Dual Links (Primary/Primary); Single
RN-SPN
HPE SD-WAN:
Prisma Access:
|
|
|
Single Device; Dual Links (Primary/Primary);
Dual RN-SPNs
HPE SD-WAN:
Prisma Access:
|
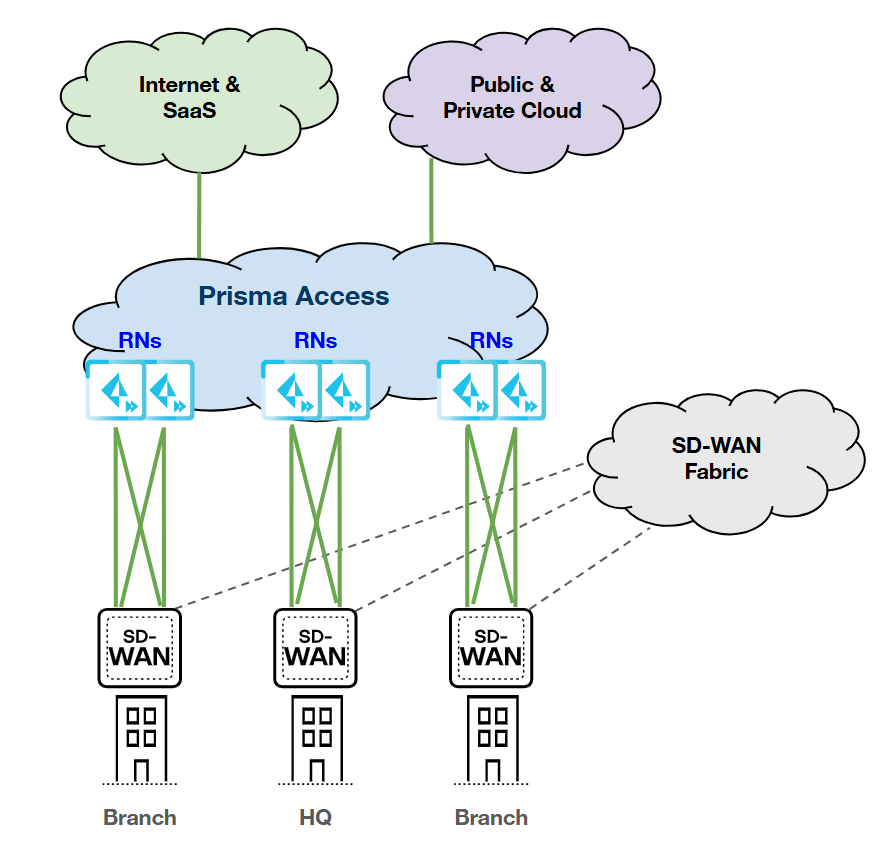
|
|
Single Device; Dual Links (Primary/Backup);
Single RN-SPN
HPE SD-WAN:
Prisma Access:
|
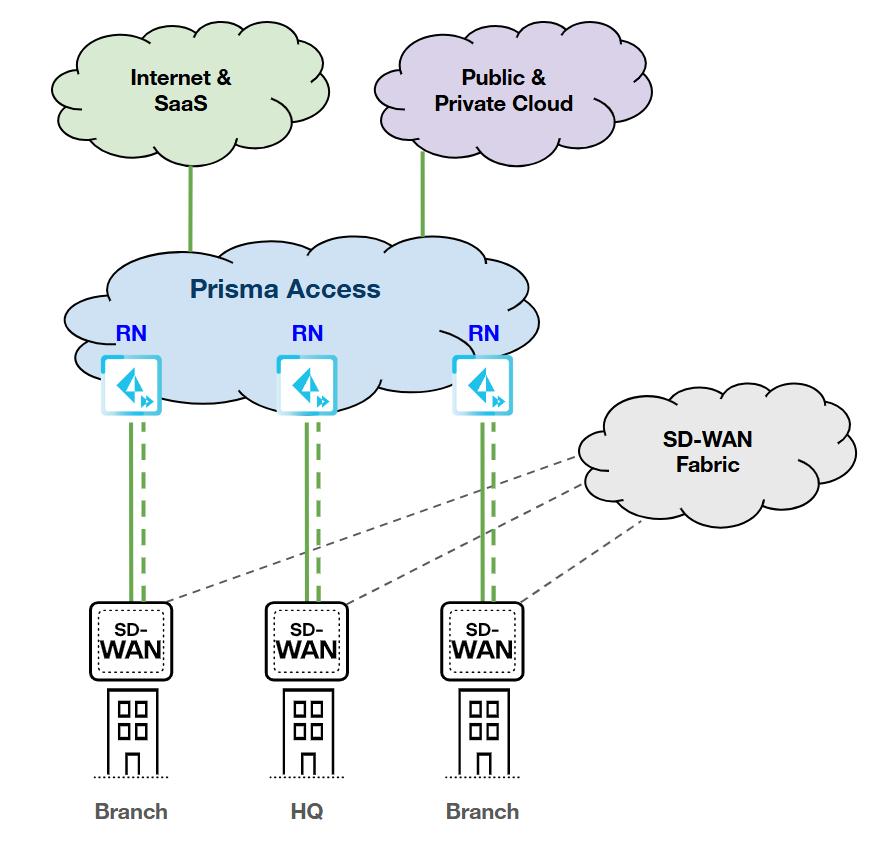
|
|
Single Device; Dual Links (Primary/Backup); Dual
RN-SPNs
HPE SD-WAN:
Prisma Access:
|
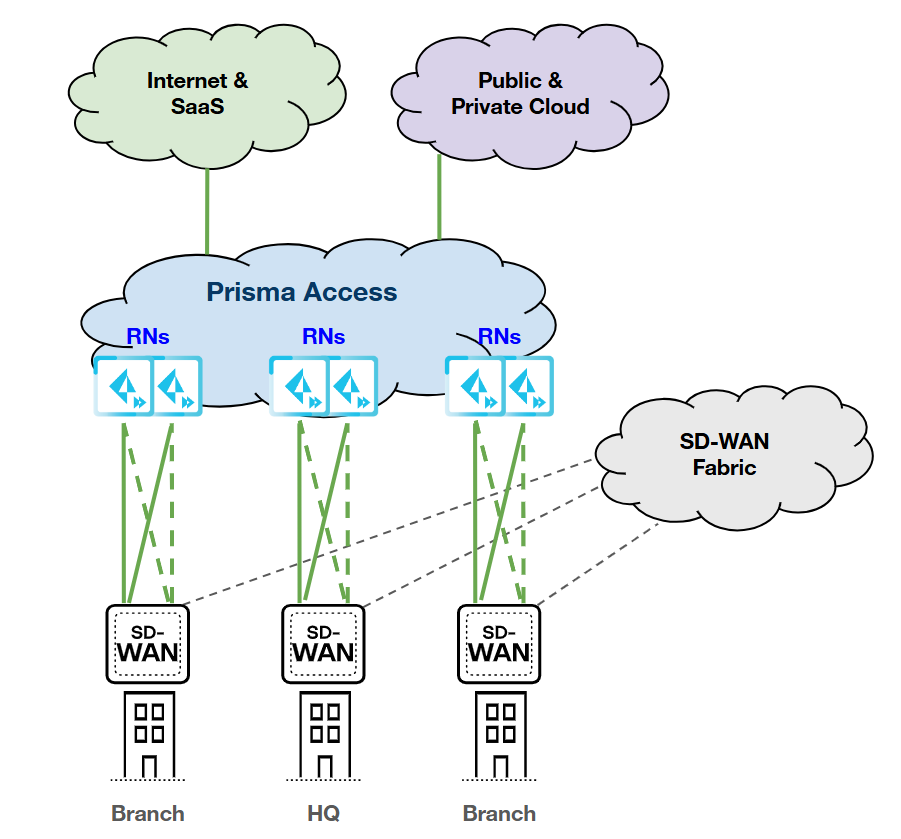
|
|
Dual Devices; Dual Links (Primary/Primary); Single
RN-SPN
HPE SD-WAN:
Prisma Access:
|
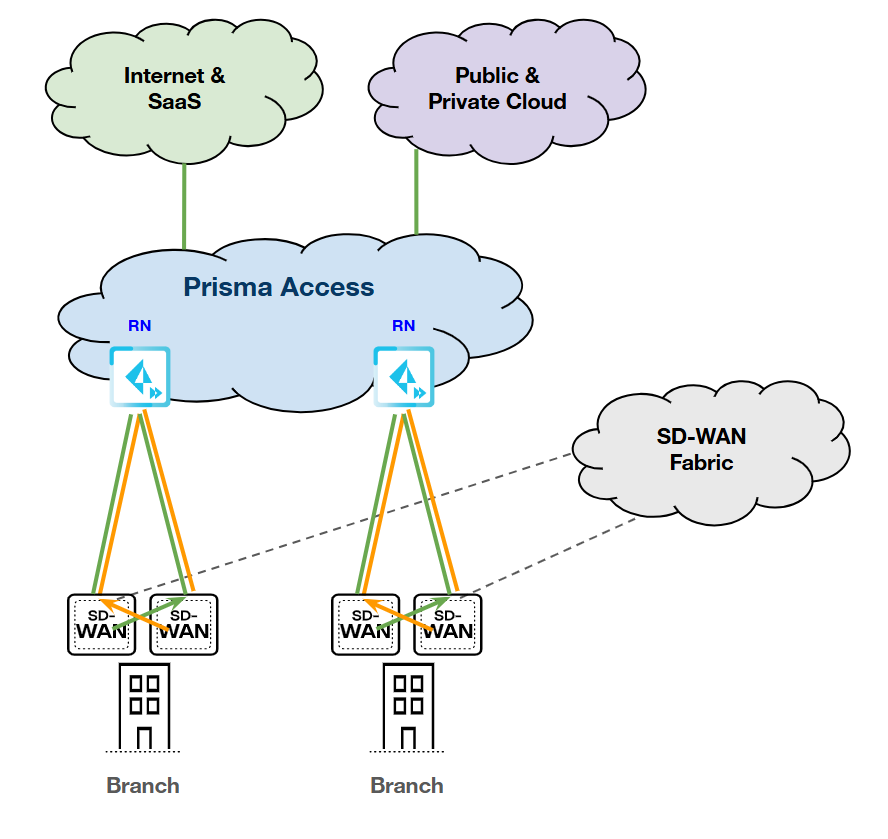
|
|
Dual Devices; Dual Links (Primary/Primary); Dual
RN-SPNs
HPE SD-WAN:
Prisma Access:
|
|
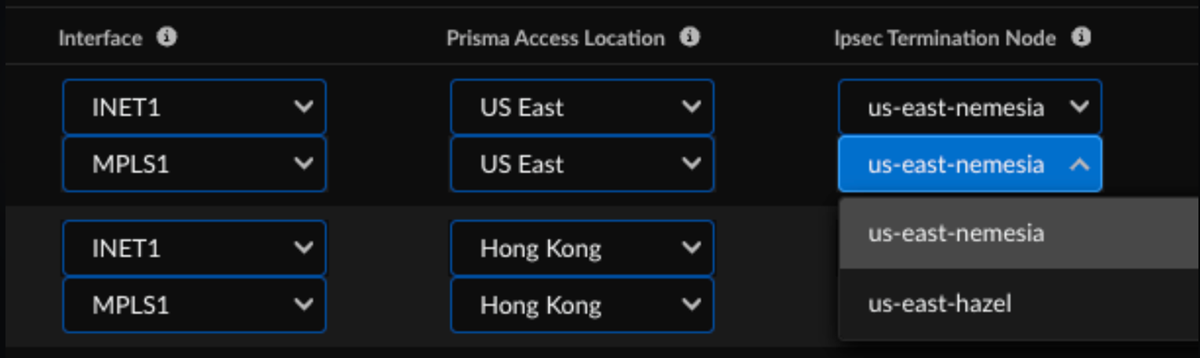
The HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access integration
automatically assigns a Device Interface (link), nearest Prisma Access location,
and IPSec termination nodes, however you can manually select different
interfaces (links), locations or nodes, if needed. Based on the topology
redundancy type and selected IPSec Termination nodes, the corresponding tunnels
will be created. For topologies requiring a single IPSec Termination node,
ensure that the same node is selected for both rows displayed in the UI.
| Redundancy Type | Number of Interface Labels on Device | Number of IPSec Termination Nodes Selected | Number of Tunnels |
|---|---|---|---|
| Single WAN | 1 | 1 |
After you enable the device, the integration
creates 1 tunnel to the IPSec termination node.
|
| Single WAN | 1 | 2 (same or different regions). |
After you enable the device, the integration
creates 2 tunnels to 2 IPSec termination nodes.
|
| Primary/Primary | 2 (both Interfaces are active) | 1 |
After you enable the device, the integration
creates 2 tunnels to the IPSec termination node.
|
| Primary/Primary | 2 (both Interfaces are active) | 2 (same or different regions). |
After you enable the device, the integration
creates 4 tunnels to 2 IPSec termination nodes.
|
| Primary/Backup | 2 (1 active and 1 backup Interface) | 1 |
After you enable the device, the integration creates 2
tunnels to the IPSec termination node.
|
| Primary/Backup | 2 (1 active and 1 backup Interface) | 2 (same or different regions). |
After you enable the device, the integration
creates 4 tunnels to 2 IPSec termination nodes.
|
| Device HA | 2 (1 active Interface in each device) | 1 |
After you enable the device, the integration
creates 4 tunnels to the IPSec termination node.
|
| Device HA | 2 (1 active Interface in each device) | 1 or 2 (same or different regions). |
After you enable the device, the integration
creates 8 tunnels to 2 IPSec termination nodes.
|
Integrate HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access
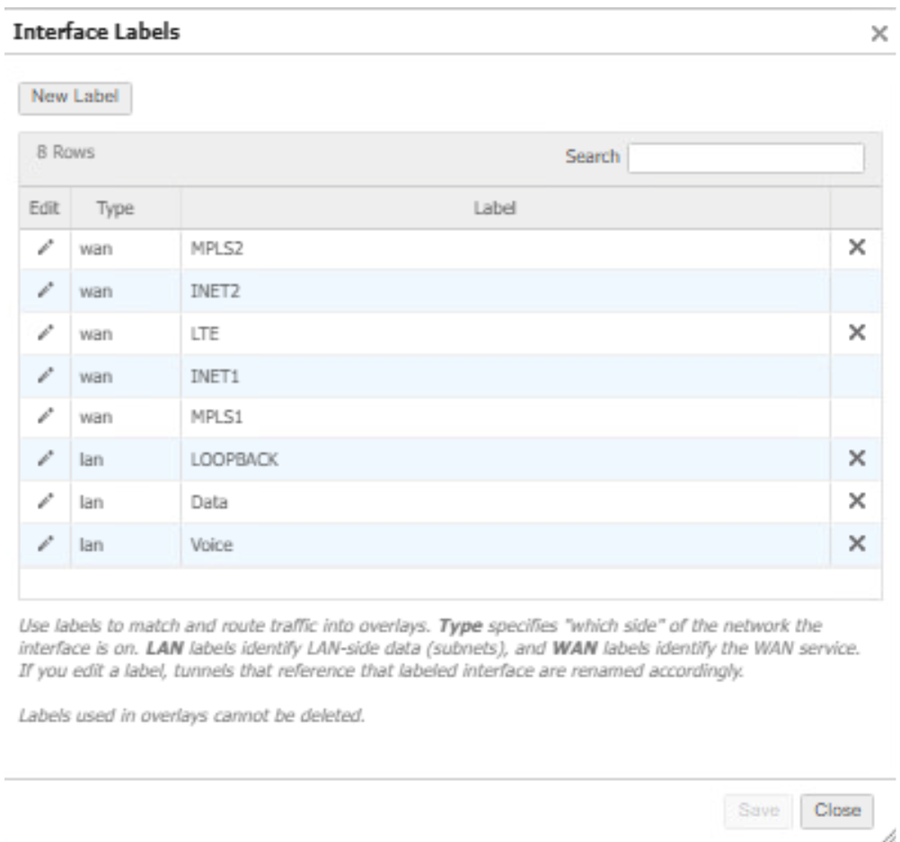
- Configure Interface labels in HPE Aruba Networking EdgeConnect SD-WAN.
- Configure valid LAN and WAN type interface labels to form IPSec tunnels to Prisma Access.
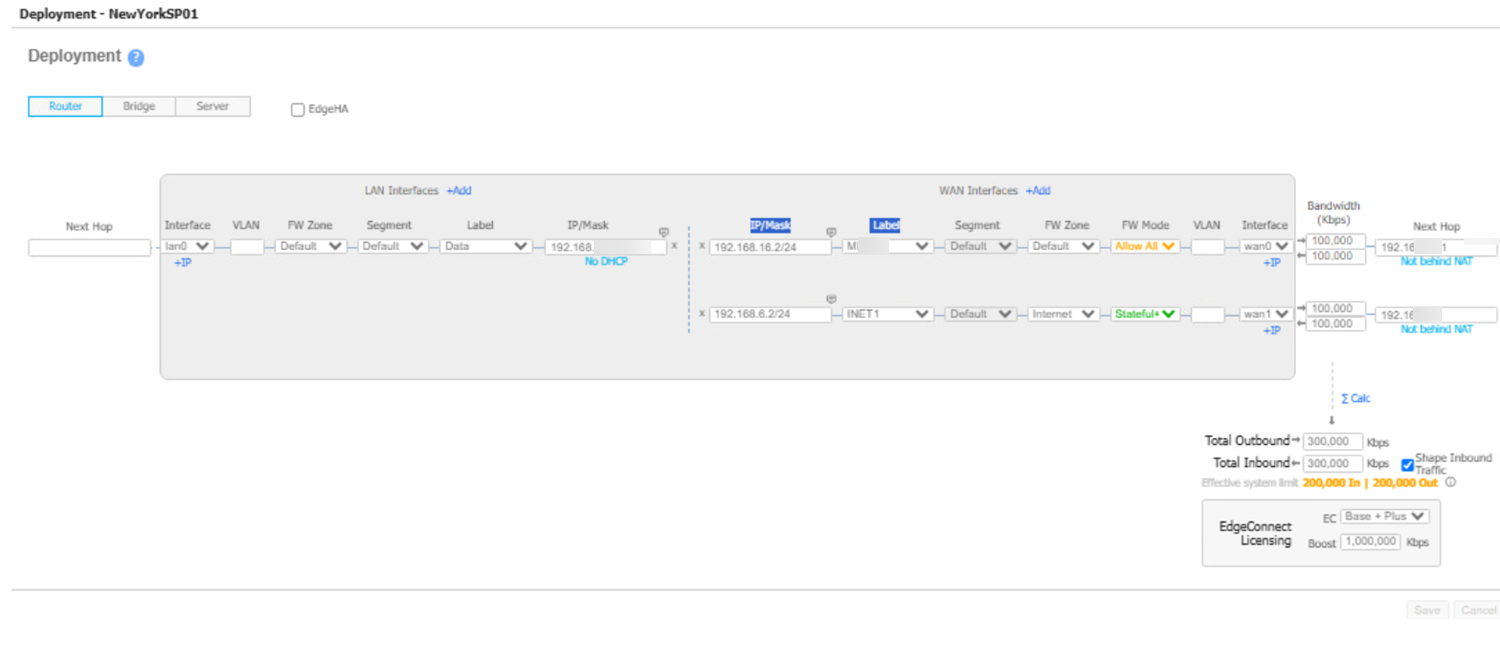
![]() Deploy the devices with appropriate labels; the integration application will later determine the topology for the device based on the WAN type Interface labels added on to the device deployment page.
Deploy the devices with appropriate labels; the integration application will later determine the topology for the device based on the WAN type Interface labels added on to the device deployment page.![]() Configure the HPE Aruba Networking EdgeConnect integration settings in Strata Cloud Manager.
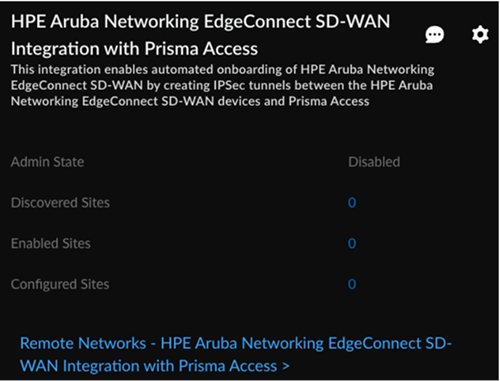
Configure the HPE Aruba Networking EdgeConnect integration settings in Strata Cloud Manager.- Go to System SettingsIntegrations.
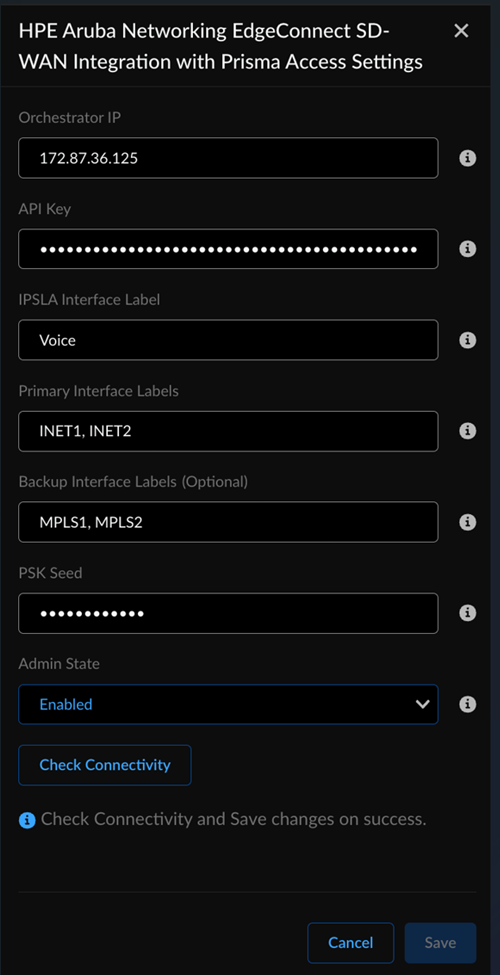
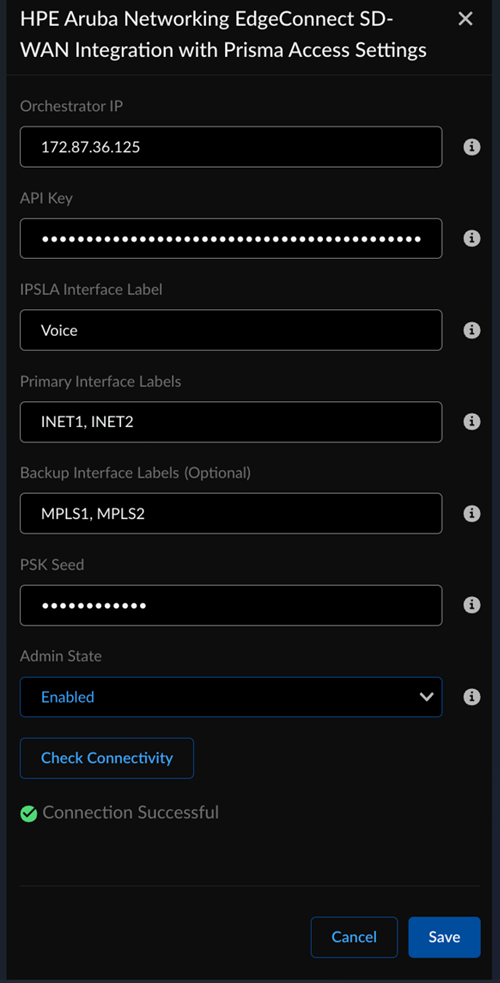
![]() Locate HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access.Click the Settings icon and add the following values on the HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access page.
Locate HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access.Click the Settings icon and add the following values on the HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access page.![]()
- IP: Enter the HPE Aruba Networking EdgeConnect instance IP address (Ex: 172.87.36.107).
- API Key: In HPE Aruba Networking EdgeConnect SD-WAN, generate an API key with the role set to SuperAdmin and leave the expiry field blank.
- IPSLA Interface Label: Enter a LAN type Interface label (case sensitive) from step1 for IPSLA configurations.
- Primary Interface Label: Specify the Interface Labels to be chosen as Primary from the previous step as comma separated values (case-sensitive). Example: INET1, MPLS1.
- (Optional) Backup Interface Labels: Specify the Interface Labels to be chosen as Backup from the previous step as comma separated values (case-sensitive). Example: INET2, MPLS2.
- (Optional) Local Identifier:
Enter an FQDN IKE identifier as the Local Identifier in the
following syntax: name@domain.com default
value: hpe-tunnel@paloaltonetworks.com.This identifier acts as a template to generate a unique ID per tunnel.
- (Optional) Remote Identifier: Enter an FQDN IKE identifier different from the Local Identifier as the Remote Identifier in the following syntax: name@domain.com default value: prisma-tunnel@paloaltonetworks.com.
- PSK Seed: Enter the PSK seed, which
is a string used to derive pre-shared keys (PSKs) per
tunnel. This is a required input as the PSK is typically used to automatically generate PSKs for the IPSec tunnels.
- Admin State: Select the Admin state
to Enabled.
- Enabled: Enables the integration to discover new devices on HPE Aruba Networking EdgeConnect SD-WAN that are eligible for tunnel formation with Prisma Access
- Paused: In the paused state, all integration activity is temporarily stopped. However, the configurations that have already been set up by the integration remain intact. This means that existing connections and policies are not affected, but no new changes will be made.
- Disabled: Disable the
integration to remove all configurations created in
Prisma Access as well as in HPE Aruba Networking
EdgeConnect SD-WAN, when a tunnel was set up between
them. Disabling the integration will bring down all tunnel formations and delete all passthrough tunnels created by the Integration Application in HPE Aruba Networking EdgeConnect SD-WAN. It must be done with caution.
Check Connectivity to verify the connection and Save the changes.![]() You can save changes only after you check connectivity each time you change the settings or configurations.This triggers a discovery process which finds eligible devices from HPE Aruba Networking EdgeConnect SD-WAN and shows them in the integration application dashboard.
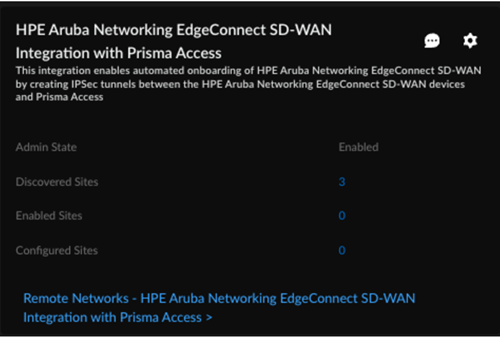
You can save changes only after you check connectivity each time you change the settings or configurations.This triggers a discovery process which finds eligible devices from HPE Aruba Networking EdgeConnect SD-WAN and shows them in the integration application dashboard.![]() After the discovery (periodic/on-demand) run of SD-WAN devices, the integration identifies the nearest Prisma Access location based on each device's geographic location, selects an appropriate location, and determines the device's redundancy type based on the supported topologies.
After the discovery (periodic/on-demand) run of SD-WAN devices, the integration identifies the nearest Prisma Access location based on each device's geographic location, selects an appropriate location, and determines the device's redundancy type based on the supported topologies.![]()
![]() In Strata Cloud Manager, establish the tunnel setup between Prisma Access and HPE Aruba Networking EdgeConnect SD-WAN devices.
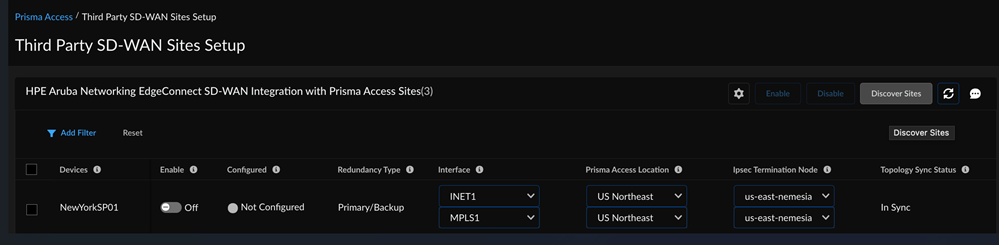
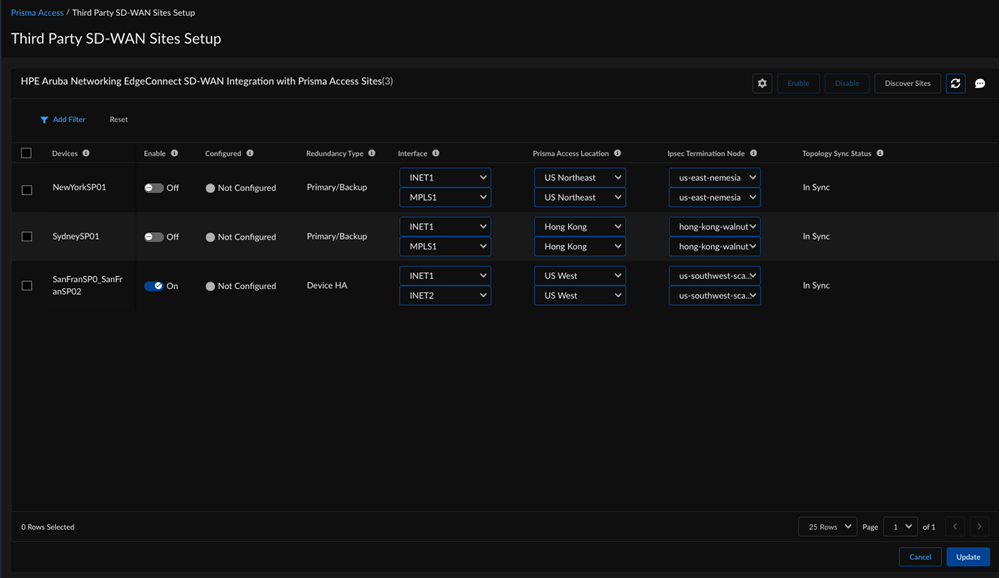
In Strata Cloud Manager, establish the tunnel setup between Prisma Access and HPE Aruba Networking EdgeConnect SD-WAN devices.- Select the site count to view the discovered HPE Aruba Networking EdgeConnect SD-WAN devices and their information.
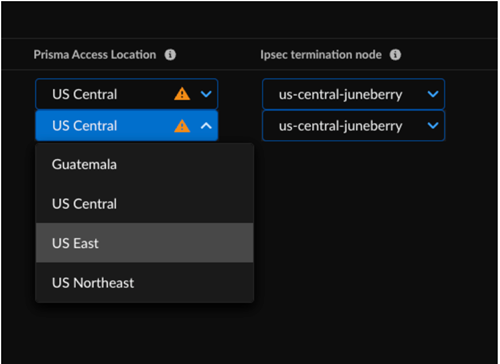
![]() The integration regularly checks for new HPE Aruba Networking EdgeConnect SD-WAN devices. You can also initiate an On-Demand Site Discovery.(Optional) Select the Interface for the device.(Optional) Select the nearest Prisma Access Location for the devices.(Optional) Select IPSec Termination Node for each site.If you select the same Prisma Access location for multiple devices, make sure to allocate bandwidth equally by choosing different IPSec termination nodes for each device sharing that location.Select the HPE Aruba Networking EdgeConnect SD-WAN device and toggle the Enable option to establish tunnel formation with Prisma Access.
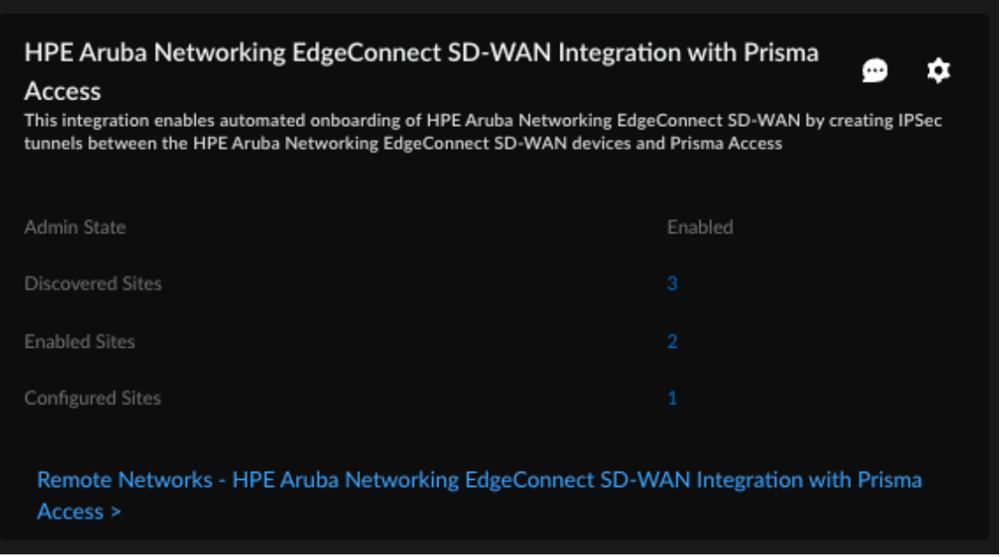
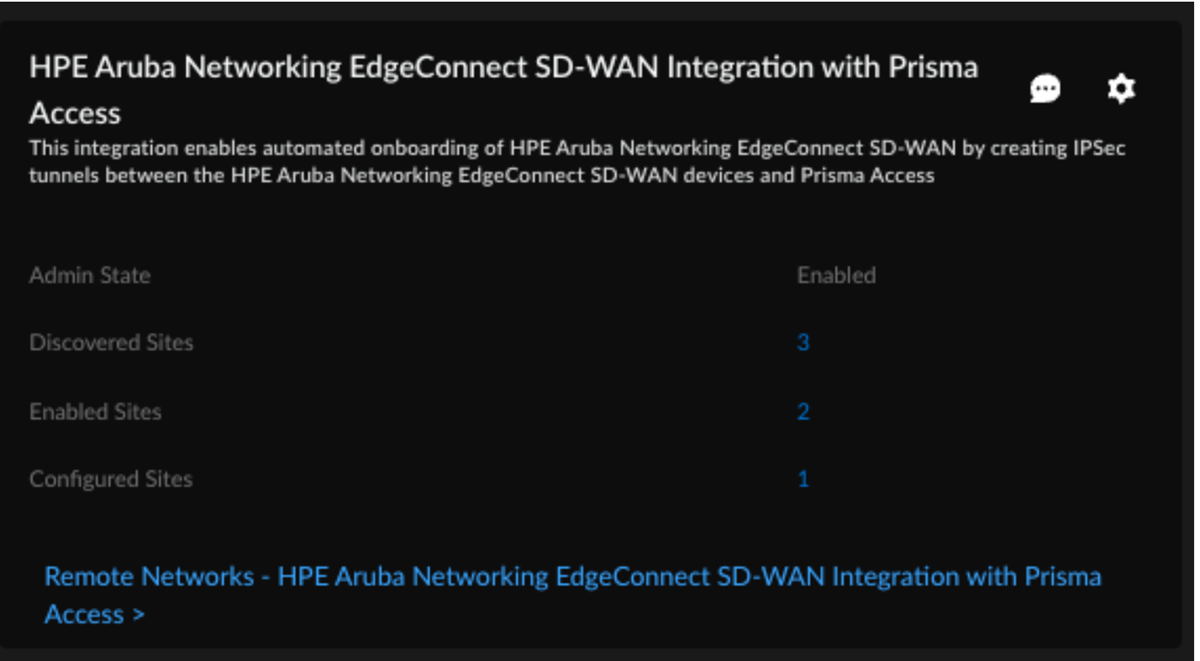
The integration regularly checks for new HPE Aruba Networking EdgeConnect SD-WAN devices. You can also initiate an On-Demand Site Discovery.(Optional) Select the Interface for the device.(Optional) Select the nearest Prisma Access Location for the devices.(Optional) Select IPSec Termination Node for each site.If you select the same Prisma Access location for multiple devices, make sure to allocate bandwidth equally by choosing different IPSec termination nodes for each device sharing that location.Select the HPE Aruba Networking EdgeConnect SD-WAN device and toggle the Enable option to establish tunnel formation with Prisma Access.![]() Update the changes.You can view the Enabled Sites and Configured Sites in the HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access system settings page.
Update the changes.You can view the Enabled Sites and Configured Sites in the HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access system settings page.![]() When you click a site count, the hyperlink opens a filtered list of sites based on that count.Verify the changes in Prisma Access.
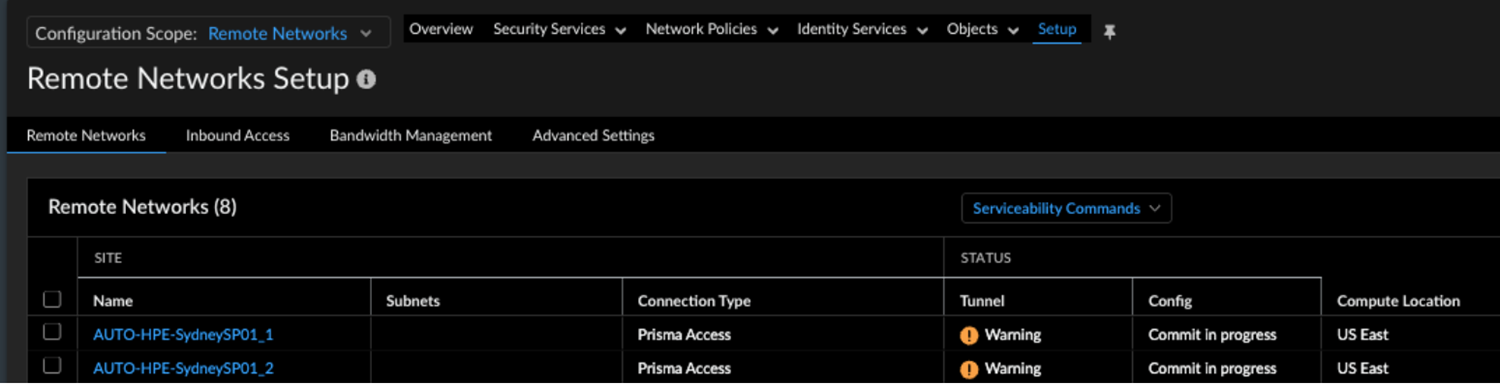
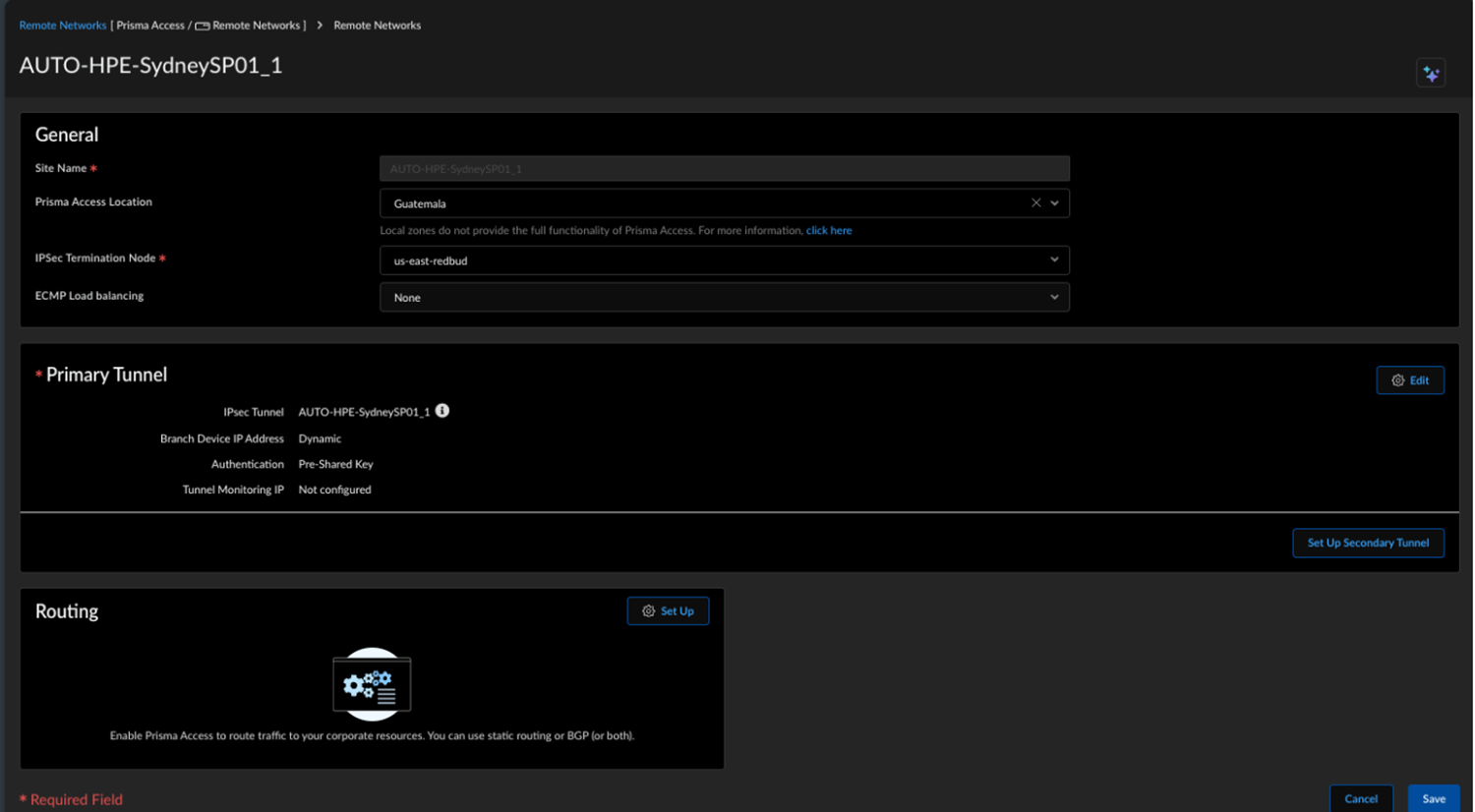
When you click a site count, the hyperlink opens a filtered list of sites based on that count.Verify the changes in Prisma Access.- In Strata Cloud Manager, go to . ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks.Alternatively, select Remote Networks - HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access on Integration Application tile.Verify the tunnel status. The integration creates remote networks automatically. Such remote networks have names with the prefix AUTO-HPE in the following syntax: AUTO-HPE-<Device_Name>.
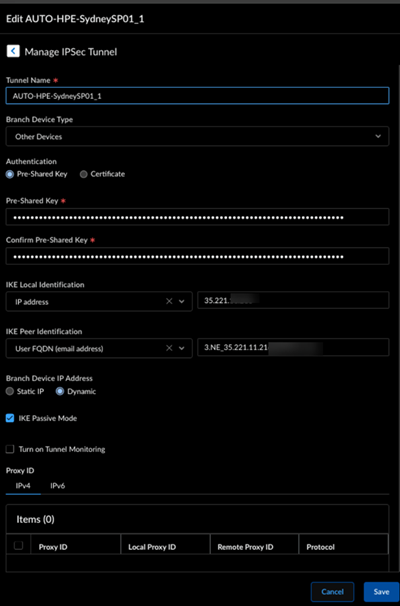
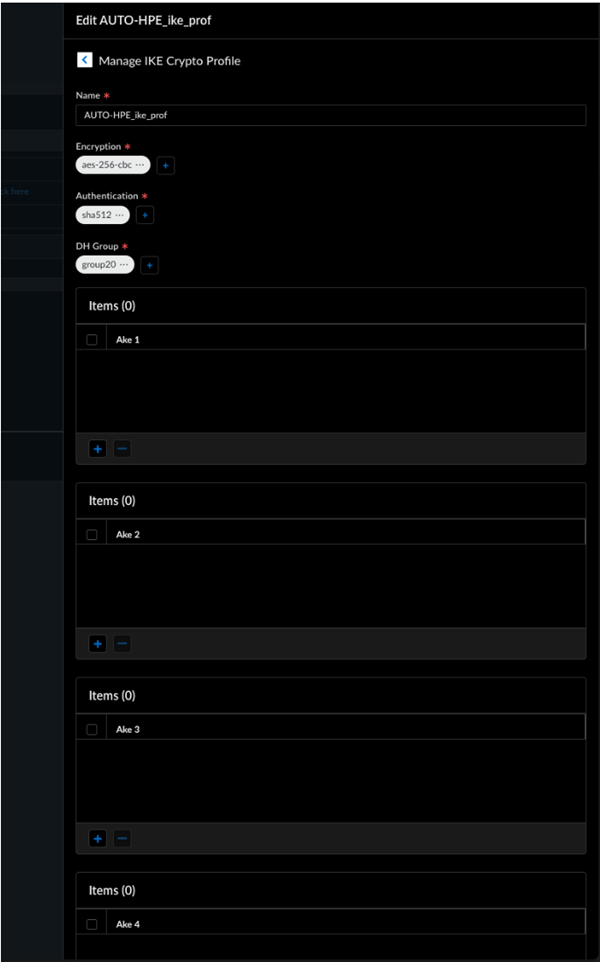
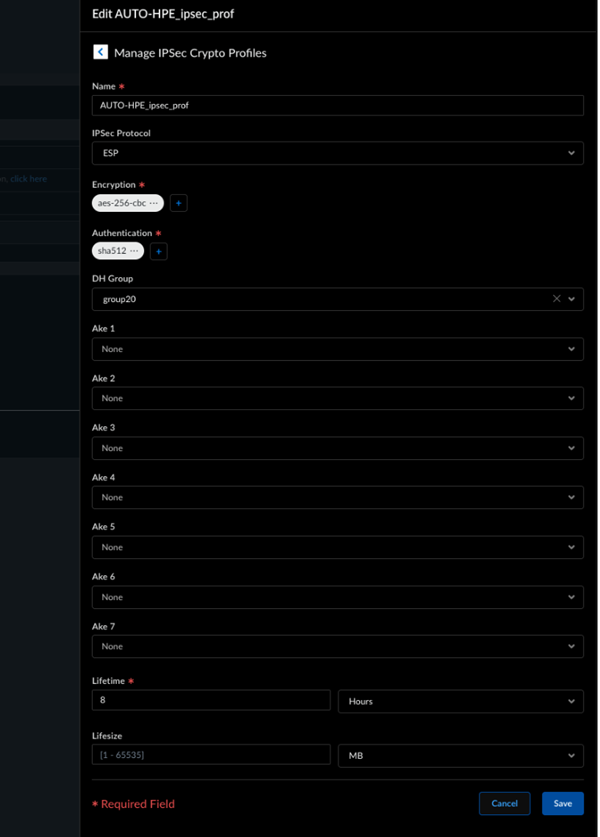
![]() The configuration status of HPE Aruba Networking EdgeConnect SD-WAN devices may take some time to show as In Sync.Select the remote network site to view the IPSec Tunnel, IKE gateway, IKE Crypto profile, and IPSec Crypto profile details.
The configuration status of HPE Aruba Networking EdgeConnect SD-WAN devices may take some time to show as In Sync.Select the remote network site to view the IPSec Tunnel, IKE gateway, IKE Crypto profile, and IPSec Crypto profile details.![]()
![]()
![]()
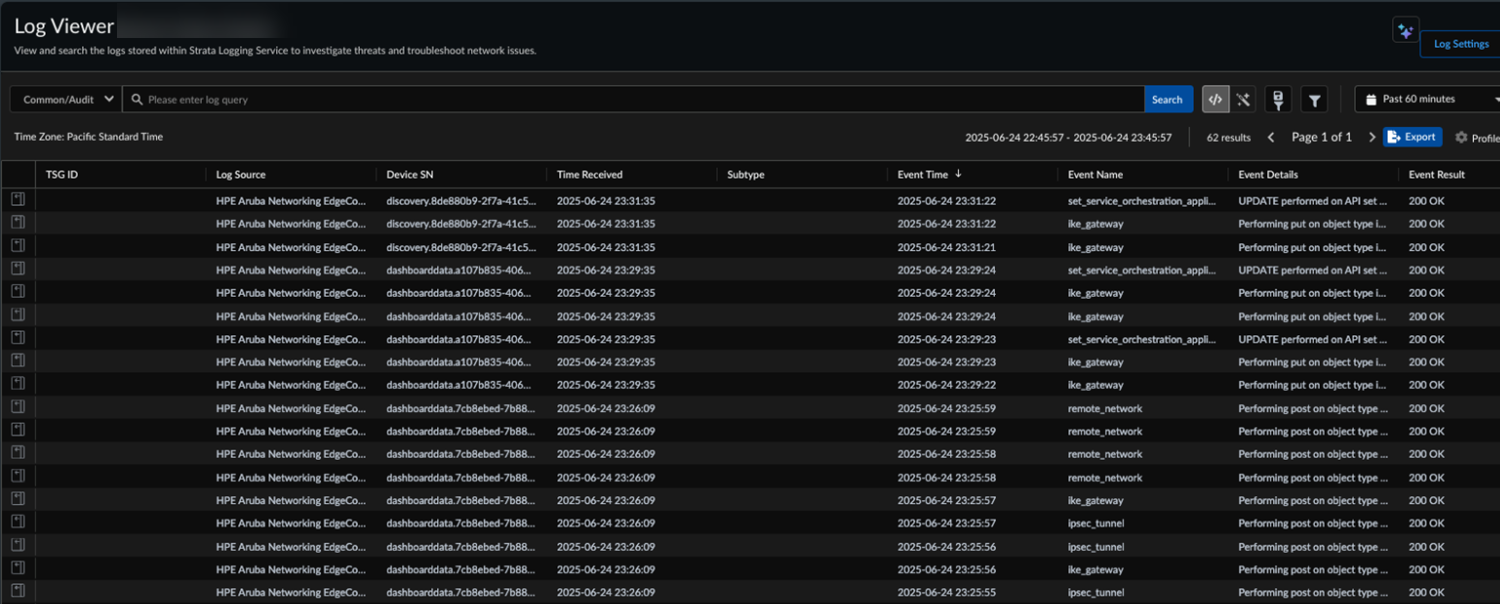
![]() Select Incidents and AlertsLog ViewerCommonAudit to view HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access integration logs.
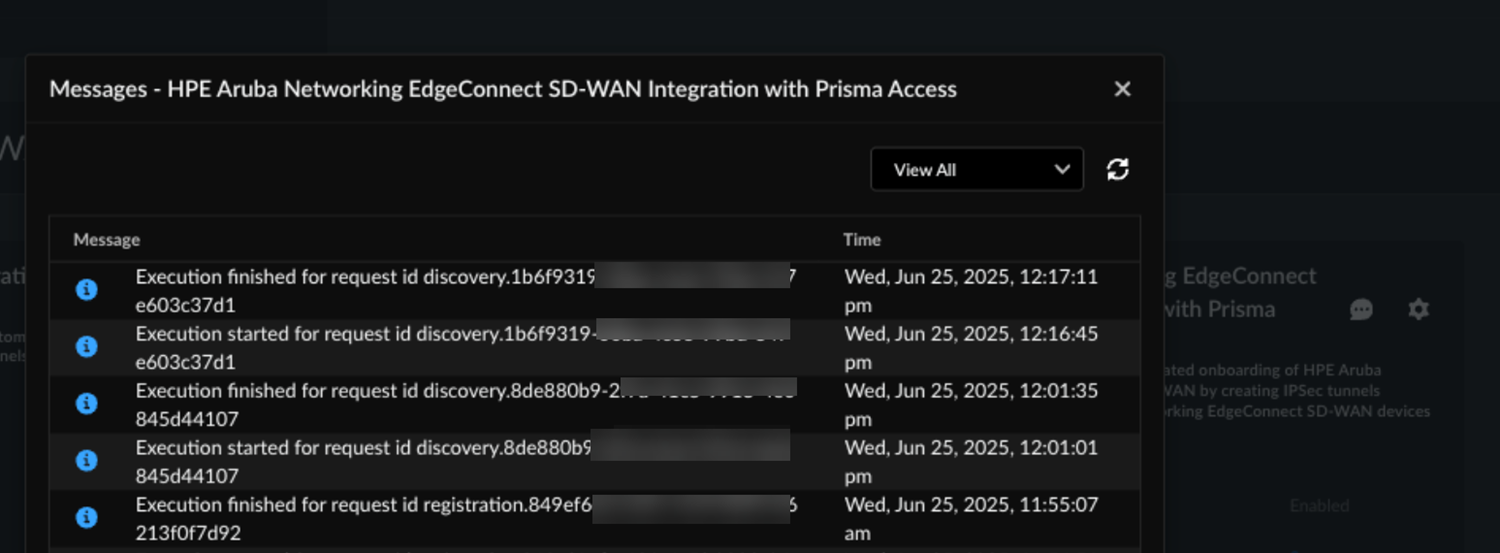
Select Incidents and AlertsLog ViewerCommonAudit to view HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access integration logs.![]() The logs specify if the changes were made in Prisma Access or in the HPE Aruba Networking Networking EdgeConnect SD-WAN.Go to the HPE Aruba Networking EdgeConnect SD-WAN integration app, to view information, errors, or warnings in the Messages section.
The logs specify if the changes were made in Prisma Access or in the HPE Aruba Networking Networking EdgeConnect SD-WAN.Go to the HPE Aruba Networking EdgeConnect SD-WAN integration app, to view information, errors, or warnings in the Messages section.![]() See Troubleshoot Integration Errors to see more error scenarios.Verify the HPE Aruba Networking Networking EdgeConnect SD-WAN configurations.
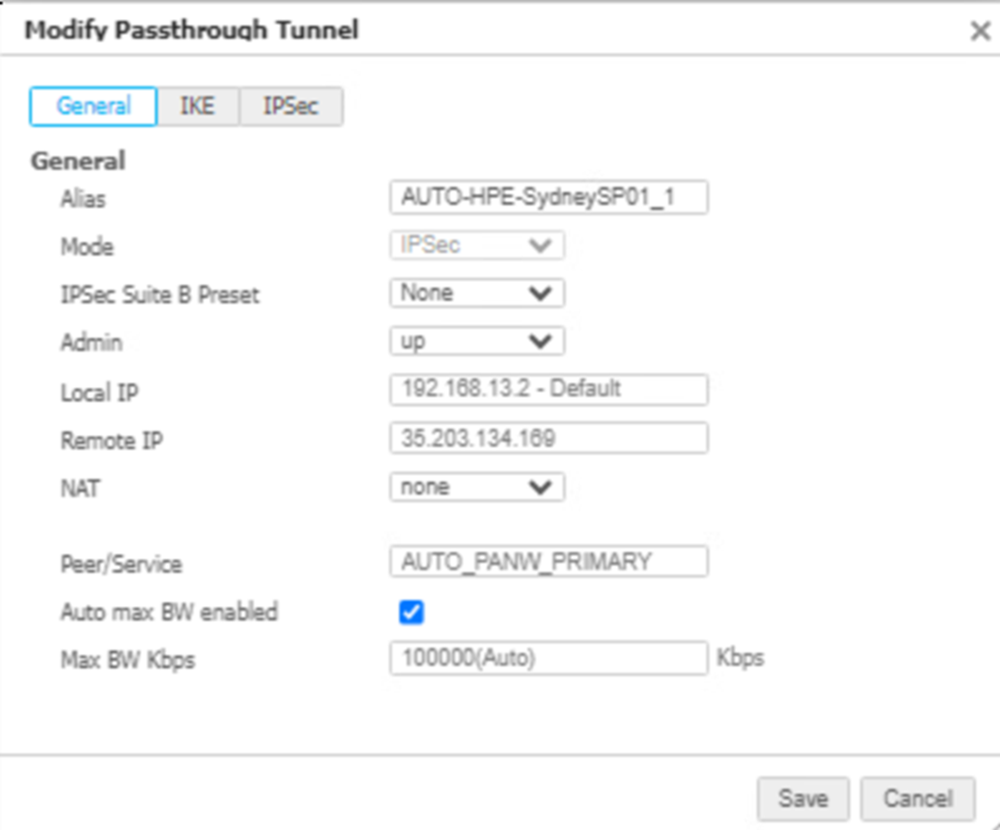
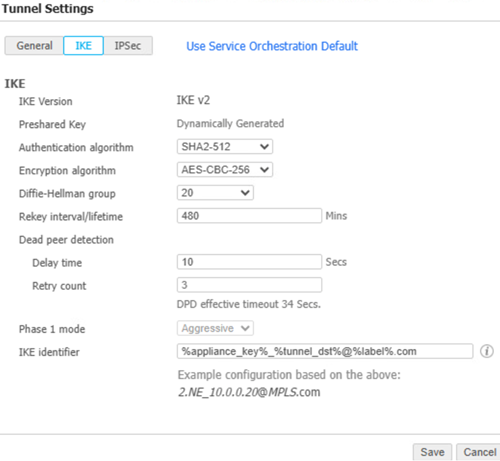
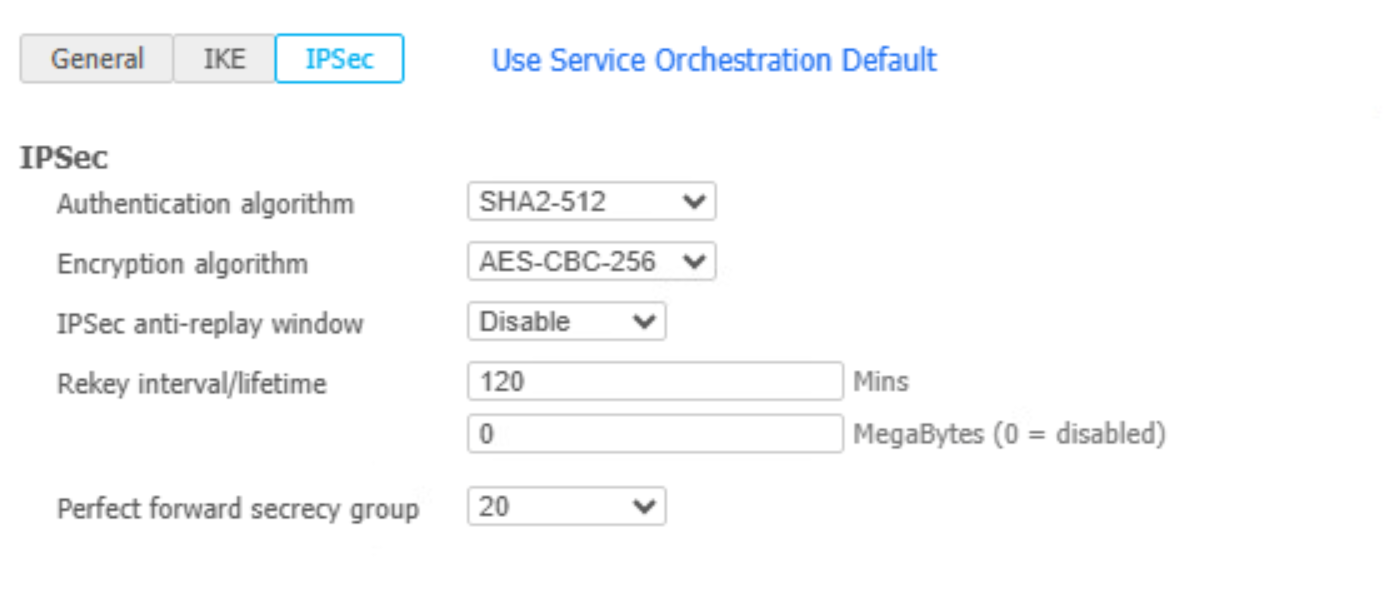
See Troubleshoot Integration Errors to see more error scenarios.Verify the HPE Aruba Networking Networking EdgeConnect SD-WAN configurations.- In EdgeConnect, go to ConfigurationNetworkingTunnelsTunnels and switch to the Passthrough tab.The integration creates Passthrough tunnels on HPE Aruba Networking EdgeConnect SD-WAN for every device that is enabled, with the following IKE AND IPSec configurations.
![]()
![]()
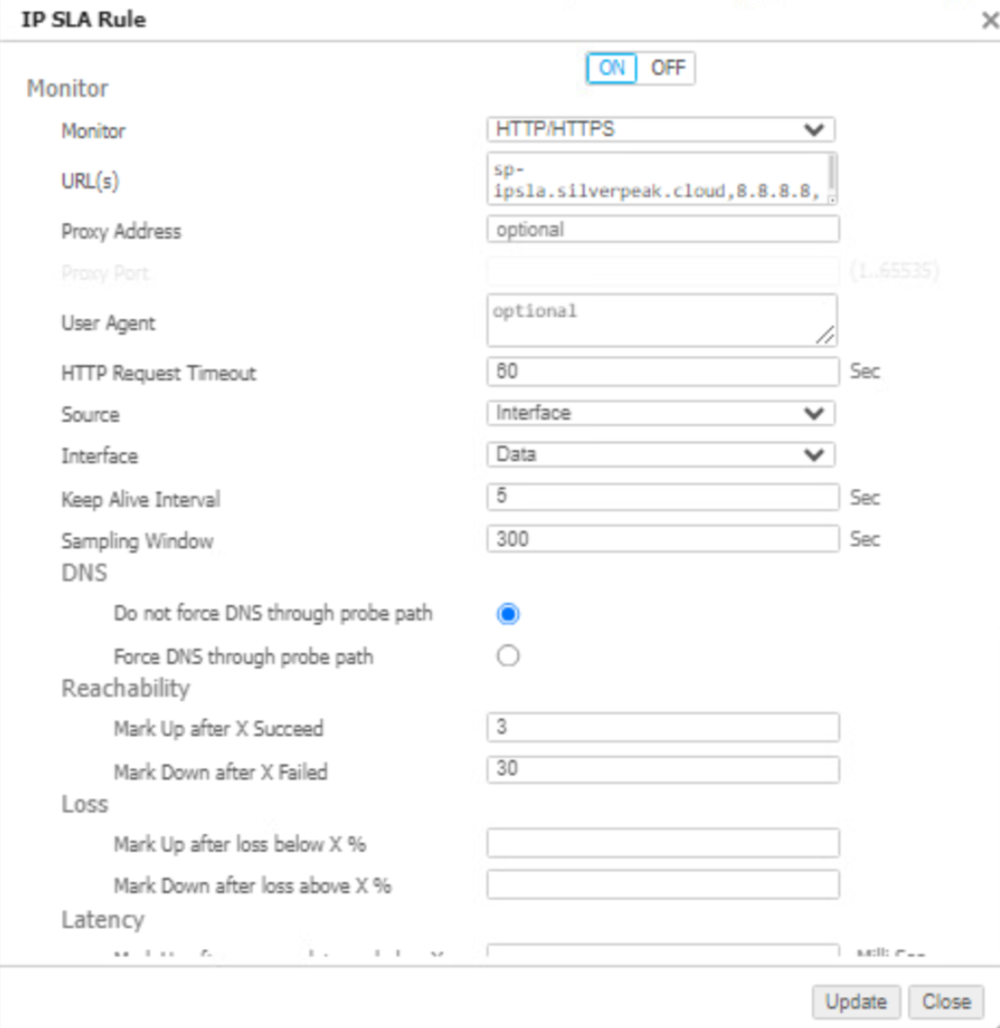
![]() Do not update the tunnel configurations manually, as the integration will overwrite any such modifications.In EdgeConnect, go to ConfigurationTemplates & PoliciesTCAsIPSLA. The integration creates IPSLA settings for each passthrough tunnel created by the Integration with the following configurations.
Do not update the tunnel configurations manually, as the integration will overwrite any such modifications.In EdgeConnect, go to ConfigurationTemplates & PoliciesTCAsIPSLA. The integration creates IPSLA settings for each passthrough tunnel created by the Integration with the following configurations.![]() Verify the tunnel status in HPE Aruba Networking Networking EdgeConnect SD-WAN.
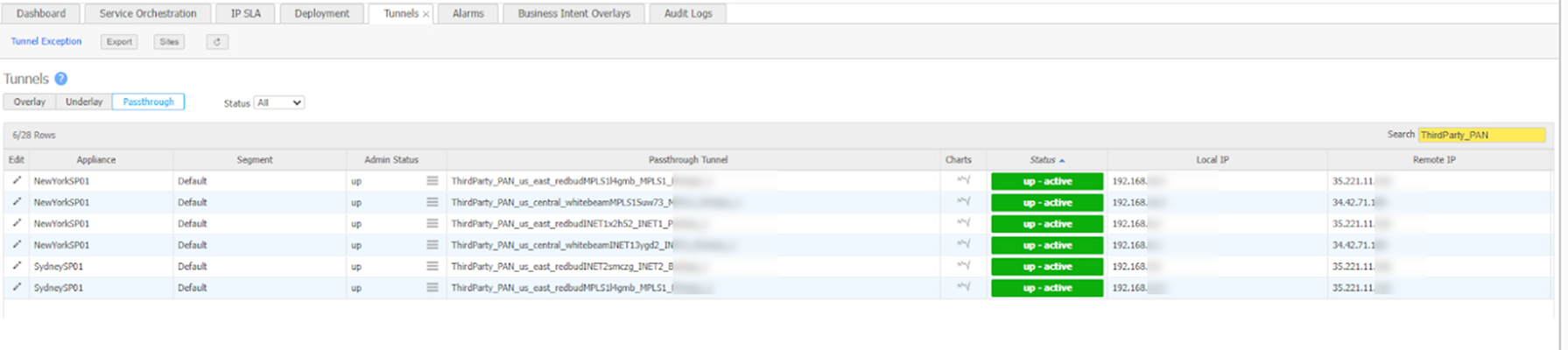
Verify the tunnel status in HPE Aruba Networking Networking EdgeConnect SD-WAN.- Log in to the HPE Aruba Networking EdgeConnect Orchestrator and navigate to ConfigurationNetworkingTunnelsTunnels and switch to the Passthrough tab (filter tunnels with AUTO-HPE-).Verify the status in the Status column of the passthrough tunnels tab.
![]()
On-Demand Site Discovery
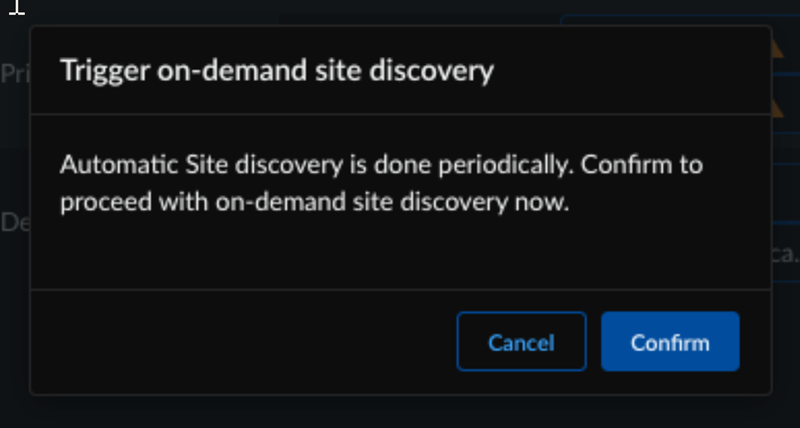
You can initiate network discovery at any time to view newly added devices in HPE Aruba or to resolve misconfigurations in integration-created objects. To start an on-demand network discovery, follow these steps: - In Strata Cloud Manager, locate HPE Aruba Networking EdgeConnect SD-WAN with Prisma Access.View the discovered HPE Aruba Networking EdgeConnect SD-WAN devices and their information by clicking the site count.Select Discover Sites to identify new eligible HPE Aruba Networking EdgeConnect SD-WAN devices when required.
![]() Review and Confirm the on-demand discovery pop-up.
Review and Confirm the on-demand discovery pop-up.![]()
Configure Routing in HPE Aruba EdgeConnect
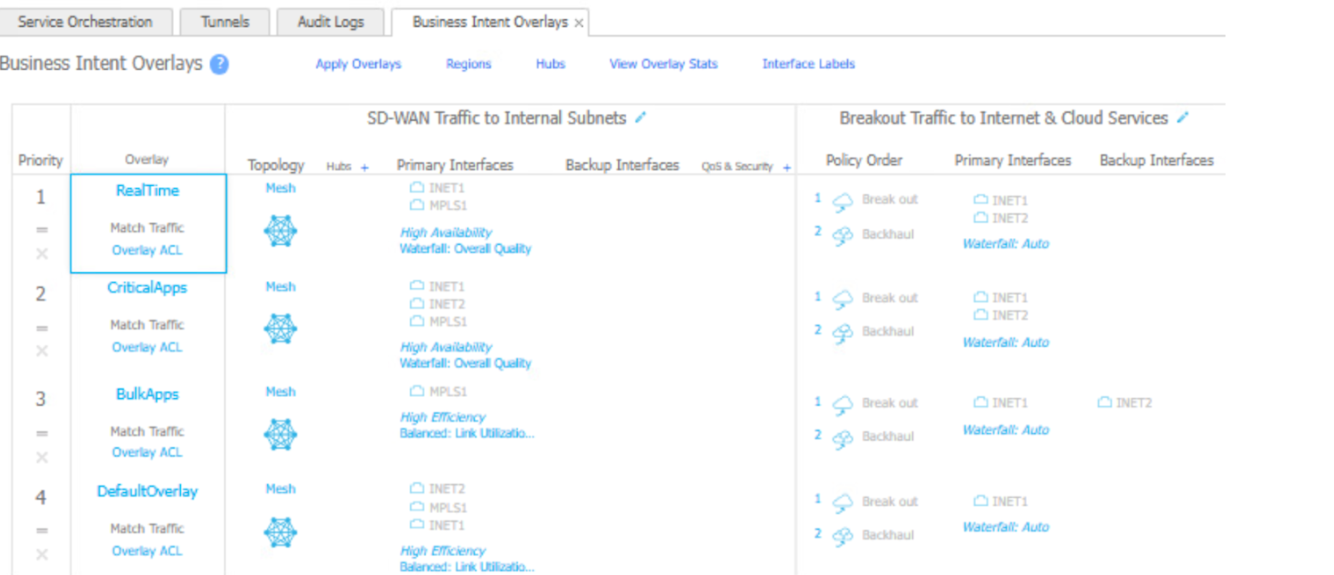
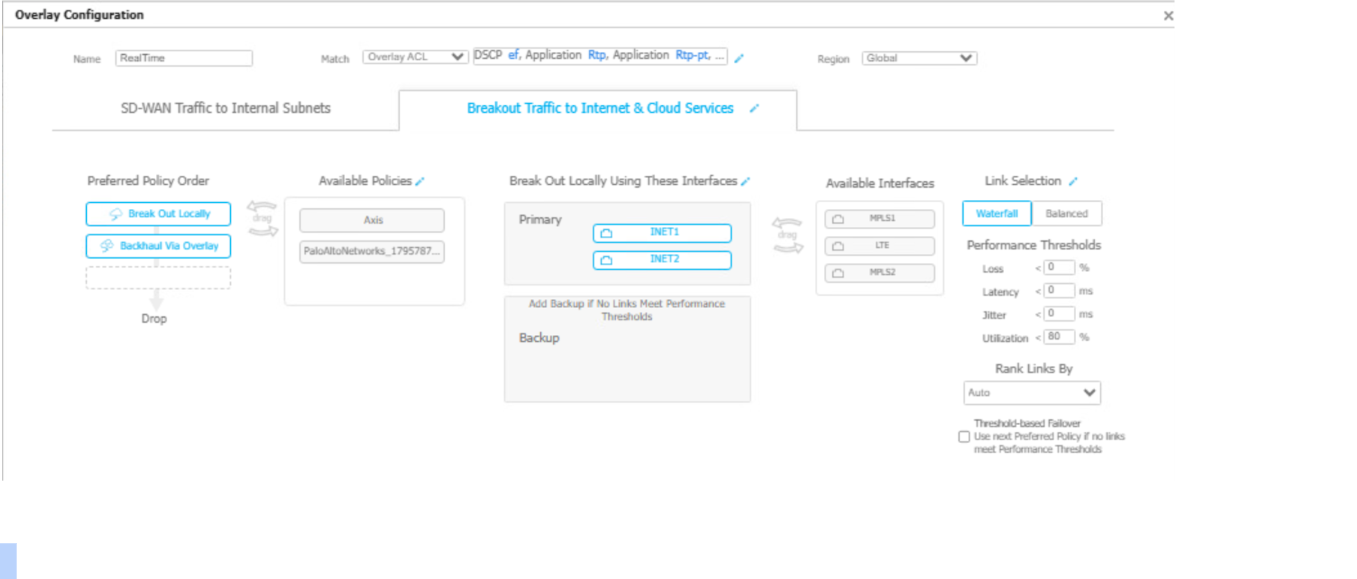
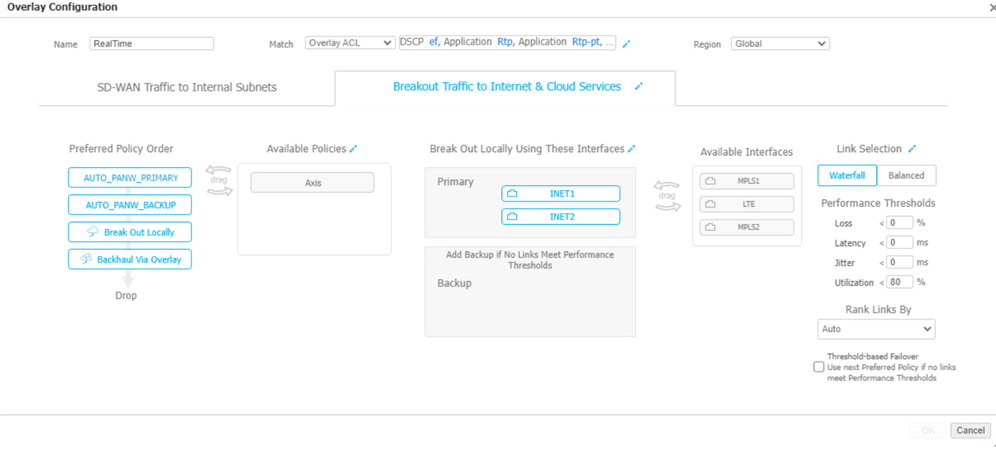
All routing configurations are managed by the HPE Aruba Networking EdgeConnect based on the policies defined in Business Intent Overlays. To ensure appliance traffic breaks out to the internet through passthrough tunnels instead of using local internet, follow the steps below: - Navigate to ConfigurationsOverlays & SecurityBusiness Intent Overlays.Select the required Overlay and browse to Breakout Traffic to Internet & Cloud Services tab, find the policies AUTO_PANW_PRIMARY and AUTO_PANW_BACKUP created by the integration under the Available Policies section.
![]() Drag and drop the Primary and Backup Policy into the Preferred Policy Order section to enable passthrough tunnel routing for appliance traffic.
Drag and drop the Primary and Backup Policy into the Preferred Policy Order section to enable passthrough tunnel routing for appliance traffic.![]()
![]() If policies are not moved to the Preferred Policy Order, traffic will default to local internet breakout instead of using passthrough tunnels.
If policies are not moved to the Preferred Policy Order, traffic will default to local internet breakout instead of using passthrough tunnels.Troubleshoot Integration Errors
Here are some common error scenarios you might encounter during the integration, along with their causes and solutions. Additionally, you can review messages in the integration settings for more information, errors, and warnings. - Scenario: No Devices Seen in Summary DashboardAfter verifying and saving the application configuration, it triggers a discovery operation, but no SD-WAN devices appear in the summary dashboard.The discovery process, which identifies devices eligible for tunnel formation with Prisma Access, is not yielding any results. This can be due to various underlying issues, often related to API communication or configuration errors.If no devices are seen in the summary dashboard, review the following:
- Navigate to the Messages tab within the Strata Cloud Manager and review for any errors or warnings related to SD-WAN APIs or configuration issues, which may provide specific details on why devices are not being discovered or displayed.
- Configuration on the Integration application settings could be incomplete: the initial discovery could not be completed due to missing or incorrect entries in the Primary and Backup Interface Label fields.
- The device is not eligible for any of the eight topologies, possibly
due to:
- Device may not have any interface labels added in the deployment page.
- Device may not have any primary interface labels.
- Discovery is not complete yet.
- Scenario: Specific Device Not Appearing on Discovery ScreenNot all devices on the HPE Aruba Service Orchestrator are eligible for tunnel formation with Prisma Access. If a particular device 'x' does not show up on the discovery screen, even though other devices are visible, it could be the device does not meet the necessary criteria.If device 'x' is not seen in the summary dashboard, review the following:
- Verify the eligibility criteria by ensuring the device is configured with an eligible WAN interface and that its configuration aligns with one of the supported topologies for tunnel formation with Prisma Access.
- Contact the Palo Alto support team in case the issue persists.
- Scenario: Configurations not Visible on HPE Aruba
OrchestratorAfter a discovery run and an Enable device operation, expected resources (Device Passthrough tunnels, IP SLA configurations, and Policies) are not visible on the SD-WAN side.If these resources are not created or visible, it indicates a problem with the integration's ability to provision configurations on the SD-WAN.
- Look into the Messages tab in Strata Cloud Manager or to check the logs further, contact the Palo Alto support team.
- Scenario: Tunnel Configuration not Visible in Strata Cloud
ManagerAfter enabling a device for tunnel formation, expected tunnel-related objects (Remote Networks, IPSec Tunnels, IKE Gateways, IKE Crypto Profile, IPsec Crypto Profile) are not visible in Strata Cloud Manager. The integration solution is responsible for creating these specific resources in Strata Cloud Manager. Their absence indicates a failure in the provisioning process on the Prisma Access side.As a general troubleshooting step for all issues, review the Status tab in the configuration tile within Strata Cloud Manager or contact the Palo Alto support team.Review to ensure the naming conventions for Strata Cloud Manager objects follow the below format:
- Objects related to the network (Remote Networks, IPsec Tunnels, IKE Gateways): AUTO-HPE-<device_name>.
- IKE Crypto Profile and IPsec Crypto Profile: AUTO-HPE-<PROF_NAME>.
- Scenario: Commit Failure in Strata Cloud ManagerStrata Cloud Manager commit failures can stem from various issues, some of which may be unrelated to this integration. However, if AUTO-HPE- objects are involved, the failure could be due to manual tampering or deletion of these objects.If you see a commit failure in Strata Cloud Manager, review the following:
- For errors not involving AUTO-HPE- objects, address them based on the validation error message. For AUTO-HPE- objects, check if they were manually modified or deleted.
- Ensure there was no attempt to manually correct configurations managed by the integration solution.
- The Discovery stage of the integration automatically re-mediates most misconfigurations during its regular scanning intervals. To expedite this process, navigate to the Discovery Summary page and trigger an on-demand discovery to verify that the integration resolves the issues.
- Scenario: Configurations are Correct; No Tunnel EstablishedThe issue where the tunnel does not establish, even though configurations on both the HPE Aruba SD-WAN and Prisma Access appear to be correct, can arise from various discrepancies or failures in the underlying infrastructure or configuration synchronization, even if the visible settings seem accurate.If you see no tunnel established, review the following:
- Confirm that the Prisma Access config push job, responsible for spinning up the Prisma Access SPNs was successful. A failure here would prevent the tunnel from forming.
- Ensure that the Service IP from Prisma Access was successfully attached to the devices on the SD-WAN side.
- Verify that the remote and local identifiers configured on the SD-WAN device precisely match the local and remote identifiers on the corresponding Prisma Access Remote Networks. Any mismatch in these identifiers will prevent tunnel establishment.
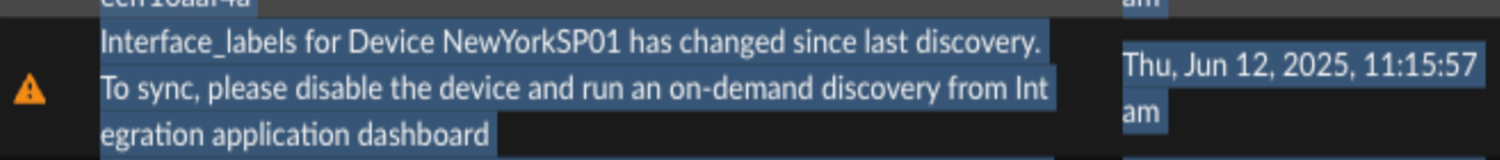
The integration solution is responsible for configuration management only. Troubleshooting connectivity issues beyond configuration alignment may require deeper network diagnostics. - Scenario: Enabled Device Manually Tampered, and Topology ChangedA previously discovered and enabled device has been manually tampered with, resulting in a change to its topology.Once a device is discovered and enabled from Strata Cloud Manager, the integration creates corresponding objects on both the Prisma Access and SD-WAN sides. This error occurs when the interface labels are modified either in the device deployment within the HPE Aruba Networking EdgeConnect or in the application settings (Primary/Backup) resulting in a change of the expected topology.
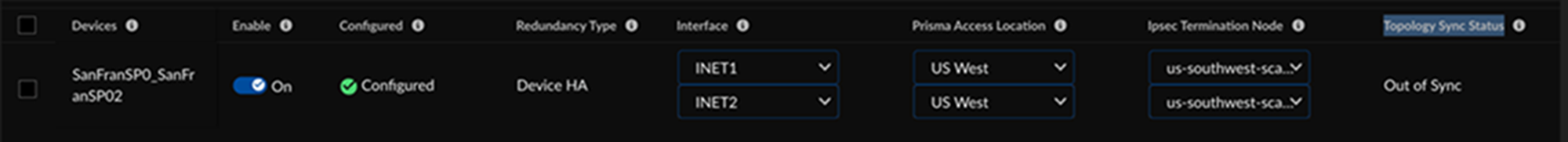
![]() A warning appears in the status box for the affected device (as shown above), and the Topology Sync Status of the affected device shows Out of Sync, however no existing configurations are deleted. If the device was not enabled for the tunnel formation, its entry in Strata Cloud Manager is automatically updated with the correct topology type (based on the modified labels) after a successful discovery run.
A warning appears in the status box for the affected device (as shown above), and the Topology Sync Status of the affected device shows Out of Sync, however no existing configurations are deleted. If the device was not enabled for the tunnel formation, its entry in Strata Cloud Manager is automatically updated with the correct topology type (based on the modified labels) after a successful discovery run.![]() If the device was enabled, review the label changes. If they are valid, you must disable the device and run an on-demand discovery from the Integration Application dashboard to sync the updated labels.
If the device was enabled, review the label changes. If they are valid, you must disable the device and run an on-demand discovery from the Integration Application dashboard to sync the updated labels.