Prisma SD-WAN
Configure Secure SD-WAN Fabric Tunnels between Data Centers
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
- Prisma SD-WAN Controller
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 6.5
- 6.4
- 6.3
- 6.1
- 5.6
- Prisma SD-WAN Controller
- Prisma SD-WAN On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Configure Secure SD-WAN Fabric Tunnels between Data Centers
Learn how to configure secure SD-WAN Fabric tunnels between data centers in Prisma SD-WAN.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma SD-WAN supports secure SD-WAN fabric tunnels between
data center sites, eliminating the need for third-party solutions or complex MPLS
configurations. With this feature, you can efficiently connect multiple data centers
across different cloud providers such as AWS, Azure, Equinix, and GCP, as well as
physical locations. You can easily provision and manage these inter-DC connections
through the Prisma SD-WAN controller web interface or via APIs,
similar to how you set up branch-to-branch tunnels.

Both the source and destination DC ION devices should have software version
6.5.1 or later to configure such tunnels.
You can configure the secure SD-WAN fabric tunnels by choosing the source
and optional destination clusters between the DC sites for creating VPNs. The secure
fabric tunnels are created by default between all the devices in a DC cluster.
All the secure fabric tunnels will be active by default based on the core
peering status. If the core peer is down, the controller marks the VPN as inactive.
We recommend that you configure either Standard VPN tunnels or secure fabric tunnels
between two data center sites and not both at the same time.
In case you have a hybrid topology, where you have both native and standard
VPNs, configure a prefix list for the first data center, which explicitly denies the
prefixes coming from the second data center on the Standard VPN path. Otherwise, the
traffic loops back to the first DC device.

After setting up secure fabric tunnels, you should refrain from distributing
Inter-DC-BGP learned prefixes over Inter-DC tunnels. Hence, after upgrading your
device to software version 6.5.1, Prisma SD-WAN sets all the existing
BGP peers to Local. This is to have better control over the
learned prefixes. If you want to distribute the learned prefixes, you will need to
change the setting to
Global.
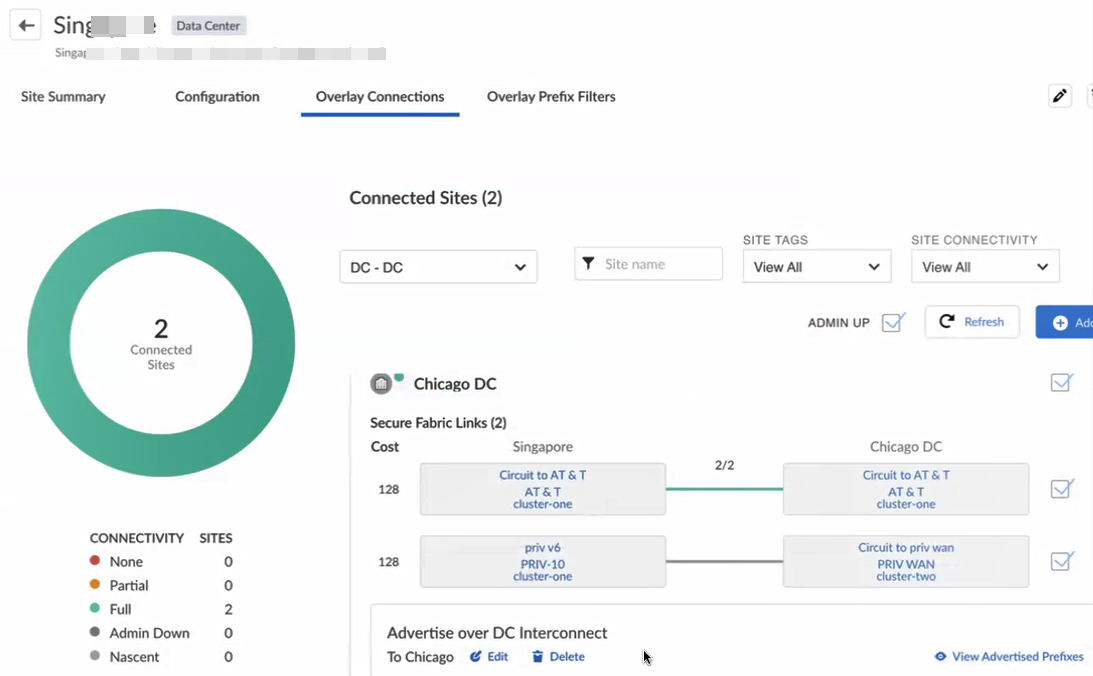
To create Secure Fabric tunnels:
- Select ConfigurationPrisma SD-WANData CentersOverlay Connections.Click Add Secure Fabric Link.
- (Optional) Enter a Name, Description, and Tags for the secure fabric tunnel.Select a Cluster and a Circuit from the source data center site.Ensure that you select Admin Up.For Destination, select a Data Center site, Hub Cluster, and Hub Circuit.You can select multiple destinations; Prisma SD-WANcreates the secure fabric tunnels between the Source Cluster and Circuit to all the selected destinations.Click Save.You can view the created Secure Fabric Links on the Overlay Connections tab.
![]() (Optional) Click View advertised prefixes to see the advertised prefixes. Click Edit to update the overlay prefix filter.You can view the metrics along with circuit health on the Site Summary page.
(Optional) Click View advertised prefixes to see the advertised prefixes. Click Edit to update the overlay prefix filter.You can view the metrics along with circuit health on the Site Summary page.Create Overlay Prefix Filters
Prisma SD-WAN distributes global prefixes from the source data center ION device to the other data center sites. To control the distribution, you can configure a filter using a prefix list. Set up this filter on the source data center ION device for which you need secure fabric tunnel connectivity.Prefixes eligible for fabric distribution:- Global static routes
- WAN path prefixes from the branch or branch gateway sites (Hop count = 1 are eligible for further distribution.)
- Site prefixes
- BGP/OSPF Global learned prefixes
Prisma SD-WAN does not distribute prefixes learned on Inter-DC VPNs further to other data centers. This prevents routing loops. Also, Prisma SD-WANdoes not distribute the Inter-DC learned prefixes to branch or branch gateway sites.The following example topology illustrates the prefix distribution in Prisma SD-WAN.![]() Note the following points with reference to prefix distribution:
Note the following points with reference to prefix distribution:- If you don't want to advertise prefixes to a BGP peer, toggle Scope to Local when configuring the BGP peer.
- If you have existing standard VPN tunnels between the data center ION
devices, note:
- Prisma SD-WAN sets the Scope to Local by default after you upgrade your device to software version 6.5.1. You will need to toggle the Scope to Global, if you want to make these prefixes eligible for distribution.
- Configure prefix lists in such a way that prefixes distributed on one path are denied on the other path, in case both Fabric tunnels and Standard VPN tunnels are active.
- If two data center ION devices are connected to a common core peer, ensure that the configuration does not distribute the prefixes over the fabric but through the common core.
To create overlay prefix filters:- Select ConfigurationPrisma SD-WANData CentersOverlay Prefix Filters.Select Add New Profile.Enter a Name for the profile and optionally enter a Description and Tags.Enter an Order, IP Prefix and select Permit or Deny.Click Submit.