Configure More than Two Service Connections to a Headquarters or Data Center Location
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
-
- Prisma Access China
- 4.0 & Later
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
-
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
Configure More than Two Service Connections to a Headquarters or Data Center Location
How to configure more than two service connections to
an HQ or data center location.
When you use two tunnels for a high-bandwidth
service connection, there is only one traffic path left available
in case of a tunnel failure, which simplifies the configuration
of a failover path. If you use more than two connections for a high-bandwidth
connection, you need to perform additional configuration to ensure
a consistent behavior for tunnel failovers.
Because you use
a summarized subnet for tunnel failover, you need to explicitly
state the service connection tunnel to use if a failover occurs.
Since BGP routing chooses the shortest number of AS-PATHs for a
route, you can prepend AS-PATHs to routes to have BGP prefer a tunnel
in the case of a failover.
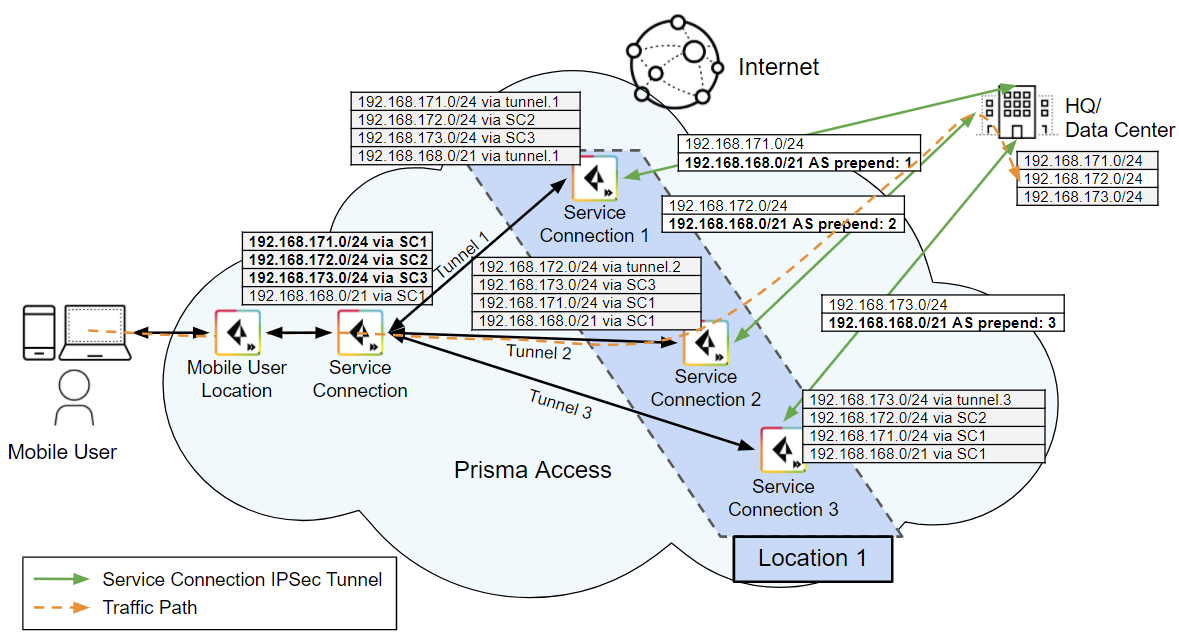
The following example shows routing
tables for a high-bandwidth service connection using three service
connections. If all three tunnels are up, Prisma Access uses the
more specific routes to reach the subnets in the headquarters or
data center location. Since the user is accessing a resource in
the 192.168.172.0/24 subnet, the service connection closest to the
mobile user checks its routing table and selects Tunnel 2 as the
path to the data center resource.
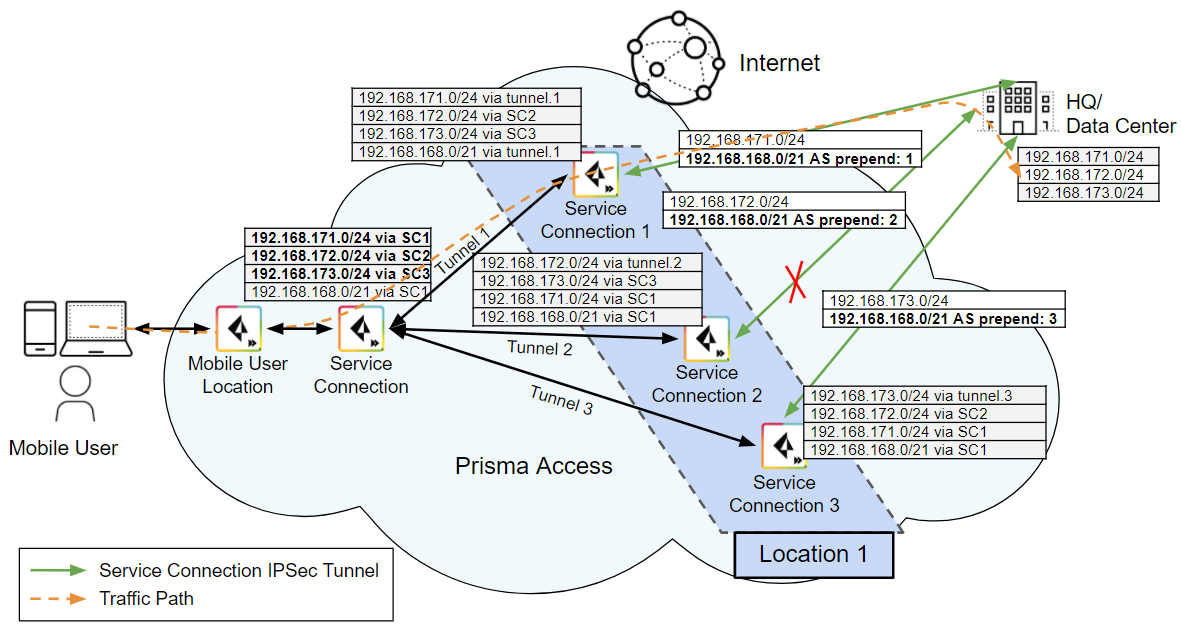
If
Tunnel 2 goes down, the more specific route to the resource in the
192.168.172.0/24 subnet is not available, so the service connection
closest to the user uses the summarized 192.168.168.0/21 subnet.
You have configured only one AS-PATH prepend for Service Connection
1; therefore, Prisma Access chooses Tunnel 1 as the failover path
because it has fewer AS-PATH prepends.
To
add prepends to routes if you are using a next-generation firewall
as the CPE, complete the following task.
- Select the virtual router BGP export profiles (NetworkVirtual RoutersBGPExport).Modify the export rule you created when you configured the service connections that has an Action of Allow.
![]() In the AS Path area, add a Prepend, then enter the number of AS-PATH prepends to add (2 in this example).
In the AS Path area, add a Prepend, then enter the number of AS-PATH prepends to add (2 in this example).![]() Repeat Steps 2 and 3 for each export rule that has an Action of Allow, adding AS-PATH prepends to match the failover scenarios you have planned for your deployment.In the examples used in this section, you add an AS-PATH prepend of 1 for the tunnel to the data center location for Service Connection 1 (tunnel.1), an AS-PATH prepend of 2 for the tunnel used for Service Connection 2 (tunnel.2), and an AS-PATH prepend of 3 for the tunnel used for Service Connection 3 (tunnel.3).When complete, this example uses the following tunnels in the even of a failover:
Repeat Steps 2 and 3 for each export rule that has an Action of Allow, adding AS-PATH prepends to match the failover scenarios you have planned for your deployment.In the examples used in this section, you add an AS-PATH prepend of 1 for the tunnel to the data center location for Service Connection 1 (tunnel.1), an AS-PATH prepend of 2 for the tunnel used for Service Connection 2 (tunnel.2), and an AS-PATH prepend of 3 for the tunnel used for Service Connection 3 (tunnel.3).When complete, this example uses the following tunnels in the even of a failover:- If tunnel.2 or tunnel.3 goes down, the traffic for the corresponding subnet fails over to tunnel.1, which has the shortest advertised AS-PATH.
- If tunnel.1 goes down, the traffic for its subnet (192.168.171.0/24) fails over to tunnel.2, which has the shortest advertised AS-PATH.
Add backup PBF or policy-based routing policies to ensure symmetric return traffic in the event of a tunnel failure.While the AS-PATH prepends ensure that the traffic from Prisma Access to the data center uses a specific tunnel in the event of a failover, you must also ensure a symmetric return path for the traffic from the data center to Prisma Access. To ensure symmetric return, use PBF or policy-based routing policies that mirror the failover scenarios you created for traffic from Prisma Access to the data center.In this example, for tunnel.1 traffic that has a source IP of 192.168.171.0/24, you create a backup PBF Policy that forces return traffic to use tunnel.2 in the event of a failover. The first PBF rule becomes disabled if the tunnel monitor IP address is not reachable; when this failover occurs, the CPE (a next-generation firewall in this example) evaluates the next rule in the list.![]() You then add more PBF rules to match the failover scenarios you created for traffic from Prisma Access to the data center.
You then add more PBF rules to match the failover scenarios you created for traffic from Prisma Access to the data center.![]()




