Prisma Access
Riverbed SteelConnect SD-WAN Solution Guide
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Riverbed SteelConnect SD-WAN Solution Guide
Use the Riverbed SteelConnect SD-WAN Solution Guide.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To use this Solution Guide, you need a knowledge of the following software and hardware
concepts:
- SD-WAN routing principles
- SteelConnect Manager (SCM)
- SteelConnect appliances (in particular, SteelConnect gateways)
- Panorama appliance configuration tasks
- Prisma Access configuration tasks
Supported IKE and IPSec Cryptographic Profiles
Prisma Access supports standard IPSec tunnels from third-party SD-WAN edge devices
using IKE and IPSec Crypto profiles.
The following table documents the IKE/IPSec crypto settings that are supported with
Prisma Access and SteelConnect SD-WAN.
A check mark indicates that the profile or architecture type is supported; a dash (—)
indicates that it's not supported. Default and Recommended settings are noted in the
table.
| Crypto Profiles | Prisma Access | SteelConnect SD-WAN | |
|---|---|---|---|
| Tunnel Type | IPSec Tunnel |

|

|
| GRE Tunnel | — | — | |
| Routing | Static Routes |

|

|
| Dynamic Routing (BGP) |

|

| |
| Dynamic Routing (OSPF) | — |

| |
| IKE Versions | IKE v1 |

|

|
| IKE v2 |

|

| |
| IPSec Phase 1 DH-Group | Group 1 |

|

|
| Group 2 | 
|

| |
| Group 5 |

|

| |
| Group 14 |

|

| |
| Group 19 |

| — | |
| Group 20 | 
| — | |
| IPSec Phase 1 Auth If you use
IKEv2 with certificate-based authentication, only SHA1 is
supported in IKE crypto profiles (Phase 1). | MD5 |

|

|
| SHA1 | 
|

| |
| SHA256 |

|

| |
| SHA384 |

|

| |
| SHA512 | 
|

| |
| IPSec Phase 1 Encryption | DES |

| — |
| 3DES | 
|

| |
| AES-128-CBC | 
| 
| |
| AES-192-CBC |

|

| |
| AES-256-CBC | 
|

| |
| IPSec Phase 1 Key Lifetime Default | 
| 
| |
| IPSec Phase 1 Peer Authentication | Pre-Shared Key |

|

|
| Certificate |

|

| |
| IKE Peer Identification | FQDN |

|

|
| IP Address |

|

| |
| User FQDN |

| — | |
| IKE Peer | As Static Peer |

|

|
| As Dynamic Peer |

|

| |
| Options | NAT Traversal |

|

|
| Passive Mode |

| — | |
| Ability to Negotiate Tunnel | Per Subnet Pair |

|

|
| Per Pair of Hosts |

|

| |
| Per Gateway Pair |

| — | |
| IPSec Phase 2 DH-Group | Group 1 |

|

|
| Group 2 | 
| 
| |
| Group 5 |

|

| |
| Group 14 |

|

| |
| Group 19 |

| — | |
| Group 20 | 
| — | |
| No PFS |

| — | |
| IPSec Phase 2 Auth | MD5 |

|

|
| SHA1 | 
|

| |
| SHA256 |

|

| |
| SHA384 |

|

| |
| SHA512 | 
| 
| |
| None |

| — | |
| IPSec Phase 2 Encryption | DES |

| — |
| 3DES | 
|

| |
| AES-128-CBC | 
|

| |
| AES-192-CBC |

|

| |
| AES-256-CBC |

| 
| |
| AES-128-CCM |

| — | |
| AES-128-GCM |

| — | |
| AES-256-GCM | 
|

| |
| NULL |

|

| |
| IPSec Protocol | ESP |

|

|
| AH |

| — | |
| IPSec Phase 2 Key Lifetime Default | 
| 
| |
| Tunnel Monitoring Fallback | Dead Peer Detection (DPD) |

| — |
| ICMP | — | — | |
| Bidirectional Forwarding Detection (BFD) | — | — | |
| SD-WAN Architecture Type | With Regional Hub/Gateway/Data Center | NA |

|
| No Regional Hub/Gateway/Data Center | NA |

| |
SD-WAN Deployment Architectures Supported by Riverbed
Riverbed supports the following deployment architectures for use with Prisma Access.
A dash (—) indicates that the deployment isn't supported.
| Use Case | Architecture | Supported? |
|---|---|---|
| Securing traffic from each branch site with 1 WAN
link (Type 1) Use an IPSec tunnel from each branch to Prisma
Access. Use a Riverbed SD-WAN appliance device at the
branch. |

| Yes |
| Securing branch and HQ sites with active/backup SD-WAN connections |
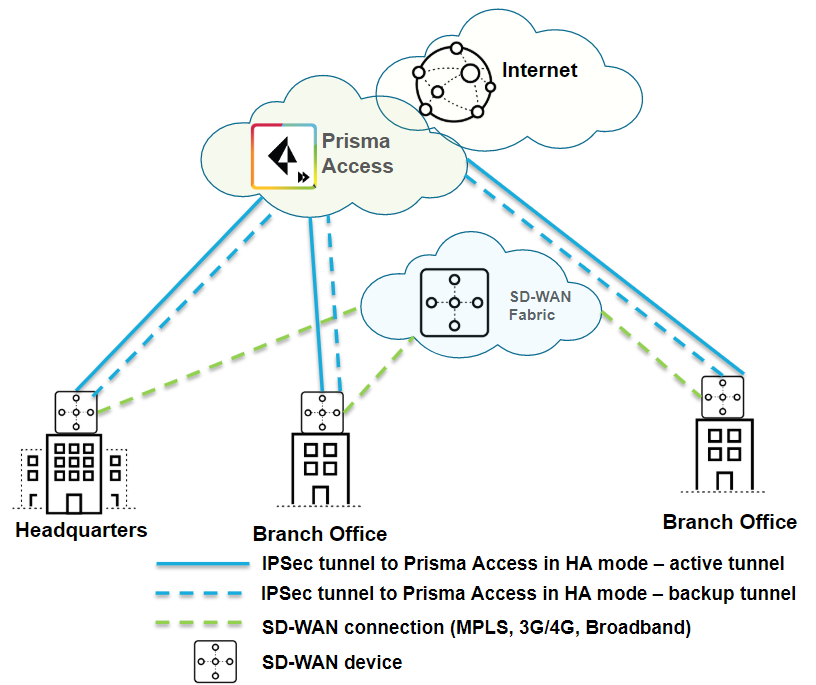
| No |
| Securing branch and HQ sites with active/active SD-WAN connections |
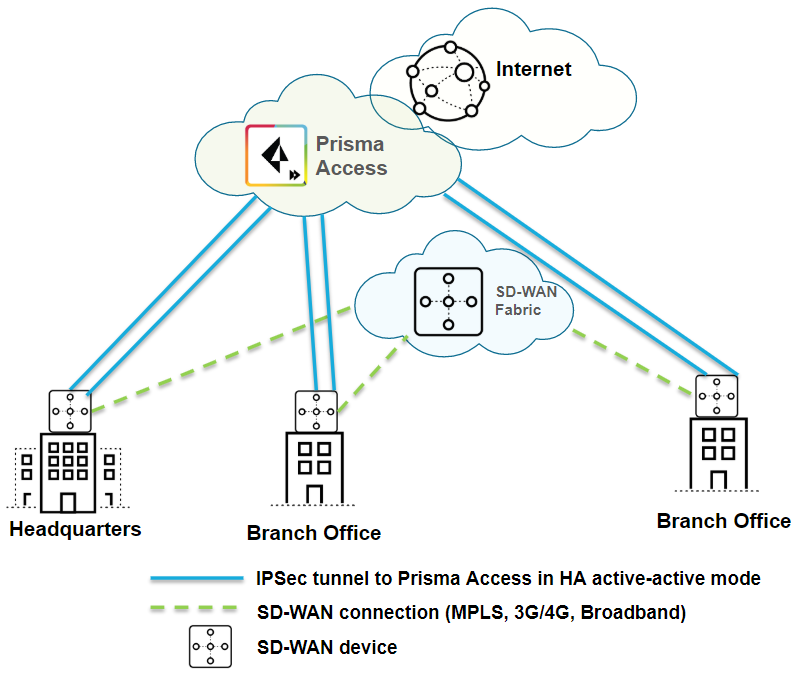
| No |
| Securing branch and HQ sites with SD-WAN edge devices in HA mode |
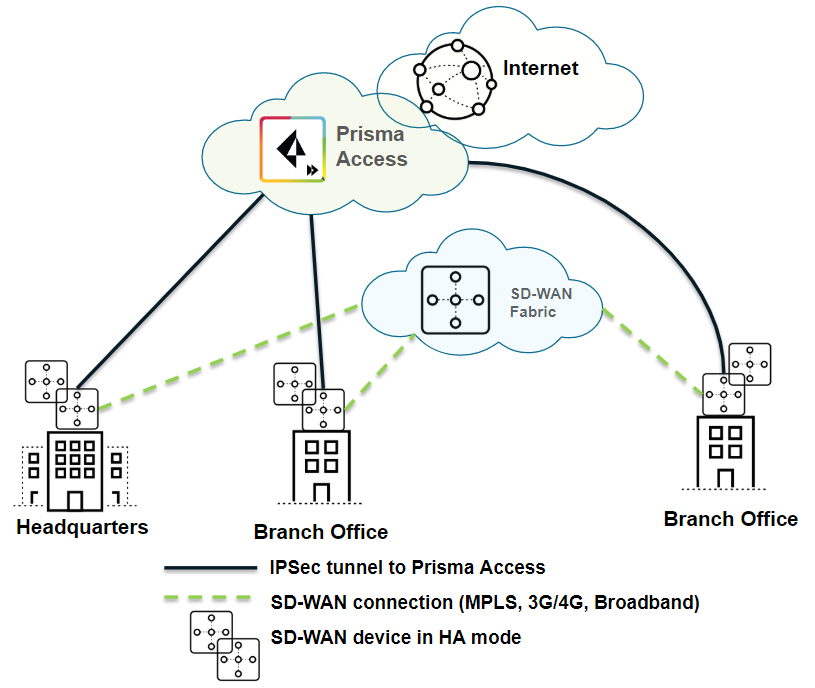
| Yes |
| Securing SD-WAN deployments with Regional Hub/POP architecture (Type 2) |
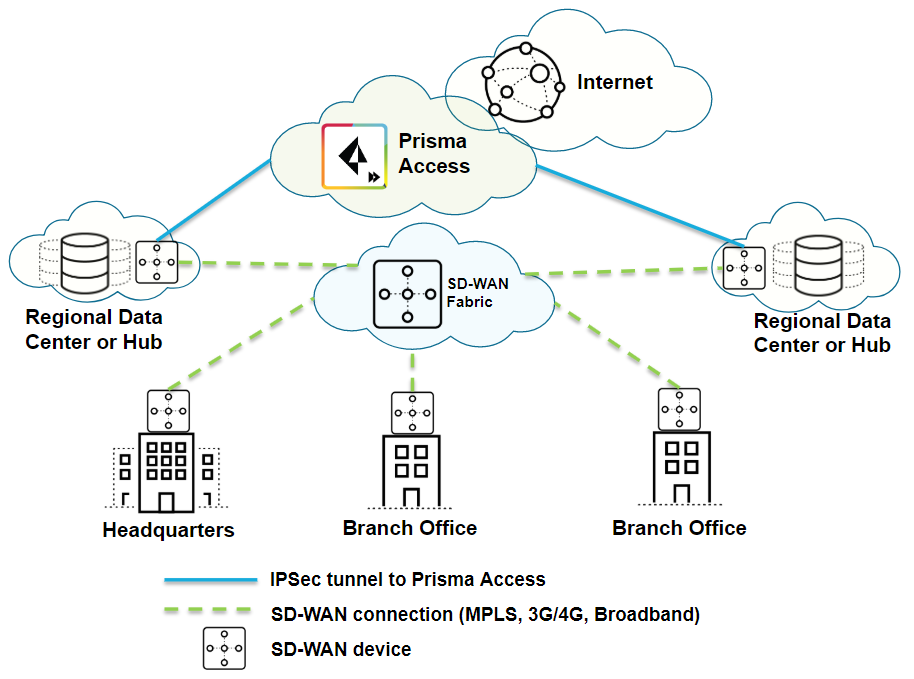
| Yes |
