Prisma SD-WAN
Configure Custom Liveliness Probe
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
-
-
- AWS Transit Gateway
- Azure vWAN
- Azure vWAN with vION
- ChatBot for MS Teams
- ChatBot for Slack
- CloudBlades Integration with Prisma Access
- GCP NCC
- Service Now
- Zoom QSS
- Zscaler Internet Access
-
-
- ION 5.2
- ION 5.3
- ION 5.4
- ION 5.5
- ION 5.6
- ION 6.0
- ION 6.1
- ION 6.2
- ION 6.3
- ION 6.4
- New Features Guide
- On-Premises Controller
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
- Prisma SD-WAN CloudBlades
Configure Custom Liveliness Probe
Learn to configure a custom liveliness probe for the Prisma Access
CloudBlades.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma Access for Networks uses the concept of an Infrastructure subnet when
creating the Service Setup under the plugin. The Infrastructure subnet is required
for services within a given Prisma Access tenant.
When you create an Infrastructure subnet, the last usable IP address provided becomes
the following set of services within Prisma Access:
- Captive Portal Redirect IP Address
- Remote Network DNS Proxy IP address
- Tunnel Monitor IP Address
When the CloudBlade creates a standard VPN to Prisma Access, the default is to
use the Tunnel Monitor IP address within the Prisma Access infrastructure, using
a Liveliness Probe. There might be instances where a probe needs to be changed from
the default to monitor additional services external of Prisma Access to meet a
specific business requirement.
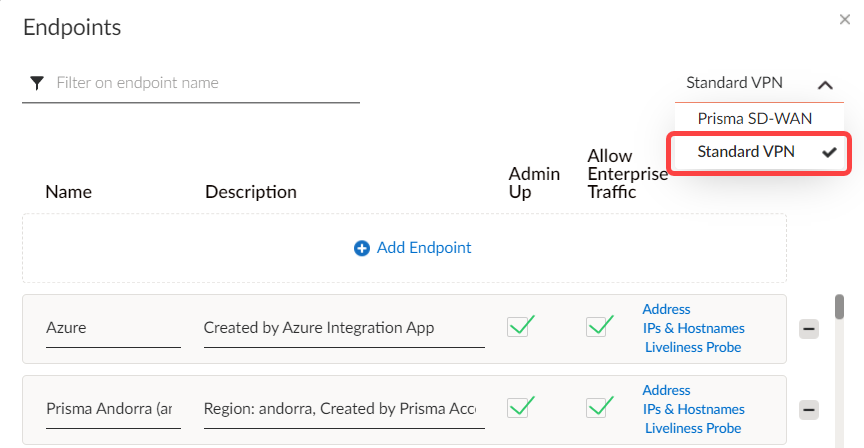
- Within the CloudBlade, the default is to use the last usable Infrastructure IP address. To use a different Liveliness Probe, uncheck the box within the CloudBlade.To configure a Custom Liveliness Probe, navigate to ManagePrisma SD-WANResourcesService & DC Groups within the Prisma SD-WAN web interface.Within the Service & DC Groups, look for and click Manage Endpoints.The default view within Endpoints will be Prisma SD-WAN.Click Standard VPN from the drop-down.
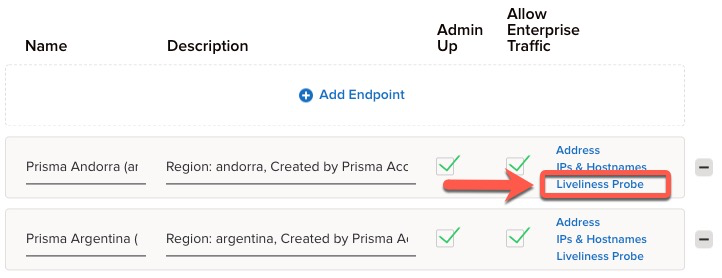
![]() For a given Prisma Access region, find and click Liveliness Probe.
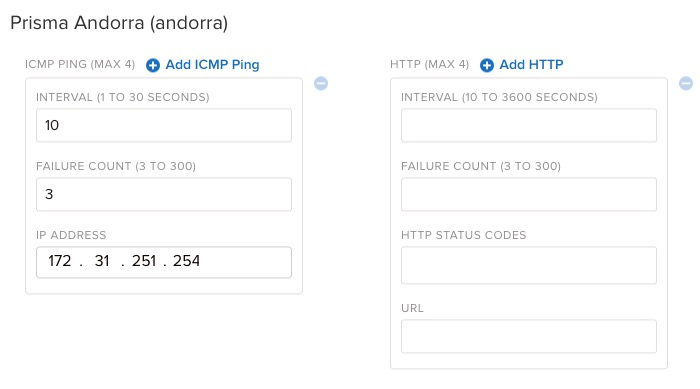
For a given Prisma Access region, find and click Liveliness Probe.![]() The default probe for Prisma Andorra, as chosen in this section, utilizes the last usable IP address in the infrastructure subnet.
The default probe for Prisma Andorra, as chosen in this section, utilizes the last usable IP address in the infrastructure subnet.![]() To add another IP address or modify the probe, edit or add an ICMP ping as appropriate.In the following example, add an additional ICMP probe.
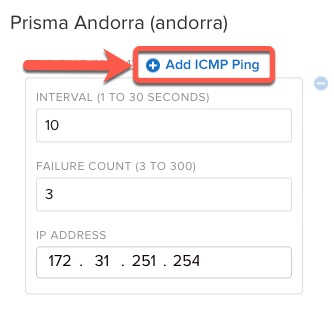
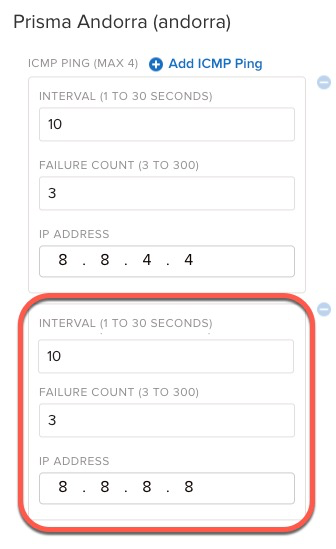
To add another IP address or modify the probe, edit or add an ICMP ping as appropriate.In the following example, add an additional ICMP probe.![]() For this standard VPN to Prisma Access (Prisma Andorra), add an additional ICMP probe to 8.8.8.8 to the Liveliness Probe.
For this standard VPN to Prisma Access (Prisma Andorra), add an additional ICMP probe to 8.8.8.8 to the Liveliness Probe.![]() Repeat this step for each location that needs adjustment on a given business requirement.
Repeat this step for each location that needs adjustment on a given business requirement.