Prisma SD-WAN
Migrate Original Policy Sets to Stacked Policy Sets
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 6.5
- 6.4
- 6.3
- 6.2
- 6.1
- 5.6
- New Features Guide
- On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Migrate Original Policy Sets to Stacked Policy Sets
Learn how to migrate original policy sets to stacked
policy sets.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Stacked
Policies provide a common administrative domain for a set of sites,
contain policy rules, and are stacked and attached to a site. With
stacked policies you can enable, disable, update, or manage policies,
including performance, priority, path selection, and security without
configuring individual ION devices at a branch or a data center.
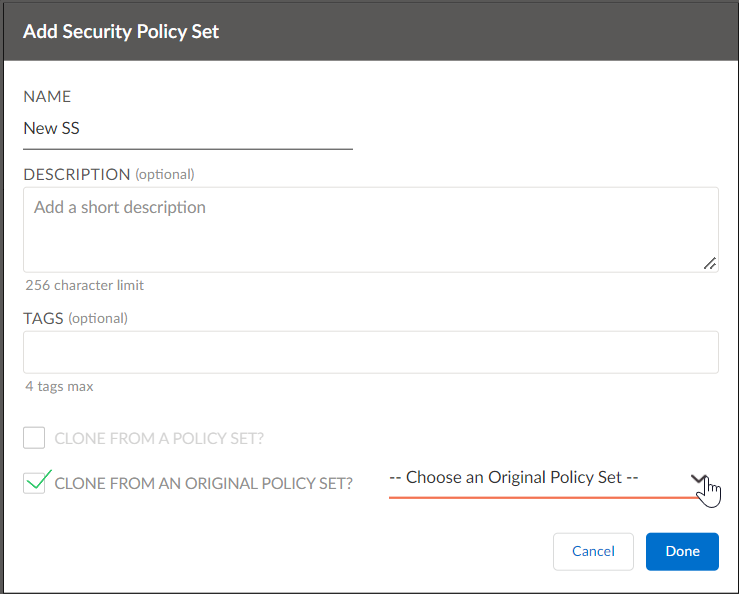
- Select ConfigurationPrisma SD-WANPolicies.Select SecuritySecurity StacksAdvancedSecurity SetsAdd Set.The example shows how to convert an original security policy set to a stacked security policy set. You can extend this to converting Path and QoS sets also.To migrate from original network policies to stacked network policies, you can clone an original network policy set into two types of stacked policy sets—stacked path policy set (for original network policies) and stacked QoS policy set (for original priority policies) and bind them separately to a site.On the Add Security Policy Set screen, enter a Name for the security policy set, and optionally enter description and tags.While adding a name, ensure that there is no stacked policy set having the same name as the original policy set.Select the Clone From an Original Policy Set check box to clone a policy set created under original policies and select a policy set to clone from the Choose an Original Policy Set drop-down.
![]() Click Done to submit your changes.The clone operation creates a new policy set stack for the original security policy set. As part of the clone operation, a policy set containing custom rules from the original policy set and a Default Rule Policy set from the default rules in the original policies is created. The Default Rule Policy set contains three different rules—default-deny, intra-zone-allow, self-zone-allow.In order for stacked security policy rules to be active, bind security policy stacks to a site.
Click Done to submit your changes.The clone operation creates a new policy set stack for the original security policy set. As part of the clone operation, a policy set containing custom rules from the original policy set and a Default Rule Policy set from the default rules in the original policies is created. The Default Rule Policy set contains three different rules—default-deny, intra-zone-allow, self-zone-allow.In order for stacked security policy rules to be active, bind security policy stacks to a site.