SaaS Agent Security
Onboard ServiceNow to SaaS Agent Security
Table of Contents
Expand All
|
Collapse All
SaaS Agent Security Docs
Onboard ServiceNow to SaaS Agent Security
Onboard ServiceNow to SaaS Agent Security to gain deep visibility and security for
your ServiceNow AI platform and apps.
Onboard ServiceNow to gain deep visibility and security for your ServiceNow AI
platform and apps. To secure access to your ServiceNow data and successfully onboard
to SaaS Agent Security, you must:
- Create an application registry that the platform will use to access your ServiceNow data via the REST API. The configuration consists of creating a user, creating an authentication scope, and using them to create an application registry.
- Onboard ServiceNow platform to SaaS Agent Security.
This onboarding procedure has been written for the
Yokohama release of ServiceNow. Since ServiceNow is highly
customizable, some steps might vary if you are onboarding using a different
version of ServiceNow.
Prerequisites
- Ensure you configure the ServiceNow SaaS Security Posture Management connector before onboarding ServiceNow to SaaS Agent Security.
- Ensure you have the necessary administrative privileges in your ServiceNow instance, including the ability to elevate your role to security_admin to create and manage Access Control Lists (ACLs).
Use the database tables on ServiceNow during onboarding and if needed troubleshoot
onboarding ServiceNow to .
Use STEPS 1 to 4 to create an application registry and STEPS 5 to 8 to
onboard ServiceNow platform to SaaS Agent Security.
- Create a user.Ensure you elevate your role to security_admin before creating the user and grant read-only access to the required tables using Access Control Lists (ACLs). Or, you could also edit existing roles.
- Sign in to your ServiceNow instance.In the search box, start typing and select User Administration - UsersNew and enter the following details:
- User ID
- First name and Last name
- Email
- Select the Web service access only check box. This is critical as it ensures the user can’t be used for interactive sign-in.
- Select the Active check box and Submit the new user record.
Since ServiceNow roles are highly customizable, you can either choose an existing role, which grants you a read-only permission to all the tables or create a custom role with read-only permissions and assign the custom roles or updated roles to the user.Create an authentication scope to limit access to ServiceNow REST APIs.During onboarding, you will log in to a ServiceNow account and will grant SaaS Agent Security access to that account. SaaS Agent Security will get access to your ServiceNow account through an OAuth 2.0 integration application that you will create. Before you create the OAuth 2.0 integration application, create an authentication scope, which will limit SaaS Agent Security's access to only the Table API. You can create a scope that allows SaaS Agent Security read-only access to the Table API. Later, you will assign this scope to your OAuth 2.0 application.- Log in to ServiceNow as an administrator.
- Make sure the REST API Auth Scope plugin (com.glide.rest.auth.scope) is activated in ServiceNow. To verify that the plugin is activated, navigate to System Definition Plugins and use the search field to locate the plugin. If the plugin isn’t installed, refer to the ServiceNow documentation to install and activate the REST API Auth Scope plugin.
- Create the authentication scope.
- Navigate to the Authentication Scopes table (sys_auth_scope.list) by using the filter navigator.
- Click New to define the authentication scope.
- Specify a meaningful Name for your
authentication scope, such as SaaS_Agent_Security_Scope.
You can optionally specify a longer
Description.Make note of the authentication scope name. You will need to specify this name later when you are configuring a REST API Auth Scope and your OAuth 2.0 integration application.
- Submit.
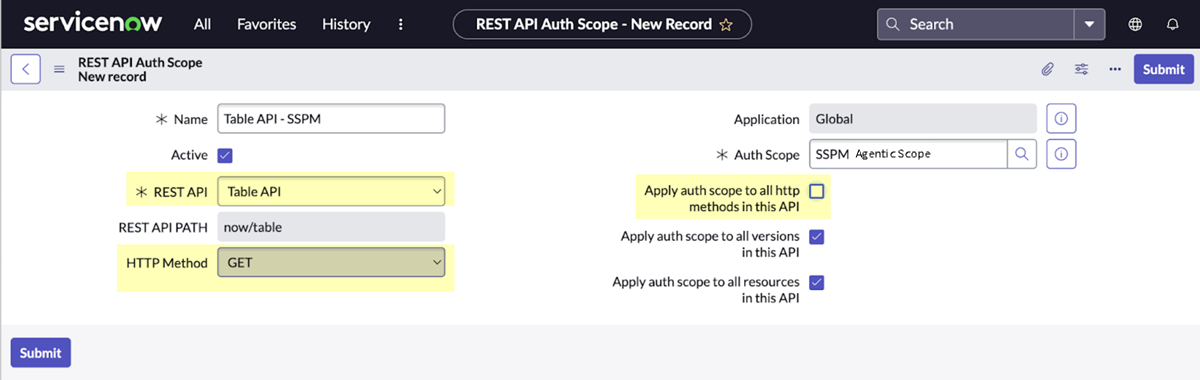
- Create a REST API Auth Scope and link it to your authentication
scope.The REST API Auth Scope is where you will limit SaaS Agent Security access to the Table API only. Allow SaaS Agent Security read-only access only (GET method).
- Navigate to the REST API Auth Scopes list (System Web ServicesAPI Auth ScopesREST API Auth Scope).
- Click New to define the REST API Auth Scope.
- In the Name field, specify a name for your REST API Auth Scope.
- From the REST API list, select Table API.
- Deselect the Apply auth scope to all http methods in this API check box.
- From the HTTP Method list, select GET.
- In the Auth Scope field, specify the name of the authentication scope that you created earlier. This specification links the REST API Auth Scope to the authentication scope.
- Submit.
![]()
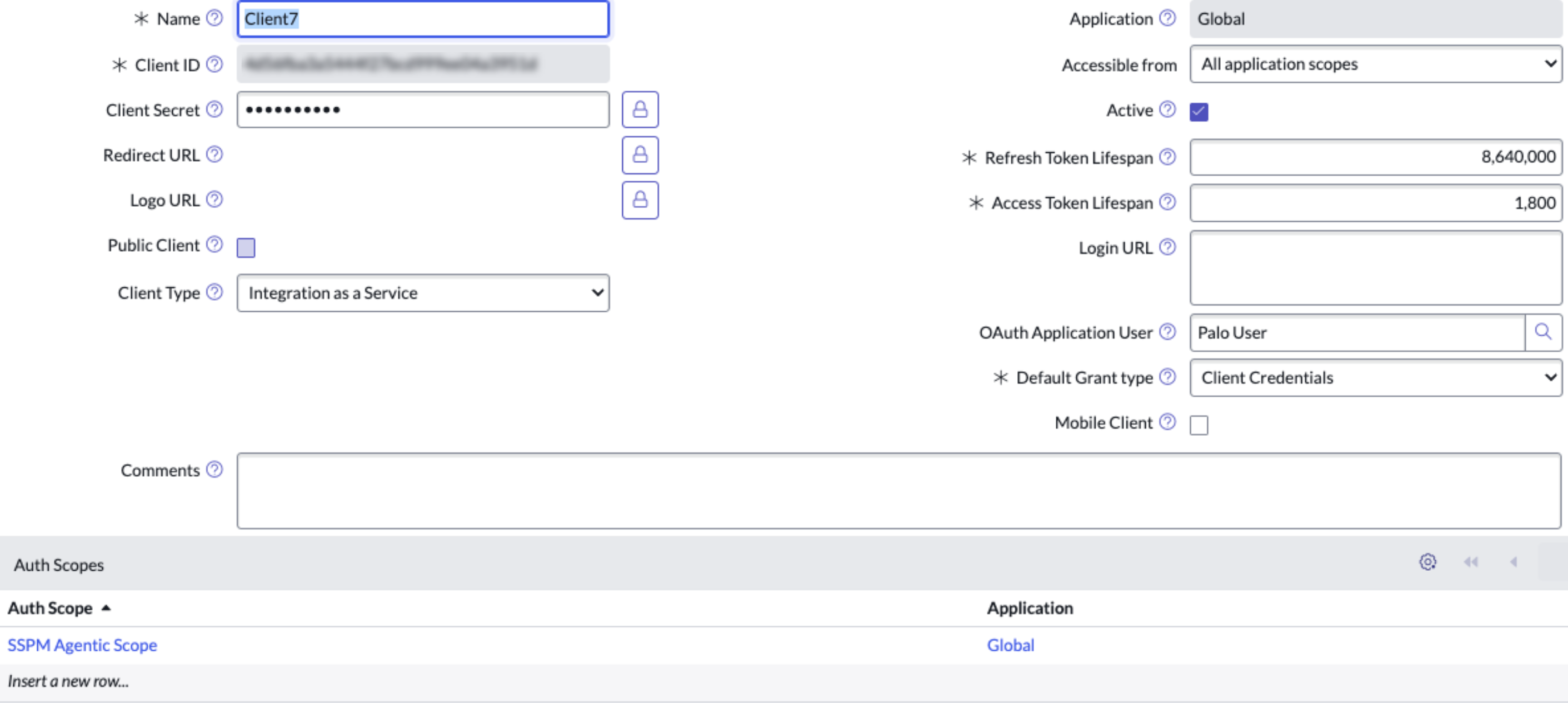
Create the Application Registry (OAuth Client)- Log in to ServiceNow as an administrator.Navigate to the Application Registries page (System OAuth Application Registry).In the Application Registries page, select NewCreate an OAuth API endpoint for external clients.Some details like Client ID and Client Secret are autogenerated. Copy them and keep it handy for the next section. Ensure the following additional details are filled in correctly:Set the Application to Global.Ensure it's accessible from All application scopes.Ensure the Active check box is selected.OAuth Application User: Enter the user you created in Step 1.Default grant type: Choose Client Credentials.Ensure that the system property glide.oauth.inbound.client.credential.grant_type.enabled is set to true.Specify your OAuth Scope that you created in Step 2 and Submit.
![]() Gather Required Information for Onboarding.After completing the configuration in ServiceNow, have the following details handy that you need for onboarding.
Gather Required Information for Onboarding.After completing the configuration in ServiceNow, have the following details handy that you need for onboarding.- ServiceNow Instance URL: The base URL of your ServiceNow instance (for example, https://your-instance.service-now.com).
- Client ID
- Client Secret
To start onboarding ServiceNow platform to SaaS Agent Security, log in to Strata Cloud Manager.Select Agent Platform OnboardingOnboard Agent PlatformServiceNow AI Platform.On the Connection page, enter the information you gathered in step 4 in the corresponding fields:- ServiceNow Instance URL: The base URL of your ServiceNow instance (for example, https://your-instance.service-now.com).
- Client ID
- Client Secret
Connect.The system validates the credentials and permissions. After the validation is successful, you will see a confirmation message.Troubleshoot Onboarding ServiceNow to SaaS Agent Security
The following table lists some common issues that you might face during onboarding ServiceNow to SaaS Agent Security and resolutions that you can try to resolve those issues. Issues Resolution Connection test fails If the connection test fails, ensure that you have copied and pasted the Instance URL, Client ID, and Client Secret correctly. Also, ensure there are no leading or trailing spaces. Permission errors during scanning If you see errors after onboarding, this is likely due to incomplete permissions. Go back to creating an application registry procedure and ensure that the role has a read-only ACL rule for every single table. Also, ensure that this role is correctly assigned to the service user.Database Tables on ServiceNow
Table Names ais_datasourceais_search_profileais_search_profile_ais_search_source_m2mais_search_sourcediscovery_credentialssc_cat_itemsn_aia_agentsn_aia_agent_tool_m2msn_aia_execution_plansn_aia_execution_tasksn_aia_messagesn_aia_skill_metadatasn_aia_team_membersn_aia_trigger_configurationsn_aia_usecasesys_aliassys_connectionsys_cs_conversationsys_cs_topicsys_gen_ai_skillsys_gen_ai_skill_applicabilitysys_hub_action_instance_v2sys_hub_action_type_definitionsys_hub_alias_mappingsys_hub_categorysys_hub_flowsys_hub_flow_basesys_one_extend_capabilitysys_scope