Changes to Default Behavior
Table of Contents
Expand all | Collapse all
Changes to Default Behavior
Review the changes to default behavior in ESM and Traps
4.2 releases.
Changes to Default Behavior in 4.2.8
There are no changes to default behavior introduced
in Traps Endpoint Security Manager and Traps agent 4.2.8.
Changes to Default Behavior in 4.2.7
There are no changes to default behavior introduced
in Traps Endpoint Security Manager and Traps agent 4.2.7.
Changes to Default Behavior in 4.2.5-h1/4.2.6-h1
There are no changes to default behavior introduced
in Traps Endpoint Security Manager and Traps agent 4.2.5-h1/4.2.6-h1.
Changes to Default Behavior in 4.2.6
There are no changes to default behavior introduced
in Traps Endpoint Security Manager and Traps agent 4.2.6.
Changes to Default Behavior in 4.2.5
There are no changes to default behavior introduced
in Traps Endpoint Security Manager and Traps agent 4.2.5.
Changes to Default Behavior in 4.2.4
The following table describes the changes to default
behavior introduced in Traps Endpoint Security Manager and Traps
agent 4.2.4.
| Feature | Change to Default Behavior |
|---|---|
| Quarantine Network Path (CYV-14673) | The Quarantine Network Path setting in the ESM Server Configuration that was supported in ESM 3.1 is now deprecated and is removed from the ESM Console. |
| SHA256 Hash Search Operator (CYV-14772) | The operator Contains used to search for SHA256 hashes that match a partial string is now deprecated and is superseded by the new operators introduced in 4.2.4. |
Changes to Default Behavior in 4.2.3
The following table describes the changes to default
behavior introduced in Traps Endpoint Security Manager and Traps
agent 4.2.3.
| Feature | Change to Default Behavior |
|---|---|
| Shellcode Preallocation Data Collection (CYV-14659) | When the Shellcode Preallocation exploit protection module triggers a security event, the Traps agent now collects ShellcodeInformation system calls and addresses with relevant forensics data collection. |
| DEP Module Advanced Setting (CYV-14553) | The Allocated Only setting—which was available from Ninja Mode of the DEP application protection module—is now deprecated and is no longer configurable from the ESM Console. |
Changes to Default Behavior in 4.2.2
The following table describes the changes to default
behavior introduced in Traps Endpoint Security Manager and Traps
agent 4.2.2.
| Feature | Change to Default Behavior |
|---|---|
| DEP Memory Handling (CYV-14450) | When a protected process attempts to access unallocated memory, the Traps DEP exploit protection module no longer triggers a security event (in notification mode) or captures the memory when this type of event occurs. This reduces the need for incompatibility rules required to prevent Traps from capturing data that was unusable. |
Changes to Default Behavior in 4.2.1
The following table describes the changes to default
behavior introduced in Traps Endpoint Security Manager and Traps
agent 4.2.1.
| Feature | Change to Default Behavior |
|---|---|
| Whitelists in Cloned Rules | When you clone a rule from the default policy that contains a whitelist, you can no longer make changes to the whitelist. This protects you from inadvertently overwriting the recommended whitelist when you clone and edit a rule from default policy. Now, to make changes to a whitelist, you can configure an exception. |
| Child Process Exceptions in Cloned Rules | When you upgrade to Traps ESM 4.2.1, the ESM
now migrates cloned rules that contains a whitelist or blacklist
to exception rules. The ESM matches parent rules containing lists
(for example, blacklist or whitelist) and determines changes to
the lists. The ESM then creates a single process exception rule
to capture the change to the policy. For cloned rules that removed
a process from a blacklist, the ESM creates a new rule which allows
the removed process. For cloned rules that added a process to a
blacklist, the ESM creates a new rule which blocks the added process. 
|
| Support File Enhancement | To assist you with hash and verdict investigation, the Traps agent now includes the local WildFire cache and log files stored in %programdata%\Cyvera\LocalSystem when it sends the Tech Support File. The WildFire cache allows you to view all hashes and verdicts that are locally stored in the agent. |
| Enhanced DLL Whitelist | The whitelist capabilities of the JIT and DLL security exploit protection modules (EPMs) has been enhanced in the default security policy. |
| Multi-ESM Setting Detection | For increased visibility, the details and
edit views of the Multi-ESM settings have changed. By default, the
ESM Console now automatically detects the internal and external
addresses, and uses those values as placeholders. In the
expanded details view of the server, the ESM Console displays indicates
the source as Autodetected for placeholder
values or as ESM Settings if you configure alternate
values. 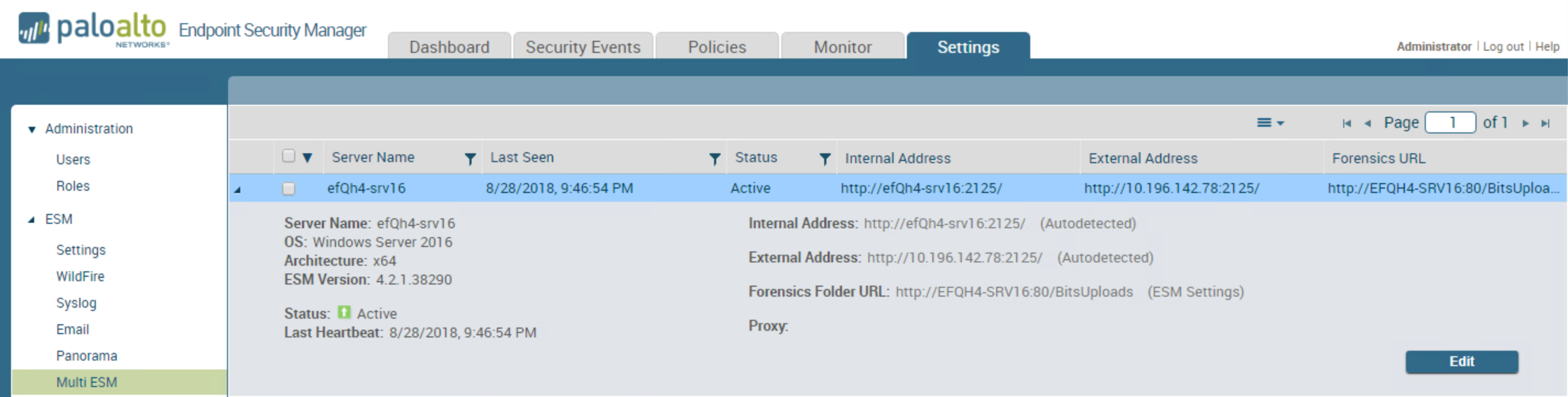
In
edit mode, the ESM Console shows auto-detected values in gray and
edited values in regular black text. |
| Automated Temp File Cleanup | The ESM Server and ESM Console now employ a cleanup policy to automatically purge files in the temp and forensic folders. The cleanup policy runs every 24 hours and removes files older than 30 days from the forensic folder and all files in the temp folders. This prevents outdated and unneeded files from impacting ESM functionality. |
Changes to Default Behavior in 4.2.0
The following table describes the changes to default
behavior introduced in Traps Endpoint Security Manager and Traps
agent 4.2.0.
| Feature | Change to Default Behavior |
|---|---|
| Child Process Protection rule merging | By default, Child Process Protection rules are now merged with the default policy. If the case of rule conflicts, the user-defined child process protection rule takes precedence. |
| Enhanced Content Updates | To align the content structure between the different management servers, the Endpoint Security Manager now supports a new content update format. To distinguish from older content updates, the Customer Support Portal now separates content updates into two sections: 3.4 to 4.1 versions and 4.2 and above. The enhanced content updates also follow a different numbering scheme. To determine the minimum supported content update version, see Associated Software and Content Versions. |
| Conditions | Some conditions in the default security policy are now defined in the new content structure using APIs. With this change, the ESM Console displays non-API definitions as N/A in the additional details view of the condition. |
