Advanced URL Filtering
Block Search Results When Strict Safe Search Is Off
Table of Contents
Block Search Results When Strict Safe Search Is Off
Enforce safe search by blocking search results for end
users on supported search engines until they set the safe search
settings to the strictest level.
| Where can I use this? | What do I need? |
|---|---|
|
Notes:
|
If you enable Safe Search Enforcement, the default
behavior of the firewall is to block search results for end users
searching on Bing, Yahoo, Yandex, or Youtube search engines until
they set their safe search setting to the strictest available option.
By default, the URL filtering safe search block page displays in
their browser. The predefined block page provides
a link to the search settings for the search engine used, so that
users can adjust the safe search setting. You can customize the safe
search block page to meet your organization’s specific needs.
If
you plan to use this method to enforce safe search, communicate
this policy to your end users before implementing it. If you prefer
to automatically redirect end users’ search query URLs to strict
safe search versions, then enable strict safe search
transparently.
Palo Alto Networks can no longer
detect if Google SafeSearch is on due to changes in Google’s implementation.
As a result, the firewall cannot enforce safe search using this
method. You may still enforce safe search transparently. However,
we cannot guarantee that Google will filter out explicit images
and content.
Block Search Results When Strict Safe Search Is Off (Strata Cloud Manager)
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS tab
and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
- Enable Safe Search Enforcement in a URL Access Management profile.
- Select ConfigurationNGFW and Prisma Access Security ServicesURL Access Management.Under URL Access Management Profiles, select an existing profile or Add Profile to create a new one. Configuration options appear.Under Settings, select Safe Search Enforcement.Save the profile.(Optional) Restrict the search engines that end users can access.
- Select ConfigurationNGFW and Prisma Access Security ServicesURL Access Management.Under Access Control, Search () for the search-engines category.
![]() Set Site Access for the search-engines category to block.In a later step, you’ll create a custom URL category (URL List type) with the search engines you want to allow.Save the profile.Apply the URL Access Management profile to Security policy rules that allow traffic from clients in the trust zone to the internet.To activate a URL Access Management profile (and any Security profile), add it to profile group and reference the profile group in a Security policy rule.Create a custom URL category for the supported search engines.In the next step, you’ll configure the firewall to decrypt traffic to this custom category.
Set Site Access for the search-engines category to block.In a later step, you’ll create a custom URL category (URL List type) with the search engines you want to allow.Save the profile.Apply the URL Access Management profile to Security policy rules that allow traffic from clients in the trust zone to the internet.To activate a URL Access Management profile (and any Security profile), add it to profile group and reference the profile group in a Security policy rule.Create a custom URL category for the supported search engines.In the next step, you’ll configure the firewall to decrypt traffic to this custom category.- Select ConfigurationNGFW and Prisma Access Security ServicesURL Access Management.Under Access Control, for Custom URL Categories, Add Category.Enter a Name for the category, such as SearchEngineDecryption.For Type of custom URL category, select URL List.Under Items, Add the following entries to the URL list:
- www.bing.*
- search.yahoo.*
- yandex.com.*
Save the custom category.Configure Site Access for the new custom URL category.- Under URL Access Management Profiles, select the profile you configured earlier.
- Under Access Control, select the new custom URL category. It appears in the Custom URL Categories section above External Dynamic URL Lists and Pre-Defined Categories.
- Set Site Access to allow.
- Save your changes.
Configure SSL Forward Proxy decryption.Because most search engines encrypt their search results, you must enable SSL Forward Proxy decryption so the firewall can inspect the search traffic and detect the safe search settings.Under the Services and URLs section of the Decryption policy rule, click Add URL Categories. Then, select the custom URL category you created earlier. New custom categories sit at the top of the list.Save the Decryption policy rule.Select Push Config to activate your changes.Verify the Safe Search Enforcement configuration.This verification step only works if you use block pages to enforce safe search. There is an alternative verification step if you enable safe search transparently.- From a computer behind the firewall, disable the strict search settings for a supported search provider. For example, on bing.com, click the Preferences icon on the Bing menu bar.
![]() Set the SafeSearch option to Moderate or Off, and click Save.Perform a Bing search (or search using another provider) to see if the URL Access Management safe search block page displays instead of search results:
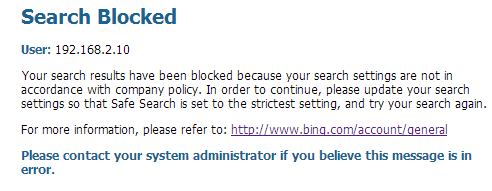
Set the SafeSearch option to Moderate or Off, and click Save.Perform a Bing search (or search using another provider) to see if the URL Access Management safe search block page displays instead of search results:![]() Use the link on the block page to update the safe search setting to the strictest setting (Strict in the case of Bing), and then click Save.Perform a search again from Bing and verify that filtered search results display instead of the block page.
Use the link on the block page to update the safe search setting to the strictest setting (Strict in the case of Bing), and then click Save.Perform a search again from Bing and verify that filtered search results display instead of the block page.Block Search Results When Strict Safe Search Is Off (PAN-OS & Panorama)
- Enable Safe Search Enforcement in a URL Filtering profile.
- Select ObjectsSecurity ProfilesURL Filtering.Select an existing profile to modify or clone the default profile to create a new profile.On the URL Filtering Settings tab, select Safe Search Enforcement.(Optional) Restrict the search engines that end users can access in the same URL Filtering profile.
- On the Categories tab, Search () for the search-engines category.
![]() Set Site Access for the search-engines category to block.In a later step, you’ll create a custom URL category (URL List type) with the search engines you want to allow.Click OK to save the profile.Apply the URL Filtering profile to Security policy rules that allow traffic from clients in the trust zone to the internet.
Set Site Access for the search-engines category to block.In a later step, you’ll create a custom URL category (URL List type) with the search engines you want to allow.Click OK to save the profile.Apply the URL Filtering profile to Security policy rules that allow traffic from clients in the trust zone to the internet.- Select PoliciesSecurity. Then, click the rule to which you want to apply the URL Filtering profile.On the Actions tab, find Profile Setting. For Profile Type, select Profiles. A list of profiles appears.For URL Filtering profile, select the profile you created earlier.Click OK to save the Security policy rule.Create a custom URL category for the supported search engines.In the following step, you’ll specify that you want to decrypt traffic to the sites in the custom category.
- Select ObjectsCustom ObjectsURL Category and Add a custom category.Enter a Name for the category, such as SearchEngineDecryption.Add the following entries to the Sites list:
- www.bing.*
- search.yahoo.*
- yandex.com.*
Click OK to save the custom category.Configure Site Access for the new custom URL category.- Go to ObjectsSecurity ProfilesURL Filtering and select the URL Filtering profile you configured earlier.
- On the Category tab, select the new custom URL category. It appears in the Custom URL Categories section above External Dynamic URL Lists and Pre-defined Categories.
- Set Site Access to allow.
- Click OK to save your changes.
Configure SSL Forward Proxy decryption.Because most search engines encrypt their search results, you must enable SSL Forward Proxy decryption so the firewall can inspect the search traffic and detect the safe search settings.On the Service/URL Category tab of the Decryption policy rule, Add the custom URL category you created earlier. Then, click OK.Commit your changes.Verify the Safe Search Enforcement configuration.This verification step only works if you use block pages to enforce safe search. There is an alternative verification step if you enable safe search transparently.- From a computer behind the firewall, disable the strict search settings for a supported search provider. For example, on bing.com, click the Preferences icon on the Bing menu bar.
![]() Set the SafeSearch option to Moderate or Off, and click Save.Perform a Bing search (or search using another provider) to see if the URL Filtering Safe Search Block page displays instead of search results:
Set the SafeSearch option to Moderate or Off, and click Save.Perform a Bing search (or search using another provider) to see if the URL Filtering Safe Search Block page displays instead of search results:![]() Use the link on the block page to update the safe search setting to the strictest setting (Strict in the case of Bing), and then click Save.Perform a search again from Bing and verify that the filtered search results display instead of the block page.
Use the link on the block page to update the safe search setting to the strictest setting (Strict in the case of Bing), and then click Save.Perform a search again from Bing and verify that the filtered search results display instead of the block page.