AI Access Security
Generate an AI Access Security Report
Table of Contents
Expand All
|
Collapse All
AI Access Security Docs
Generate an AI Access Security Report
The AI Access Security Report provides a comprehensive overview of your
organization's GenAI app usage and security posture.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following:
|
The AI Access Security Report provides a comprehensive overview of your
organization's GenAI app and plugin usage and security posture. This report helps
you understand and manage the risks associated with rapidly evolving GenAI apps in
your environment. Packed with actionable insights and tailored recommendations, this
report allows your security administrators to make informed decisions about your
GenAI app adoption strategy and security.
Key components of the AI Access Security Report include:
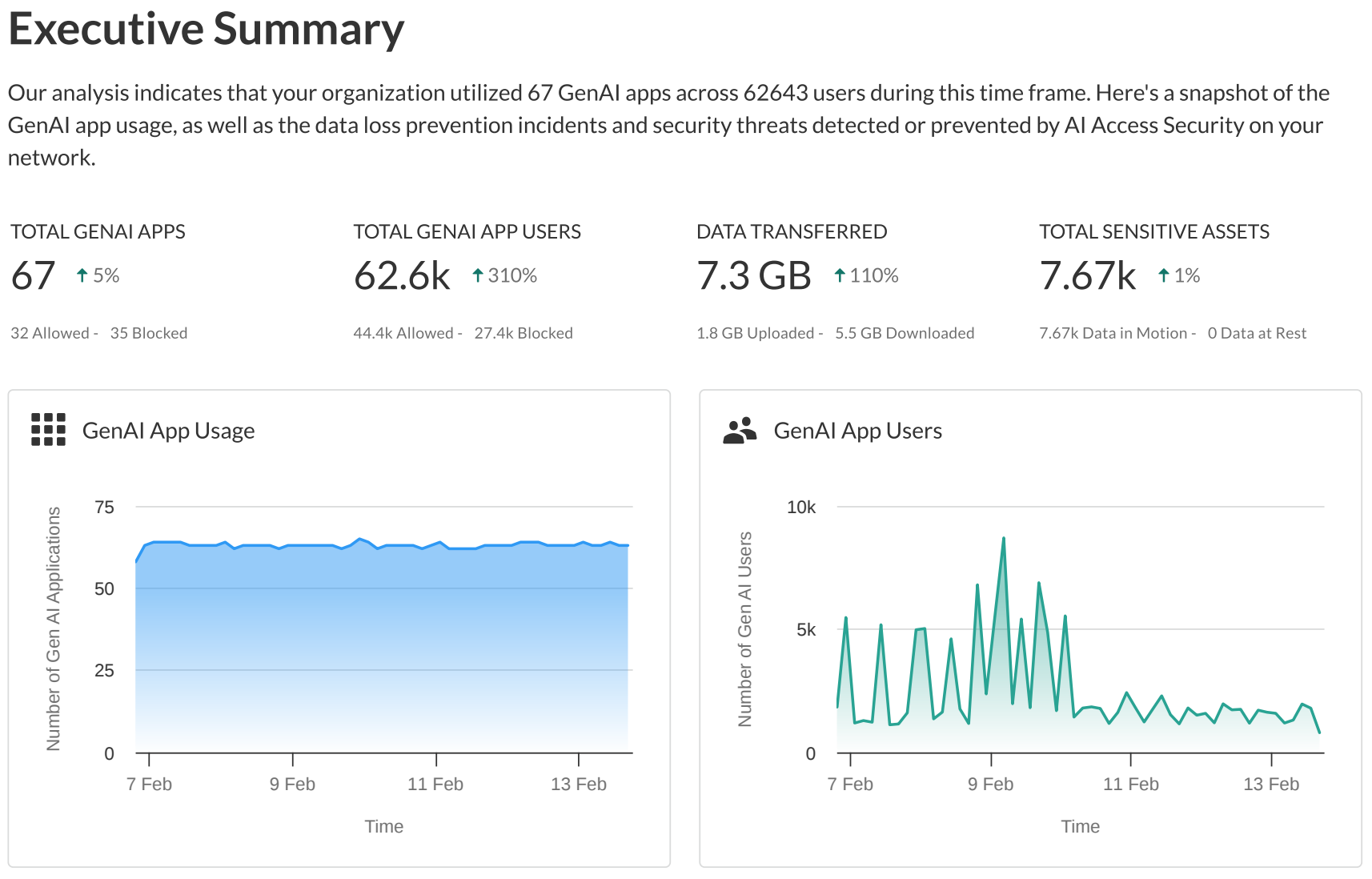
- Executive SummaryThe Executive Summary section provides a high-level snapshot of key GenAI app and plugin metrics in your organization. It offers a concise overview of:
- GenAI app usage, giving you a quick understanding of how widely users in your organization access these apps.
- The volume of data uploaded and downloaded from GenAI apps in gigabyte (GB).
- Number of sensitive data assets detected for data in motion and at rest.
The Executive Summary section gives your security administrators a quick, at-a-glance view of the GenAI app landscape within your organization. It serves as an entry point to the more detailed information provided in subsequent sections of the report, allowing your security administrators to quickly grasp your organization's overall GenAI security posture and to identify areas that might require further attention or investigation.![]()
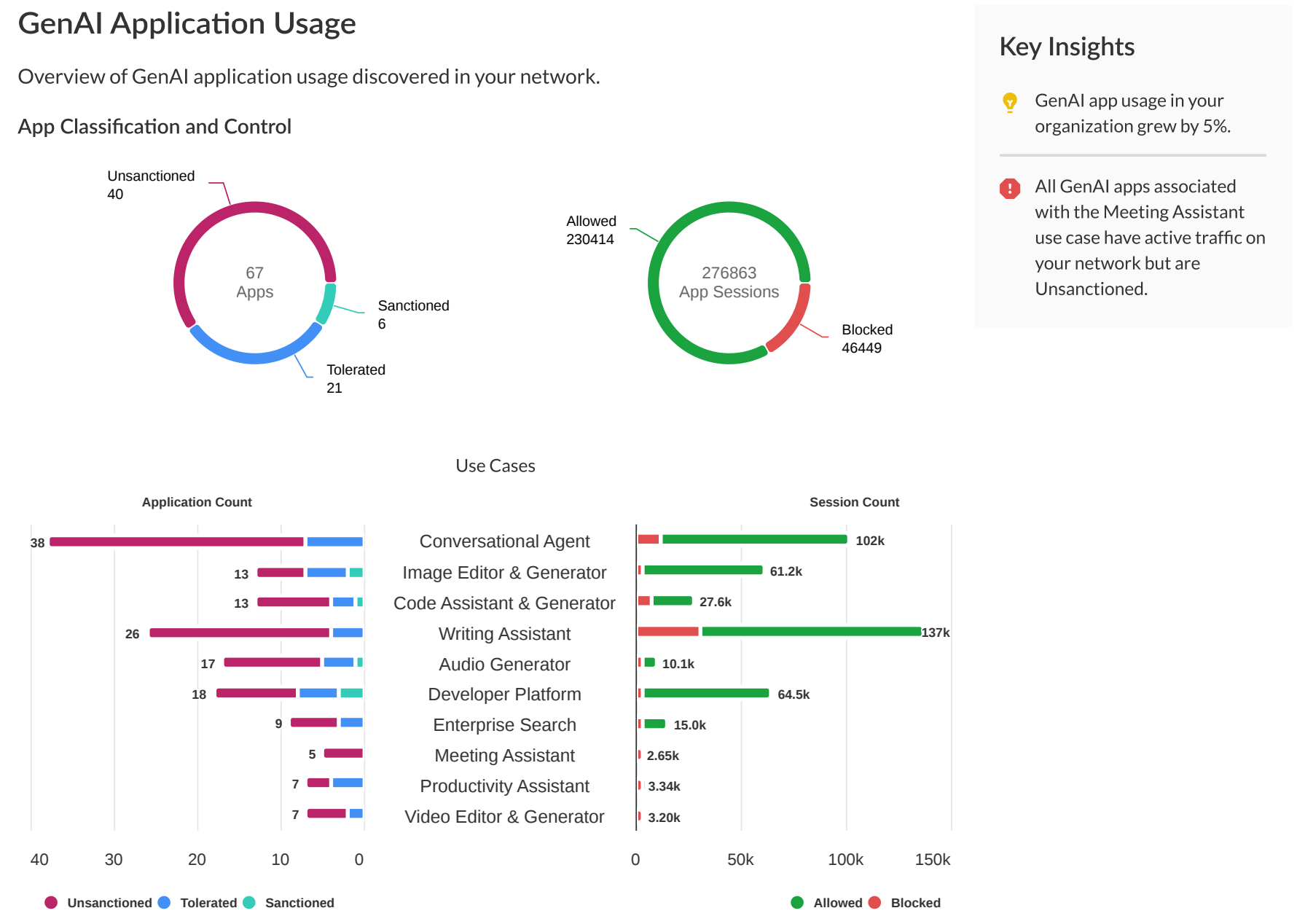
- GenAI App UsageThe GenAI App Usage section provides a comprehensive breakdown of GenAI app usage within your organization. It includes:
- Total number of GenAI Apps, showing the distribution between Allowed and Blocked GenAI apps, and Sanctioned, Tolerated, and Unsanctioned GenAI apps.
- Breakdown of GenAI use cases, categorized by the app classification (Sanctioned, Tolerated, or Unsanctioned) and whether traffic was Allowed or Blocked.
- Number of Unsanctioned but allowed apps, including the change since the start of the reporting period.
- Aggregate usage data for unsanctioned but allowed GenAI apps, including number of users and total amount of data transferred.
- Details on the top 5 Unsanctioned but allowed GenAI apps, including app name, number of users, number of sessions, and associated risk factors.
This section helps your security administrators quickly identify potential security risks, understand GenAI app utilization across different use cases, and make informed decisions about app usage policy rules and your security posture.![]()
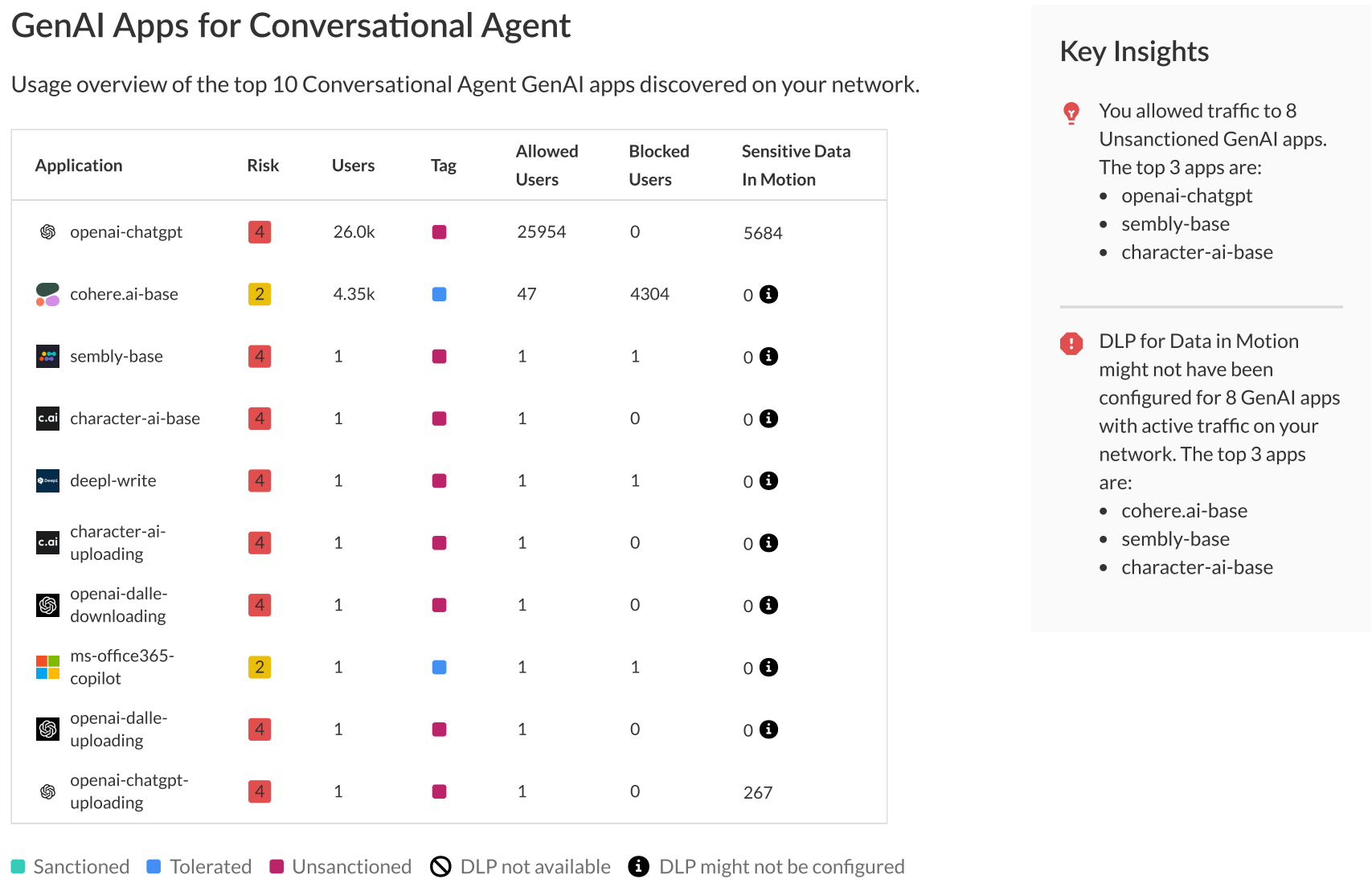
- GenAI Apps for Top Use CasesThe GenAI App for Top Uses sections provides a summary of the top 10 GenAI app used within your organization categorized by the GenAI app Use Case. It provides a detailed breakdown of the most prominent GenAI apps used within your organization and includes the following for each GenAI app:
- Name of the GenAI app used.
- Risk score associated with the GenAI app.
- Number of unique users who used the GenAI app.
- GenAI app classification, indicating whether the app is Sanctioned, Tolerated, or Unsanctioned.
- Number of unique sessions allowed and blocked for the GenAI app.
- Number of Enterprise DLP incidents generated by users accessing the GenAI app.
![]()
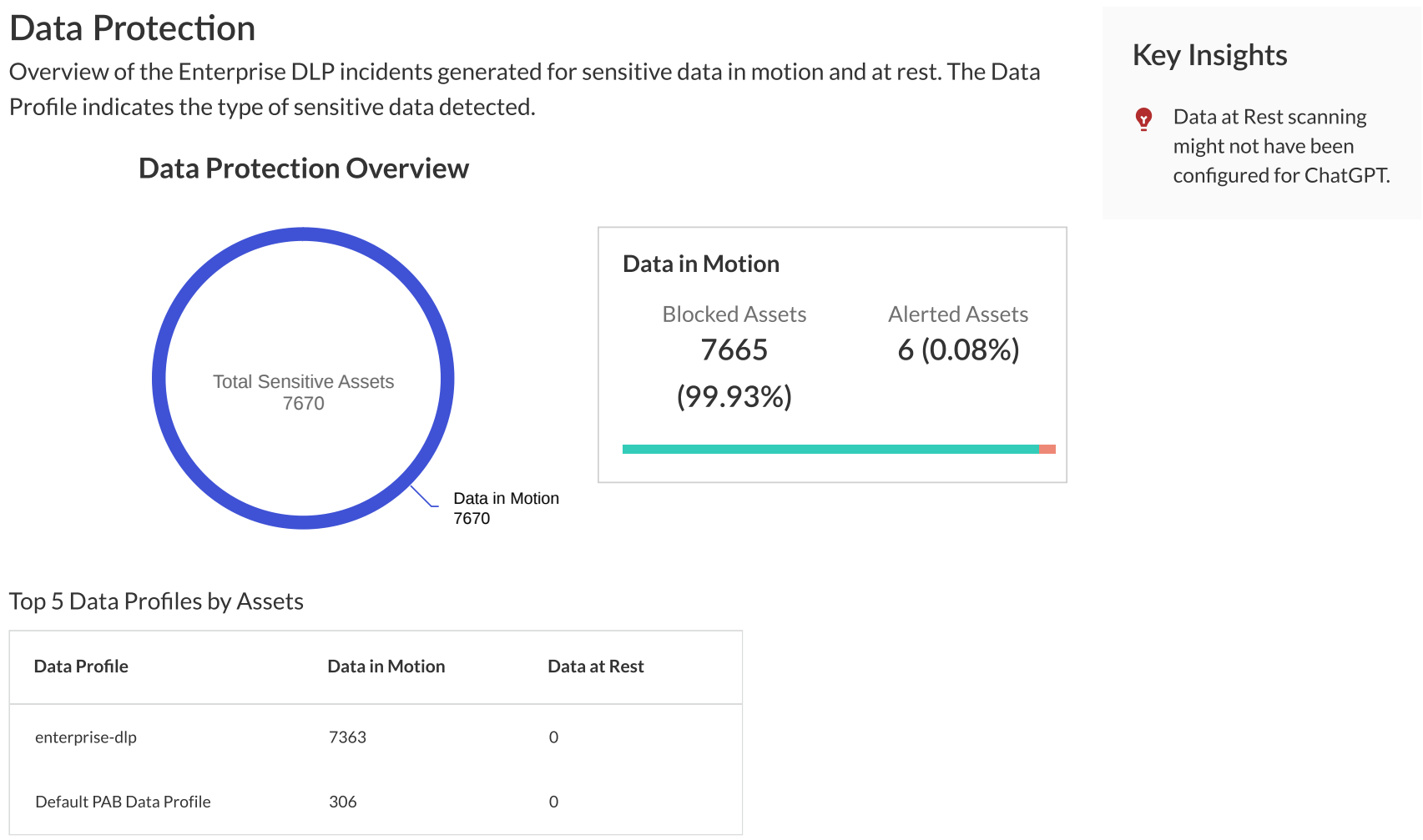
- Data ProtectionThe Data Protection section provides crucial insights into the handling of sensitive data within your organization's GenAI ecosystem. This section includes:
- Total number of sensitive assets detected, categorized as Allowed or Blocked.
- Distribution of sensitive assets across all GenAI apps, grouped by sensitive asset type.
- Detailed information on sensitive data found in the top 5 GenAI apps.
This information helps your security administrators quickly identify potential data security risks associated with GenAI app usage in your organization. By highlighting which GenAI apps are handling sensitive information and what types of sensitive data are being processed, you can prioritize your data protection efforts and adjust your Security policy rules as needed.![]()
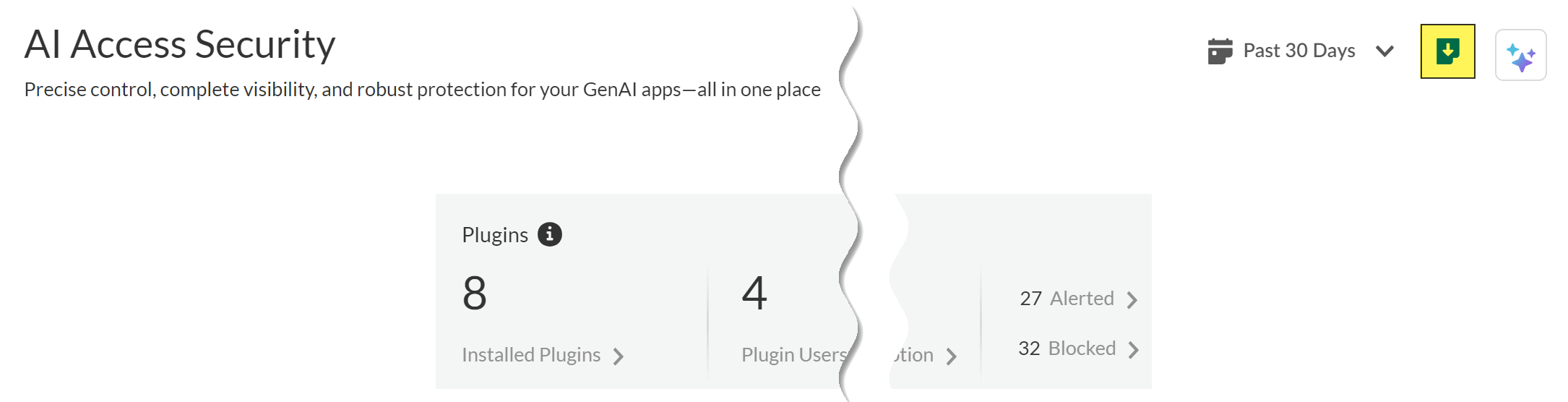
- Log in to Strata Cloud Manager.Select InsightsSECURITYAI Access.Select the time frame for the AI Access Security Report.AI Access Security supports generating a report for the Past 24 Hours, Past 7 Days, or Past 30 Days.Download the AI Access Security Report to your local device in PDF format.The default file name is AI Access Security Report <generation-date>.pdf.Don't leave or refresh the page before the AI Access Security Report download completes. Leaving or refreshing the page before the download completes interrupts the download and you must download the AI Access Security Report again.
![]() Navigate to your download folder you selected and review the AI Access Security Report.
Navigate to your download folder you selected and review the AI Access Security Report.![]()