Prisma AIRS
Secure Container Traffic in Private Cloud
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Secure Container Traffic in Private Cloud
Use Prisma AIRS AI Runtime Firewall to secure container
traffic in private clouds.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
This page also covers Panorama configurations to route traffic
through Prisma AIRS AI Runtime Firewall.
If you have
clusters in a private cloud, you can follow this workflow by applying the Helm chart
and routing the traffic through Prisma AIRS AI Runtime
Firewall.
For Panorama managed Prisma AIRS AI
Runtime Firewall, you can apply the Prisma AIRS Helm chart without going through the
deployment workflow on the Strata Cloud Manager.
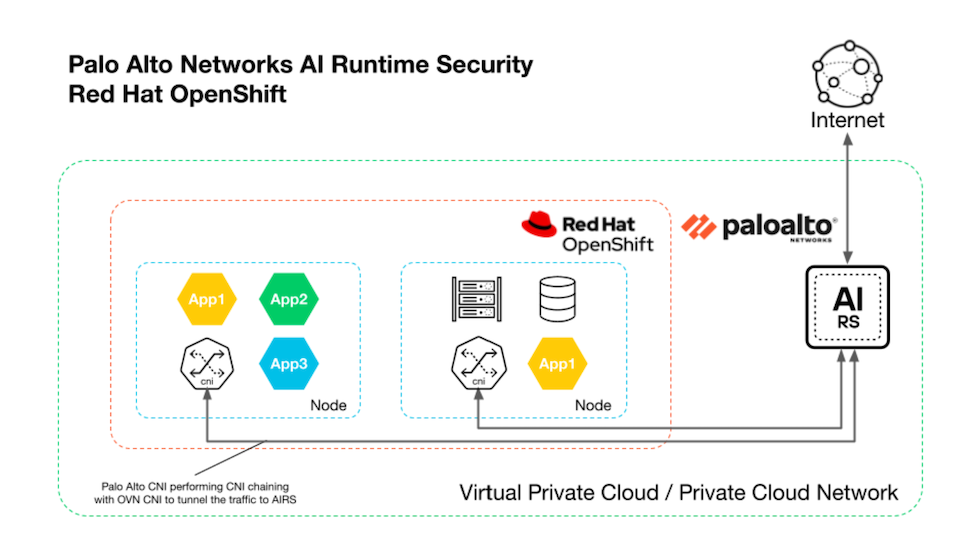
The diagram shows how Prisma AIRS AI Runtime
Firewall integrates with OpenShift using CNI chaining. In this setup, Prisma AIRS AI Runtime Firewall runs as a secondary CNI
plugin, alongside the cluster’s primary CNI. In this setup, Prisma AIRS AI Runtime Firewall redirects east-west
container traffic through Panorama-managed firewalls for real-time, AI-driven
inspection and policy enforcement.
Configure Panorama to Secure Kubernetes Clusters
Interfaces
- Log in to the Panorama Web Interface.Navigate to Network > Interfaces.Set the Configuration Scope to your AI Runtime Security folder.Select Add Interface.
- In the Ethernet tab, Configure a Layer 3 Interface for eth1/1(trust).
- Enter Interface Name (Create interface for eth1/1(trust) interface).
- Select the Layer3 Interface type.
- In Logical Routers, select `lr-private` for eth1/1.
- In Zone, select trust for eth1/1.
- In the IPV4 address, select Static or DHCP Client type.
- Enable IPV4 for eth1/1.
- Select Advanced Settings Other Info.
- Select a Management Profile or create a new one.In Administrative Management Services, enable HTTPS.
- Click Add.
Zones
- Configure Zones (Network → Zones).Select Add Zone.Enter a Name.Select the Layer3 Interface type.In Interfaces, add the $eth1 interface for the trust zone.Select Save.
NAT Policy
Configure the NAT Policy for outbound traffic. - Configure NAT policy for inbound traffic:
- Enter a Name indicating inbound traffic (for example, inbound-web).Original Packet:
- In Source zones, click add and select trust zone.
Destination:- Select trust destination zone.
- Select any Interface.
- In Addresses, click the add (+) icon and select the `app-vnet` and the Kubernetes pods CIDR you want to secure.
Choose any Service.Translated Packet:- In Translation, select Source Address Only.
- In Source Address Translation, select the Dynamic IP and Port translation type.
- In choice, select Interface Address.
- In Interface, select eth1(ethernet1/1).
- In Choice, select an IP address.
Select Save.Logical Routers
Configure private logical routers. - Log in to the Panorama Web Interface.Navigate to Network → Logical Routers → Router Settings.Enter a Name indicating a private router (for example, lr-private).In Interfaces, select eth1(ethernet1/1) for lr-private route.Refer to the section on Interfaces to see how to configure the $eth1 interface.In Advanced Settings, select Edit to configure the IPv4 Static Routes for lr-private.
- Select Add Static Route and add the following routes:Application routing:
- Enter a Name (for example, app-vnet).
- In Destination, enter the CIDR address of your application.
- In the Next Hop:
- For lr-private, in the IP Address field, enter the gateway IP address of the private interface.
Default routing:- Enter a Name.
- In Destination, enter 0.0.0.0/0.
- In the Next Hop:
- For lr-private, in the IP Address field, enter the gateway IP address of the private interface.
- Select Add or Update.
In Interface, select eth1(ethernet1/1) for lr-private.Select Add.Select Save.Security Policy
- Log in to the Panorama Web Interface.Add a security policy rule with an AI security profile attached to it.Set the security policy action to Allow.Select Commit → Commit and Push, to push the policy configurations to the Prisma AIRS AI Runtime Firewall.
Install Kubernetes Cluster and Set Up Panorama
Install Kubernetes cluster and set up Panorama. - Complete the Panorama managed Prisma AIRS AI Runtime onboarding prerequisites.Install the Kubernetes Plugin and Set up Panorama.Add Kubernetes cluster information to Panorama to ensure that the two can communicate with each other.Check the monitoring interval. The default interval at which Panorama polls the Kubernetes API server endpoint is 30 seconds.
- Navigate to Panorama Plugins Kubernetes Setup General.Ensure to select the Enable Monitoring checkbox.Click the gear icon to edit the Monitoring Interval and change to a range of 30-300 seconds.Navigate to Panorama Plugins Kubernetes Setup Cluster, and Add Cluster.Ensure that you don’t add the same Kubernetes cluster to more than one Panorama (single instance or HA pair) appliance because you may see inconsistencies in how the IP-address-to mappings are registered to the device groups.Enter a Name and the API Server Address.This is the Endpoint IP address for the cluster, which you can get from your Kubernetes deployment. Enter a name, up to 20 characters, to uniquely identify the name of the cluster. You can’t modify this name because Panorama uses the cluster name when it creates tags for the pods, nodes, and services it discovers within the cluster. The format of the API server address can be a hostname or an IP address:port number, and you don’t need to specify the port if you're using port 443, which is the default port.Select the environment Type on which your cluster is deployed.The available options are AKS, EKS, GKE, Native Kubernetes, OpenShift, and Other.Upload the service account Credential that Panorama requires to communicate with the cluster. As described in the create service accounts for cluster authentication workflow, the filename for this service account is plugin-svc-acct.json.If you're uploading the service credentials through CLI/API, please gzip the file, and then do a base64 encoding of the compressed file before you upload or paste the file contents into the Panorama CLI or API. These steps are not required if you're uploading the service credential file on the GUI.Click OK.You can leave the Label Filter and Label Selector configuration to be filled in later. This optional task enables you to retrieve any custom or user-defined labels for which you want Panorama to create tags.
Apply Helm chart to Deploy Prisma AIRS AI Runtime Firewall
This section covers how to install and configure the Helm chart to secure your Kubernetes applications based on the protection level .- Clone the GitHub repository.The helm structure looks like:|____helm |____templates |____.helmignore |____Chart.yaml |____plugin-serviceaccount.yaml |____values.yamlEdit the `values.yaml` file as per your firewall deployment:
- For a standalone firewall, update the endpoints value with the trust IP address of the standalone firewall.
- For an active/passive firewall deployment, update the endpoints
value with the trust interface IP address of the active-primary
server.These changes are valid for OpenShift and Rancher.
Here’s a sample `values.yaml` file:# Default values for ai-runtime-security. # This is a YAML-formatted file. # Declare variables to be passed into your templates. # Firewall trust interface IP Address for on-prem endpoints: 10.101.255.253 # This is the PAN CNI image cniimage: gcr.io/pan-cn-series/airs/pan-cni:latest # This is the AI firewall trust CIDR and is an optional parameter. # Helps in reducing hops in East-West cluster traffic. fwtrustcidr: "" # Resource namespace name namespace: kube-system # This is the Kubernetes Cluster ID value ranging between 1 and 2048. clusterid: 1Install the helm chart with the following command:helm install ai-runtime-security helm --namespace kube-system --values helm/values.yamlVerify the Helm installation with the following command:#List all Helm releases helm list -AThe output looks similar to:#Ensure the output shows your installation with details such as: NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION ai-runtime-security kube-system 1 2024-08-13 07:00 PDT deployed ai-runtime-security-0.1.0 11.2.2Check the pod status with the following command:kubectl get pods -AVerify that the result of the above command lists the pods with names similar to `pan-cni-*****`.Check the endpoint slices using the following command:kubectl get endpointslices -n kube-system | grep panConfirm that the output shows an ILB IP address:NAME ADDRESSTYPE PORTS ENDPOINTS AGE pan-ngfw-svc-endpoints IPv4 6080 10.101.255.253 12hEnsure that the endpoint slice IP address points to the trust interface IP address of the firewall.Verify the Kubernetes resources were created properly:a. Check the service accounts kubectl get serviceaccounts -n kube-system | grep pan b. Check the secrets kubectl get secrets -n kube-system | grep pan c. Check the services: `kubectl get svc -n kube-system | grep pan`You should see resources like pan-cni-sa (service accounts), pan-plugin-user-secret (secrets), and pan-ngfw-svc (service).Annotate at the pod level in your application yaml so that the traffic from the pod is redirected to the Prisma AIRS AI Runtime Firewall for inspection.- Annotate the pod using the below command:For VPC-level security:kubectl annotate namespace <namespace-to-be-annotated> paloaltonetworks.com/firewall=pan-fw
- In OpenShift, use the following command to annotate the app pod `yaml` file:kubectl annotate namespace <namespace-to-be-annotated> k8s.v1.cni.cncf.io/networks=pan-cniFor namespace-level security with traffic steering inspection:kubectl annotate pods --all paloaltonetworks.com/subnetfirewall=ns-secure/bypassfirewallAnnotate each pod, so the pods are moved to the "protected" state across all cloud environments.Restart the existing application pods after applying Helm and annotating the pods for all changes to take effect. This enables the firewall to inspect the pod traffic and secure the containers.For OpenShift, to make the `multus` plugin work, deploy "NetworkAttachmentDefinition" "pan-cni" in every app pod's namespace:kubectl apply -f pan-cni-net-attach-def.yaml -n <target-namespace>
