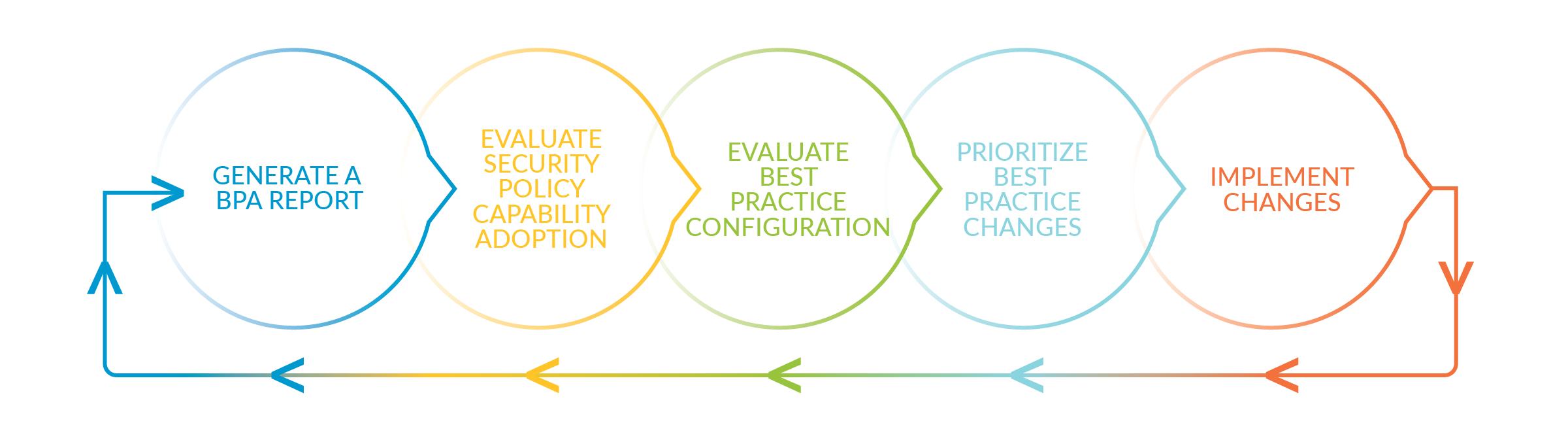
Run the Best Practice Assessment (BPA) to evaluate your security posture and prioritize improvements. Use technical documentation to take the next steps to implement those improvements and transition safely to a best practice state without risking the availability of critical applications. Run the BPA again to measure progress and prioritize the next set of security improvements, use the documentation to implement the improvements, and repeat the cycle until you reach your security goals. Security best practices reduce the attack surface, increase visibility into network traffic, prevent known and unknown attacks, and protect what’s most valuable to your business—proprietary source code, sensitive company and customer data, critical infrastructure—whatever gives your company a competitive advantage.