CN-Series
Install a Device Certificate on the CN-Series Firewall
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
-
-
- Deployment Modes
- In-Cloud and On-Prem
-
-
-
Install a Device Certificate on the CN-Series Firewall
Learn how to install a device certificate to license the CN-Series
firewall.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The firewall requires a device certificate that authorizes secure access to the Palo
Alto cloud-delivered security services (CDSS) such as WildFire, AutoFocus, and
Strata Logging Service. You must apply an auto-registration PIN to apply a CDSS
license to your CN-Series firewall deployment. Each PIN is generated on the Customer Support Portal (CSP) and unique to your Palo Alto Networks
support account. To successfully install the device certificate, the CN-Series
management plane pod (CN-MGMT) must have an outbound internet connection and the
following Fully Qualified Domain Names (FQDN) and ports must be allowed on your
network.
|
FQDN
|
Ports
|
|---|---|
|
TCP 80
|
|
TCP 443
|
|
TCP 444 and TCP 443
|
To add a device certificate to an existing deployment
without an existing device certificate, you must redeploy the CN-Series firewall
after adding the valid PIN ID and value to
pan-cn-mgmt-secret.yaml. For public cloud CN-Series
deployment, you must delete the persistent volume claim before redeployment. For
static/native Kubernetes deployments, you must delete the persistent volume claim
and persistent volume before redeployment.
- Log in to the Palo Alto Networks Customer Support Portal with your account credentials.If you need a new account, see How to Create a New Customer Support Portal User Account.Select AssetsDevice CertificatesGenerate Registration PIN.
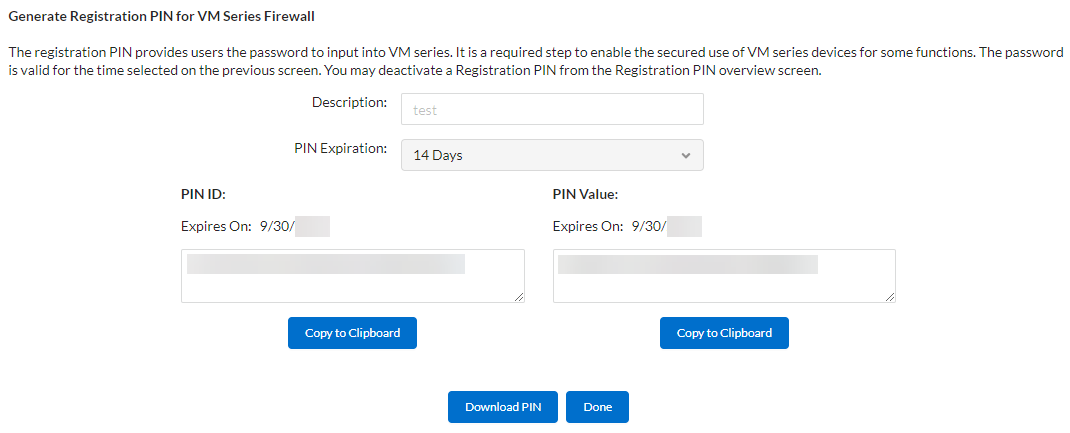
![]() Enter a Description and select a PIN Expiration from the drop-down.
Enter a Description and select a PIN Expiration from the drop-down.![]() Save the PIN ID and value.Save the PIN ID and value. This PIN ID and value are inputs in the pan-cn-mgmt-secret.yaml file used to deploy the cn-series firewall. Make sure to launch the firewall before the PIN expires.# Thermite Certificate retrieval CN-SERIES-AUTO-REGISTRATION-PIN-ID: "<your-pin-id>" CN-SERIES-AUTO-REGISTRATION-PIN-VALUE: "<your-pin-value>"
Save the PIN ID and value.Save the PIN ID and value. This PIN ID and value are inputs in the pan-cn-mgmt-secret.yaml file used to deploy the cn-series firewall. Make sure to launch the firewall before the PIN expires.# Thermite Certificate retrieval CN-SERIES-AUTO-REGISTRATION-PIN-ID: "<your-pin-id>" CN-SERIES-AUTO-REGISTRATION-PIN-VALUE: "<your-pin-value>"