CN-Series
Migrate Your CN-Series Firewall to Prisma AIRS Network Intercept
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
-
-
- Deployment Modes
- In-Cloud and On-Prem
-
-
-
Migrate Your CN-Series Firewall to Prisma AIRS Network Intercept
Learn how to migrate your CN-Series Firewall to Prisma AIRS.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Use the information on this page to migrate your CN-Series firewall to a
Prisma AIRS (formerly referred to as AI Runtime) environment. Here are the
high-level steps for the migration:
- Remove the CN-Series firewall from your deployment.Download and install the newest version of Prisma AIRS (version 11.2.x and above) from the Customer Support Portal.Create the Prisma AIRS deployment profile.Deploy using Prisma AIRS.
Remove the CN-Series Deployment
To remove your CN-Series deployment, you’ll start by deleting any firewalls using the deployment profile in the CSP account, or, you can use Panorama. Next, remove the Kubernetes plugin and any related cluster or monitoring definitions from Panorama. Uninstall the CN-Series firewall from your Kubernetes cluster by removing Persistent Volumes (PV), Persistent Volume Chains (PVCs) and the actual Kubernetes deployment.You may be able to remove all of these elements (PVs, PVCs, and the Kubernetes deployment) by accessing the YAML file used to create them; use the kubectl delete -f command.Delete Your CN-Series Firewall InstancesUse the following procedure to delete CN-Series instances:- Log into your Panorama instance.Navigate to your CN-Series deployment.Delete any firewalls that are using the CN-Series deployment.Refer to steps 5-7 in this document to learn more about transferring credits.Remove the Kubernetes Plugin on Panorama.Remove the Kubernetes plugin if your Prisma AIRS: Network Intercept deployment is managed by Strata Cloud Manager. If the deployment is managed by Panorama, do not uninstall the Kubernetes plugin.Delete your CN-Series Firewall Instance on Panorama:
- Log into your Panorama instance to remove your Kubernetes plugin components.Locate and delete YAML files (for example, pan-cn-pv-local.yaml) used to deploy your CN-Series firewall.Delete PVs/PVCs.Delete the CN-Series deployment entirely using kubectl delete -f..For on-premises deployments, delete the directories containing CN-Series firewall data on each node.
Download and Install Prisma AIRS
To use Prisma AIRS AI Runtime: Network intercept, you must activate your Software NGFW Credits using the Palo Alto Networks Customer Support Portal. These credits enable your deployments and are tied to your BYOL Prisma AIRS license.Unlike CN-Series deployments, which can be managed only from Panorama, Prisma AIRS can be managed from both Strata Cloud Manager and Panorama.Create the Prisma AIRS Deployment Profile
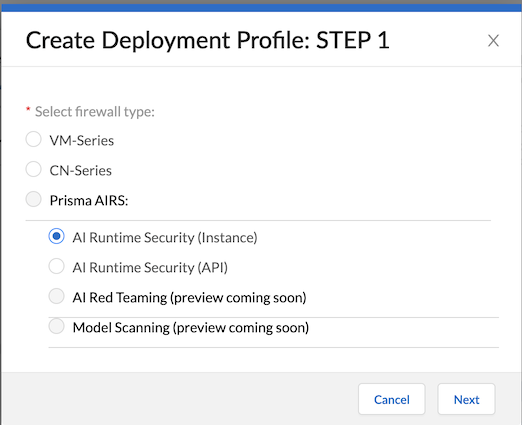
To create the Prisma AIRS deployment, you’ll need to activate and onboard Prisma AIRS: Network Intercept.Deploy Prisma AIRS AI Runtime Security: Network InterceptTo deploy Prisma AIRS AI Runtime: Network intercept, create a deployment profile in the Palo Alto Networks Customer Support Portal and associate it with a Tenant Service Group (TSG). The deployment profile defines how many vCPUs and instances you plan to use, and allows the system to allocate credits appropriately.- Log in to the Palo Alto Networks Customer Support Portal.Select Products Software/Cloud NGFW Credits.Locate your credit pool and click Create Deployment Profile. This lets you define how credits will be allocated for Prisma AIRS instances.Select AI Runtime Security (Instance) and click Next.
![]() Select PAN-OS 11.2.2 and above and click Next.PAN-OS is required for managing deployment compatibility and service integration.Enter the Prisma AIRS details:
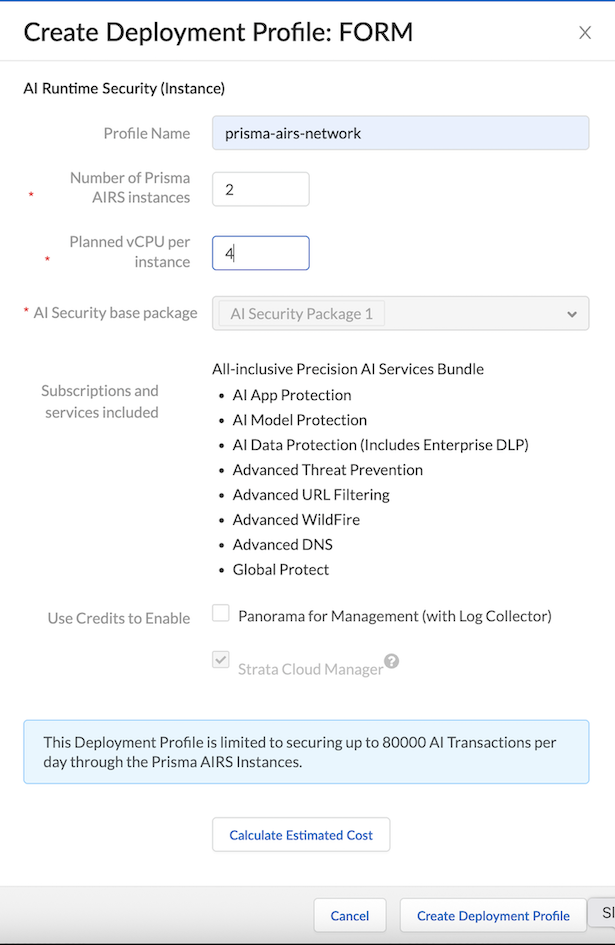
Select PAN-OS 11.2.2 and above and click Next.PAN-OS is required for managing deployment compatibility and service integration.Enter the Prisma AIRS details:- Deployment Profile Name.Number of Prisma AIRS instances.Planned vCPU per instances.Review the Prisma AIRS AI Runtime: Network intercept Setup Prerequisites and Limitations to validate your configuration.Optional Panorama for Management (with Log Collector) to create a deployment profile for Panorama maanged firewall.This step is only required for Panorama-managed deployments.Select Create Deployment Profile.The subscriptions and services used by Prisma AIRS AI Runtime: Network intercept are bundled and pre-configured. That is why, you cannot customize or modify them as part of this deployment.
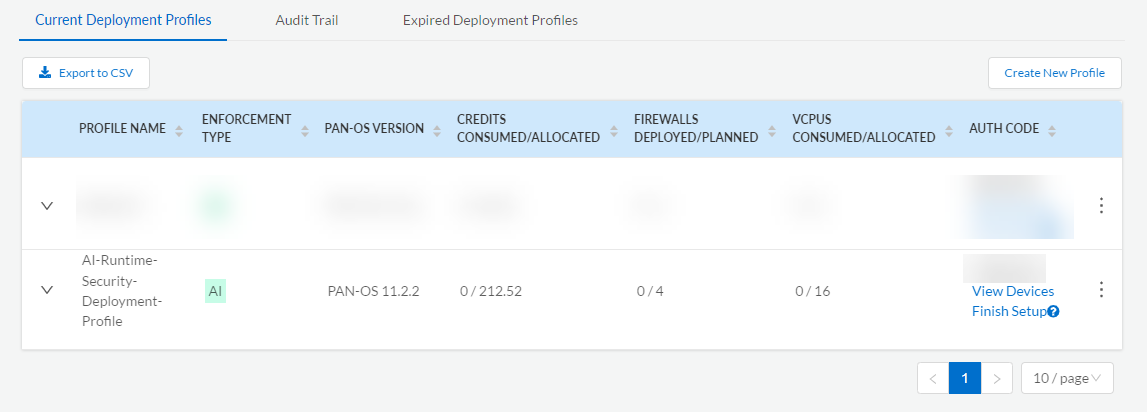
![]() You’ve now created and associated a deployment profile for Prisma AIRS AI Runtime: Network intercept. This enables you to allocate resources and begin securing AI network traffic across your selected tenant environment.Associate a Deployment Profile with a TSGAfter creating a deployment profile for Prisma AIRS, the next step is to associate it with a Tenant Service Group (TSG). This association links your deployment to a specific tenant environment and is required to activate thePrisma AIRS services.You must complete this step before onboarding cloud accounts or using runtime services.Log in to Palo Alto Networks Customer Support Portal.Select Products Software/Cloud NGFW Credits.Locate the credit pool you used to create the deployment profile and click Details.Locate the Prisma AIRS AI Runtime: Network intercept deployment profile and click Finish Setup.
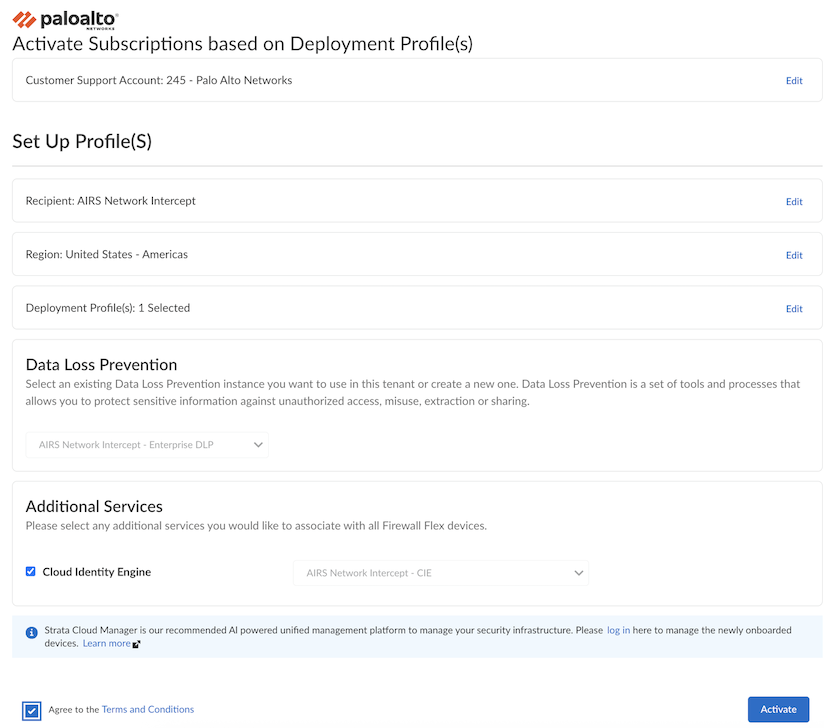
You’ve now created and associated a deployment profile for Prisma AIRS AI Runtime: Network intercept. This enables you to allocate resources and begin securing AI network traffic across your selected tenant environment.Associate a Deployment Profile with a TSGAfter creating a deployment profile for Prisma AIRS, the next step is to associate it with a Tenant Service Group (TSG). This association links your deployment to a specific tenant environment and is required to activate thePrisma AIRS services.You must complete this step before onboarding cloud accounts or using runtime services.Log in to Palo Alto Networks Customer Support Portal.Select Products Software/Cloud NGFW Credits.Locate the credit pool you used to create the deployment profile and click Details.Locate the Prisma AIRS AI Runtime: Network intercept deployment profile and click Finish Setup.![]() In the Activate Subscriptions based on Deployment Profile(s) form, select the following:Select the Customer Support Account used to create your deployment profile from the available list.Select Tenant.Verify that the Strata Logging Service is enabled for this tenant.Select a Region.In Select Deployment Profile, select the deployment profile you created previously.Click Done.Keep existing deployment profiles checked to maintain their association with the tenant.Enable Cloud Identity Engine or create a new one for centralized, cloud-based user identity management and enhanced security policy enforcement across your entire Palo Alto Networks deployment.Agree to the Terms and Conditions.Click Activate and record the Auth Code.
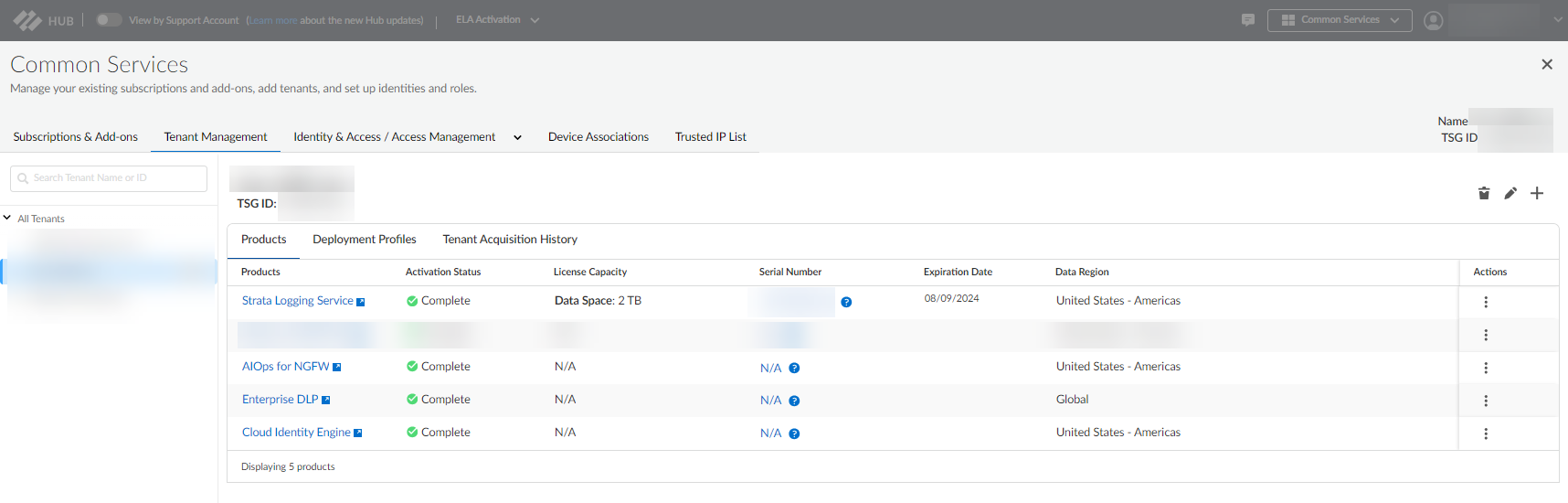
In the Activate Subscriptions based on Deployment Profile(s) form, select the following:Select the Customer Support Account used to create your deployment profile from the available list.Select Tenant.Verify that the Strata Logging Service is enabled for this tenant.Select a Region.In Select Deployment Profile, select the deployment profile you created previously.Click Done.Keep existing deployment profiles checked to maintain their association with the tenant.Enable Cloud Identity Engine or create a new one for centralized, cloud-based user identity management and enhanced security policy enforcement across your entire Palo Alto Networks deployment.Agree to the Terms and Conditions.Click Activate and record the Auth Code.![]() Verify that the TSG association succeeded by logging into the Hub, selecting Common Services → Tenant Management, and selecting your tenant.The initial association between the deployment profile and TSG may take up to 30 minutes.
Verify that the TSG association succeeded by logging into the Hub, selecting Common Services → Tenant Management, and selecting your tenant.The initial association between the deployment profile and TSG may take up to 30 minutes.![]() Make sure your Strata Logging Service license is active. If it has expired, renew it before onboarding a cloud account to avoid issues with onboarding or Terraform generation.After deployment, you can:Additional considerations:
Make sure your Strata Logging Service license is active. If it has expired, renew it before onboarding a cloud account to avoid issues with onboarding or Terraform generation.After deployment, you can:Additional considerations:- Ensure that your Strata Logging Service license is active. If it has expired, renew it before onboarding a cloud account. This will avoid issues with onboarding or Terraform generation.
- While CN-Series deployments do not support many CDSS subscriptions, Prisma AIRS supports all CDSS subscriptions. Refer to the CN-Series support table for more information.