CN-Series
Deploy the CN-Series Firewall as a Kubernetes Service on GKE
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
-
-
- Deployment Modes
- In-Cloud and On-Prem
-
-
-
Deploy the CN-Series Firewall as a Kubernetes Service on GKE
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Complete the following procedure to deploy
the CN-Series firewall as a Kubernetes Service on GKE platform:
- Set up your Kubernetes cluster.To create a cluster in GKE, do the following:
- Click the navigation menu, go to Kubernetes Engine, and then select clusters.
- Click Create.
- Select the GKE Standard as the cluster mode that you want to use, and then click Configure.
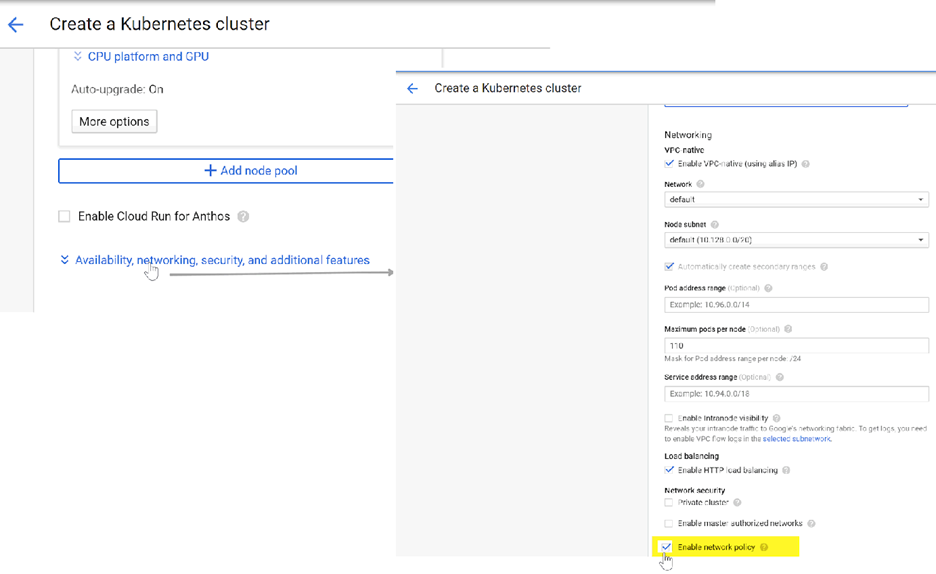
- Enter the cluster basic information including Name, Version, Location, Node subnet, and then click Create.If your cluster is on GKE, make sure to enable the Kubernetes Network Policy API to allow the cluster administrator to specify which pods are allowed to communicate with each other. This API is required for the CN-NGFW and CN-MGMT Pods to communicate.
![]()
- Verify that the cluster has adequate resources. The default GKE node pool
specification is not adequate for the CN-Series firewall. You must ensure that cluster
has the CN-Series Prerequisites resources to support the firewall:kubectl get nodeskubectl describe node <node-name>View the information under the Capacity heading in the command output to see the CPU and memory available on the specified node.The CPU, memory and disk storage allocation will depend on your needs. See CN-Series Performance and Scaling.Ensure you have the following information:
-
Collect the Endpoint IP address for setting up the API server on Panorama.Panorama uses this IP address to connect to your Kubernetes cluster.
-
Collect the template stack name, device group name, Panorama IP address, and optionally the Log Collector Group Name from Panorama.For more information, see Create a Parent Device group and template stack.
-
Collect the authorization code and auto-registration PIN ID and value.
-
The location of the container image repository to which you downloaded the images.
-
- (optional) If you configured a custom certificate
in the Kubernetes plugin for Panorama, you must create the cert
secret by executing the following command. Do not change the file
name from ca.crt. The volume for custom certificates in pan-cn-mgmt.yaml
and pan-cn-ngfw.yaml is optional.kubectl -n kube-system create secret generic custom-ca --from-file=ca.crt
- Edit the YAML files to provide the details required to
deploy the CN-Series firewalls.You must ensure that the value of PAN_PANORAMA_IP parameter on your YAML file matches with your actual Panorama IP address as shown in the diagram below:You must ensure that the parameter value of PAN_DEVICE_GROUP and PAN_TEMPLATE on your YAML file matches with the name of the device group and template stack that you created on Panorama as shown in the diagram below:You must ensure that the parameter value of PAN_PANORAMA_CG_NAME is same as the log collector name that you created.For more information, see Editable parameters in CN-Series deployment yaml files for details.
- If you are using autoscaling in your Kubernetes environment, see Enable Horizontal Pod scaling.
- Deploy the CN-NGFW service. Perform the following steps:
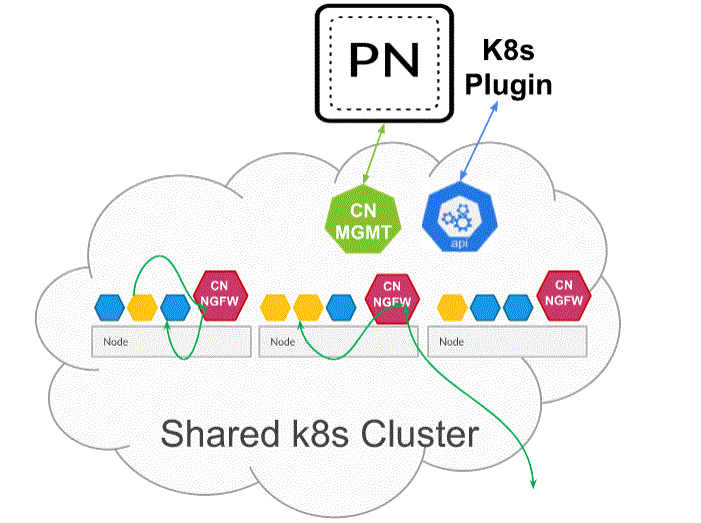
![]() When deployed as a Kubernetes Service, instances of the CN-NGFW can be deployed on security nodes and application pod traffic is redirected to an available CN-NGFW instance for inspection and enforcement.
When deployed as a Kubernetes Service, instances of the CN-NGFW can be deployed on security nodes and application pod traffic is redirected to an available CN-NGFW instance for inspection and enforcement.- Verify that you have created the service account using the pan-cni-serviceaccount.yaml.
- Use Kubectl to run the pan-cni-configmap.yaml.kubectl apply -f pan-cni-configmap.yaml
- Use kubectl to run the pan-cn-ngfw-svc.yaml.kubectl apply -f pan-cn-ngfw-svc.yamlThis yaml must be deployed before pan-cni.yaml.
- Use Kubectl to run the pan-cni.yaml.kubectl apply -f pan-cni.yaml
- Verify that you have modified the pan-cni-configmap and pan-cni YAML files.
- Run the following command and verify that your output
is similar to the following example.
![]()
- Deploy the CN-MGMT StatefulSet.By default, the management plane is deployed as a StatefulSet that provides fault tolerance. Up to 30 firewall CN-NGFW pods can connect to a CN-MGMT StatefulSet.
- (Required for statically provisioned
PVs only) Deploy the Persistent Volumes (PVs) for the CN-MGMT
StatefulSet.
- Create the directories to match the local volume names defined in the pan-cn-pv-local.yaml.You need six (6) directories on at least 2 worker nodes. Log in to each worker node on which the CN-MGMT StatefulSet will be deployed to create the directories. For example, to create directories named /mnt/pan-local1 to /mnt/pan-local6, use the command:
mkdir -p /mnt/pan-local1 /mnt/pan-local2 /mnt/pan-local3 /mnt/pan-local4 /mnt/pan-local5 /mnt/pan-local6
- Modify pan-cn-pv-local.yaml.Match the hostname under nodeaffinity, and verify that you have modified the directories you created above in spec.local.path then deploy the file to create a new storageclass pan-local-storage and local PVs.
- Verify that you have modified the pan-cn-mgmt-configmap and pan-cn-mgmt YAML
filesSample pan-cn-mgmt-configmap from EKS.apiVersion: v1 kind: ConfigMap metadata: name: pan-mgmt-config namespace: kube-system data: PAN_SERVICE_NAME: pan-mgmt-svc PAN_MGMT_SECRET: pan-mgmt-secret # Panorama settings PAN_PANORAMA_IP: "<panorama-IP>" PAN_DEVICE_GROUP: "<panorama-device-group>" PAN_TEMPLATE_STACK: "<panorama-template-stack>" PAN_CGNAME: "<panorama-collector-group>" # ctnr mode: "k8s-service", "k8s-ilbservice" PAN_CTNR_MODE_TYPE: "k8s-service" #Non-mandatory parameters # Recommended to have same name as the cluster name provided in Panorama Kubernetes plugin - helps with easier identification of pods if managing multiple clusters with same Panorama #CLUSTER_NAME: "<Cluster name>" #PAN_PANORAMA_IP2: "" # Comment out to use CERTs otherwise PSK for IPSec between pan-mgmt and pan-ngfw #IPSEC_CERT_BYPASS: "" # No values needed # Override auto-detect of jumbo-frame mode and force enable system-wide #PAN_JUMBO_FRAME_ENABLED: "true" # Start MGMT pod with GTP enabled. For complete functionality, need GTP # enable at Panorama as well. #PAN_GTP_ENABLED: "true" # Enable high feature capacities. These need high memory for MGMT pod and # higher/matching memory than specified below for NGFW pod. #PAN_NGFW_MEMORY="6Gi" #PAN_NGFW_MEMORY="40Gi" # For enabling faster datapath - AF_XDP, default is AF_PACKETV2. This requires kernel support. #PAN_DATA_MODE: "next-gen" #HPA params #PAN_CLOUD: "EKS" #PAN_NAMESPACE_EKS: "EKSNamespace" #PUSH_INTERVAL: "15" #time interval to publish metrics to AWS cloudwatchSample pan-cn-mgmt.yamlinitContainers: - name: pan-mgmt-init image: <your-private-registry-image-path>containers: - name: pan-mgmt image: <your-private-registry-image-path> terminationMessagePolicy: FallbackToLogsOnError
- Use Kubectl to run the yaml files.
kubectl apply -f pan-cn-mgmt-configmap.yamlkubectl apply -f pan-cn-mgmt-slot-crd.yamlkubectl apply -f pan-cn-mgmt-slot-cr.yamlkubectl apply -f pan-cn-mgmt-secret.yamlkubectl apply -f pan-cn-mgmt.yamlYou must run the pan-mgmt-serviceaccount.yaml, only if you had not previously completed the Create Service Account for Cluster Authentication.- Verify that the CN-MGMT pods are up by running the following command:
kubectl get pods -l app=pan-mgmt -n kube-systemIt takes about 5-6 minutes.- Deploy the CN-NGFW pods.
- Verify that you have modified the YAML files
as detailed in PAN-CN-NGFW-CONFIGMAP and PAN-CN-NGFW.containers: - name: pan-ngfw-container image: <your-private-registry-image-path>
- Use Kubectl apply to run the pan-cn-ngfw-configmap.yaml.kubectl apply -f pan-cn-ngfw-configmap.yaml
- Use Kubectl apply to run the pan-cn-ngfw.yaml.kubectl apply -f pan-cn-ngfw.yaml
- Verify that the CN-NGFW Pods are running. kubectl get pods -n kube-system -l app=pan-ngfw -o wide
- Enable horizontal pod autoscaling by performing the following steps:
- Deploy the Custom Metrics Stack Driver Adapter in your CN-Series cluster. The cluster name must be provided through a K8s secret.
- Download the GKE-specific HPA yaml files from the Palo Alto Networks GitHub repository.
- If your CN-MGMT is deployed in a custom namespace, update pan-cn-adapater.yaml with the custom namespace. The default namespace is kube-system.
- Update the HPA parameters in the GKE-specific pan-cn-mgmt-configmap.yaml.#PAN_CLOUD: "GKE"#HPA_NAME: "<name>" #unique name to identify hpa resource per namespace or per tenant#PUSH_INTERVAL: "15" #time interval to publish metrics to stackdriver
- Modify the pan-cn-hpa-dp.yaml and pan-cn-hpa-mp.yaml with the HPA_NAME (replace with the name) as updated in above pan-cn-mgmt-configmap.yaml file and update the metric based on which HPA should be triggered.
- Enter the minimum and maximum number of replicas.
- (Optional) Change the scale down and scale up frequency values to suit your deployment. If you do not change these values, the default values are used.
- (Optional) Change the threshold value for each metric you want to use for scaling. If you do not change these values, the default values are used.
- Save the changes.
- Deploy the HPA yaml files. The files must be deployed in the order described below.
- Use Kubectl to run the pan-cn-adapter.yamlkubectl apply -f pan-cn-adapter.yaml
- Use Kubectl to run the pan-cn-crole.yamlkubectl apply -f pan-cn-crole.yaml
- Use Kubectl to run the pan-cn-hpa-dp.yamlkubectl apply -f pan-cn-hpa-dp.yaml
- Use Kubectl to run the pan-cn-hpa-mp.yamlkubectl apply -f pan-cn-hpa-mp.yaml
- Verify your deployment.
- Use kubectl to verify that the custom metrics adapter pod in the custom metrics namespace.kubectl get pods -n custom-metrics
- Use kubectl to check for the HPA resource.kubectl get hpa -n kube-systemkubectl describe hpa <hpa-name> -n kube-system
For more information, see Enable Horizontal Pod Autoscaling on the CN-Series.- Verify that you can see CN-MGMT, CN-NGFW and the PAN-CNI on the Kubernetes cluster.
kubectl -n kube-system get pods- Annotate the application yaml or namespace so that the traffic from their new pods is redirected to the firewall.
You need to add the following annotation to redirect traffic to the CN-NGFW for inspection:
For example, for all new pods in the “default” namespace:annotations: paloaltonetworks.com/firewall: pan-fwkubectl annotate namespace default paloaltonetworks.com/firewall=pan-fwOn some platforms, the application pods can start when the pan-cni is not active in the CNI plugin chain. To avoid such scenarios, you must specify the volumes as shown here in the application pod YAML.volumes: - name: pan-cni-ready hostPath: path: /var/log/pan-appinfo/pan-cni-ready type: Directory- Deploy your application in the cluster.
- Modify the pan-cn-hpa-dp.yaml and pan-cn-hpa-mp.yaml with the HPA_NAME (replace with the name) as updated in above pan-cn-mgmt-configmap.yaml file and update the metric based on which HPA should be triggered.
- Use Kubectl to run the yaml files.
- (Required for statically provisioned
PVs only) Deploy the Persistent Volumes (PVs) for the CN-MGMT
StatefulSet.