Download PDF
GlobalProtect
Configure Split DNS
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
Configure Split DNS
Enable users to access applications or local resources by specifying exclusions or
inclusions and send DNS queries.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can now enable users to access applications or local resources by specifying
exclusions or inclusions and send DNS queries to a local DNS server using the physical
adapter on the endpoint. With Split DNS, you can configure which domains are resolved by
the VPN assigned DNS servers and which domains are resolved by the local DNS servers.
Configure Split DNS for GlobalProtect App on Windows and macOS Endpoints
Enable users to access applications or local resources by specifying exclusions or
inclusions and send DNS queries.
- Before you begin:
- Launch the Web Interface.Configure a GlobalProtect gatewayTo modify an existing gateway or add a new one:
- On Panorama, select NetworkGlobalProtectGateways<gateway-config>.
- On Strata Cloud Manager (Prisma Access), select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectSetupGlobalProtect AppTunnel Settings.
- On Strata Cloud Manager (NGFW), select ConfigurationNGFW and Prisma AccessConfiguration ScopeAll FirewallsDeviceGlobalProtectPortals and GatewaysGateways.
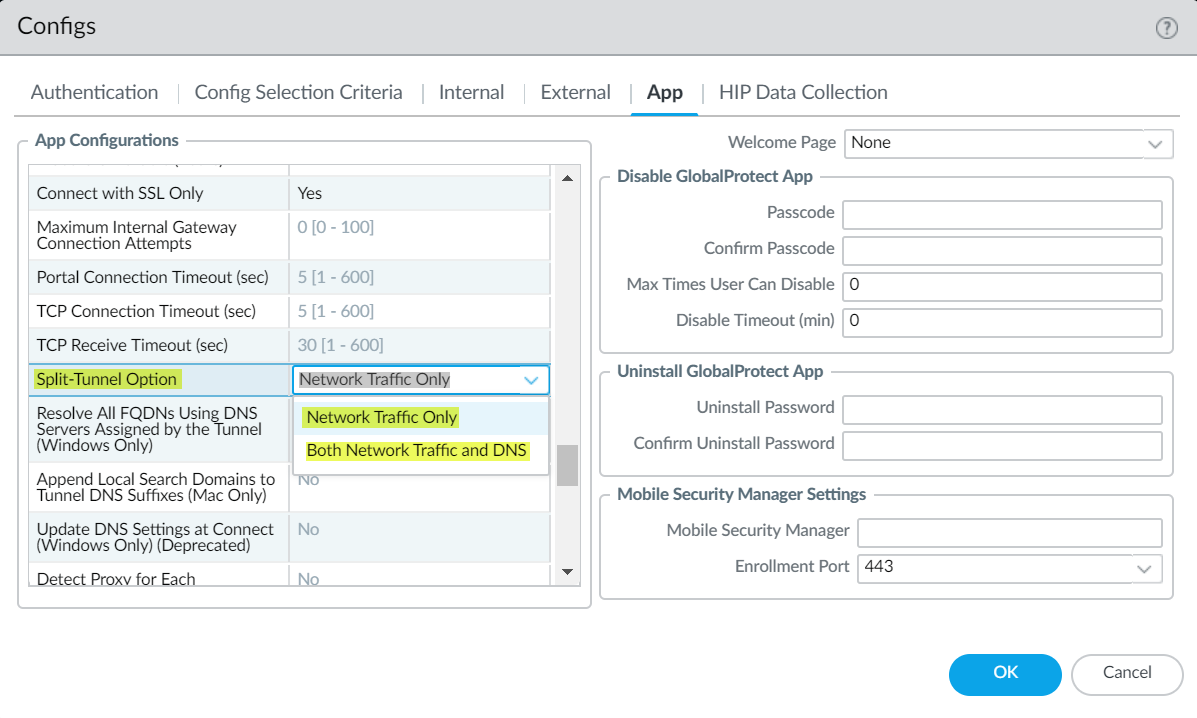
Configure a split tunnel based on the domain.Enable network traffic or both network traffic and DNS.You can enable split DNS to allow users to direct their DNS queries for applications and resources over the VPN tunnel or outside the VPN tunnel in addition to network traffic.- Select NetworkGlobalProtectPortals<portal-config> Agent<agent-config> AppSplit Tunnel Option.
- On Strata Cloud Manager (NGFW), select ConfigurationNGFW and Prisma AccessDeviceGlobalProtectPortals and GatewaysAgent SettingsAgent Tunnel Settings and then select Add Agent Tunnel SettingsSplit Tunneling.
- Select Network Traffic Only to include and exclude rules that are applied only to network application traffic and not to DNS traffic. All DNS traffic goes through the VPN tunnel irrespective of the split tunnel based on the destination domain that you specified for inclusions and exclusions. When you select Both Network Traffic and DNS the split tunnel based on the destination domain that you specified for inclusions and exclusions are applied to the DNS traffic and the associated network application traffic for that domain.
![]() Click OK twice.Commit the configuration.
Click OK twice.Commit the configuration.
Configure Split DNS for GlobalProtect App on iOS Endpoints
Configure Split DNS for GlobalProtect App on iOS EndpointsGlobalProtect now extends Split DNS-Include functionality to iOS platforms in addition to Linux, Windows, and macOS.Split-DNS -Exclude functionality is not supported on iOS platforms.With Split DNS, you can configure which domains are resolved by the GlobalProtect gateway assigned DNS servers and which domains are resolved by the local DNS servers. This is applicable when you have configured On-demand and Always-On connect method for the GlobalProtect app. If Per-App VPN configuration is set, only the network traffic and DNS traffic from the specific app that is configured will be routed through the tunnel.Split DNS will be applied regardless of connect method Always-On or On-demand. It will not be applied when you have configured Per-App using the MDM.Consider the following while configuring Split DNS functionality for iOS endpoints:- By default, all DNS is taken by the tunnel regardless of the Split-Tunnel Option app setting configured as Network Traffic Only or Both Network Traffic and DNS.
- For Windows and macOS endpoints, the corresponding traffic for DNS queries is automatically sent to the virtual adapter if it was initially sent there. Similarly, traffic for DNS queries sent to the physical adapter is sent to the physical adapter.
- For iOS and Android endpoints, IP Access Routes control which traffic is tunneled and Domain rules control which DNS queries are tunneled. If you want both DNS and traffic for the same site to be included or excluded in the VPN tunnel, you must configure separate IP and Domain rules accordingly.
- If you want to configure Split-DNS on iOS endpoints, you must:
- Add an IP Access Route (Include), so that GlobalProtect will no longer be the default route
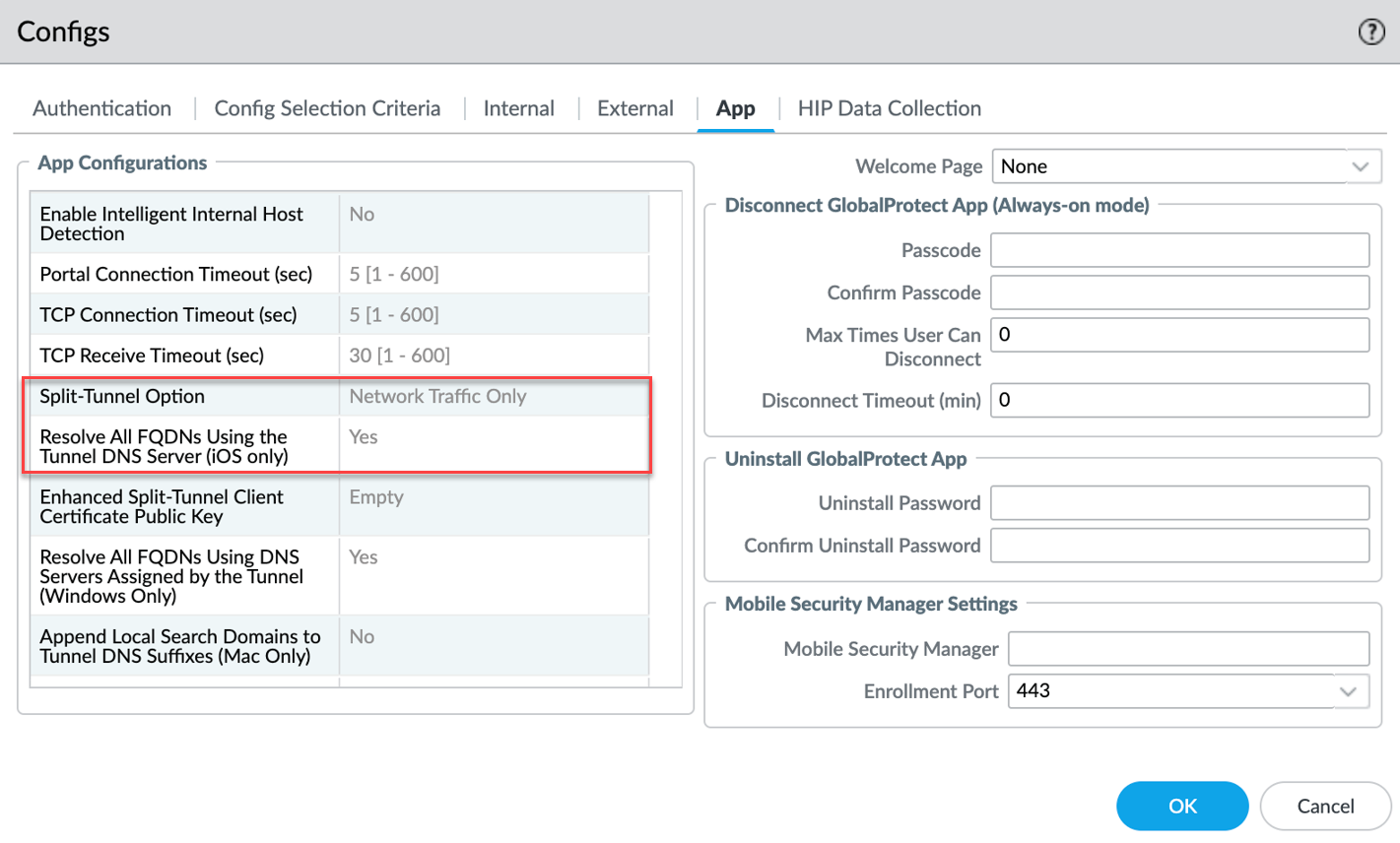
- You must set the Resolve all FQDNs using theTunnel DNS
Server option to No on the
app settings of the portal configurations. (Default value is
Yes.On Strata Cloud Manger (NGFW), select
- On Strata Cloud Manager (NGFW), select ConfigurationNGFW and Prisma AccessDeviceGlobalProtectPortals and GatewaysAgent SettingsAgent App SettingsApp ConfigurationShow Advanced Options and under DNS, select Resolve All FQDNS Using the Tunnel DNS Server (iOS only) .
- You must configure Domain include rules for any DNS traffic you want to be resolved by the tunnel DNS server.
- The setting of the Split-Tunnel Option on the app settings of the portal configurations has no impact on the splitting of DNS.
Use the following procedures to enable Split DNS functionality for iOS endpoint:- Ensure that the GlobalProtect portal is configured.To ensure that the GlobalProtect portal is configured, please confirm that the following default values of the app settings on the portal configurations are used:
- Split-Tunnel Option - Network Traffic Only
- Resolve All FQDNS Using the Tunnel DNS Server (iOS only) -Yes
![]() Ensure that the GlobalProtect gateway is configured.Configure split tunnel settings based on the DNS and Network Traffic for the GlobalProtect gateway. These settings are assigned to the virtual network adapter on the endpoint when the GlobalProtect app establishes a tunnel with the gateway.
Ensure that the GlobalProtect gateway is configured.Configure split tunnel settings based on the DNS and Network Traffic for the GlobalProtect gateway. These settings are assigned to the virtual network adapter on the endpoint when the GlobalProtect app establishes a tunnel with the gateway.- In the GlobalProtect Gateway Configuration dialog, select AgentClient Settings <client-setting-config> to select an existing client settings configuration or add a new one.If you are using Strata Cloud Manager, do one of the following:
- On Strata Cloud Manager (Prisma Access), select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessMobile Users ContainerGlobalProtectSetupGlobalProtect App. In the Tunnel Settings, select Default and specify spilt tunnel settings.
- On Strata Cloud Manager (NGFW), select ConfigurationNGFW and Prisma AccessDeviceGlobalProtectPortals and GatewaysAgent SettingsAgent Tunnel Settings and then select Add Agent Tunnel SettingsSplit Tunneling and specify split tunnel settings.
Add the access route and domain that you want to route to GlobalProtect through the VPN connection. You can add up to 200 entries to GlobalProtect Gateways the list. You can add certain traffic and DNS to be included to the tunnel by specifying the destination subnets or address object and destination domain.You can configure the split tunnel functionality for the GlobalProtect app on iOS endpoints to specify how the DNS and network traffic should be handled through the tunnel:- Only certain traffic and certain DNS to be tunneled by GlobalProtect
- Only certain traffic is included through the tunnel and exclude all DNS
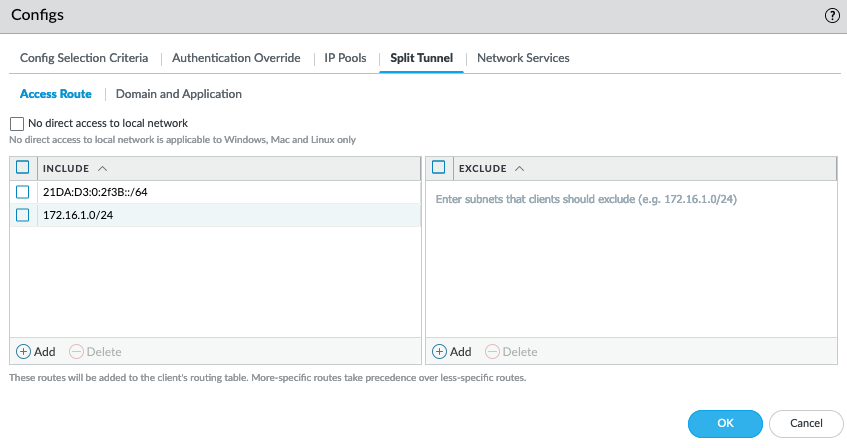
To include only certain traffic and certain DNS to be tunneled through the VPN connection- Configure the access route-based Split
Tunnel settings (Split TunnelAccess Route). In the Include area, add the destination subnets or address object (of type IP Netmask) to route only certain traffic destined for your LAN to GlobalProtect. You can include IPv6 or IPv4 subnets.
![]()
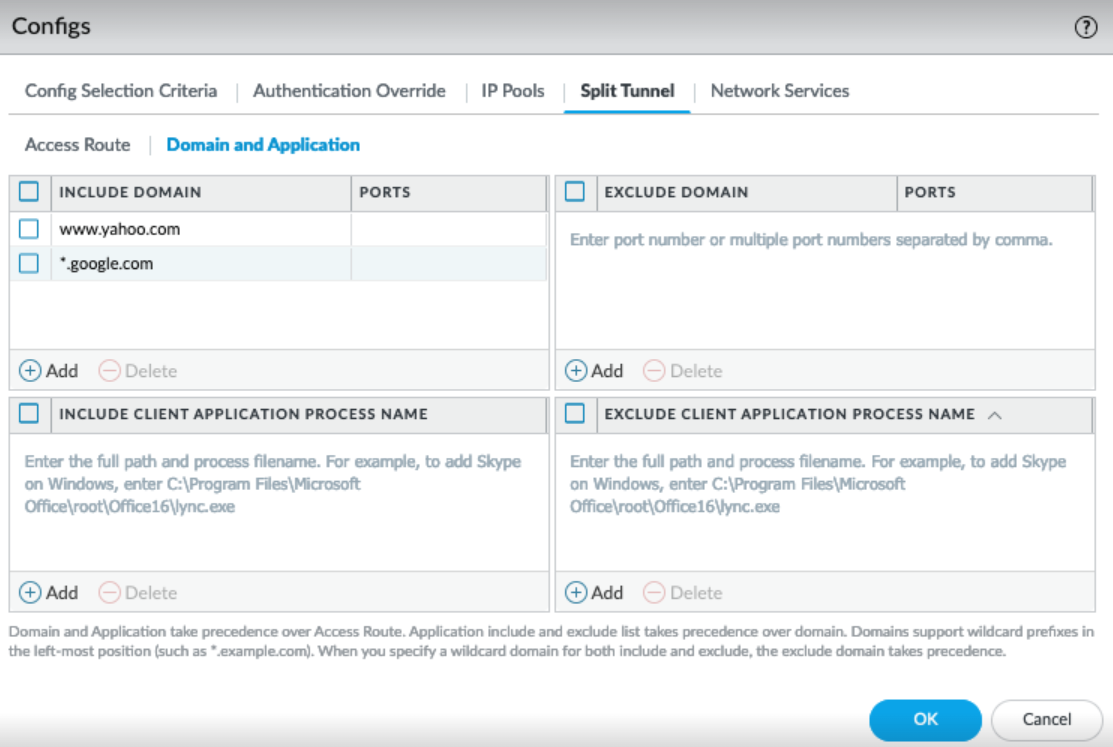
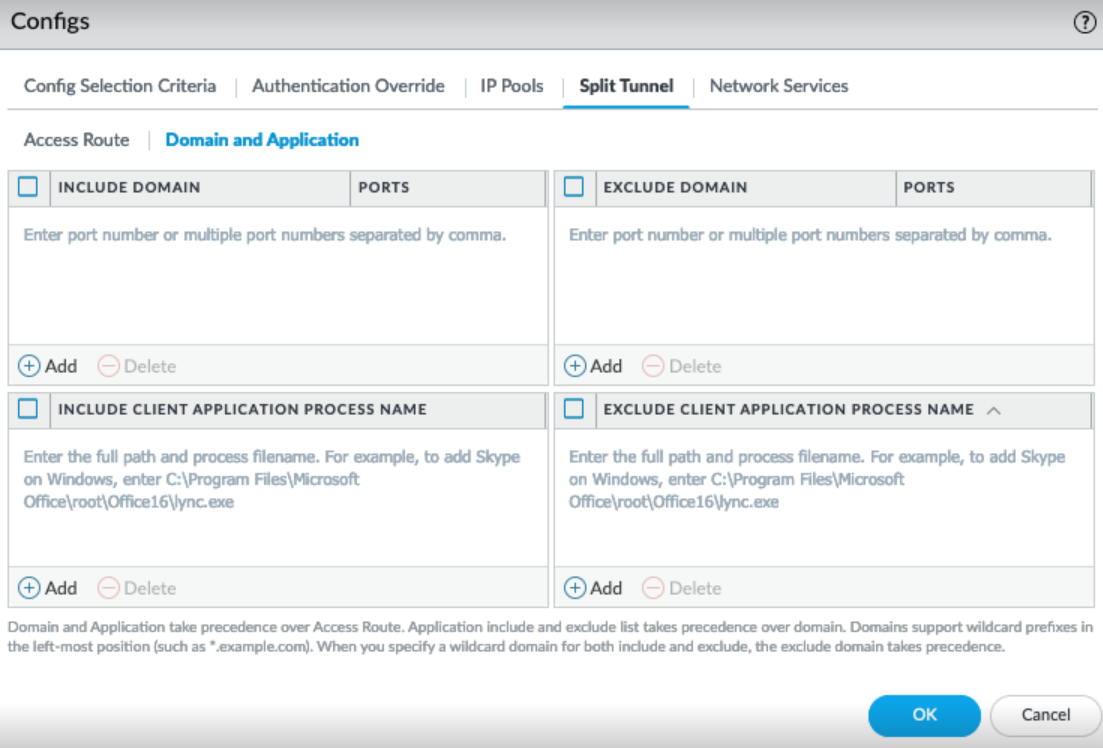
- Configure the domain-based Split Tunnel
settings (Split TunnelDomain and Application ).In the Include area, add the private domain and SaaS or public cloud applications whose DNS traffic you want to route to GlobalProtect through the VPN connection using the destination domain and port. These domain rules only apply to DNS queries and not traffic. You can add up to 200 entries to GlobalProtect Gateways the list. For example, add *.google.com to allow all Google DNS queries to go through the VPN tunnel. You can use a wildcard character (*) at the beginning of the domain name. You cannot use the wildcard character (*) in the middle or end of the domain name.
![]()
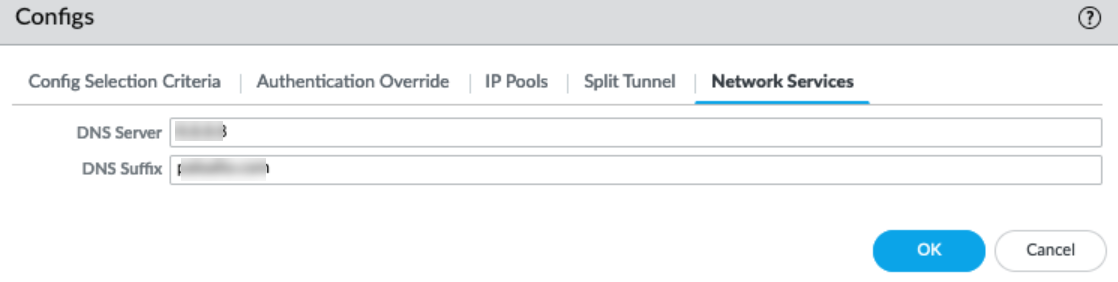
- Configure Tunnel DNS server.
- In the GlobalProtect Gateway Configuration dialog, select AgentClient Settings<client-setting-config>Network Services.
- Enter the DNS Server.
- (Optional)Enter the DNS Suffix.
- Click OK.
![]()
To include only certain traffic through tunnel and exclude all DNS- Configure the access route-based Split
Tunnel settings (Split TunnelAccess Route).In the Include area, add the destination subnets or address object (of type IP Netmask) to route only certain traffic destined for your LAN to GlobalProtect. You can include IPv6 or IPv4 subnets.
![]()
- To exclude all the DNS from going through the tunnel, leave the Include area empty (Split TunnelDomain and ApplicationInclude area). In this case, no DNS will be tunneled through the VPN connection
![]() Click OK and commit your changes.View the PanGPS.log to view the DNS Settings: For example,
Click OK and commit your changes.View the PanGPS.log to view the DNS Settings: For example,DNSSettings = { protocol = cleartext server = ( x.x.x.x, ) searchDomains = () matchDomains = ( paloaltonetworks.com, *.paloaltonetworks.com, ) matchDomainsNoSearch = YES } IPv4Settings = { configMethod = manual addresses = ( xxx.xx.xx.xx, ) subnetMasks = ( xxx.xxx.xxx.xxx, ) includedRoutes = ( { destinationAddress = 0.0.0.0 destinationSubnetMask = 0.0.0.0 }, { destinationAddress = x.x.x.x destinationSubnetMask = xxx.xxx.xxx.xxx }, ) excludedRoutes = ( { destinationAddress = xxx.xx.xx.xxx destinationSubnetMask = xxx.xxx.xxx.xxx }, ) overridePrimary = NO } IPv6Settings = { configMethod = manual addresses = ( fc00::4f, ) networkPrefixLengths = ( 128, ) includedRoutes = ( { destinationAddress = :: destinationNetworkPrefixLength = 0 }, { destinationAddress = :: destinationNetworkPrefixLength = 128 }, )Debug(13251): split-tunnel-option is network-traffic Debug(13262): Got split-tunnel-option-mobile is yessplit-tunnel-option can have the values network-traffic or network traffic and DNS and split-tunnel-option-mobile can have the value yes or no.