Device Security
Set up Aruba ClearPass for Integration
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Set up Aruba ClearPass for Integration
Set up Aruba ClearPass for integration with Device Security
through Cortex XSOAR.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
Note: These instructions are based on
Aruba ClearPass 6.9.0. They should remain valid with later versions
of ClearPass although it’s possible that some elements in the UI
might change in the future.
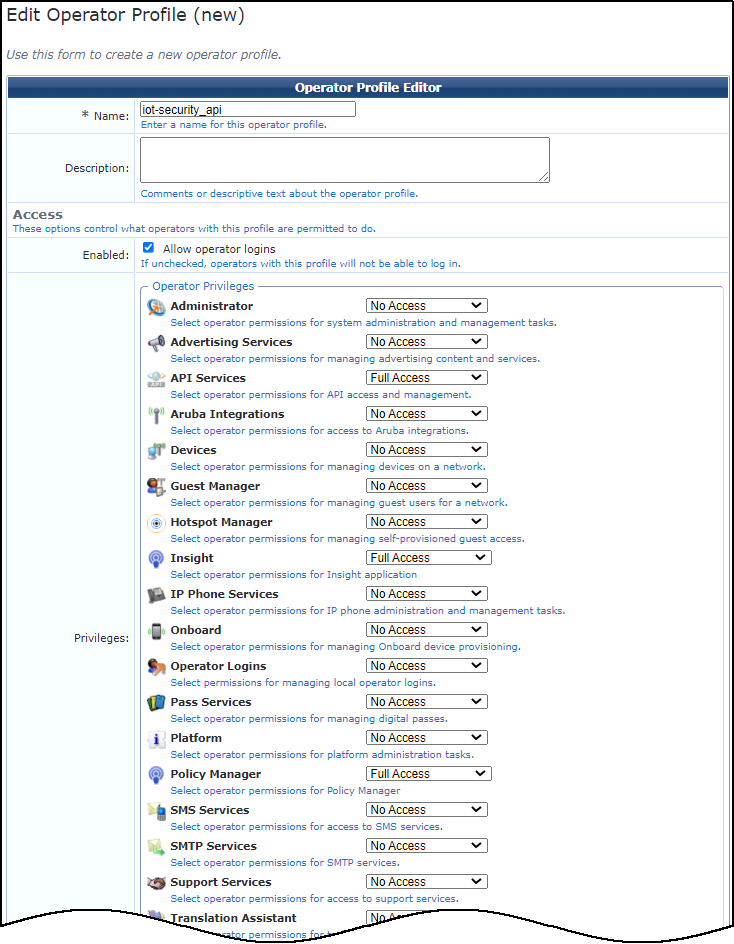
- Create an operator profile.You must use an operator profile that has full access to API services, ClearPass Insight, and ClearPass Policy Manager. If you already have such a profile, you can use that when configuring the RESTful API client. Otherwise, create a new profile as described here:
- Log in to ClearPass Guest, click AdministrationOperator LoginsProfilesCreate a new operator profile.
- Enter the following in the Operator Profile Editor that appears, leave the other settings at their default values, and then Save Changes:Name: Enter a name for the profile, such as iot-security_api.PrivilegesAPI Services: Full AccessInsight: Full AccessPolicy Manager: Full Access
![]()
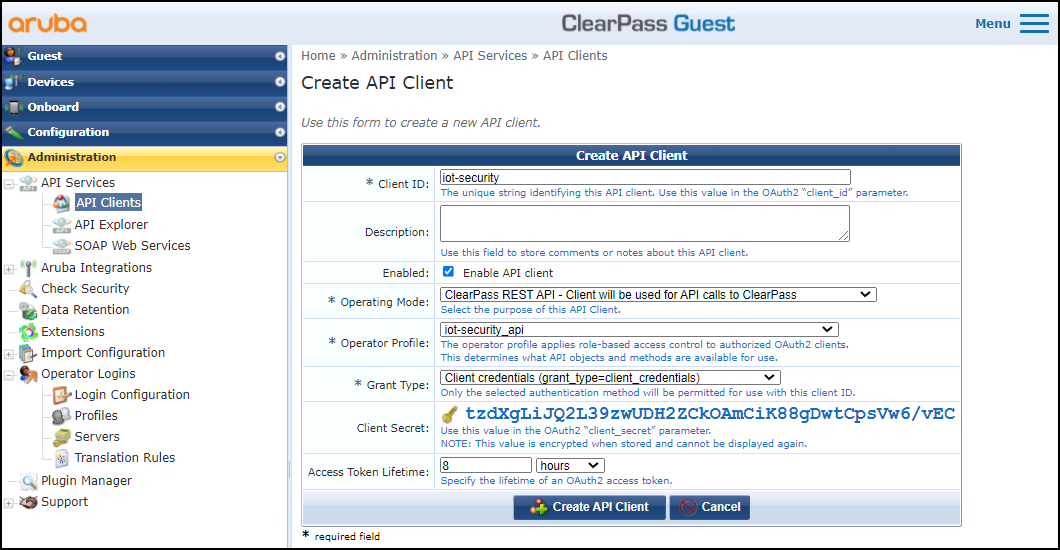
Add a RESTful API client.Define a client for the XSOAR engine to use when accessing the Aruba ClearPass API. There are two important settings that you must record so that you can enter them later when configuring an Aruba ClearPass instance on Cortex XSOAR: the client ID and client secret. The client uses the operator profile that you created in the previous step.- While still logged in to Aruba ClearPass Guest, click AdministrationAPI ServicesAPI ClientsCreate API Client.
- Enter the following in the Create API Client dialog box, leave the other settings at their default values, and then click Create API Client:Client ID: Enter a unique text string for the client ID. Note what it is so that you can enter it later when configuring the integration settings in Cortex XSOAR.Operator Profile: Choose the operator profile you configured in the previous section; for example, iot-security_api.Grant Type: Client credentials (grant_type=client_credentials)When you choose this, ClearPass Guest automatically generates a client secret and displays it. Record the client secret for later use when configuring Cortex XSOAR.
![]()
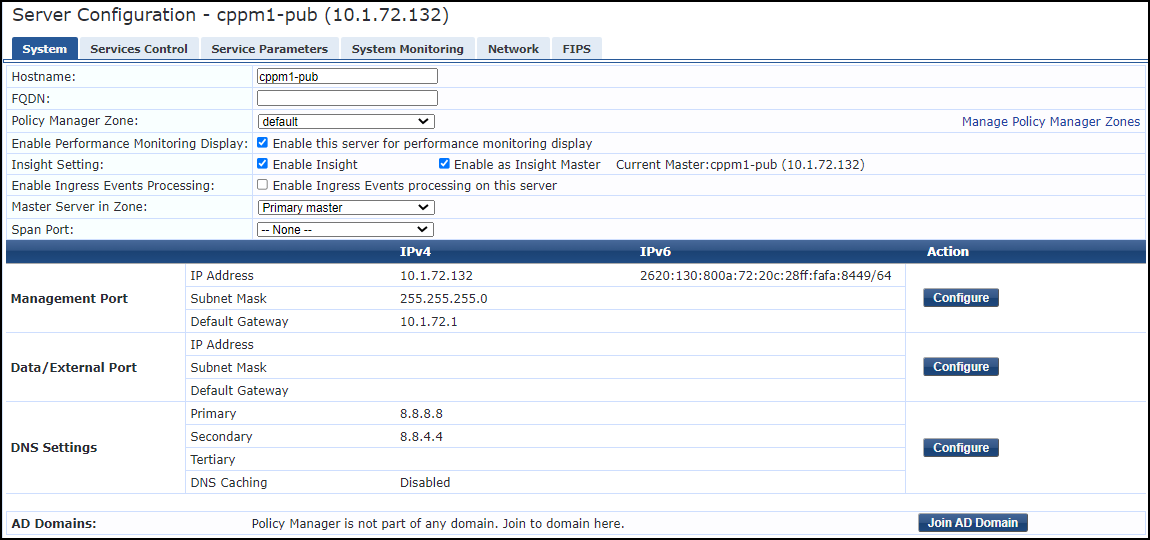
When Device Security connects through XSOAR to Aruba ClearPass, ClearPass automatically generates custom endpoint attribute names that IoT Security populates with the device data it learns. You don’t have to define these names in ClearPass; they are automatically created. The following list shows some of the default attribute names.Attribute Name Entity Data Type Comments PanwIoTProfile Endpoint String Device profile PanwIoTIP Endpoint String Device IP address PanwIoTCategory Endpoint String Category to which the device belongs PanwIoTRiskScore Endpoint String Risk score of the device PanwIoTConfidence Endpoint String Confidence score for device identification PanwIoTTag Endpoint String Asset tag, which Device Security learns from an integrated CMMS solution PanwIoTHostname Endpoint String Device hostname PanwIoTOS Endpoint String Operating system of the device PanwIoTModel Endpoint String Device model PanwIoTVendor Endpoint String Device vendor PanwIoTSerial Endpoint String Serial number of the device PanwIoTEPP Endpoint String Whether the device has endpoint protection PanwIoTInternetAccess Endpoint String Whether the device has Internet access PanwIoTAET Endpoint String Application entity title (if learned from X-ray machines, ultrasound machines, PACS servers, DICOM workstations, and DICOM viewers) If you want to use different names than those shown here, change the default attribute names in the Aruba ClearPass incremental and bulk export job settings in Cortex XSOAR. See Configure Device Security and Cortex XSOAR for Aruba ClearPass. When XSOAR next connects with ClearPass, ClearPass automatically generates the customized attribute names.Enable Insight.By enabling Insight, Device Security can enrich the device characteristics it learns from monitoring network traffic with data from ClearPass.- While logged in to ClearPass Policy Manager, click AdministrationServer ManagerServer Configuration, and then click your server name.
- On the System tab, select Enable Insight and Enable as Insight Master, leave the other settings as they are, and then Save.
![]()
Configure policies and profiles.Once Device Security and Aruba ClearPass are integrated, Device Security provides ClearPass with device profiles that you can then use to create security groups for defining network segments and access policies.- In ClearPass Policy Manager, click ConfigurationEnforcement and add policies to segment IoT devices into VLANs based on PanwIoTProfile attribute values.
- While in the same Enforcement section, add enforcement profiles to isolate and quarantine devices based on alert-triggered notifications.