Device Security
Set up Cisco ISE to Identify and Quarantine IoT Devices
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Set up Cisco ISE to Identify and Quarantine IoT Devices
Integrate Device Security through Cortex XSOAR with Cisco ISE to identify and quarantine IoT
devices.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
As an Device Security administrator, you can
selectively quarantine devices through Cisco ISE using PanwIoTAlertSeverity
and PanwIoTAlertType attributes. When you send ISE the quarantine
command, ISE quarantines impacted devices by applying policy rules
based on the alert severity, alert type, or both.
In addition
to configuring ISE to
identify IoT devices, configure the following on your Cisco
ISE system to quarantine IoT devices when there are security alerts:
- Add these custom endpoint attributes for Device Security alerts: PanwIoTAlertSeverity and PanwIoTAlertType
- Create authorization profiles
- Create exception rules
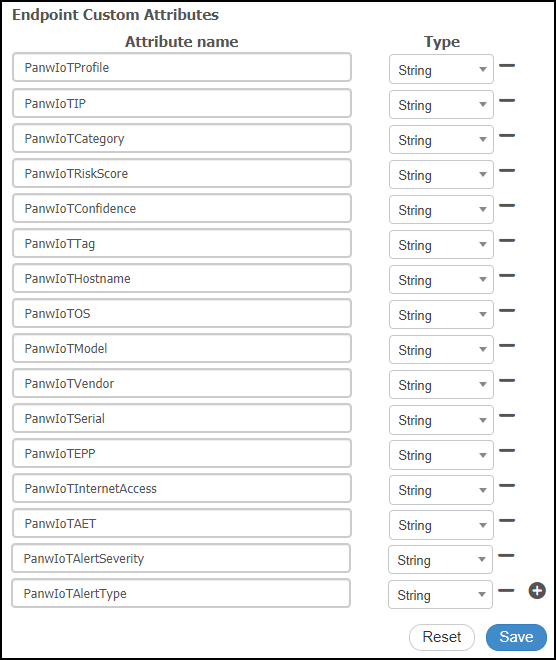
- Add Device Security endpoint attributes for alert severity and type.
- Click AdministrationIdentity ManagementSettingsEndpoint Custom Attributes.
- Click the Add icon ( + ), enter PanwIoTAlertSeverity in the Attribute name field, and then choose String from the Type drop-down list.
- Click the Add icon ( + ), enter PanwIoTAlertType in the Attribute name field, choose String from the Type drop-down list, and then Save the configuration.This is a possible set of attributes:PanwIoTProfile, PanwIoTIP, PanwIoTCategory, PanwIoTRiskScore, PanwIoTConfidence, PanwIoTTag, PanwIoTHostname, PanwIoTOS, PanwIoTModel, PanwIoTVendor, PanwIoTSerial, PanwIoTEPP, PanwIoTInternetAccess, PanwIoTAET, PanwIoTAlertSeverity, PanwIoTAlertType
![]()
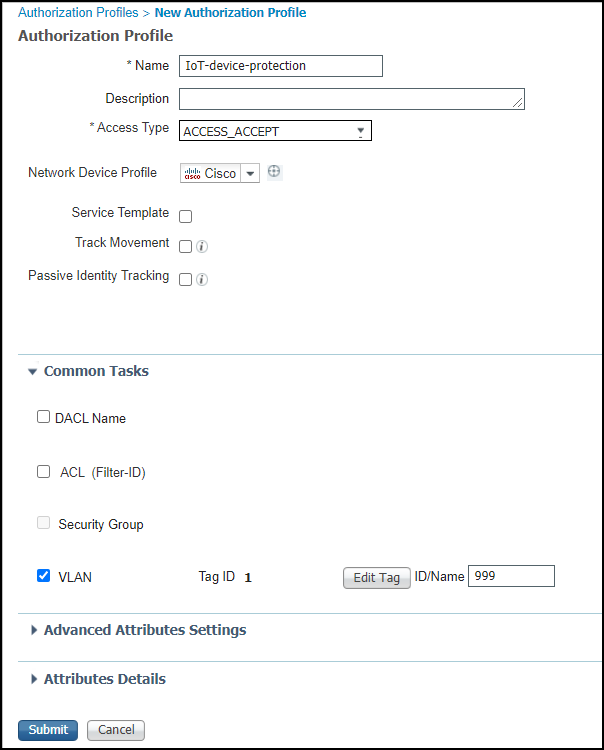
Create an authorization profile that allows IoT devices to access the network and associates them with the quarantine VLAN.- Click PolicyPolicy ElementsResultsAuthorizationAuthorization Profiles and then click Add.
- Enter settings like those described below, leave the other settings at their default values:Name: Enter a name for the profile; for example: IoT-device-protectionAccess Type: ACCESS_ACCEPTVLAN: (select); Tag ID: 1; ID/Name: 999, where 999 is the ID number of the quarantine VLAN.
![]()
- Submit the settings.
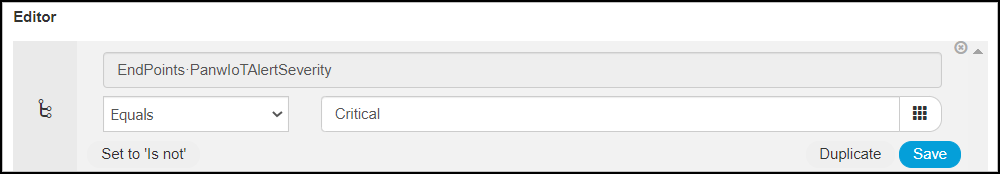
Create a condition for applying an exception rule, such as applying it when the severity is critical.- Click PolicyPolicy ElementsConditionsLibrary Conditions and then enter the following in Editor:Click to add an attribute: EndpointsPanwIoTAlertSeverityOperator: EqualsAttribute value: Critical
![]()
- Save the configuration.
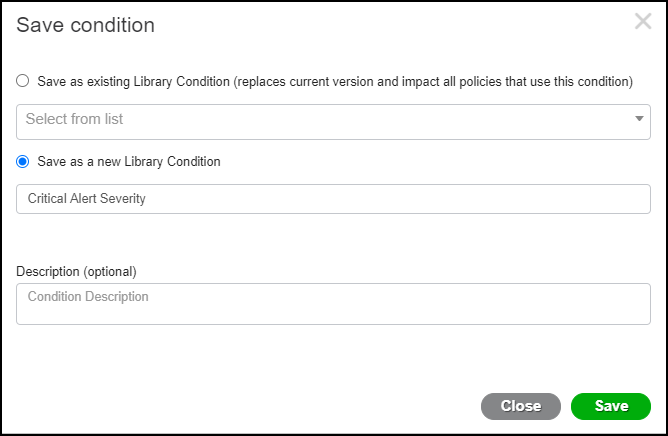
- In the Save condition dialog box, select Save as a new Library Condition, enter a name such as Critical Alert Severity in the Condition Name field, and then click Save.
![]()
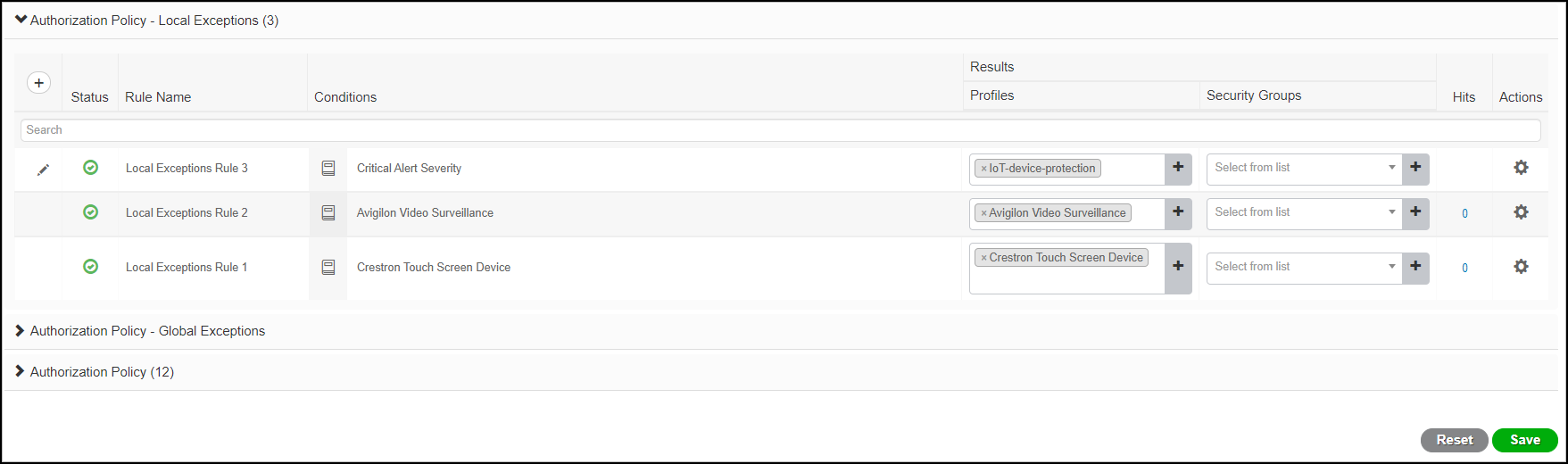
Create authorization policy exception rule that assigns devices with critical alerts to the quarantine VLAN.- Click PolicyPolicy Sets and then click the Arrow icon ( > ) to modify your existing policy set.
- Expand Authorization Policy - Local Exceptions, click the Plus icon ( + ) to add an exception rule, and then click the Plus icon ( + ) to add a condition.
- Click-drag Critical Alert Severity from the Library into the Editor and then click Use.
- In Results-Profiles, choose IoT-device-protection, which is the authorization profile you created for this condition.
![]()
- Save the configuration.When you quarantine a device in the Device Security portal, it sends the two alert attributes (PanwIoTAlertType and PanwIoTAlertSeverity) for that device (identified by its MAC address) through XSOAR to ISE. The next time that device connects to the network and requests access from Cisco ISE, the two alert attributes will match this exception rule and assign it to the quarantine VLAN.The device remains in quarantine while you investigate the cause of the alert. Once it’s resolved, you then release it from quarantine, which clears the alert attributes. When the device connects to the network and again requests access from Cisco ISE, ISE reassigns it to its usual VLAN.