Next-Generation Firewall
Disable the SIP Application-level Gateway (ALG)
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Disable the SIP Application-level Gateway (ALG)
SIP ALG creates dynamic NAT pinholes but may interfere with VoIP applications that
have NAT traversal capabilities, causing communication failures; possibly necessitating
disablement.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
This is a core Network Security feature for NGFWs and Prisma
Access; no prerequisites needed.
|
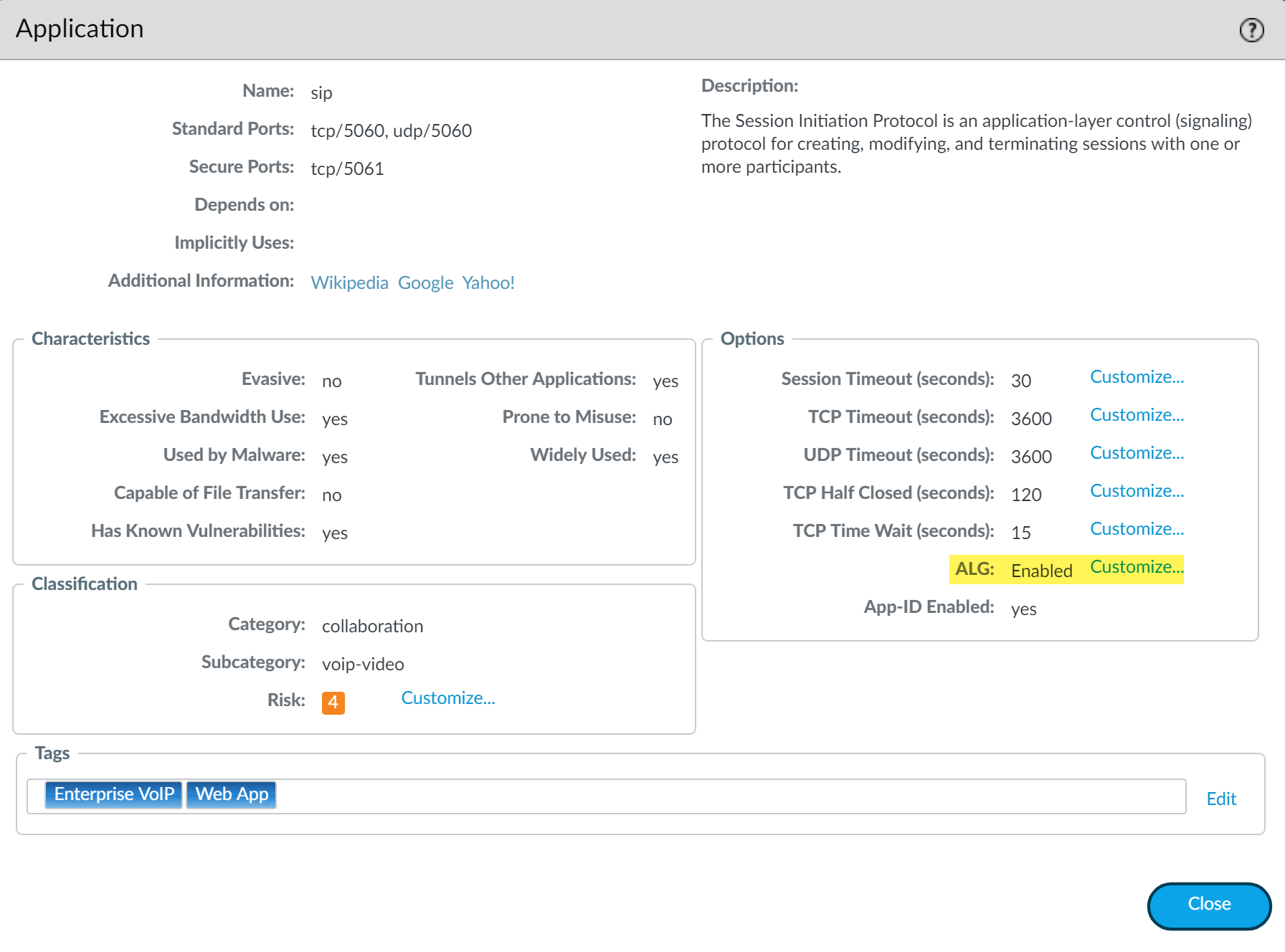
The Palo Alto Networks firewall uses the Session
Initiation Protocol (SIP) application-level gateway (ALG) to open
dynamic pinholes in the firewall where NAT is enabled. However,
some applications—such as VoIP—have NAT intelligence embedded in
the client application. In these cases, the SIP ALG on the firewall can
interfere with the signaling sessions and cause the client application
to stop working.
One solution to this problem is to define
an Application Override Policy for SIP, but using this approach disables
the App-ID and threat detection functionality. A better approach
is to disable the SIP ALG, which does not disable App-ID or threat
detection.
You can disable only the following App-IDs: sccp, sip,
teredo, and unistim.
The following procedure describes how to disable
the SIP ALG.
- Select ObjectsApplications.Select the sip application.You can type sip in the Search box to help find the sip application.Select Customize... for ALG in the Options section of the Application dialog box.
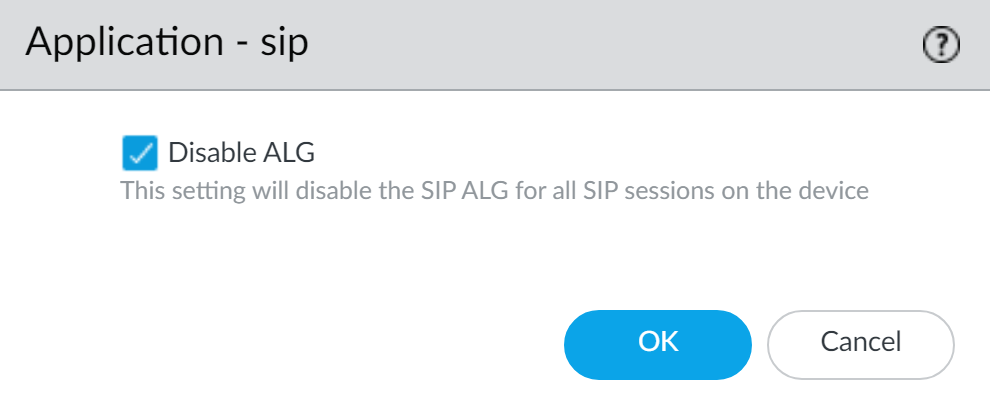
![]() Select the Disable ALG check box in the Application - sip dialog box and click OK.
Select the Disable ALG check box in the Application - sip dialog box and click OK.![]() Close the Application dialog box and Commit the change.
Close the Application dialog box and Commit the change.