Next-Generation Firewall
Take an Application Packet Capture
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Take an Application Packet Capture
You can automatically generate packet captures for network traffic it cannot
identify, as well as allowing administrators to configure custom packet captures for
specific applications.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To configure the firewall for application packet captures, you have two primary
methods:
- Take a Packet Capture for Unknown Applications
- Take a Custom Application Packet Capture
Take a Packet Capture for Unknown Applications
Palo Alto Networks firewalls automatically generate a packet capture for sessions
that contain an application that the firewall cannot identify. Typically, the
only applications that are classified as unknown traffic—tcp, udp, or
non-syn-tcp—are commercially available applications that do not yet have App-ID
signatures, are internal or custom applications on your network, or potential
threats. You can use these packet captures to gather more context related to the
unknown application or use the information to analyze the traffic for potential
threats. You can also Manage Custom or Unknown Applications by controlling
them through security policy or by writing a custom application signature and
then creating a security rule based on the custom signature. If the application
is a commercial application, you can submit the packet capture to Palo Alto
Networks to have an App-ID signature created.
- Verify that unknown application packet capture is enabled (this option is enabled by default).
- To view the unknown application capture setting, run the following CLI command:
admin@PA-220>show running application setting | match “Unknown capture”If the unknown capture setting option is off, enable it:admin@PA-220>set application dump-unknown yesLocate unknown TCP and UDP applications by filtering the traffic logs.- Select MonitorLogsTraffic.Click Add Filter, create the unknown TCP portion of the filter (Connector = “and”, Attribute = “Application”, Operator = “equal”, and enter “unknown-tcp” as the Value), and then click Add to add the query to the filter.
![]() Create the unknown UDP portion of the filter (Connector = “or”, Attribute = “Application”, Operator = “equal”, and enter “unknown-udp” as the Value), and then click Add to add the query to the filter.
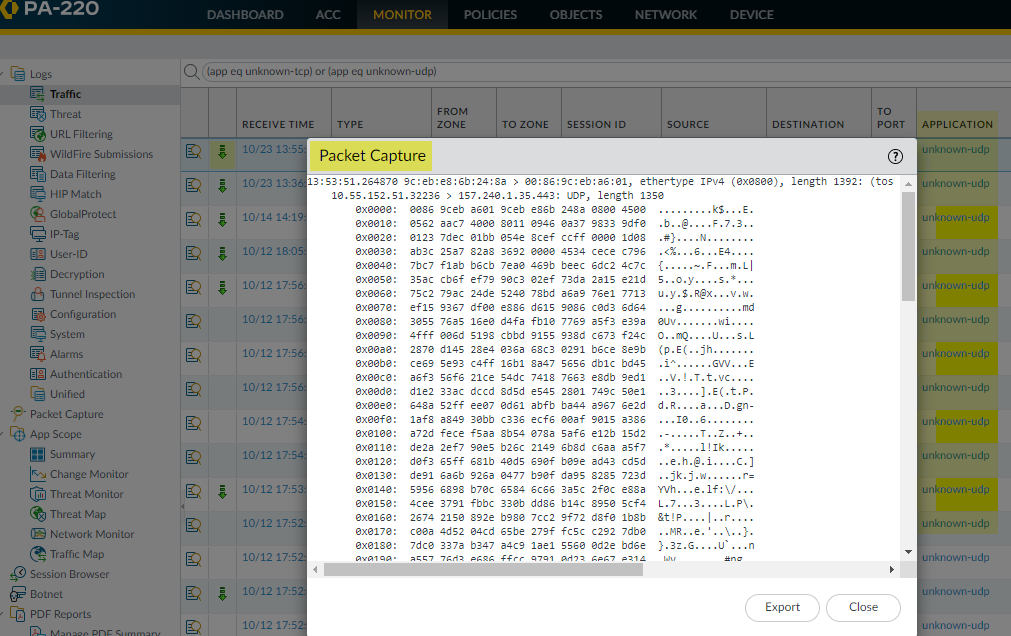
Create the unknown UDP portion of the filter (Connector = “or”, Attribute = “Application”, Operator = “equal”, and enter “unknown-udp” as the Value), and then click Add to add the query to the filter.![]() Click Apply to place the filter in the log screen query field.Click the Apply Filter arrow next to the query field to run the filter and then click the packet capture iconto view the packet capture or Export it to your local system.
Click Apply to place the filter in the log screen query field.Click the Apply Filter arrow next to the query field to run the filter and then click the packet capture iconto view the packet capture or Export it to your local system.![]()
![]()
Take a Custom Application Packet Capture
You can configure a Palo Alto Networks firewall to take a packet capture based on an application name and filters that you define. You can then use the packet capture to troubleshoot issues with controlling an application. When configuring an application packet capture, you must use the application name defined in the App-ID database. You can view a list of all App-ID applications using Applipedia or from the web interface on the firewall in ObjectsApplications.- Using a terminal emulation application, such as PuTTY, launch an SSH session to the firewall.Turn on the application packet capture and define filters.
admin@PA-220>set application dump on application <application-name> rule <rule-name>For example, to capture packets for the linkedin-base application that matches the security rule named Social Networking Apps, run the following CLI command:admin@PA-220>set application dump on application linkedin-base rule "Social Networking Apps"You can also apply other filters, such as source IP address and destination IP address.View the packet capture output to ensure that the correct filters are applied. The output displays after you enable the packet capture.The following output confirms that application capture filtering is now based on the linkedin-base application for traffic that matches the Social Networking Apps rule.![]() Access linkedin.com from a web browser and perform some LinkedIn tasks to generate LinkedIn traffic, and then run the following CLI command to turn off application packet capture:
Access linkedin.com from a web browser and perform some LinkedIn tasks to generate LinkedIn traffic, and then run the following CLI command to turn off application packet capture:admin@PA-220>set application dump offView/export the packet capture.- Log in to the web interface on the firewall and select MonitorLogsTraffic.In the log entry that you are interested in, click the green packet capture icon.
![]() View the packet capture directly or Export it to your computer. The following screen capture shows the linkedin-base packet capture.
View the packet capture directly or Export it to your computer. The following screen capture shows the linkedin-base packet capture.![]()