Next-Generation Firewall
Strata Cloud Manager
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Strata Cloud Manager
Configure an NGFW cluster of two PA-7500 Series firewalls using Strata Cloud
Manager.
Use this process to configure an NGFW Cluster of up to two PA-7500 Series firewalls
using Strata Cloud Manager.
- Select ConfigurationNGFW and Prisma Access.For the Configuration Scope, select a folder.Create an NGFW cluster.
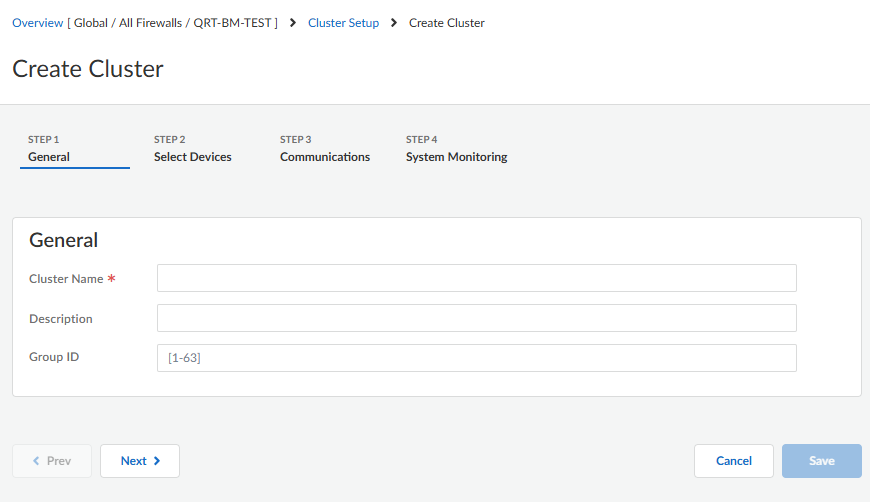
- Select Overview and in the Cluster Setup pane, select the gear icon or click on the number of clusters already configured.Select Clusters and Add Cluster.On the General tab, enter the Cluster Name containing zero or more alphanumeric characters, underscores (_), hyphens (-), dots (.), or spaces.(Optional) Enter the Group ID (in the range 1 to 63; the default is 1).
![]() Add devices to the cluster.
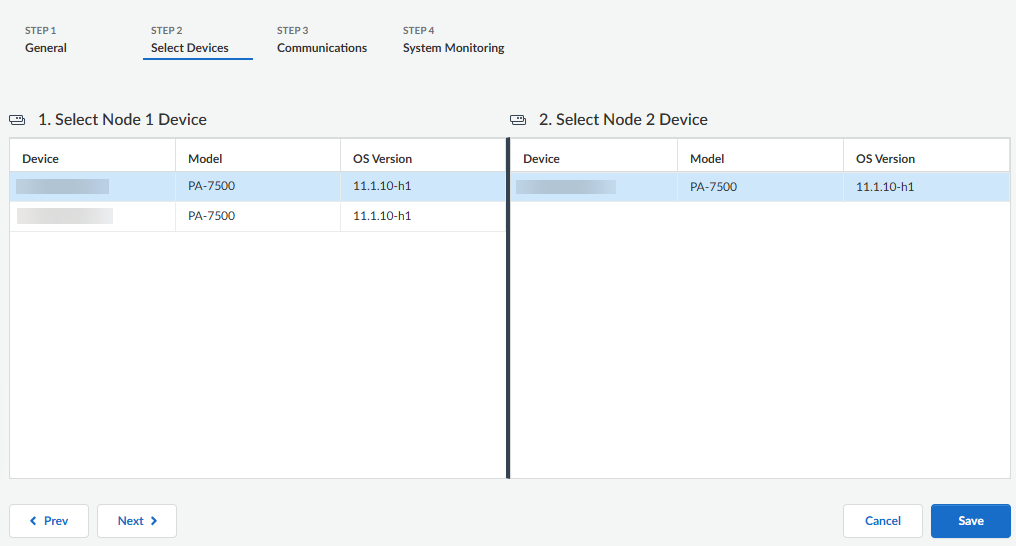
Add devices to the cluster.- On the Select Devices tab, select the Node 1 Device (a PA-7500 Series firewall to assign to the cluster).Select the Node 2 Device (the second PA-7500 Series firewall to assign to the cluster).
![]() Configure the HSCI-A and HSCI-B links.
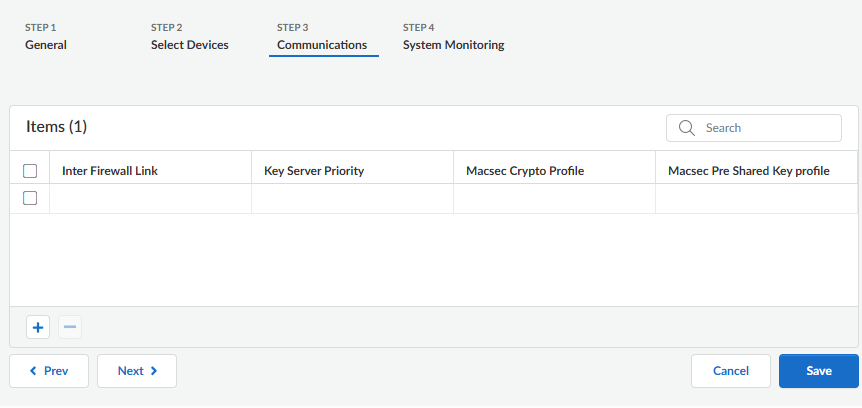
Configure the HSCI-A and HSCI-B links.- On the Communications tab, select the + and add an Inter Firewall Link by selecting hsci-a.Enter the Key Server Priority in the range 1 to 255.Select a MACsec Crypto Profile to apply to the link.Select a MACsec Pre Shared Key Profile to apply to the link.Repeat this step to configure the hsci-b link.
![]() Configure system monitoring for the NGFW cluster.
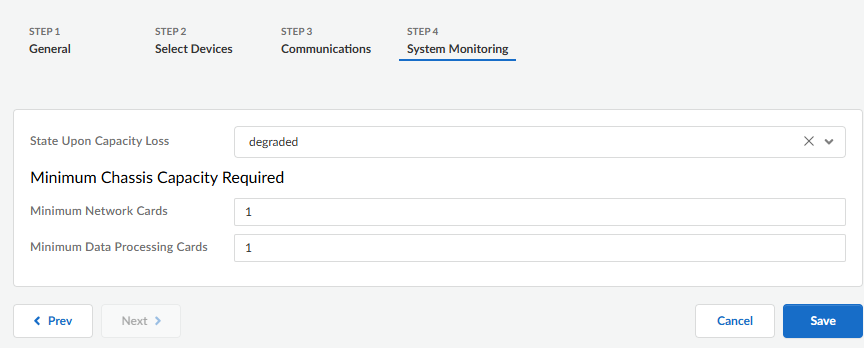
Configure system monitoring for the NGFW cluster.- On the System Monitoring tab, select the State Upon Capacity Loss: degraded or failed.Enter the Minimum Network Cards required; range is 1 to 7; default is 1.Enter the Minimum Data Processing Cards required; range is 1 to 7; default is 1.Save the configuration.
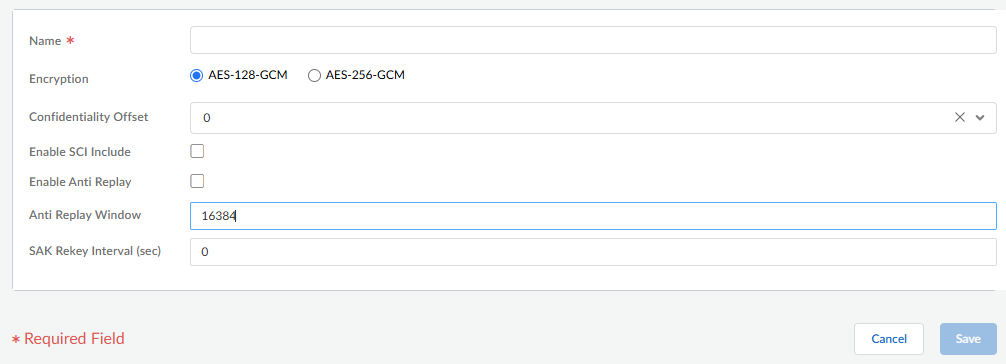
![]() Create a MACsec policy to apply to the HSCI ports.
Create a MACsec policy to apply to the HSCI ports.- On the MACsec Profiles tab, Add MACsec Policy.Enter a Name for the profile, which contains zero or more alphanumeric characters, underscores (_), hyphens (-), or dots (.). The name is a maximum of 31 characters.Select the Encryption type: AES-128-GCM (default) or AES-256-GCM.Select the Confidentiality Offset to specify a number of bytes (starting from the frame header), after which MACsec encrypts the bytes in a frame. The value is 0 (default), 30, or 50.Enable SCI Include to include the Secure Channel Identifier (SCI) tag in the Security Tag field of the MACsec header. The default is disabled.Enable Anti Replay to enable replay protection. This allows a MACsec port to accept frames out of order if they are within the Anti Replay Window. The default is disabled.Enter the Anti Replay Window size in the range 0 to 65,535; the default is 16,384. This value determines the range of packet numbers that the port will accept, for packets that might be out of order. The port will accept packets with a packet number greater than or equal to the last packet number minus the window size. For example, after the port receives packet number 12, if the window is 5, the port will subsequently accept only packets numbered 7 or higher.Specify an Anti Replay window size based on the traffic rate because the HSCI ports will likely experience packets arriving out of order due to prioritization or load balancing in the network.Enter the SAK Rekey Interval (sec) in seconds; range is 60 to 86,400; default is 3,600. Connectivity Association participants negotiate a Secure Association agreement, which includes a cipher suite and keys. A Key Server generates a Secure Association Key (SAK) from the Connectivity Association Key (CAK); the SAK is refreshed at the SAK rekey interval. The end-to-end nodes use the SAK to encrypt traffic for a given session. To avoid the SAKs of all interfaces being refreshed at the same time, MACsec might spread the rekeying actions evenly by subtracting a small random number from the SAK rekey interval.
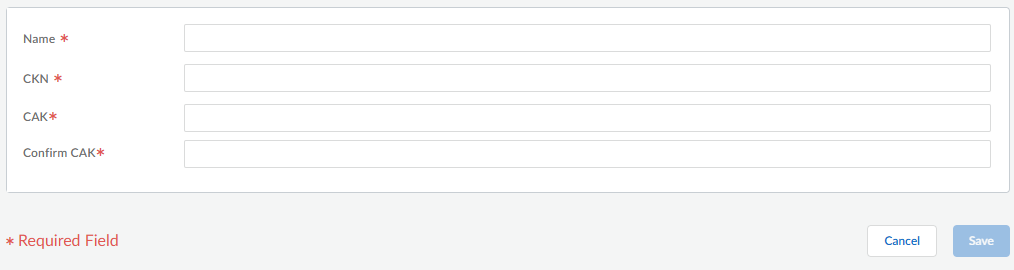
![]() Create a MACsec pre-shared key profile.
Create a MACsec pre-shared key profile.- On the MACsec Profiles tab, Add Pre Shared Key.Enter a Name for the pre shared key profile, which contains zero or more alphanumeric characters, underscores (_), hyphens (-), dots (.), or spaces. The name is a maximum of 31 characters.Enter the CKN (Connectivity Association Key Name) that identifies the Connectivity Association Key. The CKN is 1 byte to 32 bytes of hexadecimal string (2 to 64 hex digits) with an even number of digits; for example, 1234.Enter the CAK (Connectivity Association Key), which is a 16-byte hexadecimal string (32 hex digits) for AES-128-GCM, or a 32-byte hexadecimal string (64 hex digits) for AES-256-GCM. The CAK is used to generate all other keys used for MACsec. An example CAK for AES-128-GCM is 12345678912345678912345678912345. A CAK for AES-256-GCM is twice as long as a CAK for AES-128-GCM.Confirm CAK.Save the profiles.
![]()