Configure the PAN-OS Integrated User-ID Agent as a Syslog Listener
Table of Contents
End-of-Life (EoL)
Configure the PAN-OS Integrated User-ID Agent as a Syslog Listener
To configure the PAN-OS Integrated User-ID
agent to create new user mappings and remove outdated mappings through
syslog monitoring, start by defining Syslog Parse profiles. The
User-ID agent uses the profiles to find login and logout events
in syslog messages. In environments where syslog senders (the
network services that authenticate users) deliver syslog messages
in different formats, configure a profile for each syslog format.
Syslog messages must meet certain criteria for a User-ID agent to
parse them (see Syslog).
This procedure uses examples with the following formats:
- Login events—[Tue Jul 5 13:15:04 2016 CDT] Administratorauthentication success User:johndoe1 Source:192.168.3.212
- Logout events—[Tue Jul 5 13:18:05 2016CDT] User logout successful User:johndoe1 Source:192.168.3.212
After
configuring the Syslog Parse profiles, you specify syslog senders
for the User-ID agent to monitor.
- Determine whether there is a predefined Syslog Parse profile for your particular syslog senders.Palo Alto Networks provides several predefined profiles through Application content updates. The predefined profiles are global to the firewall, whereas custom profiles apply to a single virtual system only.Any new Syslog Parse profiles in a given content release is documented in the corresponding release note along with the specific regex used to define the filter.
- Install the latest Applications or Applications and Threats update:
- Select DeviceDynamic Updates and Check Now.
- Download and Install any new update.
Determine which predefined Syslog Parse profiles are available:- Select DeviceUser IdentificationUser Mapping and click Add in the Server Monitoring section.
- Set the Type to Syslog Sender and click Add in the Filter section. If the Syslog Parse profile you need is available, skip the steps for defining custom profiles.
Define custom Syslog Parse profiles to create and delete user mappings.Each profile filters syslog messages to identify either login events (to create user mappings) or logout events (to delete mappings), but no single profile can do both.- Review the syslog messages that the syslog sender generates to identify the syntax for login and logout events. This enables you to define the matching patterns when creating Syslog Parse profiles.While reviewing syslog messages, also determine whether they include the domain name. If they don’t, and your user mappings require domain names, enter the Default Domain Name when defining the syslog senders that the User-ID agent monitors (later in this procedure).Select DeviceUser IdentificationUser Mapping and edit the Palo Alto Networks User-ID Agent Setup.Select Syslog Filters and Add a Syslog Parse profile.Enter a name to identify the Syslog Parse Profile.Select the Type of parsing to find login or logout events in syslog messages:
- Regex Identifier—Regular expressions.
- Field Identifier—Text strings.
The following steps describe how to configure these parsing types.(Regex Identifier parsing only) Define the regex matching patterns.If the syslog message contains a standalone space or tab as a delimiter, use \s for a space and \t for a tab.- Enter the Event Regex for the type of events you want to find:
- Login events—For the example message, the regex (authentication\ success){1} extracts the first {1} instance of the string authenticationsuccess.
- Logout events—For the example message, the regex (logout\ successful){1} extracts the first {1} instance of the string logoutsuccessful.
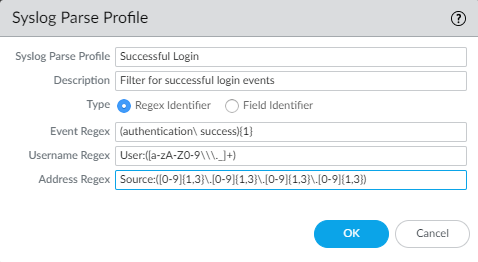
The backslash (\) before the space is a standard regex escape character that instructs the regex engine not to treat the space as a special character.Enter the Username Regex to identify the start of the username.In the example message, the regex User:([a-zA-Z0-9\\\._]+) matches the string User:johndoe1 and identifies johndoe1 as the username.Enter the Address Regex to identify the IP address portion of syslog messages.In the example message, the regular expression Source:([0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}) matches the IPv4 address Source:192.168.3.212.The following is an example of a completed Syslog Parse profile that uses regex to identify login events:![]() Click OK twice to save the profile.(Field Identifier parsing only) Define string matching patterns.
Click OK twice to save the profile.(Field Identifier parsing only) Define string matching patterns.- Enter an Event String to identify the type of events you want to find.
- Login events—For the example message, the string authentication success identifies login events.
- Logout events—For the example message, the string logoutsuccessful identifies logout events.
Enter a Username Prefix to identify the start of the username field in syslog messages. The field does not support regex expressions such as \s (for a space) or \t (for a tab).In the example messages, User: identifies the start of the username field.Enter the Username Delimiter that indicates the end of the username field in syslog messages. Use \s to indicate a standalone space (as in the sample message) and \t to indicate a tab.Enter an Address Prefix to identify the start of the IP address field in syslog messages. The field does not support regex expressions such as \s (for a space) or \t (for a tab).In the example messages, Source: identifies the start of the address field.Enter the Address Delimiter that indicates the end of the IP address field in syslog messages.For example, enter \n to indicate the delimiter is a line break.The following is an example of a completed Syslog Parse profile that uses string matching to identify login events:![]() Click OK twice to save the profile.Specify the syslog senders that the firewall monitors.Within the total maximum of 100 monitored servers per firewall, you can define no more than 50 syslog senders for any single virtual system.The firewall discards any syslog messages received from senders that are not on this list.
Click OK twice to save the profile.Specify the syslog senders that the firewall monitors.Within the total maximum of 100 monitored servers per firewall, you can define no more than 50 syslog senders for any single virtual system.The firewall discards any syslog messages received from senders that are not on this list.- Select DeviceUser IdentificationUser Mapping and Add an entry to the Server Monitoring list.Enter a Name to identify the sender.Make sure the sender profile is Enabled (default is enabled).Set the Type to Syslog Sender.Enter the Network Address (IP address) of the syslog sender.Select SSL (default) or UDP as the Connection Type.To select the TLS certificate that the firewall uses to receive syslog messages, select DeviceUser IdentificationUser MappingPalo Alto Networks User-ID Agent Setup. Edit the settings and select Server Monitor, then select the Syslog Service Profile that contains the TLS certificate you want to the firewall to use to receive syslog messages.The PAN-OS integrated User-ID agent accepts syslogs over SSL and UDP only. However, you must use caution when using UDP to receive syslog messages because it is an unreliable protocol and as such there is no way to verify that a message was sent from a trusted syslog sender. Although you can restrict syslog messages to specific source IP addresses, an attacker can still spoof the IP address, potentially allowing the injection of unauthorized syslog messages into the firewall.Always use SSL to listen for syslog messages because the traffic is encrypted (UDP sends the traffic in cleartext). If you must use UDP, make sure that the syslog sender and client are both on a dedicated, secure network to prevent untrusted hosts from sending UDP traffic to the firewall.A syslog sender using SSL to connect will show a Status of Connected only when there is an active SSL connection. Syslog senders using UDP will not show a Status value.For each syslog format that the sender supports, Add a Syslog Parse profile to the Filter list. Select the Event Type that each profile is configured to identify: login (default) or logout.(Optional) If the syslog messages don’t contain domain information and your user mappings require domain names, enter a Default Domain Name to append to the mappings.Click OK to save the settings.Enable syslog listener services on the interface that the firewall uses to collect user mappings.
- Select NetworkNetwork ProfilesInterface Mgmt and edit an existing Interface Management profile or Add a new profile.Select User-ID Syslog Listener-SSL or User-ID Syslog Listener-UDP or both, based on the protocols you defined for the syslog senders in the Server Monitoring list.The listening ports (514 for UDP and 6514 for SSL) are not configurable; they are enabled through the management service only.Click OK to save the interface management profile.Even after enabling the User-ID Syslog Listener service on the interface, the interface only accepts syslog connections from senders that have a corresponding entry in the User-ID monitored servers configuration. The firewall discards connections or messages from senders that are not on the list.Assign the Interface Management profile to the interface that the firewall uses to collect user mappings:
- Select NetworkInterfaces and edit the interface.
- Select AdvancedOther info, select the Interface Management Profile you just added, and click OK.
Commit your changes.Verify that the firewall adds and deletes user mappings when users log in and out.You can use CLI commands to see additional information about syslog senders, syslog messages, and user mappings.- Log in to a client system for which a monitored syslog sender generates login and logout event messages.Log in to the firewall CLI.Verify that the firewall mapped the login username to the client IP address:
> show user ip-user-mapping ip <ip-address> IP address: 192.0.2.1 (vsys1) User: localdomain\username From: SYSLOGLog out of the client system.Verify that the firewall deleted the user mapping:> show user ip-user-mapping ip <ip-address> No matched record