Prisma Access Agent
Prisma Access Agent Captive Portal Support
Table of Contents
Prisma Access Agent Captive Portal Support
Prisma Access Agent can now detect and handle captive portals to improve connectivity
in environments like hotels, cafes, and airports.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma Access Agent captive portal support is designed to improve the connectivity
experience for mobile users who frequently connect from networks with captive portals,
such as hotels, cafes, and airports. This feature uses the Prisma Access Agent embedded
browser to automatically detect and handle captive portal authentication, ensuring
integrated and secure access to corporate resources.
Learn about captive portal detection for macOS,
Winodws, and iOS devices, and get a preview of the captive portal user experience for
these devices. Finally, learn how to verify the presence of a captive portal (macOS and
Windows only).
Captive Portal Detection for macOS and Windows Devices
The captive portal detection mechanism uses a set of predefined URLs and network
probes to identify the presence of a captive portal. This detection process is
reliable and addresses issues where some captive portal providers could bypass
traditional detection techniques.
With captive portal detection, internet access becomes available only after users
log in to the captive portal. When a user connects to the Wi-Fi network and
Prisma Access Agent detects a captive portal, the agent launches the embedded
browser to handle the authentication process, containing the interaction within
a controlled environment and mitigating security risks associated with external
browser use.
When a user logs in successfully and the internet becomes reachable, the Prisma
Access Agent automatically establishes a connection. If the user fails to log in
to the captive portal, the agent blocks all traffic.
By default, Prisma Access Agent uses the embedded browser for SAML authentication
and captive portal.
Captive Portal Detection for iOS Devices
iOS devices automatically attempt to detect captive portals when connecting to
new networks. However, this native detection mechanism can be inconsistent,
sometimes causing the login page to never appear and preventing the user from
accessing the internet.
In per-app deployments, if iOS fails to automatically show the captive portal
login page, Prisma Access Agent will display a notification indicating the
presence of a captive portal. Users can tap the notification to manually open
the captive portal within the Prisma Access Agent embedded browser and complete
authentication. They can then enter the required credentials, accept the terms
of service, and complete the authentication process successfully to access the
internet. To enable captive portal support, enable per-app configuration
using your mobile device management (MDM) software.
This fallback mechanisms ensures that you can enforce browser traffic through the
tunnel while allowing users to maintain network access even if the operating
system's built-in captive portal detection fails. For detailed information about
how to log in to the captive portal environment for iOS per-app deployments,
refer to Use the Prisma Access Agent App for iOS
(Managed Devices).
User Experience in a Captive Portal Environment (macOS and Windows Agents)
When a user connects to a network with a captive portal, such as in a hotel or
airport, the Prisma Access Agent automatically detects the captive portal. The
embedded browser within the Prisma Access Agent
then
opens, displaying the captive portal login page. The user can enter their
credentials and accept the terms of service as required by the network provider.
The following is an example of a captive portal login page in the embedded
browser:
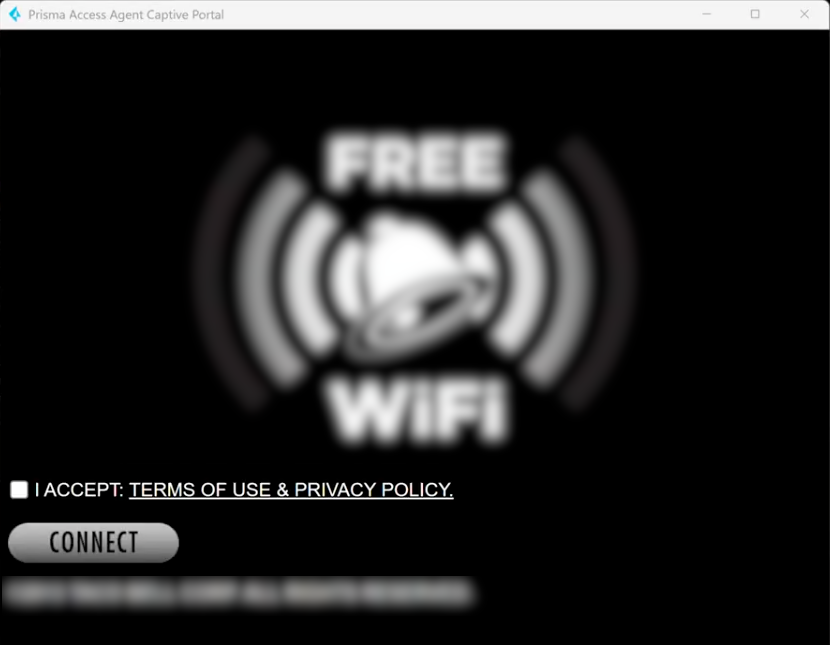
Once the user successfully authenticates through the captive portal, the Prisma
Access Agent automatically establishes a secure connection to the corporate network
if the agent is configured with an always-on connection. If they are using an
on-demand connection, they can select a location to connect to the corporate
network.
If the user disconnects from the Wi-Fi network that they use
to connect to Prisma Access Agent, they will have no connection to the internet.
After they authenticate to the captive portal in the embedded browser, they will
have a connection to their corporate network.
If the captive portal authentication fails or times out, the user can retry the
process by clicking the Connect button in the agent app.
This streamlined experience ensures that users can quickly and securely connect to
networks with captive portals, maintaining productivity while traveling or working
remotely.
User Experience in a Captive Portal Environment (Per-App iOS Agents)
When using Prisma Access Agents in a per-app configuration on iOS devices, the
captive portal experience follows a streamlined workflow. Upon connecting to a
network that requires captive portal authentication, such as public Wi-Fi at hotels,
airports, or cafes, users receive a notification from Prisma Access Agent indicating
that a captive portal is present. This serves as a backup mechanism when iOS's
native captive portal detection fails to automatically display the login page.
Users can tap the notification to launch the captive portal authentication page
within the Prisma Access Agent's embedded browser. Within this embedded browser,
users can enter their required credentials, review and accept terms of service, or
complete any other authentication steps required by the network provider. For
example:

Once the authentication process is successfully completed within the embedded
browser, users gain full internet access through the network. This streamlined
experience ensures that users can quickly and securely connect to networks with
captive portals, maintaining productivity while traveling or working remotely.
Verify the Presence of a Captive Portal (macOS and Windows Agents)
You can verify whether the agent detects a captive portal by using the Prisma
Access command-line tool (PACli) or checking the agent logs.
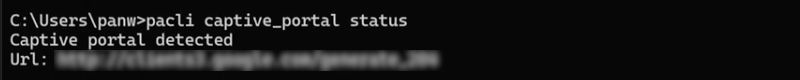
- To verify the presence of the captive portal using the PACli tool:
- Run the pacli captive_portal status command
on the endpoint. If Prisma Access Agent detects a captive portal, it
will return the Captive portal detected
message along with the URL of the captive portal login page. For
example:
![]()
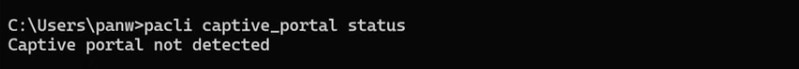
- After the user authenticates to the captive portal, the captive portal should no longer be active. Run the pacli captive_portal status command again. The command output should be Captive portal not detected. For example:
![]()
- Run the pacli captive_portal status command
on the endpoint. If Prisma Access Agent detects a captive portal, it
will return the Captive portal detected
message along with the URL of the captive portal login page. For
example:
- To check for captive portal-related activities in log files, check the agent logs as follows:
- Check the captive portal detection events, such as unexpected errors
and responses, in EndpointTroubleshooting (Prisma Access Agent) page in Strata Logging Service.The agent also writes these events to the PAS.log file on the endpoint.On Windows: %ProgramData%\Palo Alto Networks\Prisma Access Agent\Logs\PAS.logOn macOS: ~/Library/Logs/PaloAltoNetworks/Prisma Access Agent/PAS.log
- Check the captive portal detection and release events in the EndpointManagement logs in Strata Logging Service.
- Check the captive portal detection events, such as unexpected errors
and responses, in EndpointTroubleshooting (Prisma Access Agent) page in Strata Logging Service.