Prisma Access
Configure Re-authentication Timers for Dynamic Privilege Access Prisma Access Agents
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Re-authentication Timers for Dynamic Privilege Access Prisma Access Agents
Configure periodic re-authentication to maintain security compliance for Dynamic
Privilege Access-enabled Prisma Access Agent deployments.
| Where Can I Use This? | What Do I Need? |
|---|---|
Configure Re-authentication Timers for Dynamic Privilege Access Prisma Access Agents
|
|
The Dynamic Privilege Access-enabled Prisma Access Agent continuously validates user
trust through background authentication processes that do not interrupt user
activity. Customizable authentication timers extend this capability by giving you
control over when users must explicitly re-authenticate by providing their
credentials. This allows you to align authentication intervals with your
organizational security policies and compliance requirements.
Re-authentication Frequency
You can define the frequency that determines how often users must provide their
credentials. This frequency applies globally across your deployment and directly
controls the user refresh token lifetime. You set this interval between 10 hours and
30 days, with a default of 7 days.
Notification Settings
To prevent workflow disruption, you configure notification timers that alert users
before their authentication expires. You specify how many minutes in advance users
receive warnings, with a range of 5 to 120 minutes and a default of 60 minutes. You
can also customize the notification message that displays to users. If you leave the
re-authentication notification message empty, the agent displays a default
message.
Gateway Session Timeout
The gateway session timeout operates separately from re-authentication frequency and
controls how long an established connection to the gateway remains valid. You
configure this timeout at the Agent Settings level, with values ranging from 2 hours
to 30 days and a default of 10 days. This setting was previously named
Session Timeout and has been renamed to
Gateway Session Timeout for clarity. The notification
settings that were previously configurable at the agent level now map from the
Global Agent Settings.
Aggressive Authentication
For deployments requiring stricter security enforcement, you enable aggressive
authentication. This setting is available for Dynamic Privilege Access tenants and
defaults to false. When you enable aggressive authentication, the system forces
users to re-authenticate immediately during manual gateway reconnection, gateway
session extension, machine reboot, and user refresh token expiry. When aggressive
authentication is disabled, re-authentication is required only when the user refresh
token expires, and gateway session extension is seamless without requiring user
input.
Gateway Session Extension Behavior
When the Gateway Session Timeout is reached, the agent's
behavior for extending the tunnel depends on the Aggressive
Authentication configuration:
- Seamless Gateway ExtensionIf Aggressive Authentication is disabled (default), the gateway session extends automatically in the background. No user action or notification is required.
- Forced Re-authentication Gateway ExtensionIf Aggressive Authentication is enabled, users must explicitly re-authenticate.
- Users receive a notification before the re-authentication deadline.
- Clicking it starts the login flow while the tunnel remains active and backend jobs continue.
- If re-authentication is not completed in time, the tunnel disconnects, the agent app signs out, and users must log in again to restore access.
User Experience
When users reach the re-authentication threshold, their
experience varies based on your configuration and their current connection state.
Connected users receive notifications at the configured time before
re-authentication. When users click on the notification, the agent initiates the
login workflow while the existing tunnel remains up and backend jobs continue
uninterrupted. If users do not complete re-authentication before the deadline, the
user interface signs out from Endpoint Manager and users must re-authenticate to
restore access.
With aggressive authentication enabled, users must complete re-authentication while
the session timer counts down. If users complete re-authentication successfully, the
agent performs the session extension and the tunnel stays up. If users do not
complete re-authentication in time, the tunnel goes down and users must click
connect and re-authenticate to restore the tunnel.
For authentication methods using client certificates, re-authentication notification
does not apply. The agent automatically authenticates and refreshes tokens without
explicit user prompts.
Complete the following steps to maintain security compliance for your Prisma Access
Agent deployment.
- Configure global re-authentication settings that apply to all Prisma Access Agent users in your deployment.
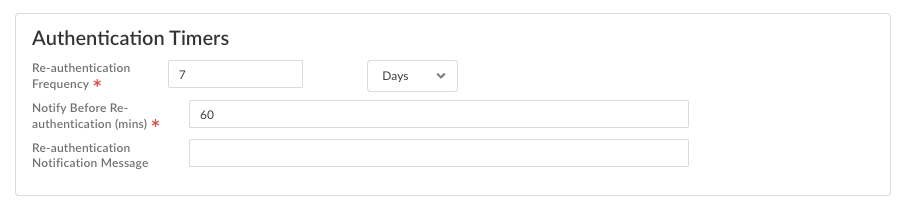
- From Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.Edit the Global Agent Settings by selecting the gear icon.In the Authentication Timers section, configure the Re-authentication Frequency by entering a value between 10 hours and 30 days. (Default: 7 days)
![]() Configure the Notify Before Re-authentication timer by entering a value in minutes between 5 and 120. (Default: 60 minutes)(Optional) Configure the Re-authentication Notification Message by taking one of the following actions:
Configure the Notify Before Re-authentication timer by entering a value in minutes between 5 and 120. (Default: 60 minutes)(Optional) Configure the Re-authentication Notification Message by taking one of the following actions:- Enter custom text with a maximum of 127 characters.
- Leave the field empty to use the default agent message ("User Session Expiring")
Save your configuration.Configure the gateway session timeout in the agent settings level to control how long an established connection remains valid.- Log in to Strata Cloud Manager as the Project Admin.Select ConfigurationNGFW and Prisma AccessOverview and expand the Configuration Scope to view the Snippets.Select the snippet you want to work with.Select ObjectsDynamic Privilege Access to open the Dynamic Privilege Access settings.Select the Agent Settings tab and select the agent setting you want to configure.In the App Configuration section, configure the Gateway Session Timeout by entering a value between 2 hours and 30 days. (Default: 10 days)
![]() Enable Aggressive Authentication to force immediate re-authentication during gateway connection and session extension events.
Enable Aggressive Authentication to force immediate re-authentication during gateway connection and session extension events.- When enabled, users must re-authenticate during manual gateway reconnection, gateway session extension, machine reboot, and user refresh token expiry.
- When disabled, re-authentication is required only when the user refresh token expires.
- The default is disabled.
Save your configuration.Push your configuration to the gateway.Verify that agents receive and apply the re-authentication timer and gateway session timeout settings.- On an endpoint running Prisma Access Agent version 26.1.1 or later, open a terminal or command prompt.Run the following command to check the Endpoint Manager status:
pacli epm status
Verify the User Refresh Token Expiry field in the output. Ensure that the value reflects your configured re-authentication frequency.Monitor agent logs for authentication timestamps, session establishment timestamps, re-authentication timer values, and authentication status.