- Home
- Prisma Access
- Prisma Access Administration
- Prisma Access Advanced Deployments
- Prisma Access Service Connection Advanced Deployments
- Preserve User-ID and Device-ID Mapping for Service Connections with Source NAT
- Preserve User and Device-ID Mapping for Service Connections with Source NAT (Panorama)
Prisma Access
Preserve User and Device-ID Mapping for Service Connections with Source NAT (Panorama)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Preserve User and Device-ID Mapping for Service Connections with Source NAT (Panorama)
Configure IPv6 availability for your Mobile Users—GlobalProtect deployments in
Panorama.
To have Prisma Access distribute User-ID mappings from GlobalProtect users to an NGFW
at the headquarters or data center in Prisma Access (Managed by Panorama), complete the
following steps.
This procedure assumes that you have the following network configuration in
place:
- You have enabled Data Traffic source NAT on the service connection.
- You have deployed an NGFW at the headquarters or data center where the private apps are located.
- You have applied security policy rules for Prisma Access on the NGFW based on zones you have created in the NGFW.
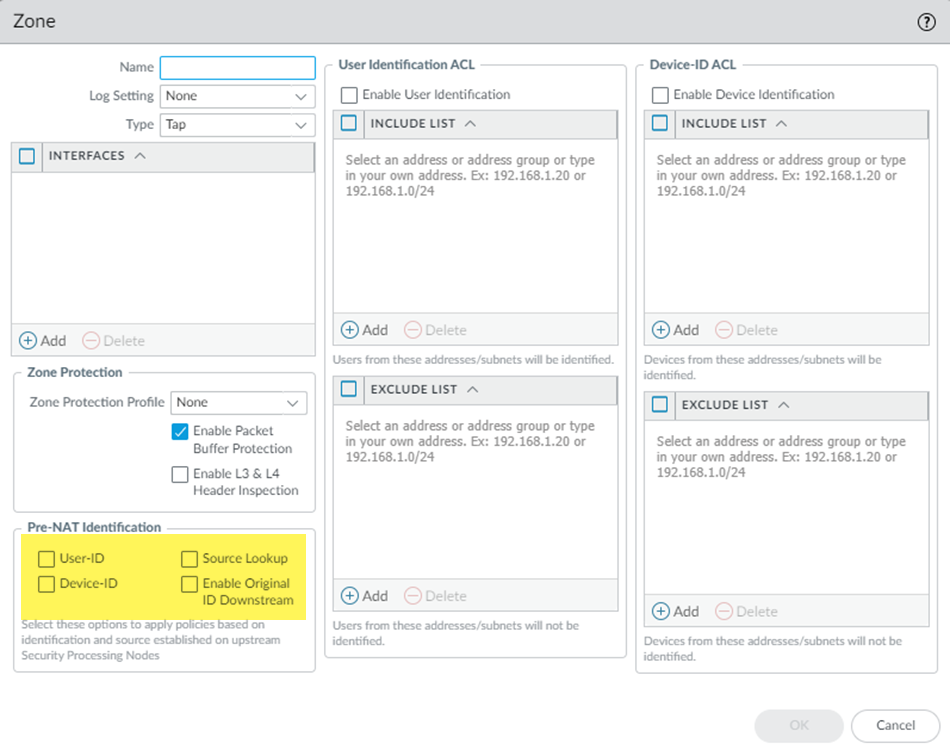
- Enter Pre-NAT Identification parameters on the NGFW.
- Log in to the NGFW, or log into the SCM or Panorama that manages the NGFW, and go to NetworkZones.Add a zone or select an existing zone.Select one or more Pre-NAT Identification parameters:
- User-ID—Preserves the mobile user User-ID mapping used before the IP addresses were NATted. Enable this if you're using User-IDs in security policy rules.
- Device-ID—Preserves the mobile user Device-ID mapping used before the IP addresses were NATted. Enable this if you're using Device-ID in security policy rules.
- Source Lookup—Enables you to match the original Source IP address received from GlobalProtect. If you're using source lookup in QoS or policy-based forwarding (PBF) policies, the source IP comparison is based on the pre-NAT source IP address. For example, if you had a security policy that allowed a source IP address of 1.1.1.1 and a destination IP address of Any, 1.1.1.1 is compared with the pre-NAT source IP address in the packet header.
- Enable Original ID Downstream—If you have two NGFWs in a row, specify this option to have the first NGFW send the pre-NAT information to the second NGFW after the first NGFW has inspected the traffic and applied policies to it. This is the default configuration on SC-CANs.
![]() Click OK and Commit your changes.Create a command-line interface (CLI) session with the NGFW and enter the following command in configuration mode:set deviceconfig setting preserve-prenat-feature yesIf you need to disable this feature in the future, enter set deviceconfig setting preserve-prenat-feature no.From the Panorama that manages Prisma Access, enable pre-NAT settings.
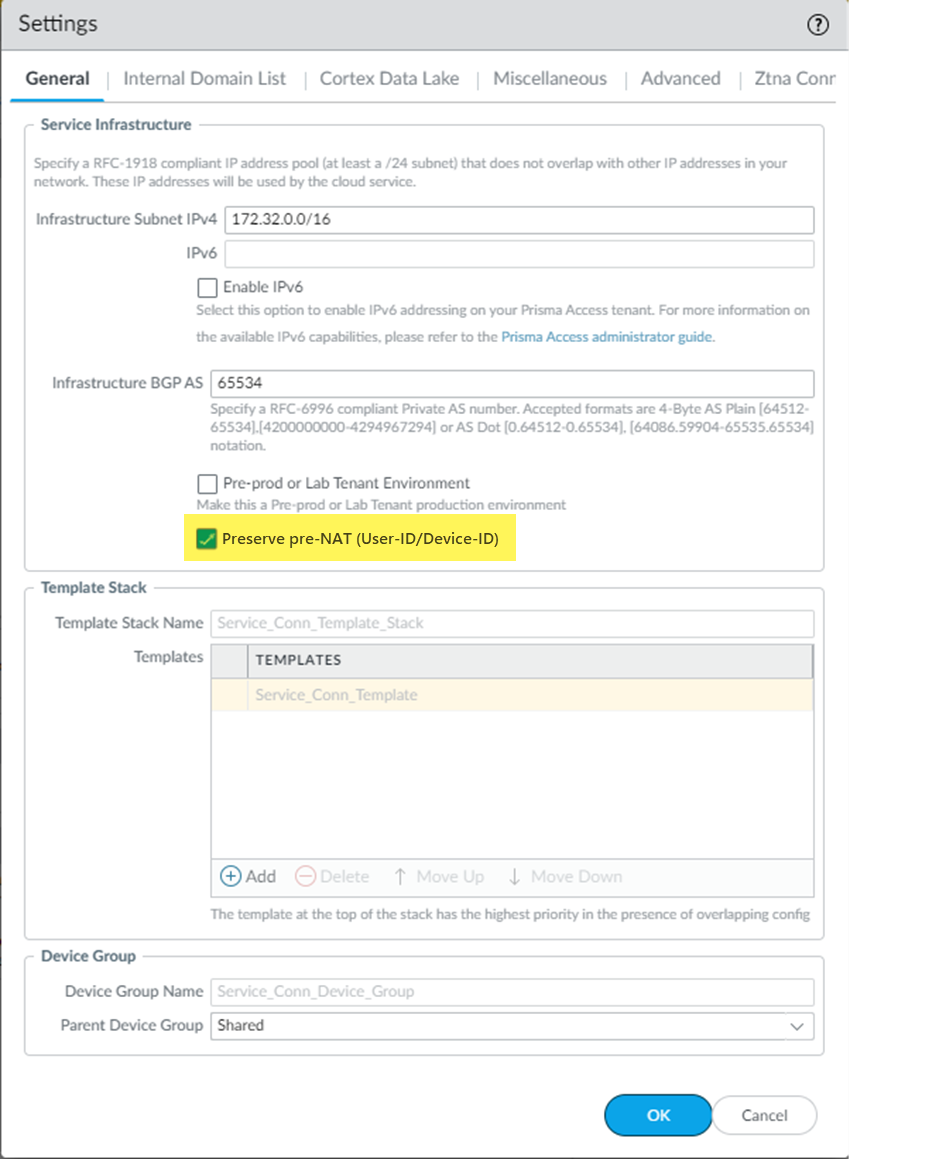
Click OK and Commit your changes.Create a command-line interface (CLI) session with the NGFW and enter the following command in configuration mode:set deviceconfig setting preserve-prenat-feature yesIf you need to disable this feature in the future, enter set deviceconfig setting preserve-prenat-feature no.From the Panorama that manages Prisma Access, enable pre-NAT settings.- Go to PanoramaCloud ServicesConfigurationService Setup and click the gear to edit the Settings.Select Preserve pre-NAT (User-ID/Device-ID).
![]() Commit and Push your changes.
Commit and Push your changes.