Prisma Access
Onboard the ZTNA Connector VM in Your Data Center
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Onboard the ZTNA Connector VM in Your Data Center
Configure the connectors that are used for ZTNA Connector.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
After you configure your Connector groups, connectors, and application targets within
Prisma Access, you must deploy the Connector VM in your data center. To simplify
Connector onboarding, deployment templates for each data center environment are
available from the Palo Alto Networks Customer Support Portal or from the cloud
provider marketplace. The template you use depends on whether you’re planning to use
a one-arm
deployment or a two-arm deployment.
Supported ZTNA Connector Deployments
ZTNA Connector initiates the connection to the Prisma Access public IP address in
the cloud, and you don't need to define any ingress firewall security rules.
However, because ZTNA Connector initiates the connection, you'll need to add
egress rules to allow ZTNA Connector access to the cloud controller and the
IPSec connection to the Prisma Access dataplane. ZTNA Connector
initiates the connection to the Prisma Access public IP address in the
cloud. For this reason, you need the following egress rules so that ZTNA
Connector can create an IPSec tunnel to Prisma Access:
- Internet Facing—Allow egress for HTTPS (TCP 443) and IKE/IPSec (UDP 500 and 4500)
- Data Center Facing—Allow egress application ports. For example, allow egress application ports HTTP (80) and HTTPS (443). These example ports are TCP ports. If your data center uses different ports, allow those ports instead.
You must configure the time to UTC for on-premises ZTNA Connector
deployments. For Cloud-based ZTNA Connector deployments, the underlying cloud VM
handles the time setting automatically.
You can deploy the Connector VM in the following deployment topologies:
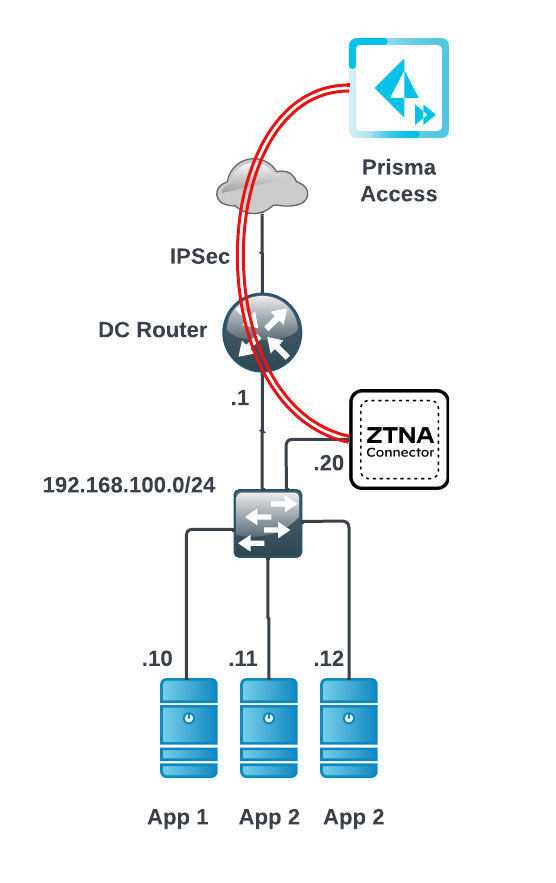
- One-Arm DeploymentOne-arm deployments are supported in cloud native environments such as AWS, Azure, GCP and OCI. In addition, one-arm deployments are supported in ESXi on-premise deployments. For other on-premise deployment for a a Kernel-based Virtual Machine (KVM) or or Microsoft Hyper-V, use the two-arm deployment.In this deployment, your ZTNA Connector is on a data center subnet that is private, with access to the internet through a data center router. Access to applications can be either locally on the same subnet, or through the data center router.The following diagram shows a sample ZTNA Connector network deployment using a one-arm deployment.
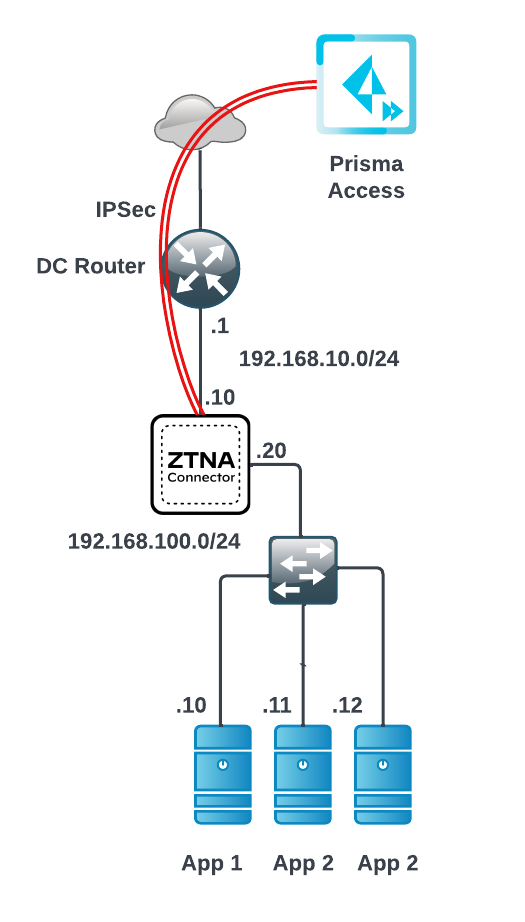
![]() Two-Arm deploymentIf you want more control over your ingress and egress security rules, or if you have an on-premise VM deployment, you can use a two arm deployment, where one interface faces the internet and one faces the data center.When setting up IP addresses on a two-arm connector, make sure that you have set up the IP address assignments for ZTNA Connector correctly before you power on the VM. For example, the following sample diagram uses 192.168.10.10 and 192.168.100.20 IP addresses. Given these sample addresses, set up the ports on ZTNA Connector for 192.168.10.10 and 192.168.100.20, or Prisma Access cannot reach the apps in the data center through ZTNA Connector. 192.168.10.10 and 192.168.100.20 are sample IP addresses and you do not have to use these IP addresses for your deployment to function.The following diagram shows a sample ZTNA Connector network deployment using a two-arm deployment.
Two-Arm deploymentIf you want more control over your ingress and egress security rules, or if you have an on-premise VM deployment, you can use a two arm deployment, where one interface faces the internet and one faces the data center.When setting up IP addresses on a two-arm connector, make sure that you have set up the IP address assignments for ZTNA Connector correctly before you power on the VM. For example, the following sample diagram uses 192.168.10.10 and 192.168.100.20 IP addresses. Given these sample addresses, set up the ports on ZTNA Connector for 192.168.10.10 and 192.168.100.20, or Prisma Access cannot reach the apps in the data center through ZTNA Connector. 192.168.10.10 and 192.168.100.20 are sample IP addresses and you do not have to use these IP addresses for your deployment to function.The following diagram shows a sample ZTNA Connector network deployment using a two-arm deployment.![]()